VMware vForum Live is Coming to Toronto on 11/9 & Houston on 11/17!
Attention IT professionals – want to discover the benefits of network virtualization, mobility, and cloud? You can at VMware vForum Live! Join our experts in-person for an interactive, all-day event that will take you through technical deep dives of VMware solutions. Sign up today for vForum Live in Toronto on Nov 9th or sign up for vForum Live in Houston on Nov 17th now!
vForum Live is your chance to collaborate with peers, interact with VMware experts and receive actionable advice on how you can simplify your IT and deliver an effective cloud strategy. From keynote speeches presented by the industry’s heaviest hitters to specific VMware solution breakout sessions, you’ll get to hear the latest tips, tricks and insights. Plus, partake in our hands-on SociaLabs in the afternoon to get direct experience working with various solutions under the guidance of a VMware expert.
Here’s a list of VMware technical leaders and industry experts who will be presenting:
- Chris Wolf, VMware CTO of the Americas – “Delivering Tomorrow’s Agile, Secure and Open Solutions, Today”
- Kevin Mitnick, internationally-known Global White Hat Hacker – “Art of Deception: How Hackers and Con Artists Manipulate You and What You Can Do About It”
- Continue reading
Industry First Micro-segmentation Cybersecurity Benchmark Released
 The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
Testing included five different network design patterns, and demonstrated how NSX micro-segmentation can provide stateful, distributed, policy-based protection in environments regardless of network topology. Topologies included –
- Flat L2 network segments
- L2 and L3 networks with centralized virtual or physical routers, representative of typical data center rack implementations built on hybrid physical and network virtualization platform / distributed virtual switch (dVS)
- Networks with connection to other physical servers
- Overlay-based networks using the Distributed Firewalls (DFW) and Distributed Logical Routers (DLR)
- Physical VLAN and overlay-based networks using service insertion technologies running on dedicated VMs (in our case, Palo Alto Networks NextGen FW with Panorama)
Coalfire’s examination and testing of VMware NSX technology utilized simulated exploits that depict likely malware and Continue reading
Multi-site with Cross-VC NSX and Palo Alto Networks Security
In a prior post, Multi-site with Cross-VC NSX: Consistent Security and Micro-segmentation Across Sites, we discussed how Cross-VC NSX provides micro-segmentation and consistent security across multiple sites. We looked at five reasons to seriously consider Cross-VC NSX for a multi-site solution in terms of security alone: centralized management, consistent security across vCenter domains/sites, security policies follow the workload(s), ease of security automation across vCenter domains/sites, and enhanced disaster recovery use case. In this post, we’ll discuss how advanced third party security services can also be leveraged in a Cross-VC NSX environment.
Prior Cross-VC NSX Blogs:
Multi-site with Cross-VC NSX: Consistent Security and Micro-segmentation Across Sites
Cross-VC NSX: Multi-site Deployments with Ease and Flexibility
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
NSX provides a solid platform for security in general: inherent isolation via logical networks, micro-segmentation via distributed firewall, edge firewall capabilities, third party guest introspection services, third party network introspection services, and a robust security policy orchestration and automation framework.
With Cross-VC NSX, micro-segmentation and consistent security policies for workloads expands beyond a single vCenter boundary. Typically, customers who have multiple sites also have multiple vCenters – at least one vCenter Continue reading
Catch the Latest #VMworld 2016 Updates in Our NSX SociaLab
So you missed VMworld 2016…You can still hear about the latest VMware NSX updates in an NSX-focused SociaLab!
Sign up for an NSX SociaLab in your area now.
NSX is the network virtualization platform for the Software-Defined Data Center (SDDC). Bring your own device to this interactive hands-on lab event where our engineering experts will guide you step-by-step through the technical features, functions and business use cases of NSX that were released at VMworld 2016 – all while you test drive the solution for yourself.
During the event, you’ll get to partake in multiple Hands-On Labs featuring logical switching, dynamic routing, distributed firewall, logical network services, all of which were featured at VMworld 2016, and more. You’ll walk away from our SociaLab knowing how to:
- Create a logical switch and attach virtual machines to it
- Understand the routing capabilities supported in NSX and the benefit of performing them at the hypervisor layer
- Explore how the distributed firewall protects a 3-tier application and create rules based on security groups & identity
Now’s your chance to hear what you missed out on at VMworld to meet our technical experts, ask questions and collaborate with peers. Don’t miss this in-person opportunity to learn Continue reading
SDN Matures – via the Federal Government…
Based on industry research and market assessments such as the most recent from Allied Market Research, we know software-defined networking is growing crazy fast and has a huge upside. The question is…is it maturing to the point the Federal Government will make it a priority?
I think the answer is YES, based on what Lt. Gen. Alan Lynn, director of the Defense Information Systems Agency has said publicly. And, it appears cyber-security is one of the biggest areas he sees SDN helping out. He explains how SDN can provide the ability to create networks on-demand and make them harder to attack.
In order to help Lt. General Lynn, we needed to get past an issue I like to call, “Barrier of Implementation”. The barrier is an approved DISA STIG for SDN. In order for federal agencies to implement a SDN solution it has to go through some sort of security accreditation. Most of all security accreditation rely on DISA STIGs for the checks and balances.
With our announcement yesterday, “VMware Receives STIG-Approval for VMware NSX to Operate on U.S. Department of Defense Networks from Defense Information Systems Agency,” VMware NSX network virtualization became the Continue reading
How Jefferson County’s IT Department Improved Their Security Posture with VMware NSX
Jefferson County, Colorado (“Jeffco”) is a local jurisdiction located against the beautiful Rocky Mountains and adjacent to the state capital in Denver. Jeffco’s IT  organization is charged with meeting the needs not only of the various internal departments of the county, but also of serving its half million residents.
organization is charged with meeting the needs not only of the various internal departments of the county, but also of serving its half million residents.
As with most IT departments, Jeffco’s IT team has some key priorities to address, including modernizing application infrastructures and bringing more efficiency to business processes — all while fundamentally enhancing security. It was these needs that led Jeffco to VMware NSX. “We’re doing as much as we can to simplify our infrastructure, yet provide more security, higher up time, and better performance,” says Matt Alexander, Senior Systems Administrator.
Like many other organizations, Jeffco first considered VMware NSX for micro-segmentation. Their network had followed the traditional model of data center security: perimeter firewalls, DMZ, internal security zone. But this legacy security model wasn’t enough. Jeffco recognized the need to treat all network traffic — regardless of whether it originated inside or outside the data center — as potentially insecure. “From a micro-segmentation and east-west firewalling perspective, we may have had the ability [in the past] but it was exceptionally expensive with physical Continue reading
Multi-site with Cross-VC NSX: Consistent Security and Micro-segmentation Across Sites
Several posts have been written prior on multi-site with Cross-VC NSX describing the fundamentals, use cases, deployment models, and flexibility Cross-VC NSX provides. In this post, we focus on the security benefits of a multi-site Cross-VC NSX solution.
Prior Cross-VC NSX Blogs:
Cross-VC NSX: Multi-site Deployments with Ease and Flexibility
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
So, why multi-site with Cross-VC NSX? The following five reasons should be enough for you to seriously consider Cross-VC NSX as a solution for your multi-site needs:
1.) Centralized Management
Centralized management of security policies across multiple vCenter domains/sites. You have one central location to configure security policies and only write the security policy once, which is then applied across all vCenter domains/sites.
2.) Consistent Security Across vCenter Domains/Sites
Consistent security policies across vCenter domains/sites provided automatically by Cross-VC NSX enables enhanced workload mobility. Security policies are configured on the primary NSX Manager and automatically synced to the secondary NSX Managers providing for uniform security across all sites.

Figure 2 Consistent Security Across Sites Continue reading
Micro-segmentation Benchmark – NSX Securing “Anywhere” Part VI
Welcome to part 6 of the Micro-segmentation Defined– NSX Securing “Anywhere” blog series. Previous topics covered in this series include
• Part I – Micro-segmentation Defined
• Part II – Securing Physical Environments
• Part III – Operationalizing Micro-segmentation
• Part IV – Service Insertion
• Part V – Context, Visibility, and Containment
Previous posts set the stage by introducing and defining the characteristics of micro-segmentation; showing how it has utility in the modern data center; how we might apply it to our existing software-defined and physical networks; how policy-driven NSX management may be used to deliver comprehensive security; and, that we can use physical and virtual third-party security appliances in conjunction with NSX to create a service chain and apply special processing to our vital network flows.
In this sixth part of the NSX Securing “Anywhere” blog, Chris Krueger of Coalfire Systems will preview some of our work in comprehensively benchmarking VMware NSX micro-segmentation. The Micro-segmentation Benchmark is a project being delivered by Coalfire Systems, Inc. an internationally recognized third party audit organization (3PAO) and leading provider of IT advisory services for security in retail, payments, healthcare, financial services, higher education, hospitality, government,and utilities. Coalfire has Continue reading
How Virtualization Will Transform Security Architectures: Spotlight at #VMworld U.S. 2016
It’s clear today that security is at a crossroads, and we are losing the cybersecurity war. VMware’s SVP of Security Products Tom Corn explained to me recently, “There are no objective measures we can credibly point to which suggest we are – in any way – succeeding as we battle to protect systems and data.”
Register for this VMworld 2016 session to learn about the transformation of security architecture
One of the biggest problems, he points out, is that Cyberwarfare is an asymmetric battle: an attacker fires a thousand bullets and only one needs to get thru. Defenders need to stop all 1,000. So what are we doing to address this challenge?
We don’t appear to have an issue with how much we spend, or that there is a lack of security innovation. We are spending at record levels, and security innovation is at an all time high.
At the heart of the issue is an architectural gap – between the applications and data we are trying to protect, and the infrastructure from which we are trying to protect them. Virtualization could be the key to solving this problem — enabling security to be architected-in, rather than bolted on. Continue reading
Context, Visibility and Containment – NSX Securing “Anywhere” Part V
 Welcome to part 5 of the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Previous topics covered in this series includes
Welcome to part 5 of the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Previous topics covered in this series includes
- Part I – Micro-segmentation Defined
- Part II – Securing Physical Environments
- Part III – Operationalizing Micro-segmentation
- Part IV – Service Insertion
In this post we describe how NSX micro-segmentation enables fundamental changes to security architectures which in turn facilitate the identification of breaches:
- By increasing visibility throughout the SDDC, eliminating all blind spots
- By making it feasible and simple to migrate to a whitelisting / least privileges / zero-trust security model
- By providing rich contextual events and eliminating false positives to SIEMs
- By providing inherent containment even for Zero Day attacks
Threat analysis is the new trend of the security landscape and established vendors as well as startups are proposing many tools to complement the current perimeter logging approach. The attraction for these tools is based on the assumption that by correlating flows from different sources within a perimeter, threat contexts will emerge and compromised systems will be uncovered. Currently, these systems go unnoticed for long periods of times because the suspicious traffic moves laterally inside the perimeter and does not traverse a security device: you can’t Continue reading
VMware NSX Breakout Session Guide – Introductory, Intermediate, Advanced #VMworld 2016
The VMware NSX network virtualization platform is bringing game-changing capabilities and benefits to businesses and organizations across a wide spectrum of industries. We have sessions covering strategic initiatives like security, automation, and application continuity, as well as more tactical use cases like micro-segmentation, IT automating IT, disaster recovery, and more. On top of that, there are sessions covering the NSX platform and operationalizing NSX. These sessions are offered in a variety of formats and range from introductory sessions perfect for those new to NSX or network virtualization, to intermediate sessions that dive into the deeper technical aspects of NSX, to advanced sessions for NSX veterans and networking experts.
And I know you’ve heard me say this before…but take a look at the list of the breakout sessions below, and then check out the schedule builder on VMworld.com to organize your week.
We’re looking forward to seeing you at VMworld US 2016.
Monday, August 29
| Time | Level | Session ID | Session Title |
| 12:30 PM – 1:30 PM | Introductory | NET7834 | Introduction to VMware NSX |
| 12:30 PM – 1:30 PM | Introductory | NET8675 | The Practical Path to NSX |
| 2:00 PM – 3:00 PM | Introductory | SEC7836 | Introduction to Security with VMware NSX |
| 3:30 PM Continue reading |
VMware NSX Technology Partner Ecosystem Session Guide #VMworld 2016
Looking to learn more about how VMware is collaborating with industry leaders and emerging startups to solve customer problems around a range of strategic initiatives and use cases? We have sessions covering strategic initiatives like security, automation, and application continuity, as well as more tactical use cases like micro-segmentation, IT automating IT, disaster recovery, and more. Our rich partner ecosystem is continuing to grow, and our partners will highlight the benefits of their integrated offerings.
Browse the list of the partner sessions below, and then check out the schedule builder on VMworld.com to organize your week. We’re looking forward to seeing you at VMworld US 2016.
Monday, August 29
| Time | Partner | Session ID | Session Title |
| 12:30 PM | VMware | NET7834 | Technical Partner Overview: Intro to VMware NSX |
| 1:00 PM – 2:00 PM | Brocade | NET9460-SPO | Use Cases for Software-Defined Data Center with NSX: Transform to Digital Business by Deploying Multi-tenant Agile Network in SDDC Environment |
| 1:00 PM – 2:00 PM | Netscout | NET9973-SPO | Accelerating Digital Transformation in Software-Defined Environments |
| 2:30 PM – 3:30 PM | HPE | NET7656-SPO | Accelerating SDDC Through Mainstream Adoption of Network Virtualization |
| 4:00 PM – 5:00 PM | Palo Alto Networks | SEC9972-SPO | Deep Dive: Secure your Multi-tenant Cloud with Palo Alto Continue reading |
VMware NSX Customer Session Guide – #VMworld 2016
Considering rounding out your adoption of the three pillars of the Software-Defined Data Center with network virtualization? Want to see how others have done it? We have more than three dozen unique customers eager to share their experiences about how VMware NSX gave them the power to virtualize their networks and take their operations and businesses to new heights.
We have a range of engaging session formats, from short quick talks to customer discussion panels to customer breakout sessions, to help you see and hear how a wide variety of organizations have put VMware NSX to work for them.
So take a look at the list of the customer sessions below, and then check out the schedule builder on VMworld.com to organize your week. We’re looking forward to seeing you at VMworld US 2016.
Sunday, August 28
| Time | Type | Session ID | Session Title |
| 1:00 PM – 1:30 PM | Quick Talk | NET9382-QT | A Software-Defined Data Center in Overseas Bases and Military Operations |
| 2:00 PM – 2:30 PM | Quick Talk | NET8769-QT | Hyper-convergence in Healthcare: The Key to Doing More with Less |
| 3:00 PM – 3:30 PM | Quick Talk | NET9004-QT | Virtually Unstoppable: Scaling NSX to Bridge the Gap between Security & Cloud Continue reading |
VMware NSX is the Networking Bridge to a Multi-Cloud Future
Across industries, the race is on to digital transformation. It’s all about business innovation and redefinition. The transformations are huge: Tesla isn’t just a car manufacturer; it’s a software business that makes cars. CITI is a software business that makes loans. GE is a software business that makes industrial equipment.
Register for this VMworld 2016 session to learn about the future of VMware NSX
Like most of the customers we talk with, your business is also going through a transformation. Lots of change. Lots of disruption. Lots of innovation. More apps, representing more services and new business models. More lines of business empowered to make decisions about the IT they’ll use to take their innovations to market. And there’s no doubt that a huge enabler of all of this has been the cloud.
Consider what some of the leading industry pundits are predicting:
- By 2019, the majority of virtual machines (VMs) will be delivered by IaaS providers.
- By 2019, more than 30% of the 100 largest vendors’ new software investments will have shifted from cloud-first to cloud-only.
- By 2020, a corporate “no-cloud” policy will be as rare as a “no-internet” policy is today
- By 2020, 50% of applications running Continue reading
Cross-VC NSX: Multi-site Deployments with Ease and Flexibility
As discussed in prior Cross-VC NSX/multi-site blogs, Cross-VC NSX allows for NSX logical networking and security across multiple vCenter domains which may also be across multiple sites. The benefits of this capability are immediately clear in terms of workload mobility, resource pooling, central management and application of consistent security policies across vCenter domains/sites, and disaster recovery. More details on these use cases can be found in the prior Cross-VC NSX blogs listed below or in the recently published NSX-V: Multi-site Options and Cross-VC NSX Design Guide. This blog post, focuses on the ease and flexibility in terms of application of Cross-VC NSX for multi-site.
Prior Cross-VC NSX Blogs:
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
In this example, vCenter, the primary NSX Manager, and the Universal Controller Cluster (UCC) is deployed at site 1. A secondary NSX Manager which is registered with the primary NSX Manager is deployed at site 2 along with its corresponding vCenter. For a quick overview on primary NSM Manager, secondary NSX Manager, and the UCC see this prior blog. For more detailed information, see the NSX-V: Multi-site Options and Cross-VC NSX Continue reading
Securing the SDDC with VMware NSX – Light Board Series
Is VMware the first company that springs to mind when you think about securing your software-defined data center (SDDC)? It should be.
In this new light board series, learn about the unique capabilities that VMware NSX brings to your SDDC for securing your virtualized environment.
Start out with some context on why networking and security go hand-in hand with the Network Virtualization is Inevitable video. Then, move on to the NSX as a Security Platform video, to learn why VMware can offer security options not possible in tradition environments.
But how to install NSX in an environment? Check out Hadar Freehling’s Castle Security with VMware NSX video. Curious about why the firewall in NSX is special? Watch the VMware NSX Distributed Firewall video. And finally, secure a VDI environment with Hadar’s VMware NSX and VDI video.
As your SDDC evolves, stay up-to-date with NSX and how it can help secure your assets. Any burning questions on securing your virtualized environment you don’t see addressed in the videos, and want to see? Let us know; and don’t be surprised if you see it addressed in a future video.
Julie
The post Securing the SDDC with VMware NSX – Light Board Series Continue reading
Micro-segmentation with Service Insertion – NSX Securing “Anywhere” Part IV
 Welcome to part 4 in the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Today we will cover the role of NSX as a foundational security platform through NSX Micro-segmentation with Service Insertion. Previous topics covered in this series includes
Welcome to part 4 in the Micro-Segmentation Defined– NSX Securing “Anywhere” blog series. Today we will cover the role of NSX as a foundational security platform through NSX Micro-segmentation with Service Insertion. Previous topics covered in this series includes
- Part I – Micro-segmentation Defined
- Part II – Securing Physical environments
- Part III –Operationalizing Micro-segmentation
This blog covers the following topics:
- Defining Service Insertion
- The Role of Service Insertion in Micro-segmentation
- Network and Guest Introspection
- NSX Service Insertion
Defining Service Insertion
In modern datacenters, network and compute services either have been or are being decoupled from the physical appliances on which they have traditionally run. In the past, a datacenter service required traffic to be steered through a series of such appliances in order to be serviced appropriately, through services such as firewalls, intrusion detection and prevention, and load balancing services. As infrastructure services transition from physical appliances to software functions, it becomes possible to deploy these services with greater granularity by inserting them into a specific forwarding path. Combining multiple functions in this manner is generally referred to as a service chain or service graph.
 Figure 1: Two distinct service chains utilizing different functions
Figure 1: Two distinct service chains utilizing different functions
Once infrastructure Continue reading
Operationalizing Micro-segmentation – NSX Securing “Anywhere” – Part III
 Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
This blog covers the following topics:
- Micro-segmentation design patterns
- Determining appropriate security groups and policies
- Deploying micro-segmentation
- Application lifecycle management with vRealize Automation and NSX
- Day 2 operations for micro-segmentation
Micro-segmentation design patterns
Micro-segmentation can be implemented based on various design patterns reflecting specific requirements. The NSX Distributed Firewall (DFW) can be used to provide controlled communication between workloads independent of their network connectivity. These workloads can, for example, all connect to a single VLAN. Distributed logical switches and routers can be leveraged to provide isolation or segmentation between different environments or application tiers, regardless of the underlying physical network, as well as many other benefits. Furthermore, the NSX Edge Service Gateway (ESG) can provide additional functionality such as NAT or load balancing and the NSX Service Insertion framework enables partner services such as L7 firewalling, agent-less anti-virus or IPS/IDS applied to workloads that need additional security controls.
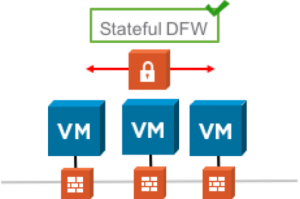
Figure 1: Leveraging the DFW to provide Continue reading
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Check-out the new NSX-V Multi-site Options and Cross-VC NSX Design Guide
The goal of this design guide is to outline several NSX solutions available for multi-site data center connectivity before digging deeper into the details of the Cross-VC NSX multi-site solution. Learn how Cross-VC NSX enables logical networking and security across multiple vCenter domains/sites and how it provides enhanced solutions for specific use cases. No longer is logical networking and security constrained to a single vCenter domain. Cross-VC NSX use cases, architecture, functionality, design, and failure/recovery scenarios are discussed in detail.
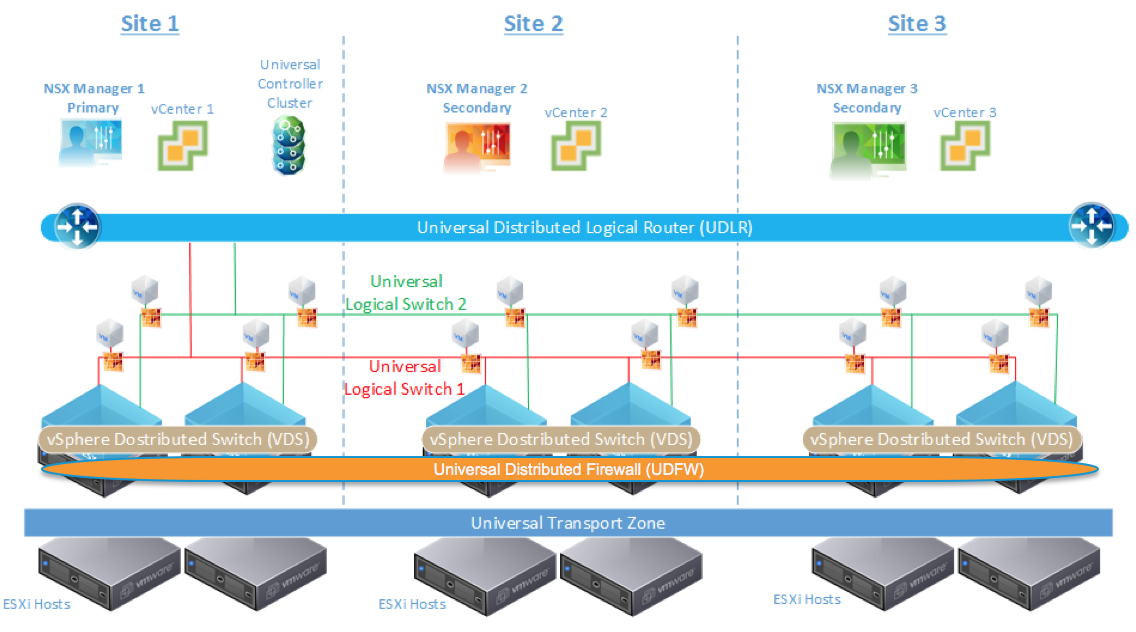
Cross-VC NSX: Logical Networking and Security Across vCenter Domains and Sites
Outlined briefly below are several important use cases that Cross-VC NSX enables in regards to Application Continuity. For additional details on Cross-VC NSX and multi-site data center solutions see the NSX-V Multi-site Options and Cross-VC NSX Design Guide.
Use Case 1: Workload Mobility
Since logical networking and security can span multiple vCenter domains and multiple sites, Cross-VC NSX allows for enhanced workload mobility which can not only span multiple sites but also multiple vCenter domains across Active-Active data centers. Workloads can now move between vCenter domains/sites on demand for tasks such as data center migration, data center Continue reading
OpenStack + VMware Light Board Series
Still confused on how VMware software works with OpenStack? This lightboard series on VMware + OpenStack is just what you need. From basic 101 level content to deeper dives discussing NSX integration, these videos will help you understand how VMware technologies can enhance and stabilize an OpenStack deployment.
If you are fairly new to the OpenStack and not new to VMware, I would suggest starting with these first three videos to help level set on OpenStack as a technology decision
- Why OpenStack?
- OpenStack Architecture & Stability
- VMware vRealize and OpenStack: A Side By Side Look
If you want to get a more in-depth understanding of how vSphere, NSX, and vSphere datastores work in the context of OpenStack, here is the playlist
- OpenStack and NSX
- OpenStack and vSphere
- OpenStack Storage & VMware Integrated OpenStack
- Getting ready to deploy VMware Integrated OpenStack
We’re working on quite a few more videos so if you have ideas for concepts you want to learn, please reach out to your VMware account team and they can forward on the request!
Also here are some more helpful resources to get you started on the path to deploying a VMware-based OpenStack Software-Defined Data Center:
- Test Drive Continue reading

