What’s new in Calico Enterprise 3.16: Egress gateway on AKS, Service Graph optimizations, and more!
We are excited to announce the early preview of Calico Enterprise 3.16. This latest release extends the active security platform’s support for egress access controls, improves the usability of network-based threat defense features, and scales visualization of Kubernetes workloads to 100s of namespaces. Let’s go through some of the highlights of this release.
Egress gateways for Microsoft Azure and AKS
Egress gateways allow you to identify the source of traffic at the namespace or pod level when it leaves a Kubernetes cluster to communicate to external resources. This makes it highly beneficial for security teams to apply access controls to specific traffic instead of opening up a larger set of IP addresses. Calico Enterprise 3.16 has added egress gateway support for Microsoft Azure and AKS in addition to our support for AWS and EKS. Check out our documentation, Configure egress gateways, Azure, to learn more.
Operator-managed deployments of egress gateways
Calico Enterprise now includes operator-managed deployments of egress gateways. This reduces operational overhead and eliminates additional steps required during software upgrades. With the Tigera Operator, egress gateways will always be automatically upgraded.
UI for workload-based web application firewalls (WAF)
Calico Enterprise’s unique workload-centric web application Continue reading
Navigating the security challenges of multi-tenancy in a cloud environment
Multi-tenancy can maximize the number of resources that are utilized in a cluster by sharing these resources between different groups, teams, or customers. However, boundaries must be placed to avoid problems associated with resource-sharing. On top of that, in a multi-tenant cluster, the number of security policies might gradually grow to the point where a slight misconfiguration could cause major security problems, performance issues, and service disruptions.
In this blog post, we will focus on multi-tenancy issues such as bandwidth shortage, security policy scaling, privacy impacts, and suggest a few solutions that you can deploy to solve them in your environment. We will also look at how an eBPF-based security design can offer better performance and help you navigate the complex multi-tenant environment with ease.
What is multi-tenancy?
Technologies such as virtualization, containerization, or any other technologies that allow a range of different workloads to share the underlying hardware resources, all have a common goal—allocate resources as efficiently as possible and make the most of the available hardware. However, it is common for workloads that are running in such an environment to not fully utilize all the potential power that the hardware can offer, and in many cases, leave a Continue reading
Process monitoring: How you can detect malicious behavior in your containers
The default pod provisioning mechanism in Kubernetes has a substantial attack surface, making it susceptible to malevolent exploits and container breakouts. To achieve effective runtime security, your containerized workloads in Kubernetes require multi-layer process monitoring within the container.
In this article, I will introduce you to process monitoring and guide you through a Kubernetes-native approach that will help you enforce runtime security controls and detect unauthorized access of host resources.
What is process monitoring?
When you run a containerized workload in Kubernetes, several layers should be taken into account when you begin monitoring the process within a container. This includes container process logs and artifacts, Kubernetes and cloud infrastructure artifacts, filesystem access, network connections, system calls required, and kernel permissions (specialized workloads). Your security posture depends on how effectively your solutions can correlate disparate log sources and metadata from these various layers. Without effective workload runtime security in place, your Kubernetes workloads, which have a large attack surface, can easily be exploited by adversaries and face container breakouts.
Traditional monitoring systems
Before I dive into the details on how to monitor your processes and detect malicious activities within your container platform, let us first take a look at some of Continue reading
The MITRE ATT&CK framework explained: Discerning a threat actor’s mindset
This is part 2 of the blog series on the MITRE ATT&CK framework for container security, where I explain and discuss the MITRE ATT&CK framework. For those who are not familiar with what the MITRE framework is, I encourage you to read part 1.
In my previous blog post, I explained the first four stages of the MITRE ATT&CK framework and the tactics used by adversaries to gain a foothold in the network or the environment within a containerized application. What happens next?
Imagine a military battalion trying to invade its enemy’s territory. What would a soldier do once they’ve infiltrated the opposition? They would take cover and wait for the right opportunity to attack. Similarly, in cyber crime, an attacker will take time to make sure they evade any type of defense that has been put in place. This is the fifth stage in the MITRE ATT&CK framework. In this article, I will explore this fifth stage, along with stages six through nine, and look at how Calico can help mitigate the attack techniques used in these stages.
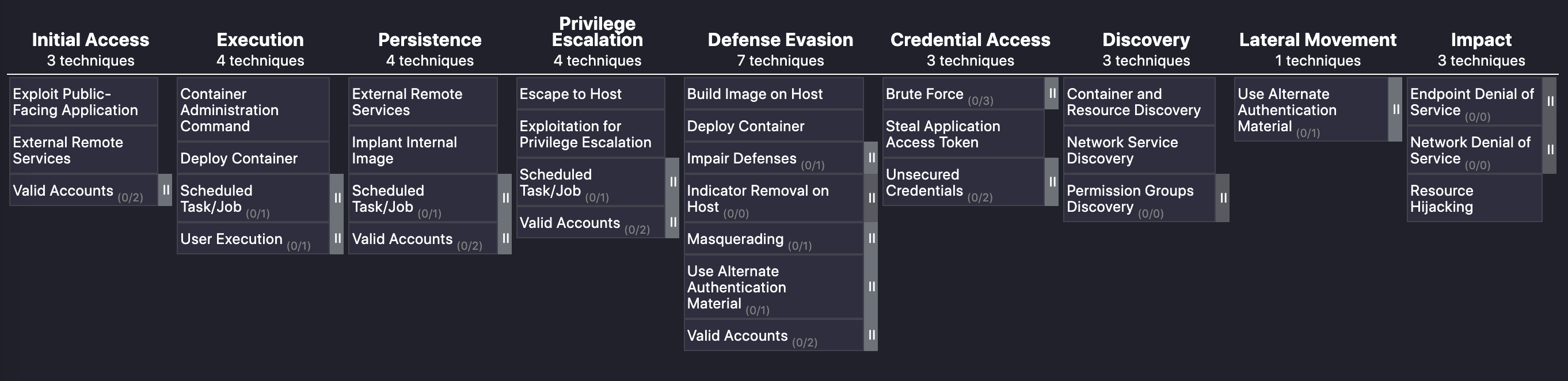
Delivery and exploitation tactics
Defense evasion
Many security solutions offer Continue reading
High throughput Kubernetes cluster networking with the Calico/VPP dataplane and accelerated memif
This blog post was written in collaboration with:
Aloys Augustin, Nathan Skrzypczak, Hedi Bouattour, Onong Tayeng, and Jerome Tollet at Cisco. Aloys and Nathan are part of a team of external contributors to Calico Open Source that has been working on an integration between Calico Open Source and the FD.io VPP dataplane technology for the last couple of years.
Mrittika Ganguli, principal engineer and architect at Intel’s Network and Edge (NEX). Ganguli leads a team with Qian Q Xu, Ping Yu, and Xiaobing Qian to enhance the performance of Calico and VPP through software and hardware acceleration.
This blog will cover what the Calico/VPP dataplane is and demonstrate the performance and flexibility advantages of using the VPP dataplane through a benchmarking setup. By the end of this blog post, you will have a clear understanding of how Calico/VPP dataplane, with the help of DPDK and accelerated memif interfaces, can provide high throughput and low-latency Kubernetes cluster networking for your environment. Additionally, you will learn how these technologies can be used to reduce CPU utilization by transferring packets directly in memory between different hosts, making it an efficient solution for building distributed network functions with lightning-fast speeds.
What’s Continue reading
Kubernetes network monitoring: What is it, and why do you need it?
In this article, we will dive into Kubernetes network monitoring and metrics, examining these concepts in detail and exploring how metrics in an application can be transformed into tangible, human-readable reports. The article will also include a step-by-step tutorial on how to enable Calico’s integration with Prometheus, a free and open-source CNCF project created for monitoring the cloud. By the end of the article, you will be able to create customized reports and graphical dashboards from the metrics that Calico publishes to get better insight into the inner workings of your cluster and its various components. In addition, you will have the fundamental knowledge of how these pieces can fit together to establish Kubernetes network monitoring for any environment.
Background
The benefits offered by cloud computing and infrastructure as code, including scalability, easy distribution, and quick and flexible deployment, have caused cloud service adoption to skyrocket. But this rapid adoption requires checks and balances to ensure that cloud services are secure and running in their desired state. Furthermore, any security events and problems should be logged and reported for future examination.
Read our guide on Kubernetes logging: Approaches and best practices
In the past, traditional monitoring solutions such as Nagios Continue reading
Calico Open Source 2022 highlights
2022 has been a year full of new releases, new events, and new projects for Open Source Calico. Let’s take a look at Project Calico’s 2022 highlights and see if you’ve missed any exciting news.
New version releases
Project Calico is maintained by Tigera’s engineering team who are dedicated to adding new features, fixing bugs, and improving the user experience. Based on the feedback and support our team has received from the community, they have successfully released three new versions of Calico in the past year: v3.22, v3.23, and v3.24.
V3.22 (January 28th 2022)
- Project Calico is now only a single directory, making it easier for contributors to add their changes
- Ability to convert Kubernetes NetworkPolicy objects into Calico NetworkPolicies
V3.23 (May 9th 2022)
- Added IPv6 VXLAN support
- Added VPP dataplane beta
- Added Calico networking support in AKS
- BGP enhancements
- Added container storage interface (CSI) support
- Added Windows HostProcess containers support (tech preview)
V3.24 (August 18th 2022)
- Added IPv6 WireGuard support
- Added IPAM API enhancements
- More operator installation configuration options
- Added ability to split IP pools
- Transitioned from pod security policies to pod security standards
Calico education and training
The newest addition to our Continue reading
Accelerating cloud-native development brings opportunities and challenges for enterprises
By 2025, Gartner estimates that over 95% of new digital workloads will be deployed on cloud-native platforms, up from 30% in 2021. This momentum of these workloads and solutions presents a significant opportunity for companies that can meet the challenges of the burgeoning industry.
As digitalization continues pushing applications and services to the cloud, many companies discover that traditional security, compliance, and observability approaches do not transfer directly to cloud-native architectures. This is the primary takeaway from Tigera’s recent The State of Cloud-Native Security report. As 75% of companies surveyed are focusing on cloud-native application development, it is imperative that leaders understand the differences, challenges, and opportunities of cloud-native environments to ensure they reap the efficiency, flexibility, and speed that these architectures offer.
Containers: Rethinking security
The flexibility container workloads provide makes the traditional ‘castle and moat’ approach to security obsolete. Cloud-native architectures do not have a single vulnerable entry point but many potential attack vectors because of the increased attack surface. Sixty-seven percent of companies named security as the top challenge regarding the speed of deployment cycles. Further, 69% of companies identified container-level firewall capabilities, such as intrusion detection and prevention, web application firewall, protection from “Denial of Service” Continue reading
What’s new in Calico v3.25
We’ve just released Calico v3.25! This milestone release includes a number of eBPF dataplane improvements designed to deliver an even faster upgrade experience, smaller memory footprint, and shorter eBPF networking object load time speed.
But before we get into the details of these changes, let’s welcome and thank our new community problem-solvers who got their first contribution requests merged into our beloved project.
Community shoutout
Documentation is the most essential part of any project since that is the go-to place for everyone to get a better idea about the capabilities or deployment of that project. So let’s start by giving a big shout-out to @cavcrosby, @Congrool, @chenbojian, and @gopihc for their attention to detail and fixing issues in the project documentation.
Shoutout to @OrvilleQ and @masap for extending the exclusion list of interfaces to make the automatic interface selection of Calico even faster.
Shoutout to @gregwhorley, @dlipovetsky, @nickperry, and @tamcore for their updates to `tigera-operator` that will make the installation and maintenance experience of Calico even better.
Shoutout to @ramanujadasu for enhancing the logic behind the unicast IP address hashing.
Shoutout to @chrisjohnson00 and @vitaliy-leschenko for enhancing the Calico windows installer and adding Continue reading
Tigera 2023 predictions: Cloud native security and the shifting landscape in 2023
Cloud computing and the use of cloud native architectures enable unparalleled performance, flexibility, and velocity. The speed of innovation has driven significant advancements across industries, but as digitalization continues pushing applications and services to the cloud, bad actors’ intrusion techniques have also become more sophisticated. The burgeoning threat landscape is top of mind for enterprise and midmarket business and security leaders, and should lead their decision-making—from the right solutions to implement, to the right partners to engage.
Economic conditions tightening and macroeconomic forces will continue introducing challenges in the coming year, but businesses that sustainably provide value to their customers and make security a foundational aspect of their organization will thrive.
Here are some trends I anticipate for 2023:
Cloud-native inflection point
While the last few years were dominated by early adopters who thrive in the technical playgrounds of emerging technologies, 2023 will see the ‘early majority’ of mainstream users begin adopting cloud-native architectures as the market reaches an inflection point. This inflection is driven by the accelerating accessibility and usability of the tools and technologies available, as the early majority prioritizes platforms that work easily over those with advanced functions that they likely won’t use.
“Shift left” has become Continue reading
Case study: How Mulligan Funding built a SOC 2-compliant fintech SaaS platform with Calico Cloud
The rise of fintech has pushed traditional financial institutions to provide online-based services and launch fintech applications. But these services must be secure and meet certain regulatory requirements, such as the Payment Card Industry Data Security Standard (PCI DSS), the General Data Protection Regulation (GDPR), or SOC 2.
When our customer, Mulligan Funding, needed to launch a new fintech SaaS platform, they had to ensure that all communication to and from the application would be secure and SOC 2 compliant, since the platform would handle sensitive personal and financial data. To achieve this, Mulligan Funding decided to standardize on Microsoft Azure Kubernetes Service (AKS) and chose Calico Cloud for its security and compliance needs.
Case study highlights
Mulligan Funding faced two major challenges when it came to achieving SOC 2 compliance:
- Ensure compliance and be notified of any control changes 24/7 in a way that’s scalable
- Gain visibility into clusters to immediately pinpoint issues that require troubleshooting
Read the case study to learn:
- How Mulligan Funding bolstered its security posture at scale through unified security policy management.
- Why deploying Calico Cloud not only helped Mulligan Funding achieve compliance, but also helped the company reduce service distributions and optimize troubleshooting.
Read Continue reading
Securing Windows workloads
Containers are a great way to package applications, with minimal libraries required. It guarantees that you will have the same deployment experience, regardless of where the containers are deployed. Container orchestration software pushes this further by preparing the necessary foundation to create containers at scale.
Linux and Windows support containerized applications and can participate in a container orchestration solution. There is an incredible number of guides and how-to articles on Linux containers and container orchestration, but these resources get scarce when it comes to Windows, which can discourage companies from running Windows workloads.
This blog post will examine how to set up a Windows-based Kubernetes environment to run Windows workloads and secure them using Calico Open Source. By the end of this post, you will see how simple it is to apply your current Kubernetes skills and knowledge to rule a hybrid environment.
Windows containers
A container is similar to a lightweight packaging technique. Each container packages an application in an isolated environment that shares its kernel with the underlying host, making it bound by the limits of the host operating system. These days, everyone is familiar with Linux containers, a popular way to run Linux-based binary files in an Continue reading
How to build a service mesh with Istio and Calico
Microservices are loosely coupled software that provides flexibility and scalability to a cloud environment. However, securing this open architecture from vulnerabilities and malicious actors can be challenging without a service mesh.
This blog post will demonstrate how you can create an Istio and Calico integration to establish a service mesh that will manipulate HTTP traffic in the application layer. This Istio-Calico integration provides a unified way to write security policies interacting with applications and implement restrictions without disturbing the entire system.
What’s a service mesh?
A service mesh is a software layer that sits between the microservices that form your workload. After deploying and enabling a service mesh system for your workloads, an injector will add a sidecar container to each. These sidecars then collect and manipulate information via the rules you provide, allowing you to secure your cluster on an application level without requiring any change inside your software.
Without a service mesh, to ensure communication integrity and confidentiality between workloads, you must modify each to embed encryption methods. On top of that, gathering insight into the events that are happening in the application layer will require modifying the workload application itself, which all requires a good amount of Continue reading
What’s new in Calico Enterprise 3.15: FIPS 140-2 compliance, new dashboards, egress gateway pod failover, and more!
Tigera provides the industry’s only active Cloud-Native Application Security Platform (CNAPP) for containers and Kubernetes. Available as a fully managed SaaS (Calico Cloud) or a self-managed service (Calico Enterprise), the platform prevents, detects, troubleshoots, and automatically mitigates exposure risks of security issues in build, deploy, and runtime stages across multi-cluster, multi-cloud, and hybrid deployments.
We are very excited to unveil Calico Enterprise 3.15 and its new capabilities that will further reduce your applications’ attack surface and improve threat detection capabilities. Read this blog to learn about some of the biggest highlights of this latest release.
FIPS-140-2 compliance for US federal regulation
US federal agencies require that any software they use be compliant with the Federal Information Processing Standard (140-2), also known as FIPS 140-2. FIPS 140-2 specifies security requirements that are satisfied by a cryptographic module of applications and environments. With the release of Calico Enterprise 3.15, you can now configure Calico Enterprise to run in a FIPS 140-2 level 1 compliant mode to pass compliance requirements when serving US federal regulatory agencies.
When installing Calico Enterprise, you now have the option to install the platform in FIPS-compliant mode. This will ensure that the Calico components that are Continue reading
New! Free self-paced workshops for containers and Kubernetes
There’s no better way to learn something than to get hands-on. Tigera is excited to present its brand new (and completely free!) self-paced workshops for containers and Kubernetes. Each workshop comes with your own provisioned sample application (Hipstershop) and Calico Cloud lab environment for a limited time.
The first self-paced workshop we’ve launched is on compliance for containers and Kubernetes. Let’s take a closer look at why you should enroll in our compliance workshop and what you’ll gain.
Why get hands-on with achieving compliance?
From the Payment Card Industry Data Security Standard (PCI DSS) to the Health Insurance Portability and Accountability Act (HIPAA) to the General Data Protection Regulation (GDPR), most industries must meet certain compliance requirements when it comes to handling personal data. This could mean implementing resource access control, isolating workloads with sensitive data, or enforcing more advanced security controls such as logging all customer confidential data transactions. No matter what sort of controls you need to implement, the compliance auditor will require proof of compliance, such as what security controls are currently in place, whether control changes can be detected, and if compliance can be verified on demand. The ephemeral nature of Kubernetes can make it Continue reading
Live next week: The CalicoCon + Cloud-Native Security Summit!
Tigera is delighted to present the annual CalicoCon + Cloud-Native Security Summit on December 7th, 2022, 9:45 a.m. – 4:00 p.m. PT. This is your chance to network with top cloud-native platform, security, DevOps, and site reliability engineer (SRE) teams, and explore real-world use cases with major players in the cloud-native industry.
Live, free, and fully virtual, the Summit gathers industry experts to explore the best practices for securing, observing, and troubleshooting cloud-native applications through real-world stories.
Who should attend?
The Summit is curated for security, DevOps, SRE, and platform architect teams in the cloud-native world.
- Security teams – Learn how to holistically secure your cloud-native applications using today’s best practices.
- DevOps and SRE teams – Find out how you can incorporate security and observability in your CI/CD pipeline to enable security, observability, and troubleshooting,
- Platform Architects – Learn architecture patterns and best practices to secure and troubleshoot cloud-native applications,
Speakers and sessions
From panels to workshops to fireside chats, the Summit offers a variety of interactive sessions. Here’s a quick peek at some of our speakers and sessions:
- Lyudmila Huzenko from Playtech will talk about Playtech’s journey with Calico toward GitOps network security management in Kubernetes.
- Tapas Continue reading
Using Calico to create a Kubernetes cluster mesh for multi-cluster environments
Kubernetes has come of age with more organizations adopting a microservices architecture at scale. But scale brings a whole slew of new challenges, especially with Kubernetes, which is designed to operate as a single cluster. However, the usage of Kubernetes, especially at leading-edge organizations operating at scale, has crossed the single-cluster threshold. Organizations are building and deploying services across multiple clusters for high availability, disaster recovery, application isolation, compliance, latency concerns, staged migration, and multi-tenancy reasons.
Regardless of the reasons to deploy multiple clusters, platform and application teams must address networking, security, and observability issues related to microservices deployed across multi-clusters, sometimes spanning hybrid and multi-cloud environments.
Calico, the most widely adopted container networking and security solution (according to a recently published container adoption report by Datadog), provides an operationally simple solution to solve the networking, security, and observability challenges of running multi-cluster Kubernetes environments.
Security, observability, and networking requirements for multiple Kubernetes clusters
In simple terms, creating a multi-cluster Kubernetes environment requires stitching multiple Kubernetes clusters together to provide a common set of services. To create a single logical environment spanning multiple clusters, the key requirements are:
- Enabling inter-cluster communication – Communication across pods located in different clusters is Continue reading
Using the MITRE ATT&CK framework to understand container security
As innovations in the world of application development and data computation grow every year, the “attack surface” of these technologies grows as well. The attack surface has to be understood from two sides—from the attacker’s side and from the organization being attacked. For the attacker, they benefit from the entry point into a system, either through the ever-growing perimeter of public-facing applications or the people managing these applications, because the probability of finding a weakness to enter from these entry points is higher. For the organization, managing the attack surface requires investing in more security tools and personnel. This can cascade into bigger security issues, which is why addressing the attack surface is essential.
The MITRE adversarial tactics, techniques, and common knowledge (ATT&CK) framework can help us understand how this large attack surface can be exploited by an adversary and how they strategize an attack. In this two-part blog, I will cover the new ATT&CK matrix for containers and how Calico provides mitigation solutions for each tactic in the matrix. In this blog, we will explore the first four tactics, which mostly deal with reconnaissance. In the second part, we will discuss the techniques and mitigation strategies once an attacker Continue reading
3 container security best practices to strengthen your overall security posture
Container environments are highly dynamic and require continuous monitoring, observability, and security. Since container security is a continuous practice, it should be fully integrated into the entire development and deployment cycle. Implementing security as an integral part of this cycle allows you to mitigate risk and reduce the number of vulnerabilities across the dynamic and complex attack surface containers present.
Let’s take a look at three best practices for ensuring containers remain secure during build, deployment, and runtime.
Securing container deployments
Securing containers during the build and deployment stages is all about vulnerability management. It’s important to continuously scan for vulnerabilities and misconfigurations in software before deployment, and block deployments that fail to meet security requirements. Assess container and registry image vulnerabilities by scanning first- and third-party images for vulnerabilities and misconfigurations, and using a tool that scans multiple registries to identify vulnerabilities from databases such as NVD. You also need to continuously monitor images, workloads, and infrastructure against common configuration security standards (e.g. CIS Benchmarks). This enables you to meet internal and external compliance standards, and also quickly detect and remediate misconfigurations in your environment, thereby eliminating potential attack vectors.
Securing containers at runtime
Containerized workloads require a Continue reading
Getting started with EKS and Calico
Cloud-native applications offer a lot of flexibility and scalability, but to leverage these advantages, we must create and deploy a suitable environment that will enable cloud-native applications to work their magic.
Managed services, self-managed services, and bare metal are three primary categories of Kubernetes deployment in a cloud environment. Our focus in this article will be on Amazon Web Service’s (AWS) managed Kubernetes service, Elastic Kubernetes Service (EKS), and capabilities that Calico Open Source adds to the EKS platform.
Managed services
A managed cluster is a quick and easy way to deploy an enterprise-grade Kubernetes cluster. In a managed cluster, mundane operations such as provisioning new nodes, upgrading the OS/Kubernetes, and scaling resources are transferred to the cloud provider, which allows you to expand your application with ease.
EKS is a managed service by AWS that offers a fault-tolerant Kubernetes control plane endpoint and automates worker node maintenance and deployment process.
Comparing popular CNI options in EKS
Most popular managed services, such as EKS, come with an official CNI that offers networking and other features for your cluster. While these CNIs are highly integrated with the underlying system, they can introduce some limitations. To remedy these limitations and unlock the Continue reading