Palo Alto Folds CloudGenix in $420M SASE Play
CloudGenix will form the second pillar of Palo Alto's emerging secure access service edge offering,...
Lenovo, Microsoft Push HCI to the Edge
Lenovo also rolled out new NVMe storage systems that integrate with AWS, Azure, Google, and IBM...
Comcast’s Jeffrey Lewis: ‘Job No. 1 Is Customer Experience’
Comcast's Jeffery Lewis sat down to share his thoughts on ActiveCore and how it is improving the...
Daily Roundup: VMware Pulls FY21 Forecast
VMware withdrew FY21 guidance citing coronavirus concerns; Kubernetes 1.18 ramped up Windows...
Security Experts Battle Hackers, COVID-19 Cyberattacks
Threat researchers at Microsoft, ClearSky, and Okta are among the hundreds of security experts...
Using Cloudflare to secure your cardholder data environment


As part of our ongoing compliance efforts Cloudflare’s PCI scope is reviewed quarterly and after any significant changes to ensure all in-scope systems are operating in accordance with the PCI DSS. This review also allows us to periodically review each product we offer as a PCI validated service provider and identify where there might be opportunities to provide greater value to our customers.
With our customers in mind, we completed our latest assessment and have increased our PCI certified product offering!
Building trust in our products is one critical component that allows Cloudflare’s mission of “Building a Better Internet” to succeed. We reaffirm our dedication to building trust in our products by obtaining industry standard security compliance certifications and complying with regulations.
Cloudflare is a Level 1 Merchant, the highest level, and also provides services to organizations to help secure their cardholder data environment. Maintaining PCI DSS compliance is important for Cloudflare because (1) we must ensure that our transmission and processing of cardholder data is secure for our own customers, (2) that our customers know they can trust Cloudflare’s products to transmit cardholder data securely, and (3) that anyone who interacts with Cloudflare’s services know that their information is Continue reading
Video: IPv6 Security Overview
When I’ve seen my good friends Christopher Werny and Enno Rey talk about IPv6 security at RIPE78 meeting, another bit of one of my puzzles fell in place. I was planning to do an update of the IPv6 security webinar I’d done with Eric Vyncke, and always wanted to get it done by a security practitioner focused on enterprise networks, making Christopher a perfect fit.
As it was almost a decade since we did the original webinar, Christopher started with an overview of IPv6 security challenges (TL&DR: not much has changed).
What Cisco Networking Learned During the Pandemic
Now that all Cisco employees work remotely, it sees more than 170,000 remote network connections...
Daily Roundup: Tier-1 Operators Back New TIP Spec
Tier-1 operators backed new TIP specifications; Juniper VP shared security strategy to make...
Is Kubernetes the Cure to Cantankerous 5G Core?
The promise of 5G hinges on adoption of cloud-native technologies and specifically Kubernetes as...
IT, OT Worlds Collide With 5G Security
Converged IT and OT security platforms are one way that service providers and security vendors are...
Juniper Security VP: Networks Must Be Threat Aware
Samantha Madrid joined the company with a very specific security strategy: change how we secure...
Speeding up Linux disk encryption
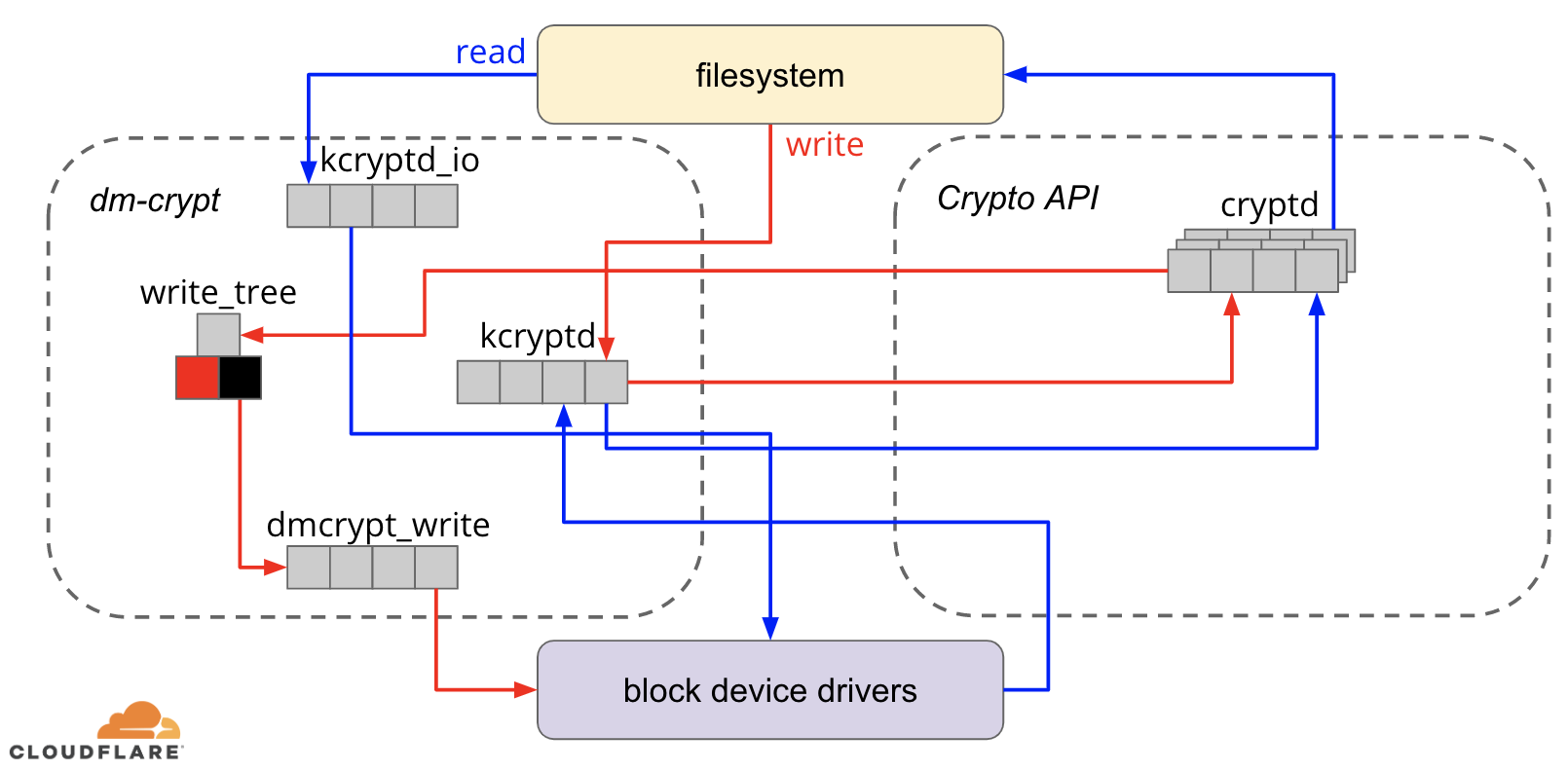
Data encryption at rest is a must-have for any modern Internet company. Many companies, however, don't encrypt their disks, because they fear the potential performance penalty caused by encryption overhead.
Encrypting data at rest is vital for Cloudflare with more than 200 data centres across the world. In this post, we will investigate the performance of disk encryption on Linux and explain how we made it at least two times faster for ourselves and our customers!
Encrypting data at rest
When it comes to encrypting data at rest there are several ways it can be implemented on a modern operating system (OS). Available techniques are tightly coupled with a typical OS storage stack. A simplified version of the storage stack and encryption solutions can be found on the diagram below:
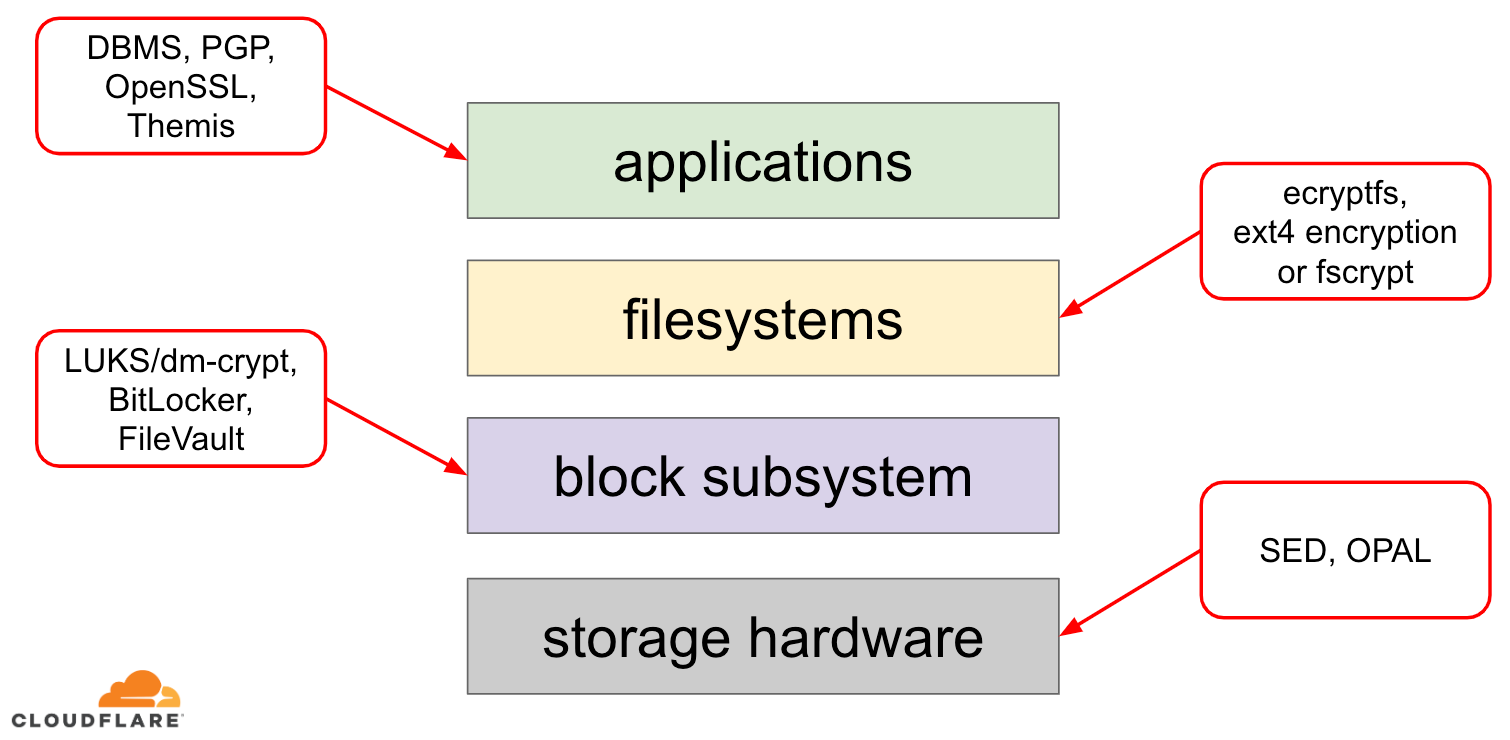
On the top of the stack are applications, which read and write data in files (or streams). The file system in the OS kernel keeps track of which blocks of the underlying block device belong to which files and translates these file reads and writes into block reads and writes, however the hardware specifics of the underlying storage device is abstracted away from the filesystem. Finally, the block subsystem actually Continue reading
Daily Roundup: Intel Warns of Financial Hit
Intel warned of financial hit; Attackers exploited remote-code execution vulnerabilities in...
Microsoft Warns of Attacks Exploiting Zero-Day Flaws
Microsoft said it’s “aware of limited targeted attacks” using the remote-code execution...
Cato Bolsters SASE-Based SDP to Serve Remote Workers
The vendor said the SASE architecture promises less complexity, shorter deployment times, improved...
SwiftStack Deploys Scalable Telecom Data Platform with Dell Technologies
SwiftStack’s data platform uses a combination of software-defined architecture engineered for the...
Deploying security.txt: how Cloudflare’s security team builds on Workers
When the security team at Cloudflare takes on new projects, we approach them with the goal of achieving the “builder first mindset” whereby we design, develop, and deploy solutions just as any standard engineering team would. Additionally, we aim to dogfood our products wherever possible. Cloudflare as a security platform offers a lot of functionality that is vitally important to us, including, but not limited to, our WAF, Workers platform, and Cloudflare Access. We get a lot of value out of using Cloudflare to secure Cloudflare. Not only does this allow us to test the security of our products; it provides us an avenue of direct feedback to help improve the roadmaps for engineering projects.
One specific product that we get a lot of use out of is our serverless platform, Cloudflare Workers. With it, we can have incredible flexibility in the types of applications that we are able to build and deploy to our edge. An added bonus here is that our team does not have to manage a single server that our code runs on.
Today, we’re launching support for the security.txt initiative through Workers to help give security researchers a common location to learn about how Continue reading
White Hat Hackers Fight COVID-19, Donate GPUs for a Cure
Security company Critical Start and its threat hunters are among the global contributors running...
Using Cloudflare Gateway to Stay Productive (and turn off distractions) While Working Remotely
This week, like many of you reading this article, I am working from home. I don’t know about you, but I’ve found it hard to stay focused when the Internet is full of news related to the coronavirus.
CNN. Twitter. Fox News. It doesn’t matter where you look, everyone is vying for your attention. It’s totally riveting…
… and it’s really hard not to get distracted.
It got me annoyed enough that I decided to do something about it. Using Cloudflare’s new product, Cloudflare Gateway, I removed all the online distractions I normally get snared by — at least during working hours.
This blog post isn’t very long, but that’s a function of how easy it is to get Gateway up and running!
Getting Started
To get started, you’ll want to set up Gateway under your Cloudflare account. Head to the Cloudflare for Teams dashboard to set it up for free (if you don’t already have a Cloudflare account, hit the ‘Sign up’ button beneath the login form).
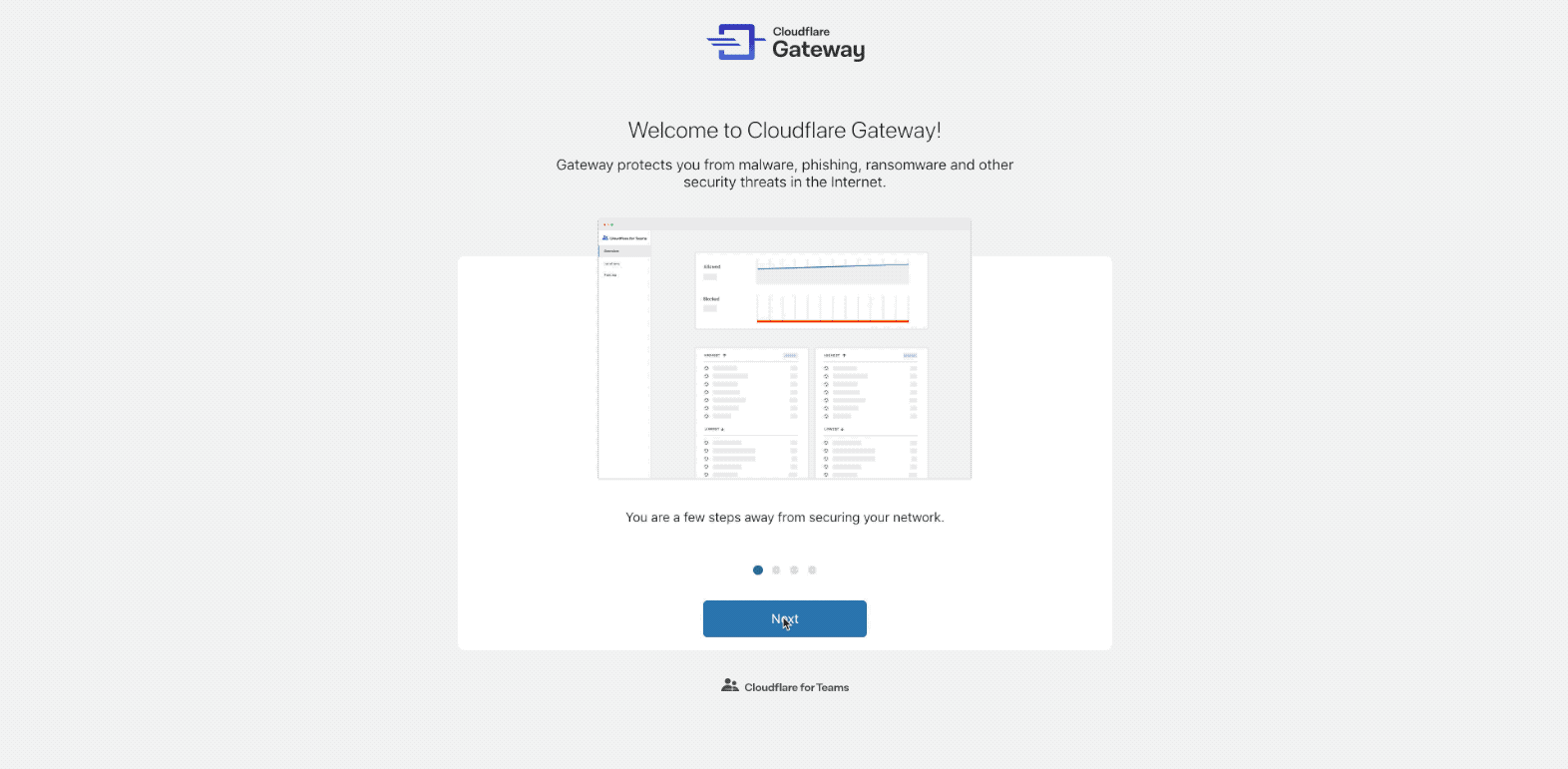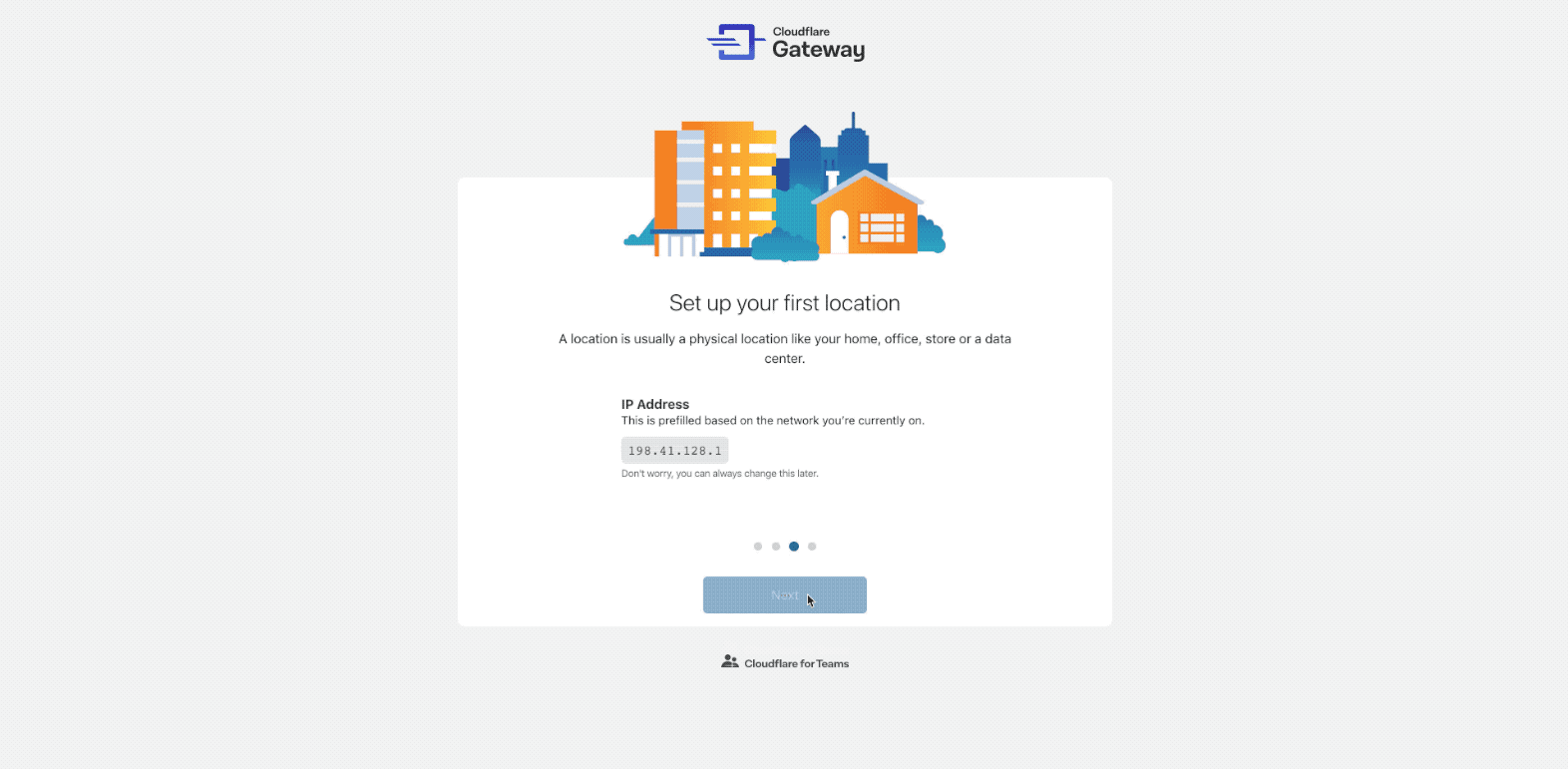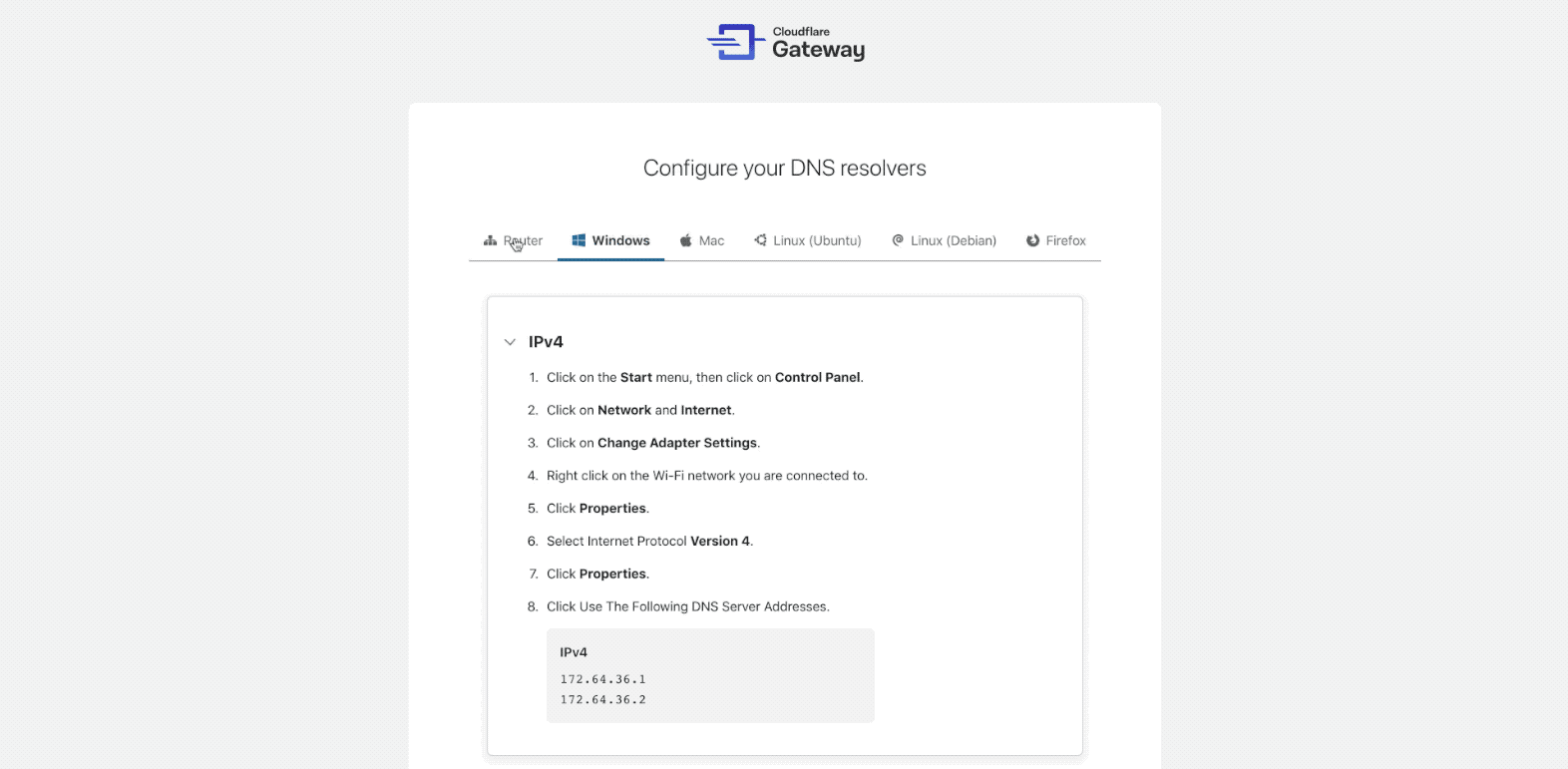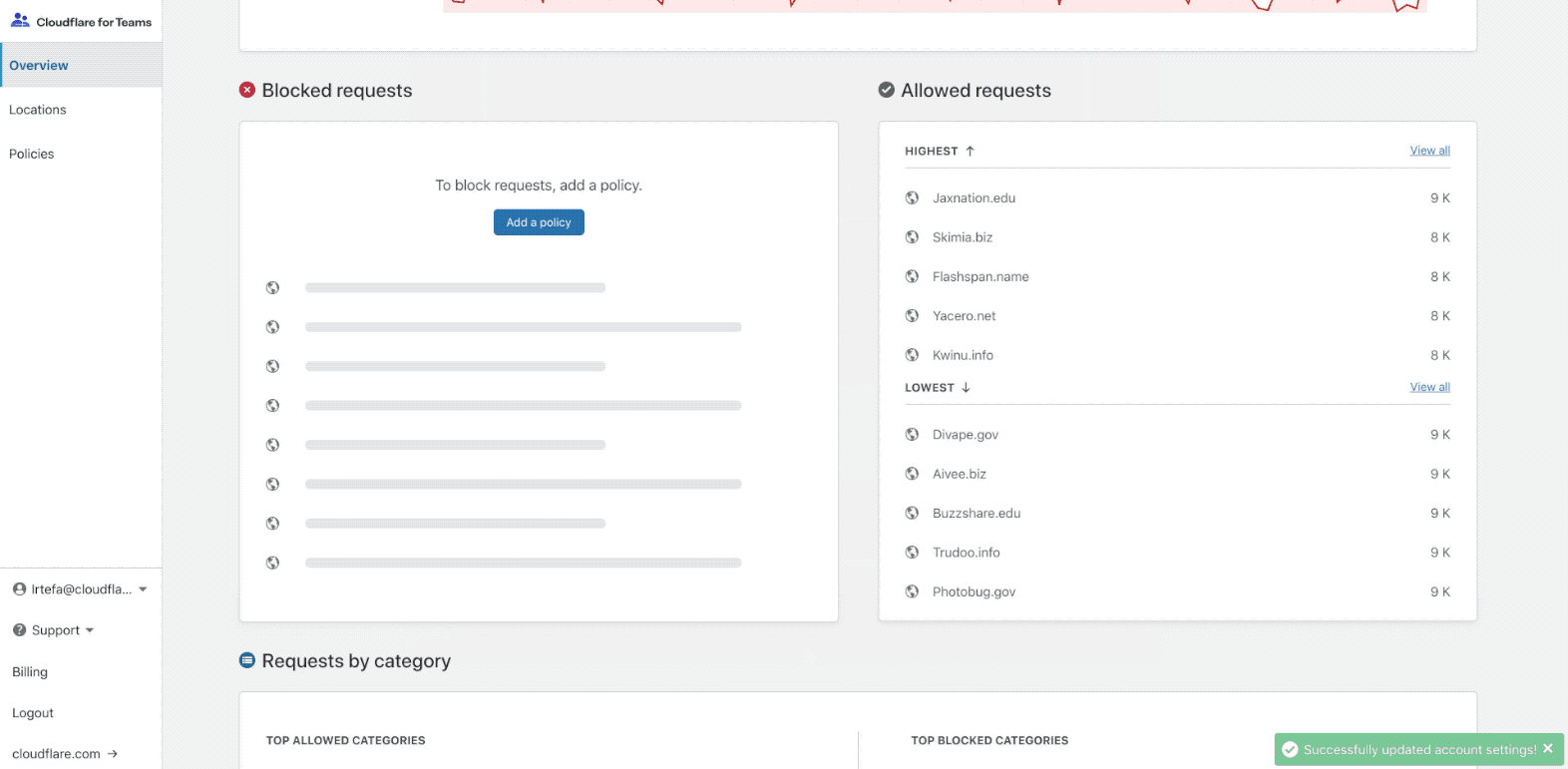
If you are using Gateway for the first time, the dashboard will take you through an onboarding experience:
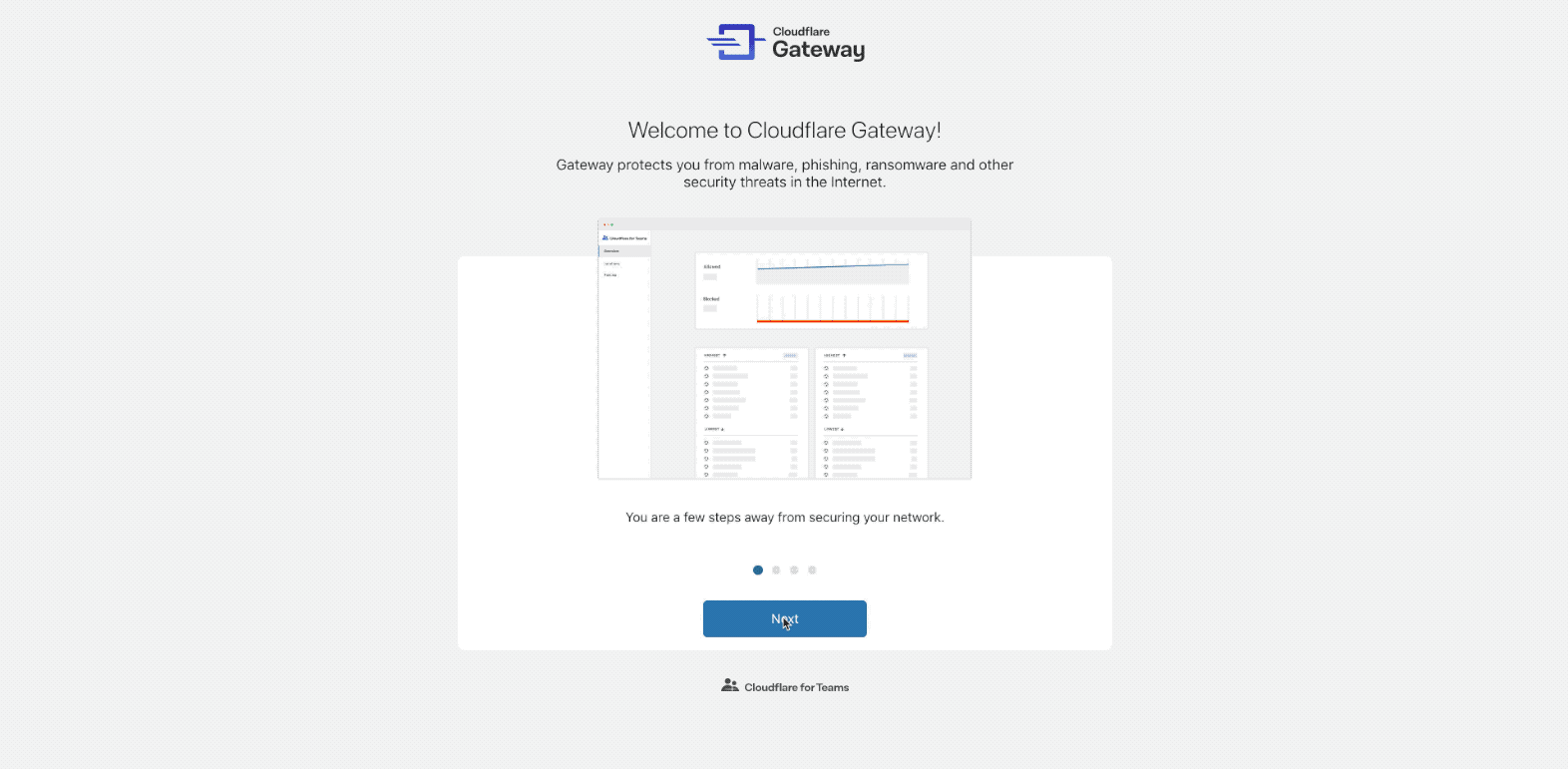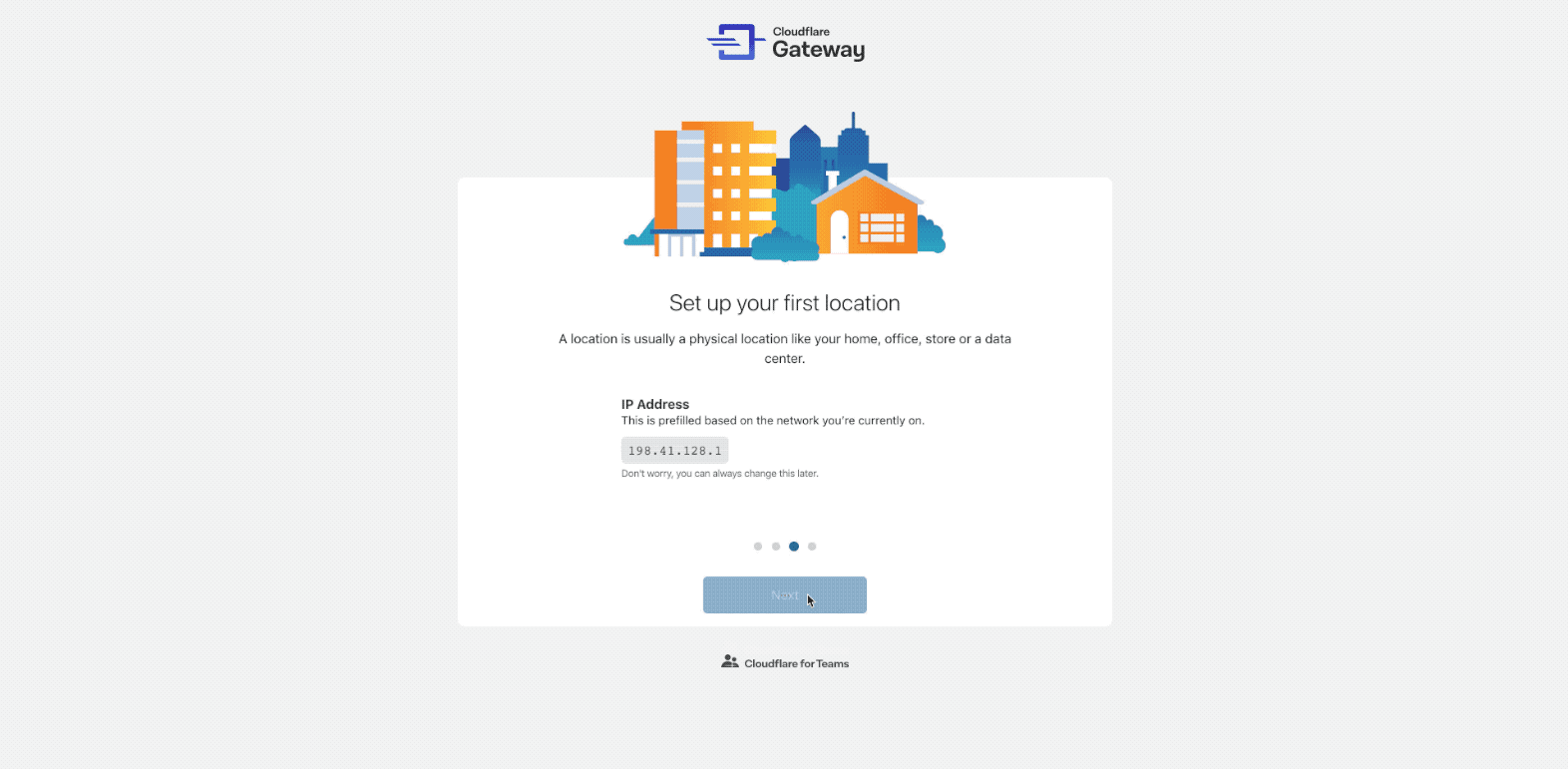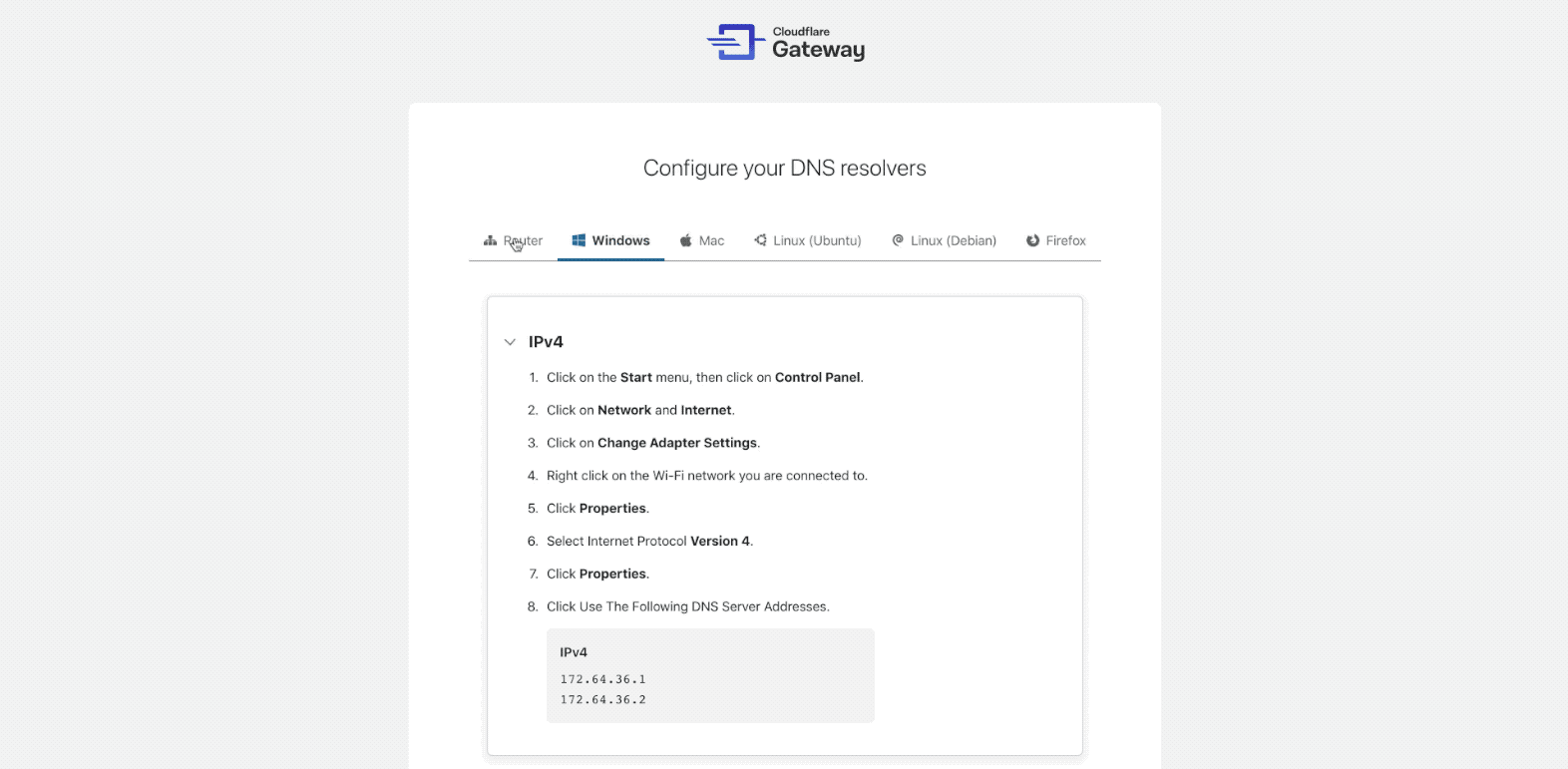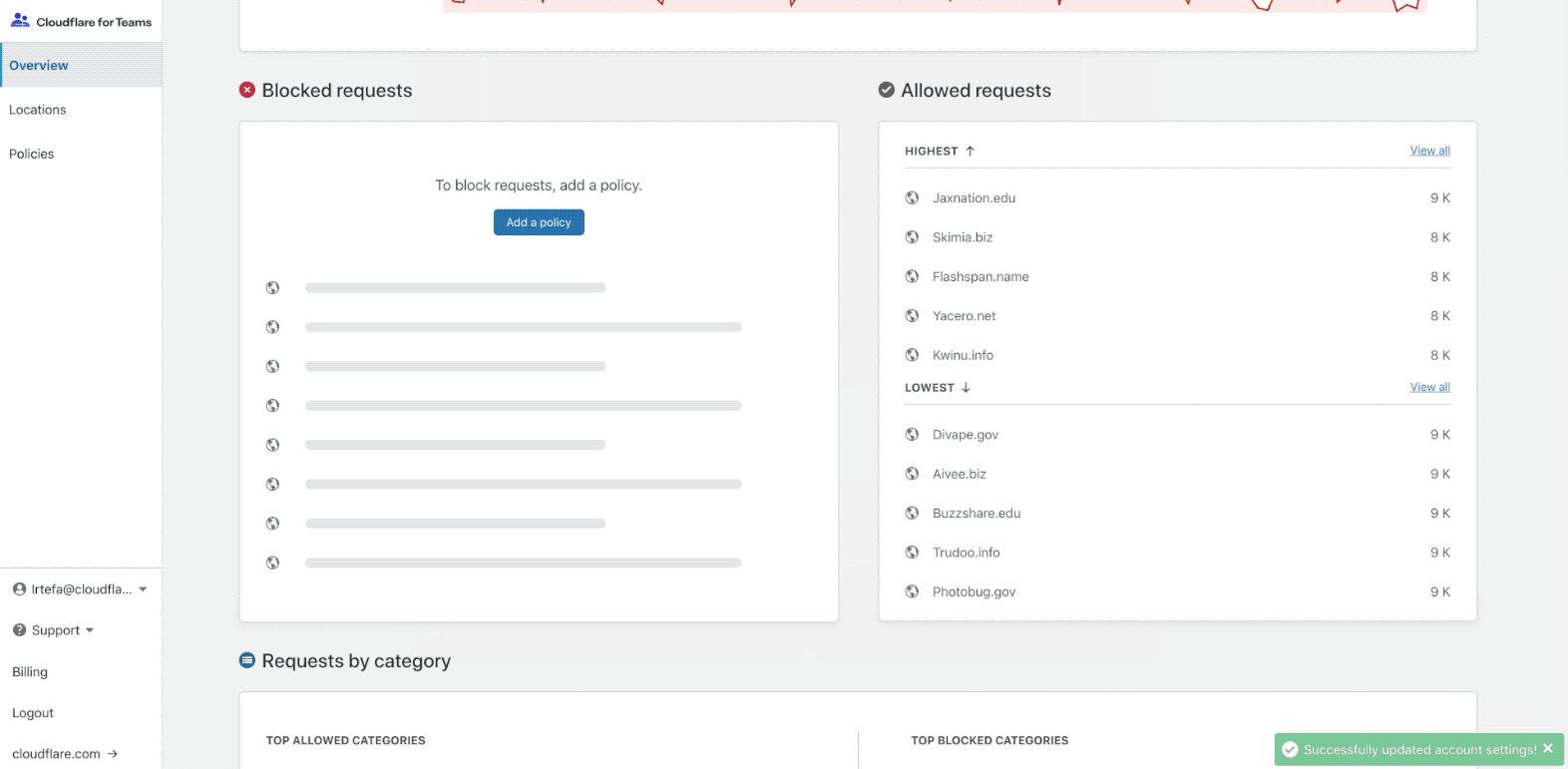
The onboarding flow will help you set up your first location. A location is Continue reading