HashiCorp Scores $175M Funding Round, $5B Valuation
The company has posted a 100% year-over-year increase in revenue during the past four years, and...
Announcing Network Analytics
Our Analytics Platform

Back in March 2019, we released Firewall Analytics which provides insights into HTTP security events across all of Cloudflare's protection suite; Firewall rule matches, HTTP DDoS Attacks, Site Security Level which harnesses Cloudflare's threat intelligence, and more. It helps customers tailor their security configurations more effectively. The initial release was for Enterprise customers, however we believe that everyone should have access to powerful tools, not just large enterprises, and so in December 2019 we extended those same enterprise-level analytics to our Business and Pro customers.

Since then, we’ve built on top of our analytics platform; improved the usability, added more functionality and extended it to additional Cloudflare services in the form of Account Analytics, DNS Analytics, Load Balancing Analytics, Monitoring Analytics and more.
Our entire analytics platform harnesses the powerful GraphQL framework which is also available to customers that want to build, export and share their own custom reports and dashboards.
Extending Visibility From L7 To L3
Until recently, all of our dashboards were mostly HTTP-oriented and provided visibility into HTTP attributes such as the user agent, hosts, cached resources, etc. This is valuable to customers that use Cloudflare to protect and accelerate HTTP Continue reading
FortiGuard Labs’ Derek Manky Talks Swarm Attacks, War of Deception
Collaboration and deception are two tools that Manky says should play a prominent role in...
Juniper Drives Kubernetes Into the Networking Conversation
The vendor has a twofold strategy to address multiple orchestration and enterprise challenges in...
SD-WAN Vendors Target SMBs as Competition Ramps Up
With at least 70 SD-WAN vendors on the market, standing out from the pack can be tricky. In an...
Weekly Wrap: Telia Taps Cisco Viptela SD-WAN
SDxCentral Weekly Wrap for March 13, 2020: The Sweden-based vendor cited Viptela's remote...
Cloudflare’s COVID-19 FAQs

As the status of COVID-19 continues to impact people and businesses around the world, Cloudflare is committed to providing awareness and transparency to our customers, employees, and partners about how we are responding. We do not anticipate any significant disruptions in Cloudflare services.
Our Business Continuity Team is monitoring the situation closely and all company personnel are kept up to date via multiple internal communication channels including a live chat room. Customers and the public are encouraged to visit this blog post for the latest information.
You can check the status of our network at www.cloudflarestatus.com. For COVID-19-related questions that aren’t answered below, please contact our Customer Support Team.
Does Cloudflare have a Business Continuity Team (BCT)?
Yes, Cloudflare’s Business Continuity Team is a cross-functional, geographically diverse group dedicated to navigating through a health crisis like COVID-19 as well as a variety of other scenarios that may impact employee safety and business continuity.
What is Cloudflare’s Business Continuity Plan in the light of COVID-19?
In addition to Cloudflare’s existing Disaster Recovery Plan we have implemented the following strategies:
- Daily Business Continuity Team meetings to determine if updates, changes, or communication need to be provided to customers, partners, and Continue reading
Cloudflare During the Coronavirus Emergency

This email was sent to all Cloudflare customers a short while ago
From: Matthew Prince
Date: Thu, Mar 12, 2020 at 4:20 PM
Subject: Cloudflare During the Coronavirus Emergency
We know that organizations and individuals around the world depend on Cloudflare and our network. I wanted to send you a personal note to let you know how Cloudflare is dealing with the Coronavirus emergency.
First, the health and safety of our employees and customers is our top priority. We have implemented a number of sensible policies to this end, including encouraging many employees to work from home. This, however, hasn't slowed our operations. Our network operations center (NOC), security operations center (SOC), and customer support teams will remain fully operational and can do their jobs entirely remote as needed.
Second, we are tracking Internet usage patterns globally. As more people work from home, peak traffic in impacted regions has increased, on average, approximately 10%. In Italy, which has imposed a nationwide quarantine, peak Internet traffic is up 30%. Traffic patterns have also shifted so peak traffic is occurring earlier in the day in impacted regions. None of these traffic changes raise any concern for us. Cloudflare's network is well provisioned Continue reading
Daily Roundup: AT&T Touts 5G Lead
AT&T peddled its 5G lead; AWS launched Bottlerocket Container OS; and Splunk made security...
Splunk Makes Security Hygiene Sexy Again
“Vulnerability management, configuration management, patch management — those things should...
Protect your team with Cloudflare Gateway

On January 7th, we announced Cloudflare for Teams, a new way to protect organizations and their employees globally, without sacrificing performance. Cloudflare for Teams centers around two core products - Cloudflare Access and Cloudflare Gateway. Cloudflare Access is already available and used by thousands of teams around the world to secure internal applications. Cloudflare Gateway solves the other end of the problem by protecting those teams from security threats without sacrificing performance.
Today, we’re excited to announce new secure DNS filtering capabilities in Cloudflare Gateway. Cloudflare Gateway protects teams from threats like malware, phishing, ransomware, crypto-mining and other security threats. You can start using Cloudflare Gateway at dash.teams.cloudflare.com. Getting started takes less than five minutes.
Why Cloudflare Gateway?
We built Cloudflare Gateway to address key challenges our customers experience with managing and securing global networks. The root cause of these challenges is architecture and inability to scale. Legacy network security models solved problems in the 1990s, but teams have continued to attempt to force the Internet of the 2020s through them.
Historically, branch offices sent all of their Internet-bound traffic to one centralized data center at or near corporate headquarters. Administrators configured that to make sure all Continue reading
Orange, Riverbed, Nuage Chat SD-WAN Pitfalls, Opportunities
And some agreed that despite the SD-WAN's advantages, MPLS wasn't going anywhere.
Microsoft Leads Massive Necurs Botnet Takedown
Between 2016 and 2019, Necurs was the most prominent spam and malware-delivery method and was...
Money Moves: February 2020
HPE buys Scytale, embraces open source security; Intel ditches Nervana, high on Habana; plus the...
Open sourcing our Sentry SSO plugin
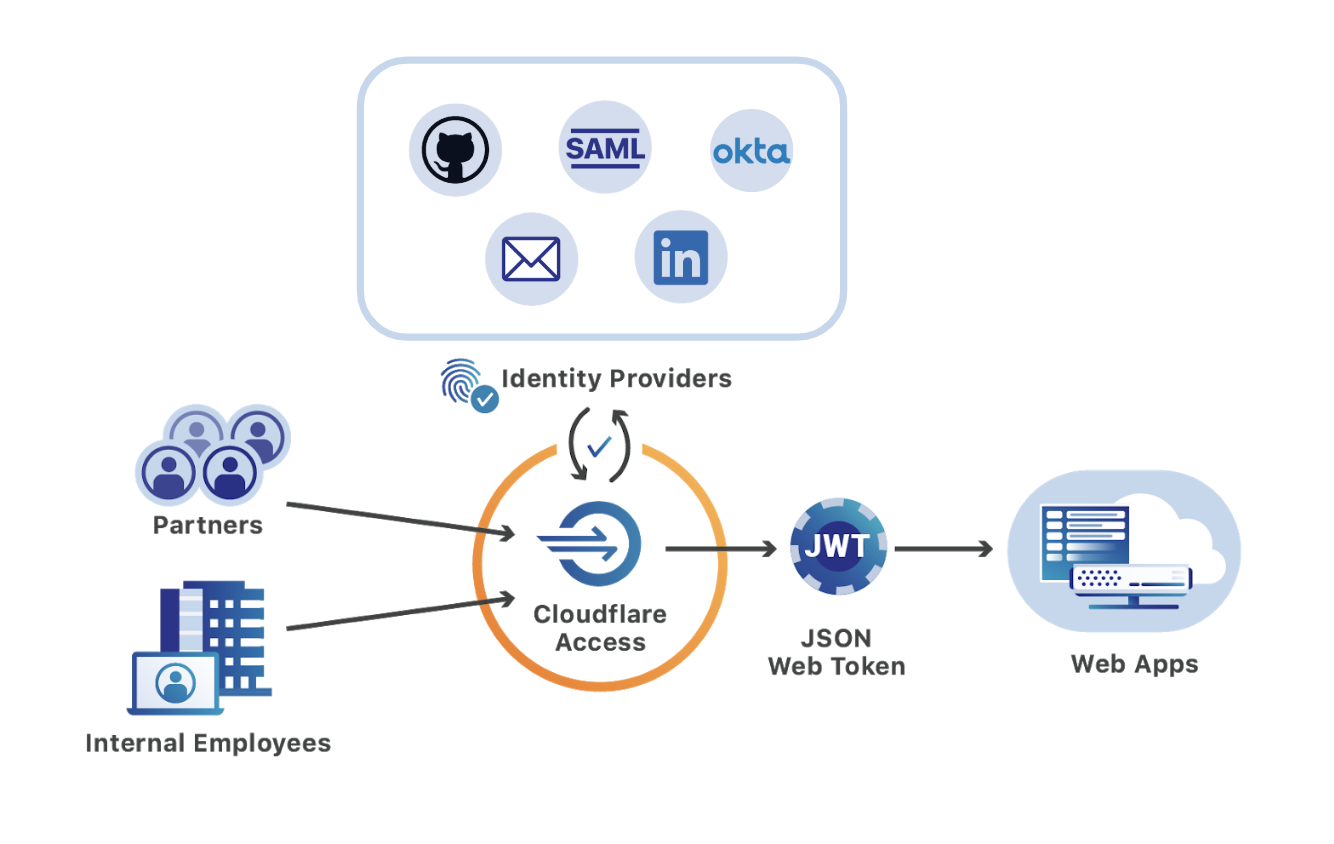
Cloudflare Access, part of Cloudflare for Teams, replaces legacy corporate VPNs with Cloudflare’s global network. Using your existing identity provider, Access enables your end users to login from anywhere — without a clunky agent or traffic backhaul through a centralized appliance or VPN.
Today, we are open sourcing a plugin that continues to improve that experience by making it easier for teams to use Cloudflare Access with one of the software industry’s most popular engineering tools, Sentry.
What is Sentry?
Sentry is an application that helps software teams find and diagnose errors in their products. We use Sentry here at Cloudflare. When you encounter an error when using a Cloudflare product, like our dashboard, we log that event. We then use Sentry to determine what went wrong.
Sentry can categorize and roll up errors, making it easy to identify new problems before investigating them with the tool’s event logging. Engineering managers here can use the dashboards to monitor the health of a new release. Product managers often use those reports as part of prioritizing what to fix next. Engineers on our team can dig into the individual errors as they release a fix.
Sentry is available in two forms: Continue reading
How Replicated Developers Develop Remotely

This is a guest post by Marc Campbell and Grant Miller, co-founders of Replicated.

Replicated is a 5-year old infrastructure software company working to make it easy for businesses to install and operate third party software. We don’t want you to have to send your data to a multi-tenant SaaS provider just to use their services. Our team is made up of twenty-two people distributed throughout the US. One thing that’s different about Replicated is our developers don’t actually store or execute code on their laptops; all of our development happens on remote instances in the cloud.
Our product, KOTS, runs in Kubernetes and manages the lifecycle of 3rd-party applications in the Kubernetes cluster. Building and validating the product requires a developer to have access to a cluster. But as we started to hire more and more engineers it became ridiculous to ask everyone to run their own local Kubernetes cluster. We needed to both simplify and secure our setup to allow every engineer to run their environment in the cloud, and we needed to do it in a way which was seamless and secure.
Previous Dev Environments with Docker for Mac
We started with each developer building Continue reading
How to Build a Highly Productive Remote Team (or Team of Contractors) with Cloudflare for Teams

Much of IT has been built on two outdated assumptions about how work is done. First, that employees all sit in the same building or branch offices. Second, that those employees will work full-time at the same company for years.
Both of these assumptions are no longer true.
Employees now work from anywhere. In the course of writing this blog post, I opened review tickets in our internal JIRA from my dining table at home. I reviewed internal wiki pages on my phone during my commute on the train. And I spent time reviewing some marketing materials in staging in our CMS.
In a past job, I would have suffered trying to connect to these tools through a VPN. That would have slowed down my work on a laptop and made it nearly impossible to use a phone to catch up on my commute.
The second challenge is ramp-up. I joined Cloudflare a few months ago. As a member of the marketing team, I work closely with our product organization and there are several dozen tools that I need to do that.
I’m hardly alone. The rise of SaaS and custom internal applications means that employees need access to all Continue reading
Mighty Morphin HPE Unleashes Container Platform
Tom Phelan, a fellow for big data and storage organization at HPE, said the container platform’s...
Postcard From San Francisco (RSAC 2020)
There was plenty to see and hear at this years RSA conference, not the least of which was the VMware announcement of a modern data center security solution for today’s private and public clouds
I can report there was brisk business at the the booth with plenty of questions on our solution. Booth duty is not everyone’s favorite but I always look forward to the opportunity to hear directly from customers. There are often questions we don’t have the answers to, but it helps us keep our focus in the areas that matter the most.
My colleague Vivek has already done a fantastic job blogging on our intrinsic security story and our announcements at this year’s event. I wanted to share some great explainer videos from our executive team.
Unshackle Legacy Security Restrictions for 2020 and Beyond
In this 20 minute video, Part#1, Tom Gillis, VMware SVP/GM of Networking and Security, covers how new data center and branch security approaches can prevent attacks in the enterprise.
Part#2 is a live demonstration of how to protect lateral traffic in the DC
In this second of two 20 minute videos, Tom is joined onstage by Continue reading
Microsoft, Intel, Fortanix Execs Get Confidential at RSA
“Confidential computing is one of the most important and relevant new paradigms that you folks...