SDxCentral Weekly News Roundup — January 1, 2016
 A departure at Wind River tops this holiday-break edition of the Roundup.
A departure at Wind River tops this holiday-break edition of the Roundup.
8 Things I Learned About SDx in 2015
 It's been a year of learning about new products, new markets... and giraffes.
It's been a year of learning about new products, new markets... and giraffes.
Trump is right about “schlong”
The reason Trump is winning is because the attacks against him are unfair. The recent schlong-gate is a great example.We regularly use words like hosed, shafted, stiffed, chapped, and boned to mean something similar. Sure, some of these derive from a base word for "penis", but are commonly used these days without any sexual or derogatory connotation. The only different about "schlonged" is that most Americans were unfamiliar with the idiom. Had Trump said "shafted" instead, this controversy would not have erupted.
It’s Unlikely Juniper Could Have Found the Security Breach Sooner
 With repo access, you can get away with a lot.
With repo access, you can get away with a lot.
2015: A Cloud Security Wake Up Call
 2015 was no stranger to security breaches, so we have to wonder: What needs to change?
2015 was no stranger to security breaches, so we have to wonder: What needs to change?
Cisco Says It Has No Juniper-Like Security Issues
 Cisco says it's found no back-door breaches. Yet.
Cisco says it's found no back-door breaches. Yet.
Why It’s Time to Build a Zero Trust Network
Network security, for a long time, has worked off of the old Russian maxim, “trust but verify.” Trust a user, but verify it’s them. However, today’s network landscape — where the Internet of Things, the Cloud, and more are introducing new vulnerabilities — makes the “verify” part of “trust but verify” difficult and inefficient. We need a simpler security model. That model: Zero Trust. Continue reading
Someone Built a Back Door Into Juniper’s Netscreen Firewalls
 It was no accident: Unauthorized code got into ScreenOS.
It was no accident: Unauthorized code got into ScreenOS.
Docker Webinar Q&A: Intro To Docker Security
Today, security is one the biggest topics within the enterprise world and tops the list of enterprise IT initiatives. As companies have begun to adopt containers within their environments, they have realized the security benefits that come with them as … ContinuedWhere do bitcoins go when you die? (sci-fi)
A cyberpunk writer asks this, so I thought I'd answer it:Plotpoint query: Someone has some bitcoins, nobody knows, they die, leave no will, have no heirs, what happens to the bitcoins?— William Gibson (@GreatDismal) December 18, 2015Note that it's asked in a legal framework, about "wills" and "heirs", but law isn't the concern. Instead, the question is:
What happens to the bitcoins if you don't pass on the wallet and password?Presumably, your heirs will inherit your computer, and if they scan it, they'll find your bitcoin wallet. But the wallet is encrypted, and the password is usually not written down anywhere, but memorized by the owner. Without the password, they can do nothing with the wallet.
Now, they could "crack" the password. Half the population will choose easy-to-remember passwords, which means that anybody can crack them. Many, though, will choose complex passwords that essentially mean nobody can crack them.
As a science-fiction writer, you might make up a new technology for cracking passwords. For example, "quantum computers" are becoming scary real scary fast. But here's the thing: any technology that makes it easy to crack this password also makes it easy to crack all of bitcoin Continue reading
Dell Preps an IPO for SecureWorks
 Before acquiring EMC, Dell seems to be forming a Federation of its own.
Before acquiring EMC, Dell seems to be forming a Federation of its own.
Force Awakens review: adequacity
The film is worth seeing. See it quickly before everyone tells you the spoilers. The two main characters, Rey and Fin, are rather awesome. There was enough cheering in the theater, at the appropriate points, that I think fans and non fans will like it. Director JarJar Abrams did not, as I feared, ruin the franchise (as he did previously with Star Trek).On the other hand, there's so much to hate. The plot is a rip-off of the original Star Wars movie, so much so that the decision to "go in and blow it up" is a soul-killing perfunctory scene. Rather than being on the edge of your seat, you really just don't care, because you know how that part ends.
While JarJar Abrams thankfully cut down down on the lens flare, there's still to much that ruins every scene he applies it to. Critics keep hammering him on how much this sucks, but JarJar will never give up his favorite movie making technique.
The universe is flat and boring. In the original trilogy, things happen for a purpose. Everything that transpires is according to Palpatine's design. And even while we find his plans confusing, we still get the Continue reading
A Different Kind of POP: The Joomla Unserialize Vulnerability
At CloudFlare, we spend a lot of time talking about the PoPs (Points of Presence) we have around the globe, however, on December 14th, another kind of POP came to the world: a vulnerability being exploited in the wild against Joomla’s Content Management System. This is known as a zero day attack, where it has been zero days since a patch has been released for that bug. A CVE ID has been issued for this particular vulnerability as CVE-2015-8562. Jaime Cochran and I decided to take a closer look.
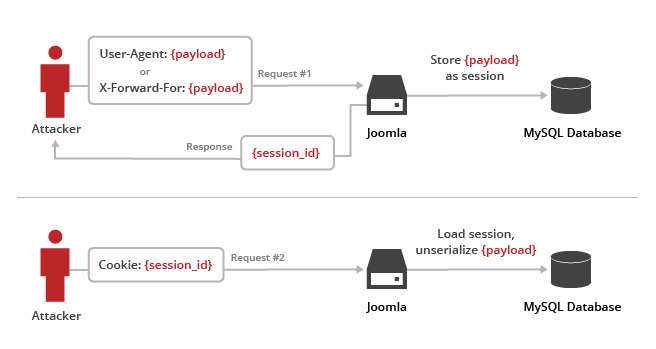
In this blog post we’ll explain what the vulnerability is, give examples of actual attack payloads we’ve seen, and show how CloudFlare automatically protects Joomla users. If you are using Joomla with CloudFlare today and have our WAF enabled, you are already protected.
The Joomla Web Application Firewall rule set is enabled by default for CloudFlare customers with a Pro or higher plan, which blocks this attack. You can find it in the Joomla section of the CloudFlare Rule Set in the WAF Dashboard.
What is Joomla?
Joomla is an open source Content Management System which allows you to build web applications and control every aspect of the content of your Continue reading
DockerCon EU 2015 Videos: Docker, Docker, Docker
And all of the videos from the Docker, Docker, Docker track at DockerCon EU 2015 are now available! Check out the recorded sessions and slides below. Getting Started with Docker – Sam Alba,Sr. Director of Engineering, Docker and Jeff Morgan, … ContinuedAll app developers should learn from WhatsApp-v-Brazil incident and defend against it
So Brazil forced the ISPs to shutdown WhatsApp (a chat app) for 48 hours, causing more than a million of their customers to move to Telegram (another chat app). Apparently, this was to punish WhatsApp for not helping in a criminal investigation.More than 1.000.000 new users from Brazil today and growing. If you've just joined, check this out: https://t.co/x1haKyjvzQ— Telegram Messenger (@telegram) December 17, 2015Well, this is similar to how ISPs block botnets. Botnets, the most common form of malware these days, have a command-channel back to the hacker that controls all the bots in the network. ISPs try to block the IP address and/or DNS name in order to block access to the botnet.
Botnets use two ways around this. One way is "fast-flux DNS", where something like "www.whatsapp.com" changes its IP address every few minutes. This produces too many IP addresses for ISPs to block. WhatsApp can keep spinning up new cloud instances at places like Amazon Web Services or Rackspace faster than ISPs can play whack-a-mole.
But ISPs can also block the domain name itself, instead of the IP address. Therefore, an app can also choose to Continue reading
No, you can’t shut down parts of the Internet
In tonight's Republican debate, Donald Trump claimed we should shutdown parts of the Internet in order to disable ISIS. This would not work. I thought I'd create some quick notes why.This post claims it would be easy, just forge a BGP announcement. Doing so would then redirect all Syrian traffic to the United States instead of Syria. This is too simplistic of a view.
Technically, the BGP attack described in the above post wouldn't even work. BGP announcements in the United States would only disrupt traffic to/from the United States. Traffic between Turkey and ISIS would remain unaffected. The Internet is based on trust -- abusing trust this way could only work temporarily, before everyone else would untrust the United States. Legally, this couldn't work, as the United States has no sufficient legal authority to cause such an action. Congress would have to pass a law, which it wouldn't do.
But "routing" is just a logical layer built on top of telecommunications links. Since Syria and Iraq own their respective IP address space, I'm not even sure ISIS is allowed to use it. Instead, ISIS has to pay for telecommunications links to route traffic through other countries. This causes Continue reading
Security ‘net

The ‘web has been abuzz with security stuff the last couple of weeks; forthwith a small collection for your edification.
The man in the middle attack is about as overused as the trite slippery slope fallacy in logic and modern political “discourse” (loosely termed — political discourse is the latest term to enter the encyclopedia of oxymorons as it’s mostly been reduced to calling people names and cyberbullying, — but of course, putting the social media mob in charge of stopping bullying will fix all of that). But there are, really, such things as man in the middle attacks, and they are used to gather information that would otherwise be unavailable because of normal security provided by on the wire encryption. An example? There is no way to tell if your cell phone is connecting to a real cell phone tower or a man-in-the-middle device that sucks all your information out and ships it to an unintended recipient before forwarding your information along to its correct destination.
Policy wonks aren’t computer experts
This Politico story polls "cybersecurity experts" on a range of issues. But they weren't experts, they were mostly policy wonks and politicians. Almost none of them have ever configured a firewall, wrote some code, exploited SQL injection, analyzed a compromise, or in any other way have any technical expertise in cybersecurity. It's like polling a group of "medical experts", none of which has a degree in medicine, or having a "council of economic advisers", consisting of nobody with economics degrees, but instead representatives from labor unions and corporations.As an expert, a real expert, I thought I'd answer the questions in the poll. After each question, I'll post my answer (yes/no), the percentage from the Politico poll of those agreeing with me, and then a discussion.
Should the government mandate minimum cybersecurity requirements for private-sector firms?
No (39%). This question is biased because they asked policy wonks, most of which will answer "yes" to any question "should government mandate". It's also biases because if you ask anybody involved in X if we need more X, they'll say "yes", regardless of the subject you are talking about.
But the best answer is "no", for three reasons.
Firstly, we experts don't know Continue reading
Some notes on fast grep
This thread on the FreeBSD mailing discusses why GNU grep (that you get on Linux) is faster than the grep on FreeBSD. I thought I'd write up some notes on this.I come from the world of "network intrusion detection", where we search network traffic for patterns indicating hacker activity. In many cases, this means solving the same problem of grep with complex regexes, but doing so very fast, at 10gbps on desktop-class hardware (quad-core Core i7). We in the intrusion-detection world have seen every possible variation of the problem. Concepts like "Boyer-Moore" and "Aho-Corasick" may seem new to you, but they are old-hat to us.
Zero-copy
Your first problem is getting the raw data from the filesystem into memory. As the thread suggests, one way of doing this is "memory-mapping" the file. Another option would be "asynchronous I/O". When done right, either solution gets you "zero-copy" performance. On modern Intel CPUs, the disk controller will DMA the block directly into the CPU's L3 cache. Network cards work the same way, which is why getting 10-gbps from the network card is trivial, even on slow desktop systems.
Double-parsing
Your next problem is stop with the line parsing, idiots. All these Continue reading