Dumb, dumber, and cybersecurity
The reason you got hacked is because you listen to dumbasses about cybersecurity, like Microsoft.An illustrative example is this article on "10 steps to protect" yourself. The vast majority of cyber threats to a small business are phishing, password reuse, and OWASP threats like SQL injection. That article addressed none of these threats.
But it gets better.
At the bottom of that article is a link to this "Cyber Security IQ" quiz at Microsoft's small-business website. The first question asks about password sharing. I show their "right" answer here:
Their correct answer is "None of the above", meaning that it's not okay to share your passwords with anybody. But this is nonsense. For your work account, of course it's okay to share your password with your boss. In fact, it's often necessary.
There have been several court cases where IT administrators have been fired, where the companies later found that the fired employee is the only one with passwords to certain critical systems. The (former) administrators were prosecuted for refusing to give their former bosses the passwords.
If your boss demands your password to your corporate accounts, of course you must give them your password.
But it Continue reading
Ethics of killing Hitler
The NYTimes asks us: if we could go back in time and kill Hitler as a baby, would we do it? There's actually several questions here: emotional, moral, and ethical. Consider a rephrasing of the question to focus on the emotional question: could you kill a baby, even if you knew it would grow up and become Hitler?But it's the ethical question that comes up the most often, and it has real-world use. It's pretty much the question Edward Snowden faced: should he break his oath and disclose the NSA's mass surveillance of Americans?
I point this out because my ethical response is "yes, and go to jail". The added "and go to jail" makes it a rare response -- lots of people are willing to kill Hitler if they don't suffer any repercussions.
For me, the hypothetical question is "If you went back in time and killed Hitler, would you go to jail for murder?". My answer is "yes". I'd still do my best to lessen the punishment. I'd hire the best lawyer to defend me. It's just that I would put judgement of my crime or heroism in the hands of others. I would pay Continue reading
Getting Started with VMware NSX Distributed Firewall – Part 1
Who saw it coming that segmentation would be a popular term in 2015?!? Gartner analyst Greg Young was almost apologetic when he kicked off the Network Segmentation Best Practices session at the last Gartner Security Summit.
As a professional with a long history in the enterprise firewall space, I know I found it odd at first. Segmentation is such a basic concept, dovetailing with how we secure networks – historically on network boundaries. Network segmentation is the basis for how we write traditional firewall rules – somehow get the traffic TO the firewall, and policy can be executed. How much more can we say about network segmentation?
But there is a problem with the reach of segmentation based on network. If traffic does not cross the firewall, you are blind. All hosts in the same network, commonly the same VLAN, can abuse each other at will. Perhaps netflow or IPS sensors are throughout your network – just to catch some of this internal network free-for-all. And the DMZ? I like to think of all these networks as blast-areas, where any one compromise could potentially take everything else on the same network down.
It’s not really network segmentation that’s all the Continue reading
Car hacking is as fake as the moonlanding
 |
| How can the flag stay up? There's no wind on the moon!! #fake |
Of course, "hacking a car" probably doesn't happen as the public imagines. Delving into the details, you'll find things you didn't expect. It's like the stars in pictures at the moon landing. Because of contrast issues with the bright foreground, the dim stars disappear. This has led to crazies saying the lack of stars are proof that the moon landings were faked, because they don't understand this technical issue. Similarly, Pogue claims car hacking is fake because the technical details don't match his ignorant prejudices.
Pogue's craziest claim is that the Jeep hack is fake because Jeep fixed the issue. Nobody can hack a Jeep as the researchers claim. But that's because the researchers proved to Jeep that it was possible, and gave time for Jeep to fix the problem. It's like claiming the 9/11 terrorist attacks are purely hypothetical, because the Twin Towers of the World Trade Center no longer exist.
The Continue reading
Biden vs Risk Analysis
HP Unplugs Its Public Cloud & Flips TippingPoint
 A concession to AWS and Azure; a handoff to Trend Micro.
A concession to AWS and Azure; a handoff to Trend Micro.
Ever Heard of Role-Based Access Control?
During my recent SDN workshops I encountered several networking engineers who use Nexus 1000V in their data center environment, and some of them claimed their organization decided to do so to ensure the separation of responsibilities between networking and virtualization teams.
There are many good reasons one would use Nexus 1000V, but the one above is definitely not one of them.
Read more ...Dell World Puts a Spotlight on Security
 SonicWALL and Dell Data Protection highlight today's Dell World launches.
SonicWALL and Dell Data Protection highlight today's Dell World launches.
DEF CON drink-off — for science!
The DEF CON hacking conference is a mixture of techies and drinkers. I propose we exploit this for science. Specifically, we should take a look at vodka. Vodka is just ethanol and water with all taste removed by distillation and filtering. We can answer two important questions.- Poorly made, cheap vodka lets too much of the (bad) flavor through. Can this be improved by running it through a filter? (Such as a cheap Brita water filter).
- Well-made vodka should be indistinguishable from each other. Can people really taste the difference? Or are they influenced by brands?
We need to science the shit out of these questions with a double-blind taste test. DEF CON is a perfect venue for getting a statistically relevant number of samples. We should setup a table in a high-traffic area. We'll ask passersby to taste a flight of several vodkas and to rate them.
I suggest the following as the set of vodkas to test.
1. Smirnoff, by far the market leading vodka in America, a "mid-shelf" vodka at $22 for a 1.75 liter bottle.
2. Grey Goose, the third most popular vodka in America, a "top-shelf" vodka for $58 a 1.75 liter bottle.
Continue reading
DH-1024 in Bitcoin terms
The ASIC power in the current Bitcoin network could do all the necessary precomputations for a Diffie-Hellman 1024 bit pair with 154 minutes worth of work. Or, the precomputation effort is roughly equal to 15 bitcoin blocks, at the current rate.(Update: I did some math wrong, it's 154 minutes not 23 minutes)
Another way of comparing is by using the website "keylength.com", which places the equivalent effort of cracking 1024 DH with 72 to 80 bits of symmetric crypto. At the current Bitcoin rate, 72 bits of crypto comes out to 15 bitcoin blocks, Continue reading
Global Impacts of Recent Leaks

Recent routing leaks remind us why monitoring Internet routing and performance is important and requires effective tools. Routing leaks are the ‘benign cousin’ of the malicious BGP route hijack. They happen accidentally, but the result is the same: traffic to affected prefixes is redirected, lost, or intercepted. And if they happen to you, your online business and brand suffers.
In this blog, we look at examples of a full-table peer leak, an origination leak, and a small peer leak and what happens to traffic when these incidents occur. As we will see, some events can go on for years, undetected and hence, unremediated, but extremely impactful never the less. As you read this blog, keep the following questions in mind. Would you know if the events described here were happening to you? Would you know how to identify the culprit if you did?
iTel/Peer1 routing leak
Starting on 10 October at 10:54 UTC, iTel (AS16696) leaked a full routing table (555,010 routes) to Peer 1 (AS13768). Normally, iTel exports 49 routes to Peer 1; however, over the course of several minutes, it leaked 436,776 routes from Hurricane Electric (AS6939) and 229,537 Continue reading
Cybereason Locks Up a $59 Million Round
 Cybersecurity firm partners with SoftBank for joint offering in Japan
Cybersecurity firm partners with SoftBank for joint offering in Japan
Security Release: Docker 1.8.3 and 1.6.2-CS7
As part of our ongoing security efforts, a vulnerability was discovered that affects the way content is stored and retrieved within the Docker Engine. Today we are releasing a security update that addresses this issue in accordance with our coordinated … ContinuedInfosec is good people
A10 DemoFriday Q&A + Video: Delivering Advanced Security & Application Policies with Cisco ACI & Thunder ADC
 The A10 and Cisco teams answer advanced security questions following their presentation on the Thunder ADC and Cisco ACI.
The A10 and Cisco teams answer advanced security questions following their presentation on the Thunder ADC and Cisco ACI.
Control Plane Protection in Cisco IOS
How does Internet work - We know what is networking
CoPP – Control Plane Protection or better Control Plain Policing is the only option to make some sort of flood protection or QoS for traffic going to control plane. In the router normal operation the most important traffic is control plain traffic. Control plane traffic is traffic originated on router itself by protocol services running on it and destined to other router device on the network. In order to run properly, routers need to speak with each other. They speak with each other by rules defined in protocols and protocols are run in shape of router services. Examples for this
SSL Certificate signed by own CA
There are a lot of “how-to” on the Internet explaining the setup procedure. This is mainly a copy / paste example for those in a hurry :)
How to setup your own CA
Cisco Strikes a Blow Against Ransomware
 A $60M Angler Exploit Kit operation gets cut in half.
A $60M Angler Exploit Kit operation gets cut in half.
Arista Takes a Macro Approach to Physical & Virtual Network Security
 It's like microsegmentation, only more 'macro.'
It's like microsegmentation, only more 'macro.'
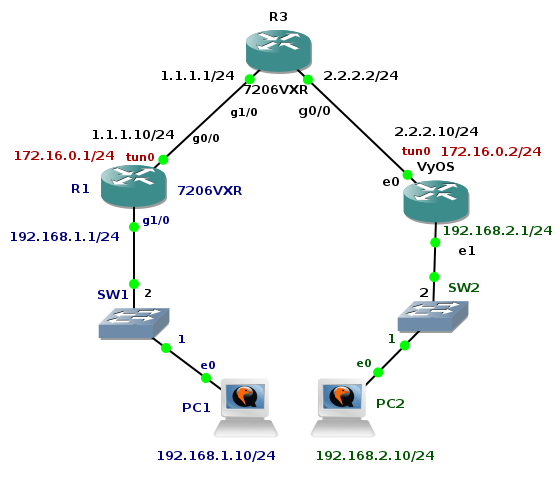
GRE over IPSec Tunnel Between Cisco and VyOS
The previous tutorial shown GRE tunnel configuration between Cisco router and Linux Core. The big advantage of GRE protocol is that it encapsulates L3 and higher protocols inside the GRE tunnel so routing updates and other multicast traffic can be successfully transferred over the tunnel. The main drawback of GRE protocol is the lack of built-in security. Data are transferred in plain-text over the tunnel and peers are not authenticated (no confidentiality). Tunneled traffic can be changed by attacker (no integrity checking of IP packets). For this reason GRE tunnel is very often used in conjunction with IPSec. Typically, GRE tunnel is encapsulated inside the IPSec tunnel and this model is called GRE over IPSec.
The tutorial shows configuration of OSPF routing protocol, GRE and IPSec tunnel on Cisco 7206 VXR router and appliance running VyOS network OS. Devices are running inside GNS3 lab an they are emulated by Dynamips (Cisco) and Qemu (VyOS).
Picture 1 - Topology
Note: VyOS installation is described here. You can easily build your own VyOS Qemu appliance using the Expect and Bash script shared in the article.
1. R3 Configuration
R3(config)# interface gigabitEthernet 1/0
R3(config-if)# ip address 1.1.1.1 255.255.255.0
R3(config-if)# no shutdown
R3(config-if)# interface gigabitEthernet 0/0
R3(config-if)# ip Continue reading