Context-Aware Micro-segmentation – Remote Desktop Session Host Enhancements for VMware Horizon
In a previous post my colleague, Stijn, discussed the enhancements to how NSX for vSphere 6.4 handles Remote Desktop Session Host, RDSH, systems with the Identity-based Firewall and Context-Aware Micro-segmentation.
Remote Desktop Services is an underlying technology from Microsoft that many vendors take advantage of to provide overlay management and application deployment technologies for. In this post, we’re going to discuss how NSX for vSphere 6.4 allows customers to run RDS hosts with granular security for VMware Horizon systems.
VMware Horizon can provide multiple users the ability to connect to a single system to access their applications using the RDSH technology. These users can be of the same type, for example all HR users, or of multiple types, HR and Engineering users. In previous versions of NSX, it was not possible to individually secure user sessions and create Distributed Firewall (DFW) rule sets according to the user session logged into an RDSH server. This meant less flexibility in controlling what users could access data center application servers without isolating one set of users to one RDSH server. This model created a very rigid architecture for Horizon customers to follow.
Horizon allows customers Continue reading
Ixia Network Security Testing Tackles Cloud Data Center Traffic
 The platform generates 25 Gb/s of encrypted traffic to test application delivery and network security.
The platform generates 25 Gb/s of encrypted traffic to test application delivery and network security.
Aerohive Access Management Tool Brings Network Security, Control to Connected Devices
 It manages any device in a campus or branch office that needs network access, the company claims.
It manages any device in a campus or branch office that needs network access, the company claims.
Dfinity Raises $61M for Blockchain-Based Open Cloud
 The startup plans to launch its decentralized cloud this year.
The startup plans to launch its decentralized cloud this year.
Check Point Pumps Up Cloud Security: ‘It’s CASB on Steroids’
 The CloudGuard technology takes a device- and application-centric approach.
The CloudGuard technology takes a device- and application-centric approach.
Cisco Gets Yet Another CVSS 10 for ASA & Firepower | Threatpost

Yet another CVSS 10 for Cisco security products
Context-Aware Micro-segmentation – an innovative approach to Application and User Identity Firewall
Summary: With Context-awareness, NSX for vSphere 6.4 enables customers to enforce policy based on Application and Protocol Identification and expands the Identity Firewall support to Multiple User Sessions.
A few weeks ago, VMware released version 6.4 of NSX for vSphere. The 6.4 release brings many new features, with Context-awareness being key from a security perspective. Micro-segmentation enables East-West security controls, and is a key building block to a secure datacenter. Context-awareness builds-on and expands Micro-segmentation by enabling customers even more fine-grained visibility and control. NSX has supported the use infrastructure or application-centric constructs such as Security Groups based on criteria like VM name or OS version, or Dynamic Security Tags describing things like the workload function, the environment it’s deployed in, or any compliance requirements the workload falls under, enabling fine-grained control and allowing customers to automate the lifecycle of a security policy from the time an application is provisioned to the time it’s decommissioned. Prior to 6.4, rules with infrastructure or application-centric grouping constructs on the Management plane, are eventually translated to 5-tuple based rules in the dataplane.
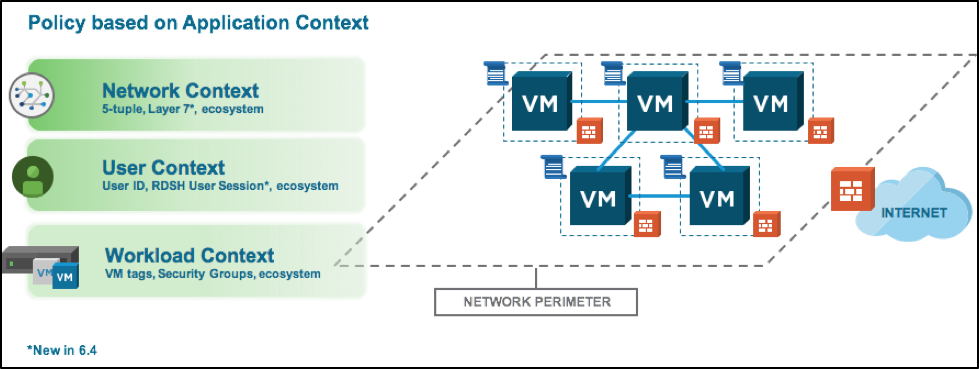 Figure: NSX drives policy based on Network, User and Workload Context
Figure: NSX drives policy based on Network, User and Workload Context
A crucial aspect of Context-awareness Continue reading
Fortinet Stock Pops on Robust 2017 Q4 Results, Modest Forecasts
 The company will also welcome a new CFO.
The company will also welcome a new CFO.
Explain Cisco ETA to Me in a Way That Even My Neighbor Can Understand It
Cisco Encrypted Traffic Analytics (ETA) sounds just a little bit like magic the first time you hear about it. Cisco is basically proposing that when you turn on ETA, your network can (magically!) detect malicious traffic (ie, malware, trojans, ransomware, etc) inside encrypted flows. Further, Cisco proposes that ETA can differentiate legitimate encrypted traffic from malicious encrypted traffic.
Uhmm, how?
The immediate mental model that springs to mind is that of a web proxy that intercepts HTTP traffic. In order to intercept TLS-encrypted HTTPS traffic, there’s a complicated dance that has to happen around building a Certificate Authority, distributing the CA’s public certificate to every device that will connect through the proxy and then actually configuring the endpoints and/or network to push the HTTPS traffic to the proxy. This is often referred to as “man-in-the-middle” (MiTM) because the proxy actually breaks into the encrypted session between the client and the server. In the end, the proxy has access to the clear-text communication.
Is ETA using a similar method and breaking into the encrypted session?
In this article, I’m going to use an analogy to describe how ETA does what it does. Afterwards, you should feel more comfortable about how Continue reading
Palo Alto Networks Stretches Security Posture Across Big 3 Public Clouds
 The new features and additional cloud support aim to provide stronger security and simplified management.
The new features and additional cloud support aim to provide stronger security and simplified management.
Top 5 From The Last 3 Months

In today’s day and age, content is king. It’s nearly impossible to keep up with the deluge of information, especially in the tech space where change is constant. We’re aware that the struggle is real. To keep you up-to-date on the latest and greatest in networking, we’ve compiled a round-up blog of the top posts from the past few months.
VMware Closes Acquisition of VeloCloud Networks
In December, VMware NSX completed its acquisition of VeloCloud Networks, bringing their industry-leading, cloud-delivered SD-WAN solution to our own growing software-based networking portfolio. The acquisition of VeloCloud significantly advances our strategy of enabling customers to run, manage, connect and secure any application on any cloud to any device. Learn all about the acquisition from SVP and GM, Networking and Security Business Unit Jeff Jennings.
VMware SDDC with NSX Expands to AWS
With VMware Cloud on AWS, customers can now leverage the best of both worlds – the leading compute, storage and network virtualization stack enabling enterprises for SDDC can now all be enabled with a click of a button on dedicated, elastic, bare-metal and highly available AWS infrastructure. Bonus: because it’s a managed service by VMware, customers can focus on the Continue reading
‘Pain Points’ Haunt Kubernetes Adoption
 Large-scale enterprises need to feel more comfortable before adoption can boom.
Large-scale enterprises need to feel more comfortable before adoption can boom.
Exclusive: U.S. consumer protection official puts Equifax probe on ice – sources | Article [AMP] | Reuters

Once again, why bother implementing IT Security when there is no downside.
Blame privacy activists for the Memo??
Former FBI agent Asha Rangappa @AshaRangappa_ has a smart post debunking the Nunes Memo, then takes it all back again with an op-ed on the NYTimes blaming us privacy activists. She presents an obviously false narrative that the FBI and FISA courts are above suspicion.I know from first hand experience the FBI is corrupt. In 2007, they threatened me, trying to get me to cancel a talk that revealed security vulnerabilities in a large corporation's product. Such abuses occur because there is no transparency and oversight. FBI agents write down our conversation in their little notebooks instead of recording it, so that they can control the narrative of what happened, presenting their version of the converstion (leaving out the threats). In this day and age of recording devices, this is indefensible.
She writes "I know firsthand that it’s difficult to get a FISA warrant". Yes, the process was difficult for her, an underling, to get a FISA warrant. The process is different when a leader tries to do the same thing.
I know this first hand having casually worked as an outsider with intelligence agencies. I saw two processes in place: one for the flunkies, and Continue reading
Why CASB Is the Fastest Growing Security Category
 Symantec, Skyhigh Networks (recently acquired by McAfee), and Netskope are leading vendors.
Symantec, Skyhigh Networks (recently acquired by McAfee), and Netskope are leading vendors.
SDxCentral’s Weekly Roundup — February 2, 2018
 AT&T to release its dNOS to Linux; Cisco buys BroadSoft; Aryaka and Radware team up.
AT&T to release its dNOS to Linux; Cisco buys BroadSoft; Aryaka and Radware team up.
It’s Time for a Collaborative G20 Digital Agenda
The G20 member states account for 85 percent of the global economy and are home to half of the world’s Internet users. From artificial intelligence to personal data protections, our physical world is being shaped by our digital world. As current president of the G20, Argentina has put a range of digital challenges on the table. But to tackle these, we need credible commitments and a long-term roadmap.
As three leading organisations from the Internet community, we welcome that Argentina continued the G20 digital work begun by Germany in 2017. Last year, Germany and the other G20 members outlined their aspirations for the development of our digital societies. And the Argentine presidency has identified five priority areas — digital inclusion, future job skills, digital government, SMEs and entrepreneurship, and Industry 4.0 — all dependent on a strong digital economy and society. Now is the year to turn these aspirations into actions.
We call on Argentina to build on this consensus with a dedicated G20 digital agenda. This roadmap must include milestones to the next G20 presidency, to be held by Japan. Priority commitments should include:
- Boost Internet access, by providing meaningful access, continuing and going to scale with Continue reading
CA Technologies Boasts Highest Revenue in 4 Years in Q3 2018 Earnings
 The company integrated two acquisitions during the quarter.
The company integrated two acquisitions during the quarter.
Rapid Micro-segmentation using Application Rule Manager Recommendation Engine
Customers understand the need for micro-segmentation and benefits it provides to enhance the security posture within their datacenter. However, one of the challenges for a Security admin is how to define micro-segmentation policies for applications owned and managed by application teams. This is even more challenging especially when you have tens or hundreds of unique applications in your data center, all of which use different port and protocols and resources across the cluster. The traditional manual perimeter firewall policy modeling may not be ideal and may not be able to scale for the micro-segmentation of your applications as it would be error-prone, complex and time consuming.
NSX addresses the how & where to start micro-segmentation challenge by providing the built-in tool called Application Rule Manager (ARM), to automate the application profiling and the onboarding of applications with micro-segmentation policies. NSX ARM has been part of NSX, since the NSX 6.3.0 release but here we will talk about Application Rule Manager (ARM) enhancement, Recommendation Engine, introduced as part of NSX 6.4.0 release. This enhancement allows you to do Rapid Micro-segmentation to your data center application by recommending “ready to consume” workload grouping & firewall policy rules.
Recorded Future Gives Companies Single View, Analysis of Security Threats
 The SaaS pushes as much of the work as possible to computing and the human on top of it "rides into victory."
The SaaS pushes as much of the work as possible to computing and the human on top of it "rides into victory."