VMware Cloud on AWS with NSX: Communicating with Native AWS Resources
If you haven’t already, please read my prior two blogs on VMware Cloud on AWS: VMware SDDC with NSX Expands to AWS and VMware Cloud on AWS with NSX – Connecting SDDCs Across Different AWS Regions; also posted on my personal blog at humairahmed.com. The prior blogs provide a good intro and information of some of the functionality and advantages of the service. In this blog post I expand the discussion to the advantages of VMware Cloud on AWS being able to communicate with native AWS resources. This is something that would be desired if you have native AWS EC2 instances you want VMware Cloud on AWS workloads to communicate with or if you want to leverage other native AWS services like AWS S3 VPC Endpoint or RDS. Continue reading
VMware Cloud on AWS with NSX: Communicating with Native AWS Resources
 If you haven’t already, please read my prior two blogs on VMware Cloud on AWS: VMware SDDC with NSX Expands to AWS and VMware Cloud on AWS with NSX – Connecting SDDCs Across Different AWS Regions; also posted on my personal blog at humairahmed.com. The prior blogs provide a good intro and information of some of the functionality and... Read more →
If you haven’t already, please read my prior two blogs on VMware Cloud on AWS: VMware SDDC with NSX Expands to AWS and VMware Cloud on AWS with NSX – Connecting SDDCs Across Different AWS Regions; also posted on my personal blog at humairahmed.com. The prior blogs provide a good intro and information of some of the functionality and... Read more →
The Meltdown and Spectre CPU Flaws Reverberate
 Linus Torvalds had harsh words for Intel.
Linus Torvalds had harsh words for Intel.
Meltdown and Spectre: Why We Need Vigilance, Upgradeability, and Collaborative Security
Today the tech media is focused on the announcement of two security vulnerabilities, nicknamed Meltdown and Spectre, that are found in almost all CPUs used in modern devices. Mobile phones, laptops, desktop computers, cloud services, and Internet of Things (IoT) devices are all vulnerable.
There are many articles being published on this topic. The best source of information I’ve found is this site by the security researchers at the Graz University of Technology:
At the bottom of that page are links to the security blog posts, advisories, and other statements from companies and organizations across the industry. In an excellent example of the principles of Collaborative Security, the announcement was coordinated with the release of patches and updates for a wide range of operating systems and devices.
For readers wanting a deeper technical dive, the site from Graz University has links to multiple academic papers. Google’s Project Zero team also published a detailed technical analysis.
From our perspective, today’s news highlights a couple of points:
- Keeping up to date on patches is critical. We each need to ensure that we upgrade our own systems and devices. If we work for organizations/companies, we need to ensure that processes are in place Continue reading
Google, Microsoft, AWS Scramble to Limit Impact from CPU Security Bugs
 These CPU security bugs have been around for 20 years, says AWS.
These CPU security bugs have been around for 20 years, says AWS.
Meltdown and Spectre
While many have already seen something on these two, this is the best set of articles I’ve found on these vulnerabilities and the ramifications.
You don’t have to worry if you patch. If you download the Continue reading
Some notes on Meltdown/Spectre
I thought I'd write up some notes.You don't have to worry if you patch. If you download the latest update from Microsoft, Apple, or Linux, then the problem is fixed for you and you don't have to worry. If you aren't up to date, then there's a lot of other nasties out there you should probably also be worrying about. I mention this because while this bug is big in the news, it's probably not news the average consumer needs to concern themselves with.
This will force a redesign of CPUs and operating systems. While not a big news item for consumers, it's huge in the geek world. We'll need to redesign operating systems and how CPUs are made.
Don't worry about the performance hit. Some, especially avid gamers, are concerned about the claims of "30%" performance reduction when applying the patch. That's only in some rare cases, so you shouldn't worry too much about it. As far as I can tell, 3D games aren't likely to see less than 1% performance degradation. If you imagine your game is suddenly slower after the patch, then something else broke it.
This wasn't foreseeable. A common cliche is that such bugs Continue reading
Why Meltdown exists
So I thought I'd answer this question. I'm not a "chipmaker", but I've been optimizing low-level assembly x86 assembly language for a couple of decades.I’d love a blogpost written from the perspective of a chipmaker - Why this issue exists. I’d never question their competency, but it seems like a violation of expectations in hindsight. Based on my very limited understanding of these issues.— SwiftOnSecurity (@SwiftOnSecurity) January 4, 2018
Let’s see if I’ve got Metldown right
I thought I'd write down the proof-of-concept to see if I got it right.So the Meltdown paper lists the following steps:
; flush cache
; rcx = kernel address
; rbx = probe array
retry:
mov al, byte [rcx]
shl rax, 0xc
jz retry
mov rbx, qword [rbx + rax]
; measure which of 256 cachelines were accessed
So the first step is to flush the cache, so that none of the 256 possible cache lines in our "probe array" are in the cache. There are many ways this can be done.
Now pick a byte of secret kernel memory to read. Presumably, we'll just read all of memory, one byte at a time. The address of this byte is in rcx.
Now execute the instruction:
mov al, byte [rcx]
This line of code will crash (raise an exception). That's because [rcx] points to secret kernel memory which we don't have permission to read. The value of the real al (the low-order byte of rax) will never actually change.
But fear not! Intel is massively out-of-order. That means before the exception happens, it will provisionally and partially execute the following instructions. While Intel has only 16 Continue reading
Fortinet FortiGate-VMX and NSX use cases
NSX is an extensible platform; other vendors security solutions can be added to it by means of the Northbound REST API, and two private APIs: NETX for network introspection, and EPSEC for guest introspection.
Fortinet’s FortiGate-VMX solution uses the NSX NETX API to provide advanced layer 4-7 services via service insertion, also called service chaining. This enables the additional inspection of VM traffic prior to that traffic reaching the vSwitch. This enhances micro-segmentation where there is need for greater application recognition, anti-malware, and other Next Generation Firewall features. The scale-out nature of NSX is maintained as NSX handles the instantiation of FortiGate service VMs on the hosts within the deployed cluster retaining its operational advantages, if the cluster grows additional FortiGate-VMX service machines will be created as needed.

One of the primary advantages to FortiGate-VMX is the availability of VDOMs for multi-tenancy in a service provider or enterprise environment – this enables segmenting traffic by organization, business group, or other construct in addition to application. The segregation includes the administration, VDOMs are managed independently of one another, this can also be used to split the different security functions such as anti-virus, IPS, and application control into isolated units or only Continue reading
VMware AppDefense & CB Defense Demo
As you may have heard, VMware and Carbon Black have come together to deliver best-in-class security architected for today’s data centers.
In this demo, you’ll see an example of how CB Defense and VMware AppDefense combine to enforce known good application behavior and detect threats using industry leading detection and response technology.
For this demo, we’ll show how an advanced security breach can come in under the guise of an innocuous application (Powershell) and often go undetected. We’ll walk through the steps that security teams can now take to respond and address the attack all in one application.

The post VMware AppDefense & CB Defense Demo appeared first on Network Virtualization.
Twistlock Ties Container and Serverless Security Into a Single Platform
 Company notes complexity remains the enemy of security.
Company notes complexity remains the enemy of security.
VMware Cloud on AWS with NSX: Connecting SDDCs Across Different AWS Regions
I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. In my prior blog post, I discussed how with VMware Cloud on AWS (VMC on AWS) customers get the best of both worlds for their move to a Software Defined Data Center (SDDC) – the leading compute, storage, and network virtualization stack for enterprises deployed on dedicated, elastic, bare-metal, and highly available AWS infrastructure. Another benefit of VMC on AWS, and the focus of this post, is that you can easily have a global footprint by deploying multiple VMC SDDCs in different regions. Continue reading
Top 5 blogs of 2017: LinuxKit, A Toolkit for building Secure, Lean and Portable Linux Subsystems
In case you’ve missed it, this week we’re highlighting the top five most popular Docker blogs in 2017. Coming in the third place is the announcement of LinuxKit, a toolkit for building secure, lean and portable Linux Subsystems.

LinuxKit includes the tooling to allow building custom Linux subsystems that only include exactly the components the runtime platform requires. All system services are containers that can be replaced, and everything that is not required can be removed. All components can be substituted with ones that match specific needs. It is a kit, very much in the Docker philosophy of batteries included but swappable. LinuxKit is an open source project available at https://github.com/linuxkit/linuxkit.
To achieve our goals of a secure, lean and portable OS,we built it from containers, for containers. Security is a top-level objective and aligns with NIST stating, in their draft Application Container Security Guide: “Use container-specific OSes instead of general-purpose ones to reduce attack surfaces. When using a container-specific OS, attack surfaces are typically much smaller than they would be with a general-purpose OS, so there are fewer opportunities to attack and compromise a container-specific OS.”
The leanness directly helps with security by removing parts not Continue reading
Simple Cyber Security Tips (for your Parents)

Today, December 25th, Cloudflare offices around the world are taking a break. From San Francisco to London and Singapore; engineers have retreated home for the holidays (albeit with those engineers on-call closely monitoring their mobile phones).
Software engineering pro-tip:
— Chris Albon (@chrisalbon) December 20, 2017
Do not, I repeat, do not deploy this week. That is how you end up debugging a critical issue from your parent's wifi in your old bedroom while your spouse hates you for abandoning them with your racist uncle.
Whilst our Support and SRE teams operated on a schedule to ensure fingers were on keyboards; on Saturday, I headed out of the London bound for the Warwickshire countryside. Away from the barracks of the London tech scene, it didn't take long for the following conversation to happen:
- Family member: "So what do you do nowadays?"
- Me: "I work in Cyber Security."
- Family member: "There seems to be a new cyber attack every day on the news! What can I possibly do to keep myself safe?"
If you work in the tech industry, you may find a family member asking you for advice on cybersecurity. This blog post will hopefully save you Continue reading
Simple Cyber Security Tips (for your Parents)

Today, December 25th, Cloudflare offices around the world are taking a break. From San Francisco to London and Singapore; engineers have retreated home for the holidays (albeit with those engineers on-call closely monitoring their mobile phones).
Software engineering pro-tip:
— Chris Albon (@chrisalbon) December 20, 2017
Do not, I repeat, do not deploy this week. That is how you end up debugging a critical issue from your parent's wifi in your old bedroom while your spouse hates you for abandoning them with your racist uncle.
Whilst our Support and SRE teams operated on a schedule to ensure fingers were on keyboards; on Saturday, I headed out of the London bound for the Warwickshire countryside. Away from the barracks of the London tech scene, it didn't take long for the following conversation to happen:
- Family member: "So what do you do nowadays?"
- Me: "I work in Cyber Security."
- Family member: "There seems to be a new cyber attack every day on the news! What can I possibly do to keep myself safe?"
If you work in the tech industry, you may find a family member asking you for advice on cybersecurity. This blog post will hopefully save you Continue reading
TLS 1.3 is going to save us all, and other reasons why IoT is still insecure
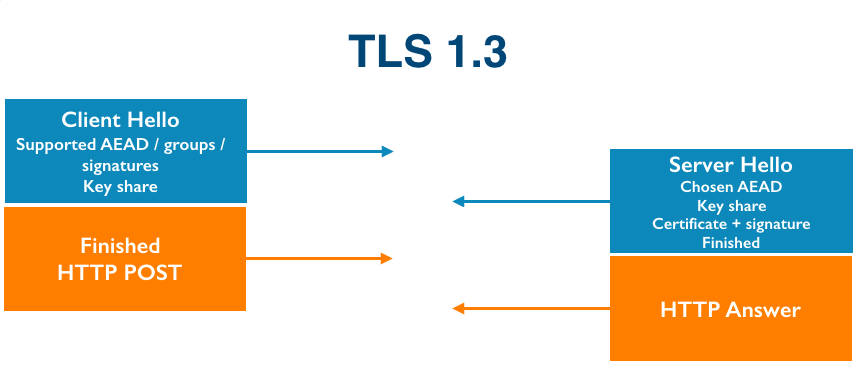
As I’m writing this, four DDoS attacks are ongoing and being automatically mitigated by Gatebot. Cloudflare’s job is to get attacked. Our network gets attacked constantly.
Around the fall of 2016, we started seeing DDoS attacks that looked a little different than usual. One attack we saw around that time had traffic coming from 52,467 unique IP addresses. The clients weren’t servers or desktop computers; when we tried to connect to the clients over port 80, we got the login pages to CCTV cameras.
Obviously it’s important to lock down IoT devices so that they can’t be co-opted into evil botnet armies, but when we talk to some IoT developers, we hear a few concerning security patterns. We’ll dive into two problematic areas and their solutions: software updates and TLS.
The Trouble With Updates
With PCs, the end user is ultimately responsible for securing their devices. People understand that they need to update their computers and phones. Just 4 months after Apple released iOS 10, it was installed on 76% of active devices.
People just don’t know that they are supposed to update IoT things like they are supposed to update their computers because they’ve never had to update things Continue reading
TLS 1.3 is going to save us all, and other reasons why IoT is still insecure

As I’m writing this, four DDoS attacks are ongoing and being automatically mitigated by Gatebot. Cloudflare’s job is to get attacked. Our network gets attacked constantly.
Around the fall of 2016, we started seeing DDoS attacks that looked a little different than usual. One attack we saw around that time had traffic coming from 52,467 unique IP addresses. The clients weren’t servers or desktop computers; when we tried to connect to the clients over port 80, we got the login pages to CCTV cameras.
Obviously it’s important to lock down IoT devices so that they can’t be co-opted into evil botnet armies, but when we talk to some IoT developers, we hear a few concerning security patterns. We’ll dive into two problematic areas and their solutions: software updates and TLS.
The Trouble With Updates
With PCs, the end user is ultimately responsible for securing their devices. People understand that they need to update their computers and phones. Just 4 months after Apple released iOS 10, it was installed on 76% of active devices.
People just don’t know that they are supposed to update IoT things like they are supposed to update their computers because they’ve never had to update things Continue reading
Top 5 Docker Customer Success Stories of 2017
The holidays are a time of joy, gratitude and reflection. As we look back on the year, we’re celebrating you, our amazing customers! You are the ones that make the Docker community special and inspire us to innovate. We appreciate the business and are grateful for the opportunity! With that we’d like to put the spotlight on the top 5 Docker Enterprise Edition (Docker EE) customer stories of 2017.
Docker Enterprise Edition Lights a New Spark of Innovation within MetLife
MetLife, the global provider of insurance, annuities, and employee benefit programs, will be celebrating it’s 150th birthday next year. To stay ahead of the competition, MetLife realizes it must be agile to more rapidly respond to changing market requirements. During the Day 2 General Session at DockerCon 2017, MetLife shared how they’re inspiring new innovation in their organization with Docker EE. MetLife also took part in the Docker MTA program designed to help customers bring portability, security, and efficiency to their traditional applications while saving on their total cost of ownership (TCO). Learn more about the Docker MTA program at Metlife in this video.

Visa Inc. Gains Speed and Operational Efficiency with Docker Enterprise Edition
In the keynote on Day Continue reading
Is Container Confusion Hindering Security Advances?
 Some organizations are taking the forklift approach too literally.
Some organizations are taking the forklift approach too literally.