Will Ransomware Die?
Ransomware has been one of the more prevalent security topics for past few years. Some probably think this form of digital destruction is here for the long haul. While this may be an accurate prediction, I can imagine a turn of events that would end this form of attack. To be clear, my theory is not that enterprise networks will plug every possible entry point. My prediction is that the ransomware business model COULD cease to be viable.
Let me expand on my position. For a business model to work, it has to have a monetization strategy. For ransomware, that strategy includes the victim sending money (typically bitcoin) to the attacker—trusting that they will be given the keys to decrypt their files. In this model, the victim has to trust their attacker [to do the right thing]. In and of itself, that seems to be an oxymoron and a plea in desperation.
So if these types of attacks fail to produce recovery options and gain widespread coverage, this trust is further eroded. To some degree this has already happened with Nyetya.
TALOS – New Ransomware Variant “Nyetya” Compromises Systems Worldwide
Without analyzing the key generation or key storage components, Talos believes Continue reading
Will Ransomware Die?
Ransomware has been one of the more prevalent security topics for past few years. Some probably think this form of digital destruction is here for the long haul. While this may be an accurate prediction, I can imagine a turn of events that would end this form of attack. To be clear, my theory is not that enterprise networks will plug every possible entry point. My prediction is that the ransomware business model COULD cease to be viable.
Let me expand on my position. For a business model to work, it has to have a monetization strategy. For ransomware, that strategy includes the victim sending money (typically bitcoin) to the attacker—trusting that they will be given the keys to decrypt their files. In this model, the victim has to trust their attacker [to do the right thing]. In and of itself, that seems to be an oxymoron and a plea in desperation.
So if these types of attacks fail to produce recovery options and gain widespread coverage, this trust is further eroded. To some degree this has already happened with Nyetya.
TALOS – New Ransomware Variant “Nyetya” Compromises Systems Worldwide
Without analyzing the key generation or key storage components, Talos believes Continue reading
Will Ransomware Die?
Ransomware has been one of the more prevalent security topics for past few years. Some probably think this form of digital destruction is here for the long haul. While this may be an accurate prediction, I can imagine a turn of events that would end this form of attack. To be clear, my theory is not that enterprise networks will plug every possible entry point. My prediction is that the ransomware business model COULD cease to be viable.
Let me expand on my position. For a business model to work, it has to have a monetization strategy. For ransomware, that strategy includes the victim sending money (typically bitcoin) to the attacker—trusting that they will be given the keys to decrypt their files. In this model, the victim has to trust their attacker [to do the right thing]. In and of itself, that seems to be an oxymoron and a plea in desperation.
So if these types of attacks fail to produce recovery options and gain widespread coverage, this trust is further eroded. To some degree this has already happened with Nyetya.
TALOS – New Ransomware Variant “Nyetya” Compromises Systems Worldwide
Without analyzing the key generation or key storage components, Talos believes Continue reading
Secure Multi-Tenancy at Scale with Docker Enterprise Edition
With the latest release of Docker Enterprise Edition (EE), enterprise organizations are able to extend the benefits of containers across their entire application portfolio. Docker EE enables rapid modernization of traditional Windows and Linux applications as well as Linux applications running on IBM Z mainframes. By addressing all of these applications, Docker EE provides the opportunity to standardize around a common packaging format for greater portability, agility, and with an additional layer of security, resulting in more teams bringing their workloads into Docker EE.
The key to operating this diverse environment is to have a way to secure and isolate the applications and the multiple teams who build, ship, and deploy them. This release of Docker Enterprise Edition makes it possible for organizations to modernize traditional applications of every variety and to do so in a secure manner that aligns to complex organizational needs.
Building a Secure Software Supply Chain for Windows Applications
Windows applications make up about half of all enterprise applications. Docker has been working closely with Microsoft to ensure that the same security benefits that are available to Linux containers are also available to Windows Server containers. When Windows containers are managed with Docker EE, organizations Continue reading
Ensuring Good with VMware AppDefense
co-author Geoff Wilmington
Traditional data center endpoint security products focus on detecting and responding to known bad behavior. There are hundreds of millions of disparate malware attacks, with over a million getting added every day. In addition, there is the threat of zero-day attacks exploiting previously unknown vulnerabilities. It becomes a never-ending race to “chase bad” without ever staying ahead of the threat landscape. What if we took an opposite approach to security? What if, instead of “chasing bad” we started by “ensuring good”?
![]() VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
Changing The Way We Secure Compute
AppDefense applies the concept of “ensuring good” by using three main techniques:
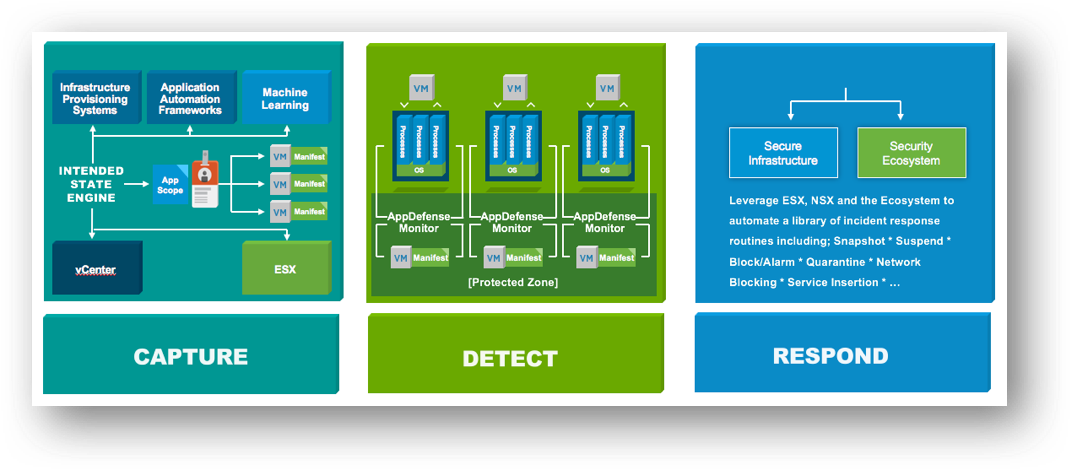
Capture
AppDefense starts by capturing Continue reading
DNS over TLS: experience from the Go6lab
After the experiment with DPRIVE at IETF99, we thought we’d try to implement it in the Go6lab and see how this actually works in day-to-day reality.
The first step was to take a look at https://dnsprivacy.org/wiki/ as we had a feeling this might be the best source for information around this topic. There’s a ton of info about DNS over TLS, but what we were really looking for was simple instructions on how to setup a recursive DNS server to serve DNS responses over TLS (port 853), as well as how to setup a local client on our device that could talk to the server and accept local DNS queries over TLS, thereby protecting our DNS communications over the Internet.
We decided that running a TLS proxy was not the way to do it, so we used CentOS 7 VPS with Unbound installed. After some time and with extensive help from Willem Toorop from NLnet Labs (thanks Willem!!!) we managed to navigate the setup process for server and client.
Firstly, we installed the default Unbound from the CentOS7 default yum repositories, which turned out not to be a very good idea, as this version is 1.4.20 Continue reading
State of MAC address randomization
tldr: I went to DragonCon, a conference of 85,000 people, so sniff WiFi packets and test how many phones now uses MAC address randomization. Almost all iPhones nowadays do, but it seems only a third of Android phones do.Ten years ago at BlackHat, we presented the "data seepage" problem, how the broadcasts from your devices allow you to be tracked. Among the things we highlighted was how WiFi probes looking to connect to access-points expose the unique hardware address burned into the phone, the MAC address. This hardware address is unique to your phone, shared by no other device in the world. Evildoers, such as the NSA or GRU, could install passive listening devices in airports and train-stations around the world in order to track your movements. This could be done with $25 devices sprinkled around a few thousand places -- within the budget of not only a police state, but also the average hacker.
In 2014, with the release of iOS 8, Apple addressed this problem by randomizing the MAC address. Every time you restart your phone, it picks a new, random, hardware address for connecting to WiFi. This causes a few problems: every time you restart Continue reading
SIDH in Go for quantum-resistant TLS 1.3
The Quantum Threat
Most of today's cryptography is designed to be secure against an adversary with enormous amounts of computational power. This means estimating how much work certain computations (such as factoring a number, or finding a discrete logarithm) require, and choosing cryptographic parameters based on our best estimate of how much work would be required to break the system.
If it were possible to build a large-scale quantum computer, many of the problems whose difficulty we rely on for security would no longer be difficult to solve. While it remains unknown whether large-scale quantum computers are possible (see this article for a good overview), it's a sufficient risk that there's wide interest in developing quantum-resistant (or post-quantum) cryptography: cryptography that works on ordinary computers we have today, but which is secure against a possible quantum computer.
At Cloudflare, our biggest use of cryptography is TLS, which we use both for serving our customers' websites (all Cloudflare sites get free HTTPS), as well as for internal inter-datacenter communication on our backend.
In the TLS context, we want to create a secure connection between a client and a server. There are basically three cryptographic problems here:
Authenticity: the server Continue reading
New Study: Understanding MANRS’ Potential for Enterprises and Service Providers
Mutually Agreed Norms for Routing Security, or MANRS, was founded with the ambitious goal of improving the security and reliability of the global Internet routing system, based on collaboration among participants and shared responsibility for Internet infrastructure. These are undoubtedly essential pillars supporting the Internet’s tremendous growth and success, but we must better articulate the incentives of contributing to global security and resilience to grow MANRS participation and reach our goals.
To do so, we engaged 451 Research to understand the attitudes and perceptions of Internet service providers and the broader enterprise community around MANRS and how it relates to their organizations. The results of the study are documented in the report: https://www.routingmanifesto.org/resources/research/.
The study results demonstrate considerable unrealized potential for MANRS, showing that enterprises are interested in security and their interest should be a strong incentive for more service providers to participate. Market education could be particularly effective in overcoming the operational inertia that many providers face.
The key points from the study are:
- While MANRS itself is not well known by enterprises, its attributes are highly valued.
- Enterprises have high expectations for MANRS efforts.
- Enterprise perceptions of MANRS can translate into increased revenue for service Continue reading
Time Synchronization, Security, and Trust
Time is something that is often overlooked or taken for granted, but the accuracy and reliability of time is critical to our lives and must be protected. Time is a core concept underlying nearly all physical and virtual systems. Distributed computer systems, key to many functions inherent in our daily lives, rely on accurate and reliable time, yet we rarely stop and think about how that time is constructed and represented. Accurate and reliable time is needed to determine when an event occurs, in what order a particular sequence of events occurs, or when to schedule an event that is to occur at a particular time in the future. Finally, and of particular interest to our trust agenda here at the Internet Society, quality reliable time is required for many of the security technologies that help provide trust for the Internet. It is a vital and often overlooked part of the Internet infrastructure.
Some specific examples where accurate reliable secure time information is vital include:
- The finance sector where there are high demands on the time synchronization of business clocks in trading systems. This is especially true in the high frequency trading where a new EU legislation called Markets Continue reading
Palo Alto Customer Wins Soar in Q4 2017
 This is the most customer wins the company has ever had during a quarter.
This is the most customer wins the company has ever had during a quarter.
Juniper Networks Acquires Security Firm Cyphort
 Cyphort’s CEO is a Juniper alum.
Cyphort’s CEO is a Juniper alum.
What’s New in Docker Enterprise Edition Webinar Recap
The latest release of Docker Enterprise Edition (EE) allows organizations to modernize Windows, Linux, and Linux-on-mainframe applications—all with minimal disruption. The release also allows organizations to run containers at scale with advanced capabilities around secure multi-tenancy and policy-based automation.
In last week’s webinar, we walked through the key new features of this release and saw a demo of Docker EE in action. If you missed the webinar, you can watch it here:
Here are the top questions from the webinar:
Q: Can you provide more information about Windows support? Which version of Windows? Is this only available with Docker Enterprise Edition?
A: You can run Windows Docker containers either with Docker Community Edition for Windows (PC) which supports Windows 10 or Docker Enterprise Edition for Windows Server 2016 (including Nano Server). Docker EE Basic is included with the Windows Server 2016 license, and you also have the option to upgrade to EE Standard or EE Advanced for Windows Server 2016 to get complete lifecycle management capabilities, Docker Trusted Registry, and advanced security features like image signing and scanning.
Q: Is it possible to deploy the Windows containers on top of a native Linux host?
A: As a form of packaging Continue reading
New: Metro- and Carrier Ethernet Encryptors Market Overview
My friend Christoph Jaggi published new versions of his Metro- and Carrier Ethernet Encryptor documents:
- Technology introduction, including an overview of encryption mechanisms, Carrier Ethernet connectivity models, typical deployments, and key management challenges.
- Market overview, including standards, control- and data plane considerations, key- and system management, and network integration.
Enjoy!
MACSec – Media Access Control Security
How Does Internet Work - We know what is networking
Media Access Control Security or MACSec is the Layer 2 hop to hop network traffic protection. Just like IPsec protects network layer, and SSL protects application data, MACSec protects traffic at data link layer (Layer 2). MACSec is standardized IEEE 802.1AE hop-by-hop encryption that enables confidentiality and integrity of data at layer 2. It encrypts entire Ethernet packet except Source and Destination MAC addresses on any device-to-device, switch-to-switch, router-to-switch, host-to-switch directly connected wired L2 connection. If we compare MACSec with, for example IPsec, MACsec provides same security but on layer 2 for each hop separately. On each hop, packets are
Introducing VMware Skyline™
VMware Skyline™: an innovative support technology, developed entirely by VMware Engineering, that provides VMware technical support engineers with extreme visibility into your (customer’s) environment.
Customers with active support subscriptions install the VMware Skyline Collector, a standalone appliance that automatically and securely collects product usage data such as configuration, feature, and performance data.

It then listens for changes, events and patterns and analyzes the information using a robust rules and machine learning engine. The rules engine is where an ever-growing library of support intelligence, product knowledge, and logic is stored to analyze inbound streams of product information. Check out the video and the blog to learn more!
The post Introducing VMware Skyline™ appeared first on Network Virtualization.
Juniper Networks Introduces Contrail Security for Cloud
 It’s using its vRouter and Contrail analytics module.
It’s using its vRouter and Contrail analytics module.
VMware Cloud Services Add Intent-Based Security for Applications
 AppDefense integrates with several technology partners including IBM Security, RSA, Carbon Black, SecureWorks, and Puppet.
AppDefense integrates with several technology partners including IBM Security, RSA, Carbon Black, SecureWorks, and Puppet.
VeloCloud Expands SD-WAN Security Ecosystem
 VeloCloud's latest members include Symantec, VMware, and Forcepoint.
VeloCloud's latest members include Symantec, VMware, and Forcepoint.
NSX Going Wild at This Year’s VMworld
Get ready! NSX is hosting a major swag giveaway at VMworld as part of a celebration for everything our customers have accomplished in 2017! At various times throughout the conference, we’ll be on the prowl, looking for folks sporting NSX gear. If you’re spotted “in the wild” adorned with anything “NSX”, you could win some awesome swag and prizes.
Join the hunt: show off your NSX pride (and your photography skills), and post photos of anything #NSX with the hashtag #NSXintheWild. Winners will be chosen at random on the VMworld floor and online, so you never know when we might have you in our sights. But make no mistake – if you’re representing NSX in the wild, you’ll be a prime target for swag.

Pay it forward: If you happen to spot some cool NSX gear in the wild, snap a photo and tweet it out using the hashtag #NSXintheWild. We hope you’ll join the fun and show off your NSX treasure. Your odds of winning some prizes will be much higher at VMworld if you do, as opposed to hitting the slots!
The post NSX Going Wild at This Year’s VMworld appeared first on Network Virtualization.

