Mellanox ConnectX-6 SmartNIC Arrives, BlueField-2 on the Way
Mellanox, which is being acquired by Nvidia in a $6.9 billion deal, announced the pair of SmartNICs...
Security that’s Designed for the Modern Data Center
The last 12 months have been incredibly exciting for the security business at VMware. Last year at RSA Conference 2019, VMware CEO Pat Gelsinger outlined our Intrinsic Security strategy in his keynote presentation, “3 Things the Security Industry Isn’t Talking About”. We also announced the VMware Service-defined Firewall, a stateful Layer 7 data center firewall. As pioneers of micro-segmentation, the Service-defined Firewall extended our leadership in protecting east-west traffic in the data center.
Later in the year, we announced two major acquisitions –Avi Networks and Carbon Black. The acquisition of Carbon Black brought to VMware an industry-leading endpoint security platform, and made the entire industry take notice of VMware’s intentions to transform security. With Avi Networks, we acquired a software-defined, elastic, and high-performance load balancer that comes equipped with a full-featured web application firewall (WAF). Maintaining the momentum in building out our security portfolio for the digital enterprise, we announced the VMware NSX Distributed Intrusion Detection and Prevention System which will bring advanced threat controls to the Service-defined Firewall.
At RSA Conference 2020, we are introducing VMware Advanced Security for Cloud Foundation, a modern data center security solution for today’s private and public clouds. This solution will include VMware Carbon Continue reading
Fortinet Forges FortiAI Security Service
The service utilizes a "self-learning" deep neural network to automate rote security tasks to...
Daily Roundup: Cisco SecureX All-In on Cloud Native
Cisco went all-in on cloud-native security with SecureX; AT&T joined Open Cybersecurity...
Seamless remote work with Cloudflare Access
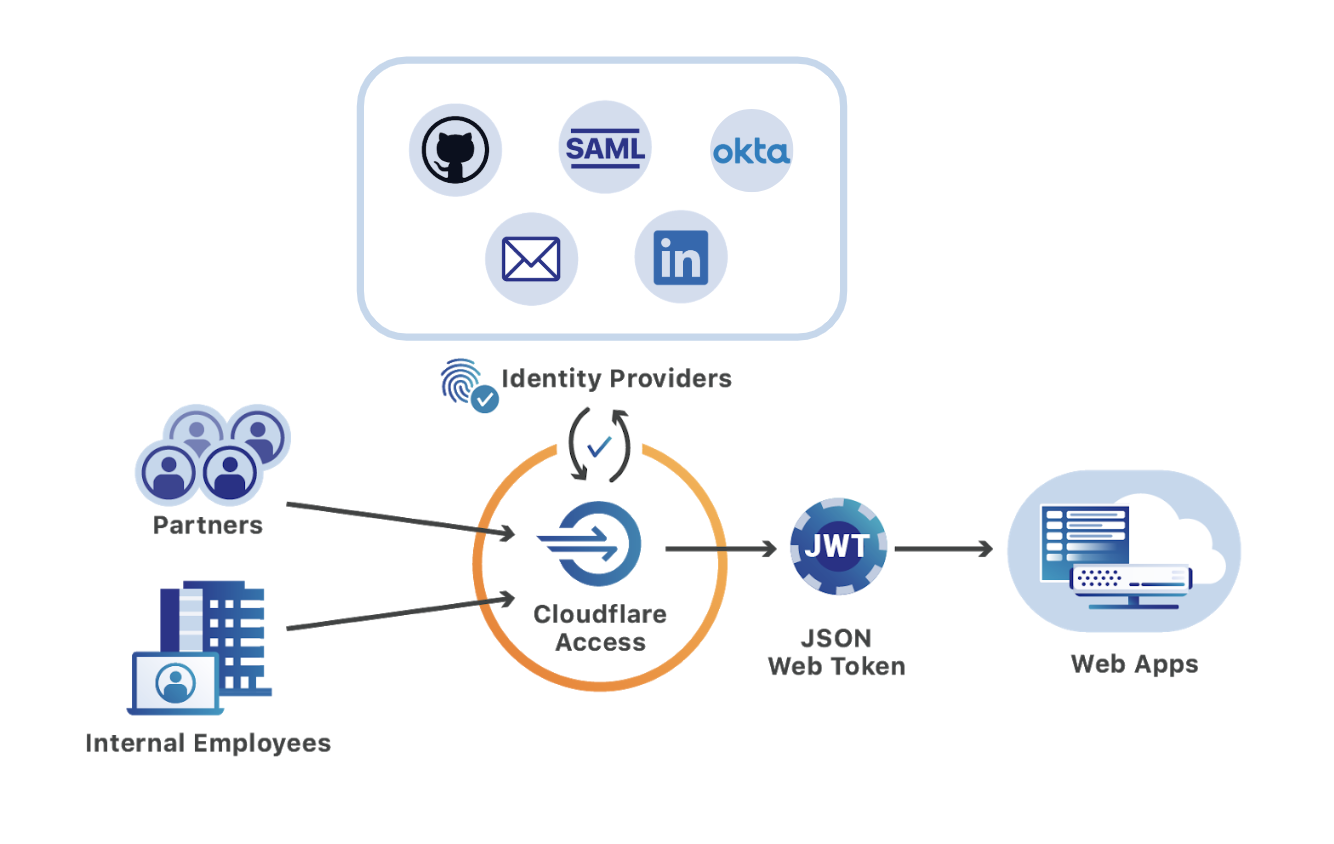
The novel coronavirus is actively changing how organizations work in real-time. According to Fortune, the virus has led to the “world’s largest work-from-home experiment.” As the epidemic crosses borders, employees are staying home and putting new stress on how companies manage remote work.
This is only accelerating an existing trend, however. Remote work has gained real traction in the last decade and Gartner projects that it will only continue. However, teams which are moving to a distributed model tend to do so slowly. When those timelines are accelerated, IT and security administrators need to be able to help their workforce respond without disrupting their team members.
Cloudflare Access can help teams migrate to a model that makes it seamless for users to work from any location, or any device, without the need for lengthy migrations or onboarding sessions. Cloudflare Access can be deployed in less than one hour and bring SaaS-like convenience and speed to the self-hosted applications that previously lived behind a VPN.
Leaving the castle-and-moat
When users share a physical space, working on a private network is easy. Users do not need clunky VPN clients to connect to the resources they need. Team members physically sit close Continue reading
Verizon Warns of Rising Enterprise Mobile Security Risk
The operator’s third annual survey on mobile security concluded that 43% of respondents believe...
Cisco SecureX Unifies Network, Cloud, Endpoint Security
Cisco’s 2020 CISO Benchmark Study found that 28% of security professionals say that managing a...
RSA Caps Chronicle’s Rollercoaster Ride to Google Cloud
At the annual security event, Google Cloud rolled out new security features including threat...
Juniper Fuses AI, Connected Security at RSA
It’s also getting a little bit SASE with its secure SD-WAN, but executives say they’ll talk...
AT&T, Raytheon, Armis Join Open Cybersecurity Alliance
The group also today made available OpenDXL Ontology, which it says is the first open source...
The Big Trends That Were set to Shape MWC Barcelona
The event might not be happening, but that doesn't mean we are going to ignore the big trends we...
Kubernetes Security Plagued by Human Error, Misconfigs
Exposures and data breaches due to misconfigurations have become an “alarmingly common” trend...
Cisco Viptela Joins ConvergeOne’s SD-WAN Lineup
The announcement marks Cisco's second service provider announcement in the past month.
Using your devices as the key to your apps
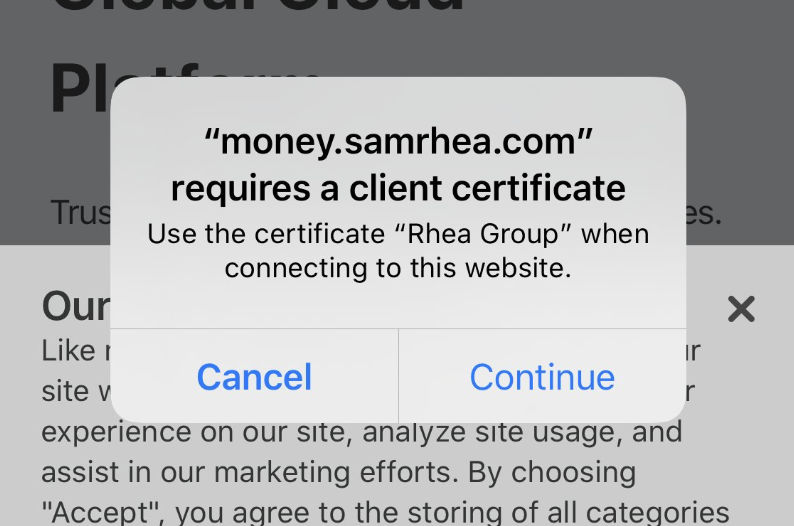
I keep a very detailed budget. I have for the last 7 years. I manually input every expense into a spreadsheet app and use a combination of sumifs functions to track spending.
Opening the spreadsheet app, and then the specific spreadsheet, every time that I want to submit an expense is a little clunky. I'm working on a new project to make that easier. I'm building a simple web app, with a very basic form, into which I will enter one-off expenses. This form will then append those expenses as rows into the budget workbook.
I want to lock down this project; I prefer that I am the only person with the power to wreck my budget. To do that, I'm going to use Cloudflare Access. With Access, I can require a login to reach the page - no server-side changes required.
Except, I don't want to allow logins from any device. For this project, I want to turn my iPhone into the only device that can reach this app.
To do that, I'll use Cloudflare Access in combination with an open source toolkit from Cloudflare, cfssl. Together, I can convert my device into a secure key for this application Continue reading
Weekly Wrap: Dell Sells RSA Security Biz for $2 Billion
SDxCentral Weekly Wrap for Feb. 21, 2020: The RSA deal includes the upcoming RSA security...
Why TIA Calls Supply Chain Security the ‘Most Critical Global Telecom Issue’
The industry group recently launched an initiative to develop telecommunications supply chain...
Banks and the Digital Revolution: Can this arranged marriage lead to love?
Networks at financial branches like banks require high security, low latency and constant...
Huawei Fails to Reverse Federal Ban
"Contracting with the federal government is a privilege, not a constitutionally guaranteed right,"...
Fortinet Firewall Update Tames 5G, IoT ‘Elephant Flows’
The company claims the appliance is capable of simultaneously juggling millions of connections per...
Daily Roundup: Dell Sells RSA, Bags $2B
Dell bagged $2B with the sale of RSA; AT&T shared threat intelligence; and Orange teamed up...