OCP Blesses AT&T’s Disaggregated Security Architecture Push
This programmable fabric with embedded security functions will allow network operators to deploy...
Intel Vulnerability Serious But Unlikely, Experts Say
The bug would allow an attacker to exploit a known vulnerability in Intel's CSME to gain access to...
How Cloudflare keeps employees productive from any location

Cloudflare employs more than 1,200 people in 13 different offices and maintains a network that operates in 200 cities. To do that, we used to suffer through a traditional corporate VPN that backhauled traffic through a physical VPN appliance. It was, frankly, horrible to work with as a user or IT person.
With today’s mix of on-prem, public cloud and SaaS and a workforce that needs to work from anywhere, be it a coffee shop or home, that model is no longer sustainable. As we grew in headcount, we were spending too much time resolving VPN helpdesk tickets. As offices around the world opened, we could not ask our workforce to sit as every connection had to go back through a central location.
We also had to be ready to scale. Some organizations are currently scrambling to load test their own VPN in the event that their entire workforce needs to work remotely during the COVID-19 outbreak. We could not let a single physical appliance constrain our ability to deliver 26M Internet properties to audiences around the world.
To run a network like Cloudflare, we needed to use Cloudflare’s network to stay fast and secure.
We built Cloudflare Access, part Continue reading
Huawei backdoors explanation, explained
Today Huawei published a video explaining the concept of "backdoors" in telco equipment. Many are criticizing the video for being tone deaf. I don't understand this concept of "tone deafness". Instead, I want to explore the facts.Does the word “#backdoor” seem frightening? That’s because it’s often used incorrectly – sometimes to deliberately create fear. Watch to learn the truth about backdoors and other types of network access. #cybersecurity pic.twitter.com/NEUXbZbcqw— Huawei (@Huawei) March 4, 2020
This video seems in response to last month's story about Huawei misusing law enforcement backdoors from the Wall Street Journal. All telco equipment has backdoors usable only by law enforcement, the accusation is that Huawei has a backdoor into this backdoor, so that Chinese intelligence can use it.
That story was bogus. Sure, Huawei is probably guilty of providing backdoor access to the Chinese government, but something is deeply flawed with this particular story.
We know something is wrong with the story because the U.S. officials cited are anonymous. We don't know who they are or what position they have in the government. If everything they said was true, they wouldn't insist on being anonymous, but would stand up Continue reading
Weekly Wrap: AT&T Puts More Jobs on the Chopping Block
SDxCentral Weekly Wrap for March 6, 2020: The telecom giant cited "headcount rationalization" as a...
Verizon Boosts Security With Blockchain, Adds MDR
One of the services encrypts and replicates identity data across multiple online servers on the...
Headcount: Firings, Hirings, and Retirings — February 2020
SAP revamped org structure, exited 2 board members; Intel slashed jobs despite record quarter; plus...
4 Ways SD-Branch Is Transforming Retail Networks
Retail SD-branch can help a business retain customers, offer them better service, and increase...
A requirements spec for voting
In software development, we start with a "requirements specification" defining what the software is supposed to do. Voting machine security is often in the news, with suspicion the Russians are trying to subvert our elections. Would blockchain or mobile phone voting work? I don't know. These things have tradeoffs that may or may not work, depending upon what the requirements are. I haven't seen the requirements written down anywhere. So I thought I'd write some.One requirement is that the results of an election must seem legitimate. That's why responsible candidates have a "concession speech" when they lose. When John McCain lost the election to Barack Obama, he started his speech with:
"My friends, we have come to the end of a long journey. The American people have spoken, and they have spoken clearly. A little while ago, I had the honor of calling Sen. Barack Obama — to congratulate him on being elected the next president of the country that we both love."This was important. Many of his supporters were pointing out irregularities in various states, wanting to continue the fight. But there are always irregularities, or things that look like irregularities. In every election, if a Continue reading
Pwned Passwords Padding (ft. Lava Lamps and Workers)
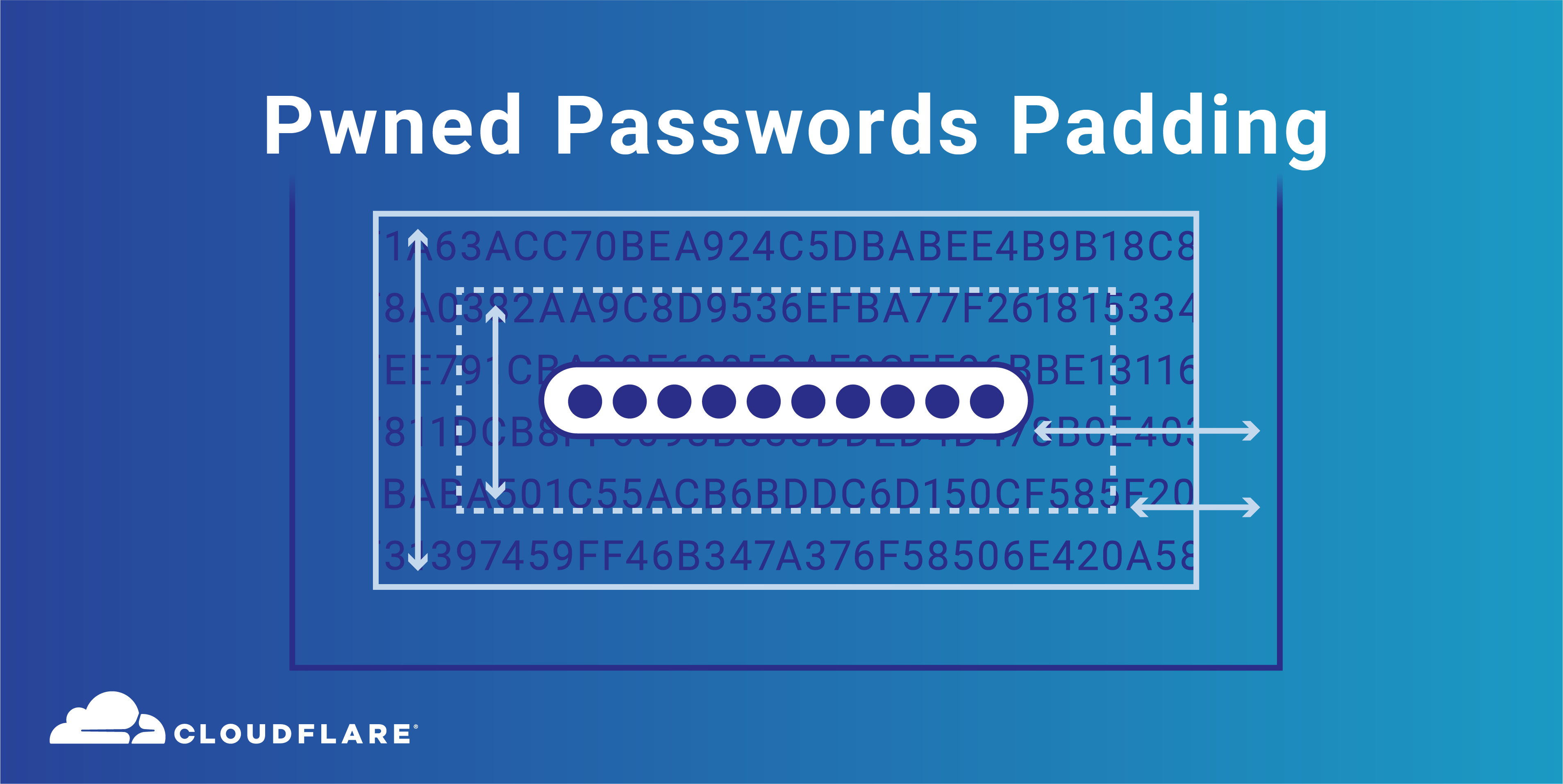
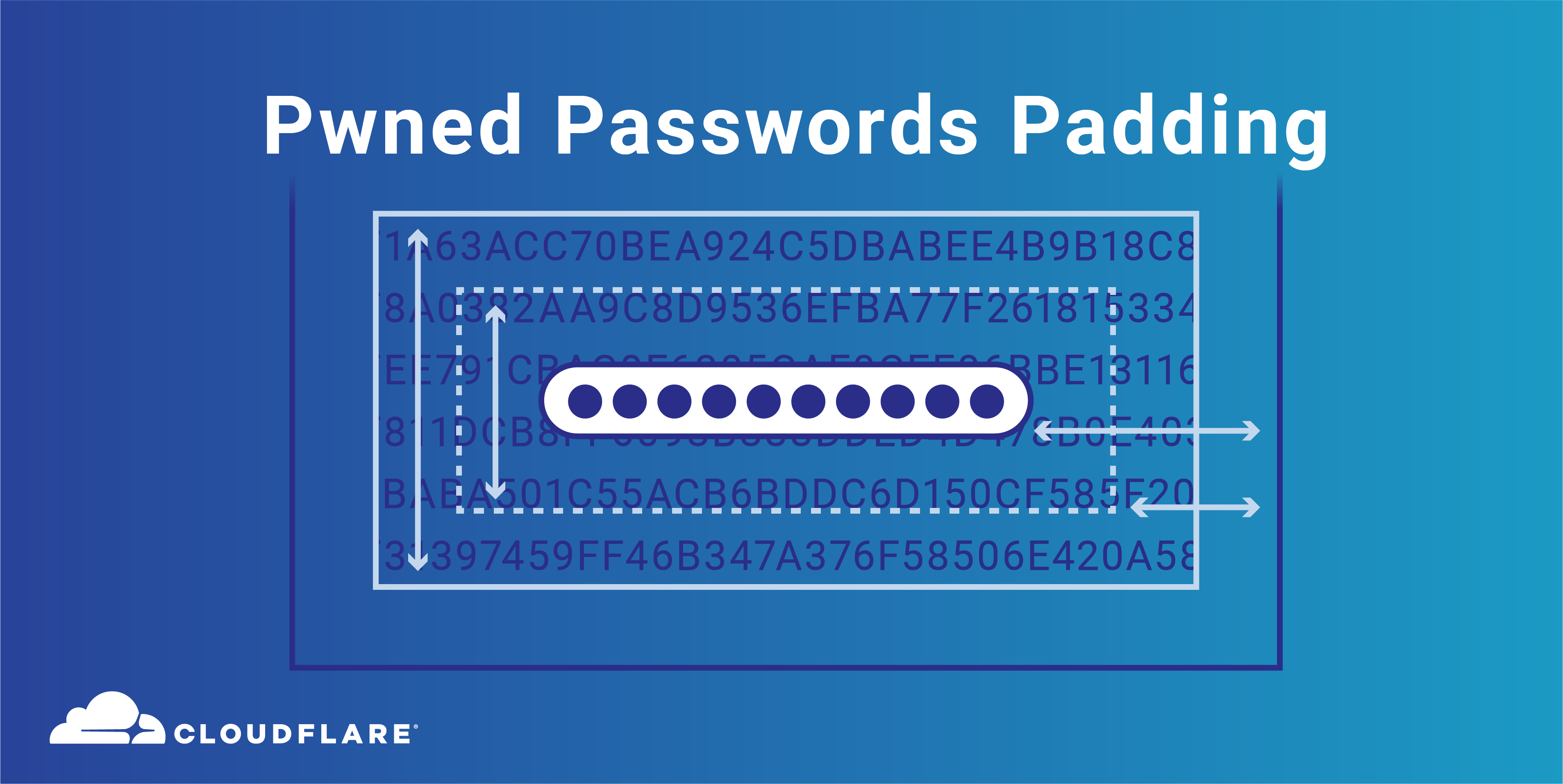
The Pwned Passwords API (part of Troy Hunt’s Have I Been Pwned service) is used tens of millions of times each day, to alert users if their credentials are breached in a variety of online services, browser extensions and applications. Using Cloudflare, the API cached around 99% of requests, making it very efficient to run.
From today, we are offering a new security advancement in the Pwned Passwords API - API clients can receive responses padded with random data. This exists to effectively protect from any potential attack vectors which seek to use passive analysis of the size of API responses to identify which anonymised bucket a user is querying. I am hugely grateful to security researcher Matt Weir who I met at PasswordsCon in Stockholm and has explored proof-of-concept analysis of unpadded API responses in Pwned Passwords and has driven some of the work to consider the addition of padded responses.
Now, by passing a header of “Add-Padding” with a value of “true”, Pwned Passwords API users are able to request padded API responses (to a minimum of 800 entries with additional padding of a further 0-200 entries). The padding consists of randomly generated hash suffixes with the usage Continue reading
Did We Just Attend the Last Trade Show Ever at RSA?
Security professionals tend to be at least a moderately paranoid bunch, and adding a real virus to...
Rakuten Mobile Dismisses Open RAN Skeptics
The open RAN framework is 40% cheaper than traditional telecommunication infrastructure, according...
Claris Rides Apple Hook for Low-Code Nirvana
The low-code vendor is Apple's only direct software play in the B2B space.
Daily Roundup: Nokia CEO Walks the Plank
Nokia CEO walked the plank; VMware's winning streak came to a screeching halt; and Marvell injected...
Cisco’s Wendy Nather: Never Say This to a CISO
When Cisco acquired Duo Security, Nather’s was the only CISO advisory team. Cisco quickly saw the...
Marvell Injects New Life Into Infrastructure Chips
The chips are designed to power networking equipment like switches, routers, secure gateways,...
SDxCentral’s Top 10 Articles — February 2020
SAP revamps organizational structure, exits 2 board members; coronavirus kills MWC Barcelona; and...
Technical Details of Why Cloudflare Chose AMD EPYC for Gen X Servers

From the very beginning Cloudflare used Intel CPU-based servers (and, also, Intel components for things like NICs and SSDs). But we're always interested in optimizing the cost of running our service so that we can provide products at a low cost and high gross margin.
We're also mindful of events like the Spectre and Meltdown vulnerabilities and have been working with outside parties on research into mitigation and exploitation which we hope to publish later this year.
We looked very seriously at ARM-based CPUs and continue to keep our software up to date for the ARM architecture so that we can use ARM-based CPUs when the requests per watt is interesting to us.

In the meantime, we've deployed AMD's EPYC processors as part of Gen X server platform and for the first time are not using any Intel components at all. This week, we announced details of this tenth generation of servers. Below is a recap of why we're excited about the design, specifications, and performance of our newest hardware.
Servers for an Accelerated Future
Every server can run every service. This architectural decision has helped us achieve higher efficiency across the Cloudflare network. It has also given us more Continue reading
VMware Suffers Operational Indigestion
The company began to lose momentum coming out of its latest fiscal year in which it made 10...
Daily Roundup: Huawei CSO Mocks US Security Policy
Huawei CSO mocked US security policy; Palo Alto Networks added X factor to $560M Demisto buy; and...