Tanzu Service Mesh Acceleration using eBPF
Performance and Security Optimizations on Intel Xeon Scalable Processors – Part 1
Contributors
Manish Chugtu — VMware
Ramesh Masavarapu, Saidulu Aldas, Sakari Poussa, Tarun Viswanathan — Intel
Introduction
VMware Tanzu Service Mesh built on open source Istio, provides advanced, end-to-end connectivity, security, and insights for modern applications—across application end-users, microservices, APIs, and data—enabling compliance with Service Level Objectives (SLOs) and data protection and privacy regulations.
Service Mesh architecture pattern solves many problems, which are well known and extensively documented – so we won’t be talking about those in this blog. But it also comes with its own challenges and some of the top focus areas that we will discuss in this series of blogs are around:
- Performance
- Security
Intel and VMware have been working together to optimize and accelerate the microservices middleware and infrastructure with software and hardware to ensure developers have the best-in-class performance and low latency experience when building distributed workloads with a focus on improving the performance, crypto accelerations, and making it more secure.
In Part 1 of this blog series, we will talk about one such performance challenge (with respect to service mesh data path performance) and discuss our solution around that.
The current implementation Continue reading
Announcing VMware HCX 4.4
VMware HCX continues to evolve with the release of HCX 4.4 which includes several key enhancements in multiple different areas. These enhancements are going to address new requirements, stabilize the current feature set and provide additional security. This blog aims to highlight the major changes in HCX 4.4.
Transport AnalyticsFollowing the release of HCX 4.1, the HCX team undertook an effort to better understand how various aspects of a network underlay (including bandwidth, packet loss and latency conditions) affect migration outcomes. We called this effort the Network Underlay Characterization for HCX. During the 4.2 release, the characterization exercise enabled us to officially support services over VPN/SD-WAN, along with the Network Underlay minimum requirements to support any underlay agnostically. We also published detailed tech paper (See Network Underlay Requirements and HCX Performance Outcomes). This document guides the reader through the characterization exercise (manually using command line tooling). HCX 4.4 adds Transport Analytics the HCX, allowing the user to execute performance baselining for the HCX service transport on-demand and visualizes transport performance in real-time and as time-series graphs. This enables the migration administrator to understand the network underlay conditions reflected in the transport and plan Continue reading |
10 Reasons Why Customers Choose VMware NSX to Automate Networking and Security
By now, you’ve probably heard about why you should automate network management. Not only does automation save time and effort, but it also reduces risk. As Gartner notes, for instance, organizations that automate about 70 percent of their network change management operations will see a 50 percent reduction in outages. They’ll also cut in half the time it takes to roll out new services.
The bigger question many teams face surrounding network automation, however, is how to automate. With so many tools on the market that promise to help automate networking and security, which solution is the best fit for your needs? What should you look for from an automation lens when considering a networking platform?
To provide clarity on those questions, we’ve put together a list of the reasons why customers choose VMware NSX in order to deploy applications at scale with greater speed, efficiency, and security. VMware NSX, the platform for network virtualization, provides instant and programmatic provisioning for fast, highly available, and secure infrastructure. The automation capabilities of NSX listed below maximize time savings and minimize risk when managing distributed, multi-cloud environments. Continue reading
Navigating NSX Module in PowerCLI 12.6
With the release of PowerCLI 12.6, a new module VMware.Sdk.Nsx.Policy was added to provide PowerShell binding for NSX Policy Manager APIs. This new module is auto generated from the NSX Policy API spec exposing all the features related to policy objects in NSX. The module also exposes cmdlets to Create/Edit/Delete NSX objects. This blog explains the use of PowerCLI NSX module, goes through all the different ways new cmdlets can be found and shows how to view documentation on the cmdlets with examples.
Navigating the new cmdlets
Along with the cmdlets to connect, disconnect and modify the NSX objects, there are a few helper cmdlets that make looking up new relevant cmdlets very easy.
The first one is Get-NsxOperation. This is a new feature in VMware.Sdk.Nsx.Policy and is ideal with you need to find the PowerCLI command that corresponds to an API operation and vice versa. You can also narrow down the search result using Where-Object and Select-Object filters.
Example:
Get-NsxOperation -Method GET -Path '/infra/segments'
Since the cmdlets by default returns all paths that start with /infra/segments you can also limit the search to exact match with client-side filter:
Get-NsxOperation -Method get Continue reading
NSX-T 3.2.1: Rolling Upgrade for NSX Management Plane
VMware NSX 3.2.1 continues to deliver enhancements for improving the VMware NSX upgrade process, including rolling upgrades that shorten upgrade maintenance windows and improved visibility into the NSX upgrade progress.
During the upgrade, the management plane will always be available, normal operation, ie, API calls, configuration changes, adding and removing Transport Nodes can be performed. If there’s an issue that occurred during the upgrade, users can roll back to the previous release without deploying a new NSX cluster and restoring the backup. The rolling upgrade feature applies to only the NSX Manager upgrade portion of the upgrade. In other words, the sequence of the NSX components upgrade remains in the following order: NSX Upgrade Coordinator upgrade, NSX Edge upgrade, Host upgrade, then the NSX Manager upgrade.
How Rolling Upgrade works
Prior to NSX 3.2.1 release, we upgrade all the manager nodes in the management cluster simultaneously. The advantage of the parallel upgrade is that it takes less time to upgrade the management plane. The tradeoff is that the management plane will not be available for a period during the upgrade process. With the rolling upgrade, the manager nodes will be upgraded sequentially. During the management upgrade Continue reading
Migrate from Cross-VC to Federation using NSX-T Migration Coordinator
NSX-T 3.2.1
With the VMware NSX-T 3.2.1 release, Migration Coordinator adds one more game changing feature: migrating from multisite NSX for vSphere deployments directly to NSX Federation. This feature builds on top of the User Defined Topology mode of migration. Folks familiar with the User Defined Topology will find the workflow similar and following the same simple model.
In this blog post, we will look at this new feature and how to leverage it. Please check out the resource links for more information on Migration Coordinator. Here, we will start with a high-level overview before digging into the details.
Migration Coordinator
Migration Coordinator is a tool that was introduced around 3 years ago, with NSX-T 2.4, to enable customers to migrate from NSX for vSphere to NSX-T. It is a free fully supported tool that is built into NSX-T. Migration Coordinator is flexible with multiple options enabling multiple ways to migrate based on customer requirements.
With the NSX-T 3.2 release, Migration Coordinator offered three primary modes for migration:
- Migrate Everything: From edges, to compute, to workloads — in an automated fashion and with a workflow that is like an in-place upgrade on existing hardware. This mode only needs enough resources to host NSX-T manager appliances and edges along Continue reading
Business Agility and Continuity with NSX Federation and Traceflow
Resilient application architectures have evolved quite significantly over the years. It is increasingly more common for Enterprises to deploy multiple data centers to support flexible workload placement and redundancy to achieve application and network high availability.
Here, we discuss key reasons to deploy multiple data centers and how NSX Federation and the recently introduced traceflow support simplify associated infrastructure strategy and implementation.
Workload Placement and Mobility
Applications and the associated infrastructure (compute, storage, networking, and security) are deployed in multiple locations to support workload mobility between these locations for use cases such as Data Center migration and Disaster Recovery testing.

Figure: Multi-Cloud Mobility
Data Center Expansion
In this scenario, IT runs out of capacity at a location (rack, building, site) and wants additional capacity at a different location for hosting new applications. Capacity can be of different types such as compute (servers), and/or storage, and/or network (bandwidth).
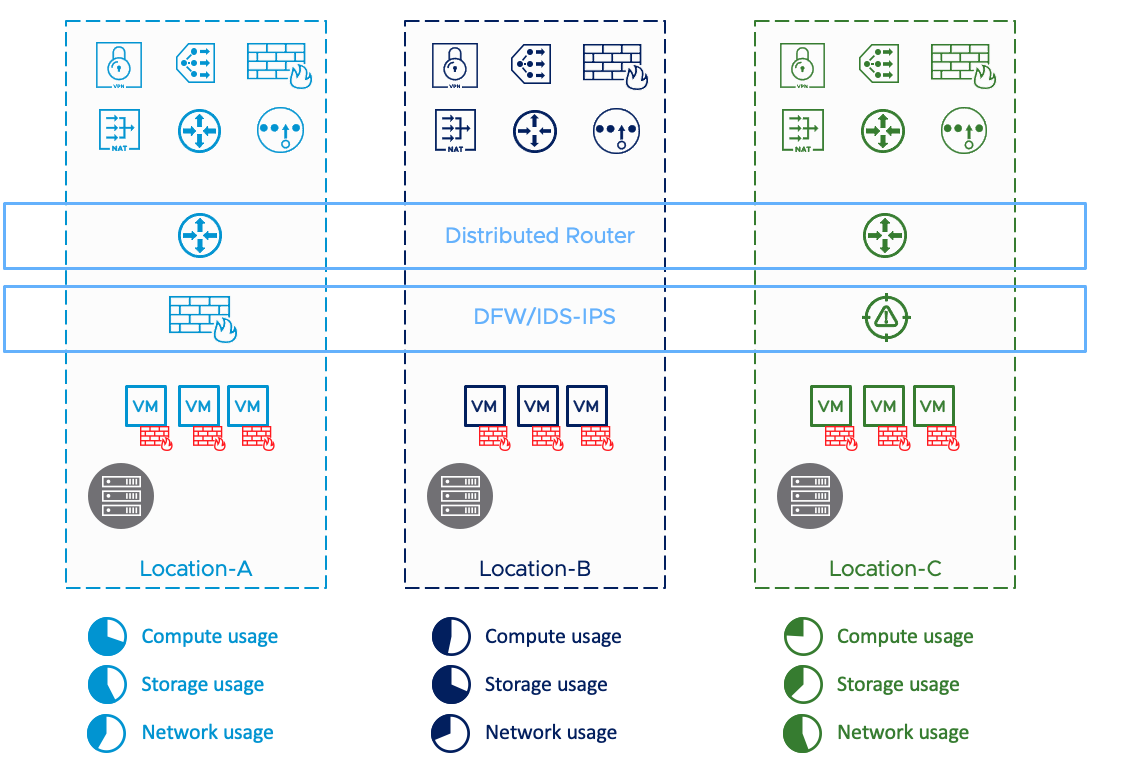
Figure: Multi-Cloud Growth
Disaster Avoidance / Disaster Recovery
This is a scenario where you lose one of your locations completely (rack, building, site) and you need to maintain the availability of your application services (compute, storage, network and security).

Figure: Multi-Location DR
Simplifying Deployment and Operations with NSX Federation
Tips for Putting Zero Trust into Practice in Kubernetes-Based Environments
If you work in IT, you’ve probably heard lots of talk in recent years about “zero trust,” a security strategy that requires all resources to be authenticated and authorized before they interact with other resources, rather than being trusted by default.
The theory behind zero trust is easy enough to understand. Where matters tend to get tough, however, is actually implementing zero-trust security and compliance, especially in complex, cloud-native environments.
Which tools are available to help you enforce zero-trust security configurations? What does zero trust look like at different layers of your stack – nodes, networks, APIs and so on? What does it mean to enforce zero trust for human users, as compared to machine users?
To answer questions like these, we’ve organized a webinar, titled “Zero Trust Security and Compliance for Modern Apps on Multi-Cloud,” that will offer practical guidance on configuring a zero-trust security posture in the real world.
The one-hour session will focus in particular on enforcing zero-trust in Kubernetes-based environments, with deep dives into the following:
- How to protect human and machine users in Kubernetes using a zero-trust model.
- Meeting Kubernetes data privacy and compliance requirements through zero trust.
- Securing user-to-app communications with zero-trust networking policies Continue reading
VMware named a Leader in Cloud Networking in GigaOm Radar Report
We’re delighted to report that GigaOm, a global provider of technology industry insights and analysis, has placed VMware in the leader ring in the GigaOm Radar Report for Cloud Networking 2022. In the leader ring, VMware is placed in the Platform Play and Maturity quadrant. This is a testament to the robustness of VMware’s cloud networking solution and its leading position in the cloud networking space. Click here to download the complete report.

Noting VMware’s broad portfolio of networking solutions, which covers the entire network stack and includes native network features for observability, micro-segmentation, and beyond, GigaOm says that VMware is in a leading position to help enterprises with complex networking requirements “modernize and optimize their infrastructure.”
Cloud Network Evaluation Criteria
The report evaluates 11 vendors that provide tools or platforms to help build and operate cloud networks. They include major enterprises like VMware, as well as several smaller companies.
GigaOm assessed the vendors on a variety of criteria, including:
- Network traffic security and micro-segmentation.
- Observability.
- Troubleshooting and diagnostics.
- Optimization and autoscaling.
- APIs and IaC integration.
- Application-aware infrastructure.
- Solution management.
VMware received a triple-plus score – the highest evaluation possible – for most of the categories given above.
Continue reading
Multi-Tenancy Datacenter with NSX EVPN
The data center landscape has radically evolved over the last decade thanks to virtualization.
Before Network Virtualization Overlay (NVO), data centers were limited to 4096 broadcast domains which could be problematic for large data centers to support a multi-tenancy architecture.
Virtual Extensible LAN (VXLAN) has emerged as one of the most popular network virtualization overlay technologies and has been created to address the scalability issue outlined above.
When VXLAN is used without MP-BGP, it uses a flood and learns behavior to map end-host location and identity. The VXLAN tunneling protocol encapsulates a frame into an IP packet (with a UDP header) and therefore can leverage Equal Cost Multi-Path (ECMP) on the underlay fabric to distribute the traffic between VXLAN Tunneling Endpoints (VTEP).
Multi-Protocol BGP (MP-BGP) Ethernet VPN (EVPN) allows prefixes and mac addresses to be advertised in a data center fabric as it eliminates the flood and learns the behavior of the VXLAN protocol while VXLAN is still being used as an encapsulation mechanism to differentiate the traffic between the tenants or broadcast domains.
A Multi-Tenancy infrastructure allows multiple tenants to share the same computing and networking resources within a data center. As the physical infrastructure is shared, the physical Continue reading
A New One-Stop Shop for Network Security Topics
Your trusty NSX blog is going through a big change.
We’re uniting our VMware security content in the newly designed VMware Security blog.
Don’t worry, you’ll still be able to find the latest on network automation, application mobility, and load balancing. All the networking content you count on, that’s staying right here.
However, if you’re looking for current and future articles on network security and threat research, those will now be found in a new home—a blog that centralizes security content across VMware into a single channel.
You no longer need to switch (blog) channels for security news, insights, and resources. The newly designed VMware Security Blog will become your new one-stop-shop for key perspectives from experts, specialists, and leaders across VMware NSX, Threat Analysis Unit, and Carbon Black.
On the new blog, you can expect to find all the network security content you know and love — including:
- Important insights and announcements regarding threat research, endpoint security, and network security
- Key analysis of recent ransomware attacks, insights on techniques deployed, and how threats can be detected and mitigated
- Infographics, data points, and award recognition illustrating the strength of VMware security solutions
- Invites Continue reading
10 Reasons to Implement Network Automation – Low Effort, High Impact
In 2022, nearly 77% of technology professionals see the need for improvement in their data center network automation strategies. Despite years of predictions about applications and data migrating to the public cloud, a consensus has been that data centers remain the indispensable core of any digital infrastructure. While the public cloud has a vital role to play and it continues to grow, enterprises and service providers continue to rely on data centers to power their operations. To remain relevant in a cloud-centric world, data centers must modernize – needing scalable, efficient, and agile operations. Highly manual processes do not scale gracefully, therefore calling for organizations and their data centers to adopt network automation or be left behind.
VMware is proud to have an opportunity to sponsor Enterprise Management Associates (EMA) in producing The Future of Data Center Network Automation research report. This report analyzes cutting-edge technology of data center automation – drawing on quantitative and qualitative research done by EMA analysts – focusing on how tech orgs are planning, implementing, and using data center network automation solutions, the specific technologies they’re using, and the benefits and challenges associated with data center network automation. Using real-time VMware customers Continue reading
#VMwareNSXChat Recap: NSX-T 3.2
In our most recent Twitter chat, we were joined by Vivek Bhandari, Varun Santosh, and Srini Nimmagadda to answer common questions about NSX-T 3.2, its benefits, how it works, and more. Dive in below for the full recap of our NSX-T 3.2 #VMwareNSXChat.
Question 1: If you had to describe NSX-T 3.2 to a friend using just one sentence (or using just 280 characters) what would you say? #VMwareNSXChat
Varun: Stronger security, simplified networking, easy operations – what’s not to like #VMwareNSXchat!
Vivek: It’s like going from a flip phone to a touch screen smartphone. Gamechanger! #VMwareNSXChat
Question 2: What are the key Networking and Policy enhancements? #VMwareNSXChat
Varun: NSX-T 3.2 simplifies network provisioning thru prescriptive NSX deployment from vCenter, deeper integration with Antrea, Federation support for VM tag replication, enhanced migration coordinator, and enhanced monitoring and troubleshooting. #VMwareNSXChat
Question 3: What are the key security enhancements? #VMwareNSXChat
Vivek: NSX-T 3.2 is a quantum leap forward bringing advanced security in a distributed architecture. It now includes network traffic analysis (NTA) and network detection and response (NDR), malware prevention with sandboxing, L7 gateway firewall, and more. #VMwareNSXChat
Vivek: Of Continue reading
Micro-segmentation and Beyond with NSX Firewall
VMware-based workload environments are the norm in private clouds for enterprise-class customers. 100%[1] of Fortune 500 companies deploy vSphere/ESXi. Further, ~99% of Fortune 1000 and ~98%[2] of Forbes Global 2000 companies deploy vSphere/ESXi. VMware’s deep presence in enterprise private clouds has made NSX Firewall the preferred micro-segmentation solution for these enterprises.
Below, we expand on how the NSX Firewall has developed its prominent position in enterprise private clouds.
Agentless and Agent-based Operation
Virtualized x86 workloads on hypervisors represent ~80%[3] of all enterprise workloads. VMware’s hypervisor-based micro-segmentation solution – NSX Firewall – is the preferred agentless solution for such workloads because of the solution’s tight integration with the rest of the VMware eco-system.
~15% of workloads at enterprises are x86-based (Windows, Linux) but not virtualized. The NSX Firewall handles these workloads with NSX agents.
~5% of workloads at enterprises are non-x86-based. VMware provides an (agentless) layer 2-7 gateway firewall that supports micro-segmentation for these workloads. Note that the gateway firewall eliminates the need for integration with physical switches, routers, and load-balancers.
Between these mechanisms, 100% of all workloads in the private cloud are protected. In practice, given VMware’s penetration of enterprises, VMware’s agentless solutions apply to the vast Continue reading
Hermetic Malware: Multi-component Threat Targeting Ukraine Organizations
Contributors: Giovanni Vigna, Oleg Boyarchuk, Stefano Ortolani
Introduction
The continued assault on Ukraine will go down in history as the first one that was truly carried out both kinetically on the battlefield and virtually using cyberattacks against the computer infrastructure of the invaded nation.
As the invasion started and escalated, new malware threats were introduced by malicious actors to harm Ukrainian organizations. Early in the assault, security researchers have observed the emergence of new threats that appears to be developed ad hoc to be key tools in cyber-war efforts.
In addition to well-known attacks and threats, such as network DDoS and ransomware, these threats included “wipers,” whose sole purpose is the disabling of the targeted hosts, often combined with other tools that allow the attackers to infect the largest number of hosts possible.
While these attacks targeted specific organizations, there is a substantial risk that in the highly connected, distributed environments used to exchange and share information in multi-national organizations these attacks might spill beyond their intended targets.
It is therefore of paramount importance to understand these threats in order to help protect both Ukrainian organizations and the rest of the world. To this end, CISA has published a series Continue reading
The 7 Requirements of Highly Effective Load Balancers
As Stephen R. Covey stated in his popular book, The 7 Habits of Highly Effective People, “True effectiveness requires balance.” VMware agrees. And when it comes to accelerating modern application delivery, true application effectiveness requires a modern load balancer. So, with a respectful nod to Stephen R. Covey, here are the seven requirements of highly effective load balancers.
- Be proactive with self-service. Move away from “create a ticket and wait” developer experiences to self-service, role-based access control for owners to provision, troubleshoot, and monitor their own apps.
- Begin with the end in mind with on-demand autoscaling. Automation drives great user experiences. Plan for peak usage times without causing overprovisioning and idle capacity.
- Put things first with a 100 percent software solution. The need to support on-premises data center and multi-cloud deployments means that enterprises need to choose applications that work consistently across different environments with a single point of orchestration.
- Think win-win with real-time insights and visibility into application traffic. A modern load balancer should collect real-time application telemetry and provide insights into each transaction and end-user patterns.
- Seek first to understand, then to be understood with security insights. App vulnerabilities stem from incorrect access control policies Continue reading
Connect and Secure your Apps with Antrea and VMware NSX-T 3.2
The release of VMware NSX-T 3.2 and VMware Container Networking with Antrea 1.3.1-1.2.3 delivers on VMware’s vision to have heterogeneous Antrea clusters running anywhere integrate with NSX-T for centralized container policy management and visibility.

NSX-T becomes the single pane of glass for policy management when connected to Antrea clusters. The Antrea clusters could be running on VMware Tanzu platform, RedHat OpenShift or any upstream Kubernetes cluster. Inventory management, tagging, dynamic grouping and troubleshooting can be extended to Antrea clusters along with native Kubernetes network policies and Antrea network policies to be centrally managed by NSX-T.
Integrating Antrea to NSX-T

Antrea to NSX-T interworking Architecture
Antrea NSX Adapter is a new component introduced to the standard Antrea cluster to make the integration possible. This component communicates with K8s API and Antrea Controller and connects to the NSX-T APIs. When a NSX-T admin defines a new policy via NSX APIs or UI, the policies are replicated to all the clusters as applicable. These policies will be received by the adapter which in turn will create appropriate CRDs using K8s APIs. The Antrea Controller which is watching these policies run the relevant computation and sends the results Continue reading
Learn About the Threats Lurking in Your Linux-Based Multi-Cloud
78% of the most popular websites are powered by Linux, which means malware targeting Linux-based operating systems are attacking multi-cloud environments at an alarming rate. Threats such as ransomware, cryptomining components, and remote access tools (RATs) take advantage of weak authentication, vulnerabilities, and misconfigurations in container-based infrastructures. To support IT leaders and cybersecurity professionals in their transformation to top-tier ransomware and malware defense, VMware is proud to sponsor a 1-hour long live webcast on Exposing Threats Lurking in Your Linux-Based Multi-Cloud, on February 28th, at 2 pm ET, presented by SC Media.
In this exclusive partnership with CyberRisk Alliance, our subject matter researchers Giovanni Vigna, Sr. Director of Threat Intelligence, VMware, and Brian Baskin, Technical Lead, Threat Analysis Unit, VMware, explore:
- Existing characterization techniques and how to safeguard against sophisticated malware
- Ransomware and cryptominer power players that target Linux systems following cross-pollination and evolution
- How to fight back against these threats with a combination of approaches, policies, and mechanisms
The webinar is an extension of the recently released Exposing Linux-based Threats Lurking in Your Multi-Cloud threat report, which included in-depth research conducted by the VMware Threat Analysis Unit (TAU) on Continue reading
Threat Landscape Report – Malware in Linux-Based Multi-Cloud Environments
Ransomware-as-a-service has become an increasingly more visible threat to organizations, and we continue to see sophisticated ransomware attacks across multi-cloud environments. A new VMware Threat Analysis Unit report exposes just how agile attackers have become by weaponizing ransomware, cryptojacking, and Remote Access Tools (RATs) in Linux-based environments. The report clearly outlines the steps attackers take once they’ve obtained a foothold in their target cloud environment, either executing ransomware or deploying cryptojacking components. In addition to these two types of attacks, our threat researchers also present how threat actors implant themselves using RATs.
In the report, a team of highly skilled and dedicated threat researchers and security professionals provide an in-depth analysis to these key findings:
- Malware targeting Linux-based systems is fast, becoming an attacker’s way into high-value, multi-cloud environments. The report uncovers that Linux is the most used operating system across multi-cloud environments, as 78% of the most popular websites are powered by Linux.
- Ransomware targeting Linux-based systems is becoming highly sophisticated. The main threats in most multi-cloud environments are ransomware, cryptojacking, and RATs. However, ransomware targeting these systems has evolved to target host images and require high-level host monitoring and analysis.
- Monero Continue reading
Emotet Is Not Dead (Yet) – Part 2
Emotet attacks leveraging malicious macros embedded in Excel files continue, with new variants and novel tactics, techniques, and procedures (TTPs). Following our recent report, we observed new waves of Emotet campaigns abusing legitimate Windows features, such as batch scripts and the mshta utility, combined with PowerShell, to deliver Emotet payloads.
In this follow-up blog post, we first provide an overview of the delivery processes of Emotet payloads in typical attacks. Then, we examine the recent variants and reveal how techniques evolved in these attacks.
Emotet payload delivery chain
The Emotet infection chain typically starts with a spam email containing a malicious document in the attachment (see Figure 1). The attachment can be either a Word document or an Excel file with embedded VBA or Excel 4.0 (XL4) macros. To entice the user to enable macro execution in Microsoft Word or Excel, the file displays social engineering content when opened. Once macro execution has been enabled, the embedded macro is executed, leading to the delivery process of an Emotet payload.

Figure 1: A typical Emotet payload delivery chain.
As highlighted in Figure 1, there are typically two ways to deliver an Emotet payload:
- Executing macros to download the payload Continue reading