Spotlight on NSX Performance at VMworld 2020
As we ramp up towards one of the premiere online tech events — in one of the most extraordinary years of a lifetime — I would like to shine a spotlight on what is being planned around NSX performance during this year’s virtual conference to help you get the most out of the event. VMWorld 2020 is right around the corner — and for the first time in two decades, it’s free! So, Register Now if you haven’t done so already!
NSX Performance Thus Far
Over the years, we’ve looked at the NSX performance numbers with and without hardware-level features, such as Geneve Offload and Geneve Rx Filters, that are key to optimal performance. If these topics are new to you, I would encourage reading up on the performance section of the NSX-T Reference Design Guide for a working knowledge of NSX-T performance before attending this year’s NSX-T Performance Session at VMworld.
NSX-T Performance Session at VMworld 2020
Given the virtual format of this year’s NSX-T Performance Session, I’ve decided to take a slightly different approach. Not only will I share performance numbers, but I’ll also demonstrate how different hardware-level features influence performance, and I’ll discuss feature and tuning Continue reading
NSX for vSphere to NSX-T Migration Resources at VMworld 2020
VMworld, the industry’s largest virtualization-specific event, is right around the corner! As you get ready for VMworld, this blog is your resource for key sessions around migrating from NSX for vSphere to NSX-T. And, via the comments below, this blog is also your channel to connect back with us if you have any questions, need further clarifications, or would like a follow up call on migration strategies.

Learn from the Experts at VMworld
So, you’re on NSX for vSphere and you’ve been coming across all the use cases addressed by NSX-T. To take advantage of those use cases, you decide you want to move to NSX-T. And you’re wondering:
- Are there any VMware-supported built-in tools?
- Can I do this by myself?
- Is there a migration process that resembles upgrading?
- Can this be done without adding net-new hardware?
We Answer Those Questions At VMworld Breakout Sessions
Join us at the VMworld breakout session VCNC1150: Migrating from NSX for vSphere to NSX-T Data Center Using Migration Coordinator as we explore various migration approaches and dive into a detailed demo of Migration Coordinator. Designed to provide the simple experience of an upgrade, Migration Coordinator is a built-in tool that allows our customers Continue reading
Evolution of Excel 4.0 (XL4) Macro Weaponization Presentation
What is Virus Bulletin?
Virus Bulletin (often abbreviated as “VB”) is a magazine devoted to the discussion of malware and spam and has been around over 30 years. It is the forum in which security researchers and professionals discuss and share new directions in both the development of and protection against malware and spam. VB’s annual conference is almost as old as the magazine and has traditionally takes place in late September or early October each year.
Why Attend VB2020?
As always, this year’s VB conference covers a broad spectrum of topics by some of the most talented security researchers in the world. Included in the agenda is a paper published by three members of our VMware Threat Analysis Unit discussing how the weaponization of XL4 macros in Excel has evolved.
Excel 4.0 (XL4) macros have become increasingly popular for attackers, as many security vendors struggle to play catchup and detect them properly. This technique provides attackers with a simple and reliable method to get a foothold on a target network, as it simply represents an abuse of a legitimate 30-year-old feature of Excel and does not rely on any vulnerability or exploit to be successful.
Register to attend Continue reading
Explore VMware Tanzu Service Mesh at VMworld 2020

It’s that time of year again — VMworld! And while this year, due to COVID-19, we’re pivoting to a virtual format, we’ll, we still be delivering a top-notch event with great sessions on cutting edge innovations. And the best part is, it’s FREE!
One of the hottest topics these days is service mesh, which is an abstraction that takes care of service to service communication, security, and observability. At VMware, we’re the “abstraction company” — but we’re not just working on the immediate use cases that the rest of the pack are working on, we’re ahead of the game, extracting a lot more value from our unique position vis a vis abstraction.
Service Mesh Sessions You Won’t Want to Miss:
I’ve compiled a list of our service mesh sessions below so you can easily register for them:
- Introduction to Tanzu Service Mesh [MAP1231] – This session, delivered by yours truly and Oren Penso, will take you step by step from understanding what service mesh is at the most basic level to understanding the unique value of VMware’s Tanzu Service Mesh. As we usually do, this session will have plenty of good demos.
- Connect and Secure Your Applications Through Continue reading
Announcing VMware Container Networking with Antrea for Kubernetes
By Cody McCain, Senior Product Manager and Susan Wu, Senior Product Marketing Manager, Networking and Security Business Unit
Enterprises benefit from collaborative engineering and receive the latest innovations from open source projects. However, it’s a challenge for enterprise to rely solely on community support to run their operations. This is because community support is best-effort and cannot provide a pre-defined SLA.
While Kubernetes itself is open source, and part of Cloud Native Computing Foundation (CNCF), it takes an ecosystem of surrounding technologies as curated by CNCF—from the container registry and storage engine to the container network plugin to run Kubernetes.
Announcing VMware Container Networking with Antrea
With the new release of VMware Container Networking with Antrea, enterprises get the best of both worlds – access to the latest innovation from Project Antrea and world-class support from VMware. Container Networking with Antrea is the commercial offering consisting of and 24/7 support for Project Antrea.
Container Networking with Antrea will package the latest release of Project Antrea version 0.9.1. Antrea is a purpose-built Kubernetes networking solution for public and private clouds building upon Open vSwitch, the open source technology optimized for distributed multi-layer switching performance. Antrea is designed to run anywhere Kubernetes Continue reading
How to Simplify and Accelerate Network Segmentation
Network segmentation—splitting a network into subnetworks or segments—is widely accepted to be a powerful and effective method for improving cybersecurity within the data center. Yet even though it’s acknowledged to be an essential component of network security hygiene, organizations have frequently avoided putting segmentation into practice.
Why? Because historically network segmentation has been complex, disruptive, and time-consuming to implement, requiring extensive changes to the physical network and/or network addresses. The potential impact of taking applications offline for network changes means that many organizations decide to forego this industry-wide best practice. Teams that do forge ahead often face months- or years-long effort to create security zones by re–architecting the network, relocating equipment, and re-assigning IP addresses.
It doesn’t have to be that way. Today there’s an elegant solution that greatly simplifies and accelerates network segmentation: VMware NSX Service-defined Firewall. Purpose–built to protect east-west traffic, VMware Service-defined Firewall enables segmentation without any disruptive physical network or address changes.
Attackers Love Flat Networks
To back up a step, let’s examine why network segmentation Continue reading
Eliminate East-West Traffic Hair-Pinning
A firewall is a firewall, right? While on the surface that assumption may appear to be correct, a closer look reveals that there are critical differences between a traditional, appliance-based firewall that protects your network perimeter and a distributed, scale-out internal firewall that protects east-west traffic within your data center.
It’s true that both types of firewalls monitor network traffic, detect threats, and block malicious activity. However, appliance-based firewalls are designed to monitor north-south traffic, which has different volumes and characteristics than east-west traffic. Traditional north-south firewalls were never designed to be used interchangeably to protect both north-south and east-west traffic.

Figure 1: Data center traffic patterns
While it might appear to be the right choice, provisioning appliance-based firewalls for east-west traffic monitoring is not only expensive, it’s highly ineffective in delivering the level of control and performance required to protect growing numbers of dynamic workloads.
Creating Traffic Jams During Volume Spikes
One of the most common drawbacks of using appliance-based firewalls as internal firewalls is the need to hairpin east-west traffic to and Continue reading
The NSX-T Gateway Firewall Secures Physical Servers
To date, our blog series on securing physical servers with NSX Data Center has covered the use of bare metal agents installed in a physical server. In this scenario, NSX bare metal agents provide management and enforcement of security policy for the physical server. For a quick recap of how NSX Data Center secures physical server traffic, please review our first and second blogs in this multi-part series. In this article, we will discuss the use of one of the NSX-T Gateway services of an NSX Edge Node. Specifically, the NSX-T Gateway Firewall secures physical servers.
What’s The NSX-T Edge?
The NSX-T Edge is a feature-rich L3-L7 gateway. A brief review of some NSX-T Edge services:
- Via Tier-0 Gateway, routing between the logical and the physical using dynamic routing protocols (eBGP and iBGP) as well as static routing
- Via Tier-1 Gateway, routing between logical network segments, or from logical network segments to uplink to the Tier-0 Gateway
- Routing for IPv4 and IPv6 addresses
- Load Balancing via NSX-T Edge, which offers high-availability service for applications and distribution of network traffic load
- Network Address Translation (NAT), available on tier-0 and tier-1 gateways
- To manage IP addresses, the configuration of DNS (Domain Continue reading
Phased Approach to Securing a Data Center
In the fight against relentless cyberattacks, organizations have long relied on traditional perimeter firewalls to protect sensitive workloads and information in the data center. But today, in the era of distributed applications and hybrid cloud environments, we know that perimeter defenses are not enough to stop cybercriminals.
To improve security postures inside corporate networks — which means protecting against both bad actors who penetrate perimeter defenses and malicious insiders — organizations must monitor, detect, and block hostile east-west (internal) traffic using internal firewalls.
To date, network and security professionals have generally viewed securing east-west traffic as too complex, expensive, and time-consuming for their brownfield, and even greenfield, data centers. At VMware, we agree with that perception: it’s certainly true for organizations trying to detect and prevent the lateral movement of attackers by employing traditional, appliance-based perimeter firewalls as internal firewalls.
There’s a Better Way to Secure the Data Center
Instead of awkwardly forcing appliance-based firewalls to serve as internal firewalls, organizations should employ a distributed, scale-out internal firewall specifically Continue reading
From Micro-segmentation to Internal Firewalling
The Evolution of VMware NSX Service-defined Firewall
Today, many people take micro-segmentation for granted. It’s incredible to recall that just a few years ago, VMware introduced micro-segmentation to support the concept of Zero Trust — a security model that does not automatically trust entities within the security perimeter. Fast forward to the present, and many people have embraced that concept and made it their own. Meanwhile, VMware has extended its solution for micro-segmentation into a full-blown internal firewall. Let’s step back in time and see how VMware progressed from the initial micro-segmentation use case to today’s powerful Service-defined Firewall, deployed by thousands of organizations.
Pioneering the Market for Micro-segmentation
Back in 2013, VMware pioneered micro-segmentation with the release of VMware NSX, the VMware network virtualization and security platform, which propelled VMware into the world of software-defined network and security virtualization. This initial release enabled customers to run a complete Layer 2-Layer 4 stack in software. The guiding philosophy was to make world-class security easy to operationalize.
Some customers used NSX for network segmentation: they created virtual security zones in software where they had previously used hardware. Other customers adopted NSX for micro-segmentation: they were now able to provide Continue reading
NSX Secures Physical Servers with Bare Metal Agents
Our last blog on how NSX secures physical servers provided background on why physical server security is crucial. We cover the percentage share of physical servers to all workloads in the data center and the specific roles physical servers still play. Today, physical servers by percentage are playing a decreasing role in the data center. However, it’s still a vital one, as we pointed out in our last blog on Securing Physical Servers with NSX Service-defined Firewall. In this blog, we will cover a primary way VMware NSX provides secure connectivity for physical servers using a bare metal agent. VMware NSX-T can now offer secure connectivity for Linux and Windows Server physical servers.
How NSX Distributed Firewall Protects Physical Servers
There are several ways in which NSX can provide security for physical servers. Our original article, Extending the Power of NSX to Bare Metal, outlines each of these methods.
- NSX Distributed Firewall (DFW) ingress rules for traffic from physical servers to virtual workloads
- NSX DFW egress rules for traffic from virtual workloads to physical servers
- The NSX Edge using centralized firewall rules to secure traffic between virtual and physical workloads
- Use NSX agents in Physical Servers

VMware NSX Continue reading
VMware NSX-T Service Insertion and Gigamon GigaVUE Cloud Suite
We are delighted that our valued partner, Gigamon, and it’s GigaVUE Cloud Suite has met the certification requirements for VMware NSX-T service insertion.
Service Insertion for NSX-T
The concept of service insertion is key for the NSX platform, enabling users to seamlessly add third party applications at various points throughout the network. Having a robust ecosystem of partners provides maximum flexibility for NSX-T, allowing customers to add partner functionality, tailored to their unique requirements without degrading performance elsewhere in the software-defined data center (SDDC). Partner applications are put through a rigorous certification process ensuring the highest level of interoperability and reliability.
With the certification, GigaVUE Cloud Suite is now interoperable with VMware’s NSX-T and vCenter Server through APIs for improved agility and reduced manual management tasks. Gigamon customers now have comprehensive application visibility across complex hybrid environments, including east-west traffic, at scale.

Learn more
Please join the VMware and Gigamon teams at a joint webinar, Illuminate Applications in VMware-based Clouds to Secure and Optimize, on June 30, 10 am PDT. Learn about NSX service insertion, Gigamon GigaVue, and the advantages and a demo of Gigamon next-generation network visibility solutions.
The post VMware NSX-T Service Insertion and Gigamon GigaVUE Continue reading
Seven Reasons Why Network Automation Is Important
Organizations today constantly seek greater agility and speed in their IT operations. They’re looking to seize market advantage by innovating with new technology and quickly responding to shifting market trends. Meanwhile, IT teams seek higher levels of simplicity and automation – and more efficient allocation of limited resources – in order to support these larger business goals.
Why Businesses Need Network Automation
A major roadblock many organizations face in the drive for efficiency is that their enterprise network is far more difficult to manage than ever before. Distributed workloads and distributed IT resources have led to extremely complex configurations and poor visibility across the environment. To make matters worse, much of the management work on these networks has traditionally been performed manually, via command-line entry. That’s proved to be tedious, costly, unnecessarily rigid, and prone to error.
Industry reports find as much as 40-80% of network failures are the result of human error
Network outages are of course a large pain point in enterprise networking, but there are certainly others. Complex, hard-to-manage networks are hindering business innovation, making critical security improvements more difficult, and driving up costs. This set of drawbacks has naturally led to a search for better Continue reading
Advancing from VMware NSX for vSphere to NSX-T
We introduced VMware NSX to the market over seven years ago. The platform has helped thousands of customers worldwide transform their network and bring the public cloud experience on-premises. This resulted in higher levels of automation and insight, which, in turn, saved time and money. However, as customers continued to drive new use cases and requirements, we wanted to ensure NSX was completely future-ready; hence NSX-T was born.
The Next Generation of NSX is NSX-T
NSX-T is the next generation of network virtualization and security platform with a complete L2-L7 suite of services, delivering switching, routing, firewalling, analytics, and load balancing entirely in software. Unlike NSX-V, NSX-T supports a variety of heterogeneous endpoints such as VMs, containers, and bare metal servers. The platform enables a wide range of use-cases in intrinsic security, networking and security for multi-cloud and modern apps, and network automation. The past few releases delivered many new networking and security innovations on NSX-T, prominent among these are the ultimate crown jewels of the platform – NSX Intelligence, Federation, and NSX Distributed IDS/IPS.
Migrating from NSX for vSphere to NSX-T is top of mind for customers that need to transition. Here are answers to some questions that you, Continue reading
VMware Announces Intent to Acquire Lastline
By Tom Gillis, SVP and GM, Networking and Security Business Unit, VMware
EDITORIAL UPDATE: On June 18, 2020 VMware officially closed its acquisition of Lastline. The blog post below has been amended to reflect that announcement.
VMware announced its intent to acquire Lastline, a pioneer in anti-malware research and AI-powered network detection and response, and on June 18, 2020 the acquisition closed. This is an important step forward for VMware’s vision of Intrinsic Security, as it allows us to further take advantage of the intrinsic attributes of our virtualization platform to yield innovative security capabilities. Our aim is not to replicate that which exists today, but rather to build security solutions that we can uniquely deliver, spanning from the heart of the data center to users in a branch office and all the way to mobile users at home or on the road.
In the security industry, the nature of threats changes so rapidly that security technology is constantly being re-invented. In this context, it is not the algorithms per se that matter; it is the people that make the algorithms. Great people build great products, and great products build great companies. And that’s why we are so Continue reading
How to Navigate NSX-T Policy APIs for Network Automation
According to the Gartner blog post, 2019 Network Resolution: Invest in Network Automation, the top network resolution of 2019 was network automation. This isn’t surprising since traditional automation of networking and security has always been a challenge due to the cumbersome processes, lack of governance, and limited or non-existent management tools.
Organizations that automate more than 70% of their network change activities will reduce the number of outages by at least 50% and deliver services to their business constituents 50% faster
VMware NSX-T Data Center solves this by enabling rapid provisioning of network and security resources with layered security and governance. By using various network automation tools, you can quickly and effectively keep up with the demands of your developers and application owners who expect a quick turnaround on resource requests. In this blog post we’ll look at how NSX-T Policy APIs simplifies network automation.
What Are NSX-T Policy APIs?
At the center of NSX network automation lies the single point of entry into NSX via REST APIs. Just like traditional REST APIs, NSX-T APIs support the following API verbs: GET, PATCH, POST, PUT, DELETE. The table below shows the usage:

A New API Object Model
Introduced in Continue reading
Secure Bare Metal Servers with VMware NSX Data Center
Securing workloads across an entire environment is the fundamental goal of a policy. But workloads come in a variety of form factors: virtual machines, containers, and bare metal servers. In order to protect every workload, experts recommend isolating workloads wherever possible — avoiding dependency on the host operating system and its firewall. Relying on the host firewall creates the dependency of a host to defend itself.
Securing virtual workloads is a task best handled by the hypervisor. Offering security via inspection of traffic on the virtual network interfaces of the virtual workload achieves the security you want. It also delivers isolation for security enforcement. Workloads to secure bare metal servers come in many form factors and a variety of means to achieve policy enforcement.

Bare Metal Servers Still Serve A Purpose
Bare metal servers remain in use for a variety of reasons. Securing these servers remains a necessary task in today’s virtualized data center. Reasons we still use bare metal servers:
- There may be no way to virtualize various operating systems, like AIX and Solaris.
- Device-specific systems, such as medical equipment, or systems specific to other virtual markets may not yet have been virtualized. In some cases they may not Continue reading
How to Use Migration Coordinator’s Automated Maintenance Mode
Migrate from VMware NSX for vSphere to NSX-T with Minimal Downtime
In order to help easily migrate from NSX for vSphere to NSX-T, with minimal downtime, the latest release of VMware NSX-T 3.0 introduces Maintenance Mode to NSX-T Migration Coordinator (a tool that has been built into NSX-T since the 2.4 release). The Migration Coordinator tool is designed to run in-place on the same hardware that is running NSX for vSphere, and swap out NSX for vSphere bits with NSX-T.
This blog post is a follow up to the previous blog, Migration from VMware NSX for vSphere to NSX-T, which covers Migration Coordinator. For more details on the Migration Process, please check out the previous blog. This blog focuses on the Maintenance Mode feature which is part of the NSX-T 3.0 release.
What is Migration Coordinator?
Migration Coordinator is a tool that runs on NSX-T Manager. Its disabled by default since migrating from NSX for vSphere to NSX should only be a one-time task.
How to Enable Migration Coordinator
To enable Migration Coordinator, simply log in to NSX Manager via SSH and run the command “start service migration-coordinator”.
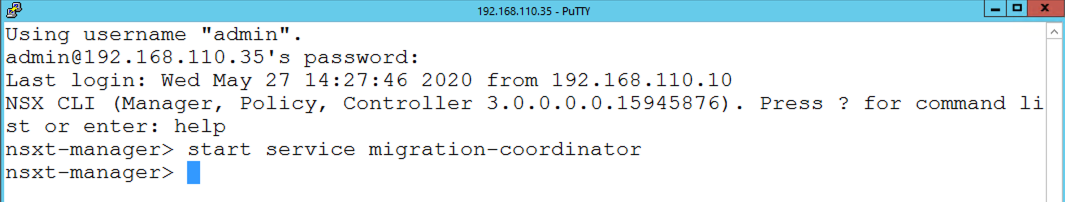
Note: This command is also Continue reading
Use Layer 7 Application Identity in Your Segmentation Policies
With the launch of VMware NSX in 2013, VMware pioneered micro-segmentation. Back then our solution was based on stateful Layer 4 filtering. We’ve added in dynamic grouping, enabling policies based on VM context such as VM Name, Operating System or Security Tags. Using dynamic grouping, the life cycle of a Service-defined Firewall policy is directly tied to the life cycle of the workloads/application it’s protecting. This is radically different from traditional firewalls which use IP-address based policies.
Another addition to our Service-defined firewall is Layer 7 Application Identity. You may be familiar with the concept from the perspective of a perimeter firewall where it can be used to allow access to Facebook chat but block access to Facebook games. The data center is different and so are the use cases for layer 7 Application Identity.
In this blog I will cover why organizations should use Layer 7 Application Identity in their data center segmentation policies.
What Are the Problems with Port-Based Rules?
While stateful Layer 4 firewalls have significantly reduced both the complexity and security gaps that come with configuring stateless Access Control Continue reading
Security Field Day #XFD3 with the VMware NSX Security Team

The Gestalt IT team is back with another exciting set of Field Day presentations. Multiple IT product vendors, including VMware, and independent thought leaders will share information and opinions in a presentation and discussion format. The complete VMware agenda and speaker lineup for the morning of the 14th is listed in detail below.
In summary, VMware’s focus for #XFD3 is why a new approach to security is required in the modern era. This security vision is present across all of the solutions, technologies, and bundles that we are bringing to the market. The VMware speakers, Dhruv, Stijn, Ray, and Ashish are planning to cover diverse topics ranging across Service-defined Firewall (SDFW), IDS/IPS, NSX Intelligence, DDoS, and WAF.
Video 2: Dhruv Continue reading
