7 Layers: IoT Part 1 — You, Me, and IoT
This week is the first in a two-part series on the Internet of Things. We answer: What is IoT? And...
Akamai Puts Script Attacks in Its Crosshairs
“The evolution of web applications has not gone unnoticed by attackers, and web defenders...
Juniper Claims Mist Win Rate Against Cisco Tops 80%
Mist serves as the heart of Juniper’s AI-driven enterprise strategy. And Mavis is the brain.
Palo Alto Networks Weathers Pandemic With Strong Earnings
The company’s Q3 revenues hit $869.4 million, up 20% year over year, bolstered by a pandemic...
Securing work-at-home apps
In today's post, I answer the following question:Our customer's employees are now using our corporate application while working from home. They are concerned about security, protecting their trade secrets. What security feature can we add for these customers?The tl;dr answer is this: don't add gimmicky features, but instead, take this opportunity to do security things you should already be doing, starting with a "vulnerability disclosure program" or "vuln program".
Gimmicks
First of all, I'd like to discourage you from adding security gimmicks to your product. You are no more likely to come up with an exciting new security feature on your own as you are a miracle cure for the covid. Your sales and marketing people may get excited about the feature, and they may get the customer excited about it too, but the excitement won't last.
Eventually, the customer's IT and cybersecurity teams will be brought in. They'll quickly identify your gimmick as snake oil, and you'll have made an enemy of them. They are already involved in securing the server side, the work-at-home desktop, the VPN, and all the other network essentials. You don't want them as your enemy, you want them as your friend. You Continue reading
Use Layer 7 Application Identity in Your Segmentation Policies
With the launch of VMware NSX in 2013, VMware pioneered micro-segmentation. Back then our solution was based on stateful Layer 4 filtering. We’ve added in dynamic grouping, enabling policies based on VM context such as VM Name, Operating System or Security Tags. Using dynamic grouping, the life cycle of a Service-defined Firewall policy is directly tied to the life cycle of the workloads/application it’s protecting. This is radically different from traditional firewalls which use IP-address based policies.
Another addition to our Service-defined firewall is Layer 7 Application Identity. You may be familiar with the concept from the perspective of a perimeter firewall where it can be used to allow access to Facebook chat but block access to Facebook games. The data center is different and so are the use cases for layer 7 Application Identity.
In this blog I will cover why organizations should use Layer 7 Application Identity in their data center segmentation policies.
What Are the Problems with Port-Based Rules?
While stateful Layer 4 firewalls have significantly reduced both the complexity and security gaps that come with configuring stateless Access Control Continue reading
CISSP is at most equivalent to a 2-year associates degree
There are few college programs for "cybersecurity". Instead, people rely upon industry "certifications", programs that attempt to certify a person has the requisite skills. The most popular is known as the "CISSP". In the news today, European authorities decided a "CISSP was equivalent to a masters degree". I think this news is garbled. Looking into the details, studying things like "UK NARIK RQF level 11", it seems instead that equivalency isn't with master's "degrees" so much as with post-graduate professional awards and certifications that are common in industry. Even then, it places CISSP at too high a level: it's an entry level certification that doesn't require a college degree, and teaches students only familiarity with buzzwords used in the industry rather than the deeper level of understanding of how things work.Security Field Day #XFD3 with the VMware NSX Security Team

The Gestalt IT team is back with another exciting set of Field Day presentations. Multiple IT product vendors, including VMware, and independent thought leaders will share information and opinions in a presentation and discussion format. The complete VMware agenda and speaker lineup for the morning of the 14th is listed in detail below.
In summary, VMware’s focus for #XFD3 is why a new approach to security is required in the modern era. This security vision is present across all of the solutions, technologies, and bundles that we are bringing to the market. The VMware speakers, Dhruv, Stijn, Ray, and Ashish are planning to cover diverse topics ranging across Service-defined Firewall (SDFW), IDS/IPS, NSX Intelligence, DDoS, and WAF.
Video 2: Dhruv Continue reading
McAfee, CrowdStrike, Palo Alto Networks Track Evolving COVID-19 Cyberattacks
Three reports show cyberattacks continue to mutate along with the COVID-19 pandemic, and they...
Money Moves: April 2020
Nokia faced a hostile takeover bid; Google eyeing a D2iQ purchase; T-Mobile to slash $30M in cloud...
‘SD-WAN Has to Evolve,’ Says Cisco Exec
Steven Wood, Cisco’s principal engineer of enterprise architectures and SD-WAN, made the...
Cisco Firewall Bugs Leave Networks Vulnerable to Attacks
The Cisco Adaptive Security Appliance alone has more than 1 million deployments globally, according...
Fortinet Weathers Pandemic Storm, Posts Robust Q1 Earnings
“Our ability to directly manage our supply chain and shipping logistics allowed us to quickly...
Cloudflare Bot Management: machine learning and more

Introduction

Building Cloudflare Bot Management platform is an exhilarating experience. It blends Distributed Systems, Web Development, Machine Learning, Security and Research (and every discipline in between) while fighting ever-adaptive and motivated adversaries at the same time.
This is the ongoing story of Bot Management at Cloudflare and also an introduction to a series of blog posts about the detection mechanisms powering it. I’ll start with several definitions from the Bot Management world, then introduce the product and technical requirements, leading to an overview of the platform we’ve built. Finally, I’ll share details about the detection mechanisms powering our platform.
Let’s start with Bot Management’s nomenclature.
Some Definitions
Bot - an autonomous program on a network that can interact with computer systems or users, imitating or replacing a human user's behavior, performing repetitive tasks much faster than human users could.
Good bots - bots which are useful to businesses they interact with, e.g. search engine bots like Googlebot, Bingbot or bots that operate on social media platforms like Facebook Bot.
Bad bots - bots which are designed to perform malicious actions, ultimately hurting businesses, e.g. credential stuffing bots, third-party scraping bots, spam bots and sneakerbots.
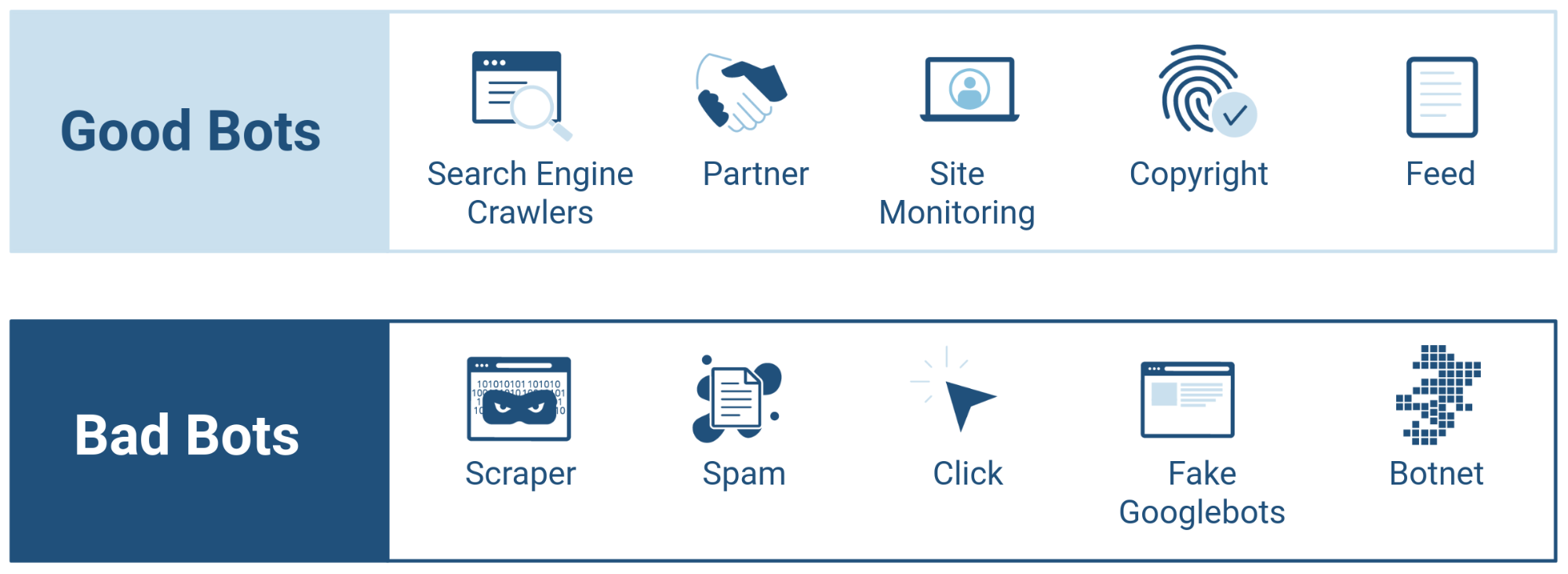
Bot Management - blocking Continue reading
Microsoft Azure Sentinel Powers Open Systems’ Threat Detection
Open Systems’ customers liked the Sentinel technology, but wanted the threat detection and...
Former Check Point Execs Score $20M for Orca Security
With the Series A round, in addition to $6.5 million in seed funding, Orca plans to double its team...
Daily Roundup: Cisco Debunks Security Myths
Cisco debunked security myths; Nvidia bought Cumulus; and T-Mobile claimed 5 standalone 5G firsts.
How Rakuten Mobile Corralled Vendors for Its Open RAN Vision
Complexities were abundant and corralling vendors for a virtualized, cloud-native, open radio...