Blockchain Makes an Appearance at Mobile World Congress 2018
 The new Trusted IoT Alliance looks at the intersection of IoT, security, and blockchain.
The new Trusted IoT Alliance looks at the intersection of IoT, security, and blockchain.
Report: Distributed IoT Security and Standards Workshop at NDSS 2018
Network and Distributed Systems Security (NDSS) Symposium is in full swing for its 25th anniversary year. As usual the NDSS program includes a really impressive array of great content on a wide range of topics. Prior to the main event there were four one-day workshops on themes related to the topic of NDSS: Binary Analysis Research, DNS Privacy, Usable Security, and the workshop I’d like to delve into here, Distributed IoT Security and Standards (DISS).
The DISS workshop received 29 submissions and accepted 12 papers. In an interesting twist on the usual scientific workshop format, the presented papers were all still in draft form and will now be revised based on the Q&A and offline discussions that took place as a result of the workshop. Revised papers will be published by the Internet Society in due course.
Introducing proceedings, co-chair Dirk Kutscher explained that it has become evident that the success of the Internet of Things (IoT) depends on sound and usable security and privacy. Device constraints, intermittent network connectivity, the scale of deployments, economic issues all combine to create an interesting and challenging environment for the research community to address.
A decentralised approach to IoT security Continue reading
Busy Week for MANRS, Routing Security, and More at APRICOT 2018
APRICOT 2018 is underway in in Kathmandu, Nepal, and as usual the Internet Society is an active participant in many areas of Asia Pacific’s largest international Internet conference. The workshops are taking place this week, with the conference happening next week. Here are some of the conference activities where we’ll be.
Routing Security BoF
On Sunday, 25 February, from 18:00 to 19:00 (UTC +05:45), Aftab Siddiqui and Andrei Robachevsky will moderate a Birds of a Feather (BoF) session on routing security. From the abstract, the session will provide a space where “…operators can share their approach in securing their own infrastructure and keeping the internet routing table clean as well. Also, this will provide a platform to review and highlight various BCOP documents to address routing security.” The Mutually Agreed Norms for Routing Security (MANRS) initiative is a key piece of the routing security puzzle.
Tech Girls Social
On Monday, 26 February, from 13:00 to 14:00 (UTC +05:45), Salam Yamout will be speaking at the Tech Girls Social. This session provides a space for APRICOT participants to talk and network in an open, friendly environment. The event is open to ANYONE who is interested and is not restricted to Continue reading
The Challenges of Securing the Multi-Cloud Network
 The digital transformation driving the adoption of multi-cloud networks requires an equivalent security transformation.
The digital transformation driving the adoption of multi-cloud networks requires an equivalent security transformation.
Security Experts Shine a Spotlight on Automation, Managed Services at Mobile World Congress
 The rise of 5G and IoT devices means the threat landscape is larger than ever.
The rise of 5G and IoT devices means the threat landscape is larger than ever.
Starting Today: NDSS Highlights the Best in Internet Security Research

You’ve undoubtedly heard about all sorts of Internet security vulnerabilities and incidents causing harm around the world, but the flip side of all that doom and gloom is all the promising efforts underway to create a more secure, private, and trusted Internet. Starting today and going through Wednesday (18-21 February), the Network and Distributed Systems Security (NDSS) Symposium takes place to present groundbreaking research in the world of Internet security.
This year marks the 25th anniversary of NDSS, and the Internet Society is proud to have been associated with it for over 20 years now. A key focus of the Internet Society has long been improving trust in the global open Internet. In order to promote this trust, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that brings them together. NDSS is a top tier forum for highlighting this research.
NDSS 2018 is four full days featuring:
- Two exciting keynotes from Ari Juels and Parisa Tabriz
- Four workshops on Binary Analysis Research (BAR), Decentralized IoT Security and Standards (DISS), DNS Privacy (DNSPRIV), and Usable Security (USEC).
- A full program of 71 excellent peer-reviewed research papers organized into Continue reading
The Week in Internet News: Can Blockchain Improve IoT?
Blockchain merges with IoT? Could Blockchain technology help the Internet of Things become more resilient? IBM thinks so. The company is exploring ways to use Blockchain to build trust between devices and to accelerate transactions on the IoT. EETimes explores the issue.
Grand Theft IoT: Someone involved in the online community for the video game, “Grand Theft Auto: San Andreas” has spun up a new botnet made up of IoT devices, according to security firm Radware. For the price of $20, the botnet can supposedly launch a 300gbps Distributed Denial of Service attack, reports Motherboard.
AI on the rise: Nearly after of all CIOs have plans to implement artificial intelligence in the future, according to a recent Gartner survey. The IT research firm recommends that companies rolling out AI projects aim low to start, and focus augmenting workers instead of replacing them, according to a story on TechRepublic.
Where the jobs are: For a time, it appeared that actual deployments of Blockchain seemed to be lagging behind the buzz. But that appears to be changing, with Blockchain developers now in high demand, TechCrunch reports. Blockchain jobs are the second fastest growing category in the labor market, with 14 job openings Continue reading
Keeping our users safe
To everyone in Cloudflare, account security is one of our most important tasks. We recognize that to every customer on our platform, we are critical infrastructure. We also know that the simplest attacks often lead to the most devastating of outcomes. Most people think that if they are going to get hacked it will be by some clever ”zero day”. The reality couldn’t be farther from the truth.
Attackers are smart and they have realized that even in 2018, the human is still the weakest link in the chain. The 2017 Verizon breach report identified that 81% of hacking related breaches occurred as a result of weak credentials or credential theft, an increase from the 63% reported in 2016’s breach report.
Source: Verizon 2017 data breach report
Your credentials are as important as your house or car keys. If someone copies or steals them, the repercussions can be catastrophic. If you suspect someone has access to your house keys you change your locks. If you aren’t fast enough, someone might break in.
Likewise if you realize that someone might have access to your password, the remedy is to change it. Too often, as with house keys, we are slow to Continue reading
VMware Buys Cloud Security Startup CloudCoreo
 The deal boosts VMware's multi-cloud and security plays.
The deal boosts VMware's multi-cloud and security plays.
Celebrating the 25th Anniversary of NDSS
 This year we are celebrating the 25th anniversary of the Network and Distributed System Security Symposium (NDSS). NDSS is a premier academic research conference addressing a wide range of topics associated with improving trust in the Internet and its connected devices. A key focus of the Internet Society has long been improving trust in the global open Internet. In order to promote this trust, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that connects them together.
This year we are celebrating the 25th anniversary of the Network and Distributed System Security Symposium (NDSS). NDSS is a premier academic research conference addressing a wide range of topics associated with improving trust in the Internet and its connected devices. A key focus of the Internet Society has long been improving trust in the global open Internet. In order to promote this trust, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that connects them together.
NDSS 2018 is about to get underway in San Diego, CA (18-21 February). It will be the biggest NDSS symposium yet, featuring 71 peer-reviewed papers, 20 posters, 4 workshops, 2 keynotes, and a co-located research group meeting. Record registration numbers are a key indicator that NDSS 2018 is featuring vital and timely topics. Below are some of the highlights expected in the coming week.
Workshops
This year’s program officially starts with four workshops on Sunday, 18 February. NDSS workshops are organized around a single topic and provide an opportunity for greater dialogue amongst researchers and practitioners in the area. Each of this year’s workshop have dynamic agendas.
Cisco Gives Cloud-Based Endpoint Security Products an MSSP Makeover
 Cisco will “actively pursue” MSSP customers across its entire portfolio, SVP says.
Cisco will “actively pursue” MSSP customers across its entire portfolio, SVP says.
Oracle Acquires DDoS Mitigation and Security Startup Zenedge
 Oracle gains its AI-driven web application firewall and DDoS mitigation software.
Oracle gains its AI-driven web application firewall and DDoS mitigation software.
Netronome’s Niel Viljoen Discusses the SmartNIC Market, AI, & New Operator Requirements
 In this interview, Niel Viljoen, CEO and founder of Netronome, discusses the new networking requirement in the data center, the failure of Moore’s Law, and a new wave of computing that he believes represents the future.
In this interview, Niel Viljoen, CEO and founder of Netronome, discusses the new networking requirement in the data center, the failure of Moore’s Law, and a new wave of computing that he believes represents the future.
Juniper’s Multi-Cloud Push Begins with Multi-Connectivity
 Multi-cloud means everything has to be connected to everything else.
Multi-cloud means everything has to be connected to everything else.
Workshop on Binary Analysis Research (BAR) 2018 at NDSS on 18 February
Binary analysis refers to the process where human analysts and/or automated systems scrutinize the underlying code in software to discover, exploit, and defend against malice and vulnerabilities, oftentimes without access to source code. Through protecting legacy software deployed in all types of devices and platforms in the modern world, binary analysis techniques are becoming more and more critical in making our everyday life and our society more secure.
A Workshop on Binary Analysis Research (BAR) will be co-located with the Network and Distributed System Security Symposium (NDSS), and held in San Diego, CA, USA, on February 18, 2018.
The Workshop aims to provide an interaction point for researchers doing work in binary program analysis, with half of the workshop dedicated to traditional paper sessions and the other half to a roundtable discussion among researchers, implementers, and end-users of binary analysis techniques. BAR has attracted attention of many researchers, especially tool and framework authors, who actively work to create cutting-edge techniques and build powerful tools. Here we are happy to announce that eight high-quality academic papers have been accepted to appear in the paper sessions of the workshop, with presenters from both academia and industry. Researchers and authors of several Continue reading
HTTPS or bust: Chrome’s plan to label sites as “Not Secure”

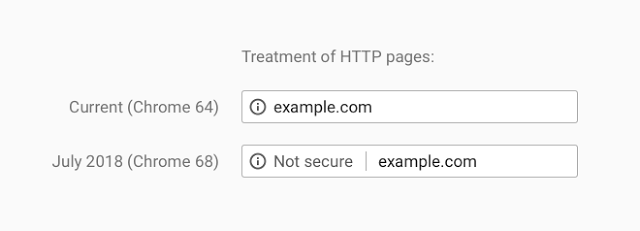
Google just announced that beginning in July 2018, with the release of Chrome 68, web pages loaded without HTTPS will be marked as “not secure”.
More than half of web visitors will soon see this warning when browsing unencrypted HTTP sites, according to data from Cloudflare’s edge that shows 56.62% of desktop requests originate from Chrome. Users presented with this warning will be less likely to interact with these sites or trust their content, so it’s imperative that site operators not yet using HTTPS have a plan to do so by July.
How did we get here (and why)?
To those who have followed the Chrome team’s public statements, this announcement comes as no surprise. Google has been gearing up for this change since 2014, as Chrome boss Parisa Tabriz tweeted and Chris Palmer memorialized in a widely distributed email. While this step is an important and potentially jarring one for users, it’s by no means the last step that Google will take to influence website administrator behavior for the better.
But why are they making this change (now)? Google’s primary motivation for driving HTTPS adoption is simple: a safe browsing experience is good for business. Users that feel Continue reading
AT&T Macro-Sizes its Microservices Supplier Program
 The carrier deployed more than 300 microservices last year.
The carrier deployed more than 300 microservices last year.
AI and Rules Drive Deepfence App-Focused Container Security
 The company's approach is to diffuse an attack before it explodes.
The company's approach is to diffuse an attack before it explodes.
Cloud Security Alliance Puts ERP Applications in its Crosshairs
 Future CSA papers will address SAP and Oracle ERP security.
Future CSA papers will address SAP and Oracle ERP security.
Citrix Acquires Cedexis to Improve App Performance in Hybrid Clouds
 Citrix will integrate Cedexis’ programmable traffic steering technology into its portfolio.
Citrix will integrate Cedexis’ programmable traffic steering technology into its portfolio.