Iran Cyberattacks Targeting US Companies Imminent, Experts Warn
“Beginning in the next 24 hours you will see cyberattacks manifesting as a harbinger for kinetics...
Deep Dive: How Does the Consumer Sector Score on Privacy and Security?

In April 2019 the Internet Society’s Online Trust Alliance released its 10th annual Online Trust Audit & Honor Roll. The Audit looks at the security and privacy practices of over 1,000 of the top sites on the Internet from retailers to government sites. In this post we will take a deeper dive into the Consumer section of the Audit. The Consumer section is a diverse set of sites including travel sites, hotels, and dating sites (see the methodology of the report for the full list).
In 2018 the Consumer section improved its standings with 85% making the honor roll, up from 76% in 2017. This was largely due to improvements in email security. Despite these gains in overall email security, TLS 1.3 adoption was actually down in 2018 (largely due to a change in the list of retail sites). Despite this OTA advocates the adoption of TLS 1.3.
Where these sites did stand out, compared to other sectors, was in privacy scores. Overall, the Consumer sector scored 43 out of 55 on their privacy tracker score, among the highest of any sector, and 33 out of 55 on their privacy statement, also among the highest.
The Consumer section Continue reading
Introducing Cloudflare for Teams
Ten years ago, when Cloudflare was created, the Internet was a place that people visited. People still talked about ‘surfing the web’ and the iPhone was less than two years old, but on July 4, 2009 large scale DDoS attacks were launched against websites in the US and South Korea.
Those attacks highlighted how fragile the Internet was and how all of us were becoming dependent on access to the web as part of our daily lives.
Fast forward ten years and the speed, reliability and safety of the Internet is paramount as our private and work lives depend on it.
We started Cloudflare to solve one half of every IT organization's challenge: how do you ensure the resources and infrastructure that you expose to the Internet are safe from attack, fast, and reliable. We saw that the world was moving away from hardware and software to solve these problems and instead wanted a scalable service that would work around the world.
To deliver that, we built one of the world's largest networks. Today our network spans more than 200 cities worldwide and is within milliseconds of nearly everyone connected to the Internet. We have built the capacity to stand Continue reading
Security on the Internet with Cloudflare for Teams


Your experience using the Internet has continued to improve over time. It’s gotten faster, safer, and more reliable. However, you probably have to use a different, worse, equivalent of it when you do your work. While the Internet kept getting better, businesses and their employees were stuck using their own private networks.
In those networks, teams hosted their own applications, stored their own data, and protected all of it by building a castle and moat around that private world. This model hid internally managed resources behind VPN appliances and on-premise firewall hardware. The experience was awful, for users and administrators alike. While the rest of the Internet became more performant and more reliable, business users were stuck in an alternate universe.
That legacy approach was less secure and slower than teams wanted, but the corporate perimeter mostly worked for a time. However, that began to fall apart with the rise of cloud-delivered applications. Businesses migrated to SaaS versions of software that previously lived in that castle and behind that moat. Users needed to connect to the public Internet to do their jobs, and attackers made the Internet unsafe in sophisticated, unpredictable ways - which opened up every business to a Continue reading
Cloudflare + Remote Browser Isolation
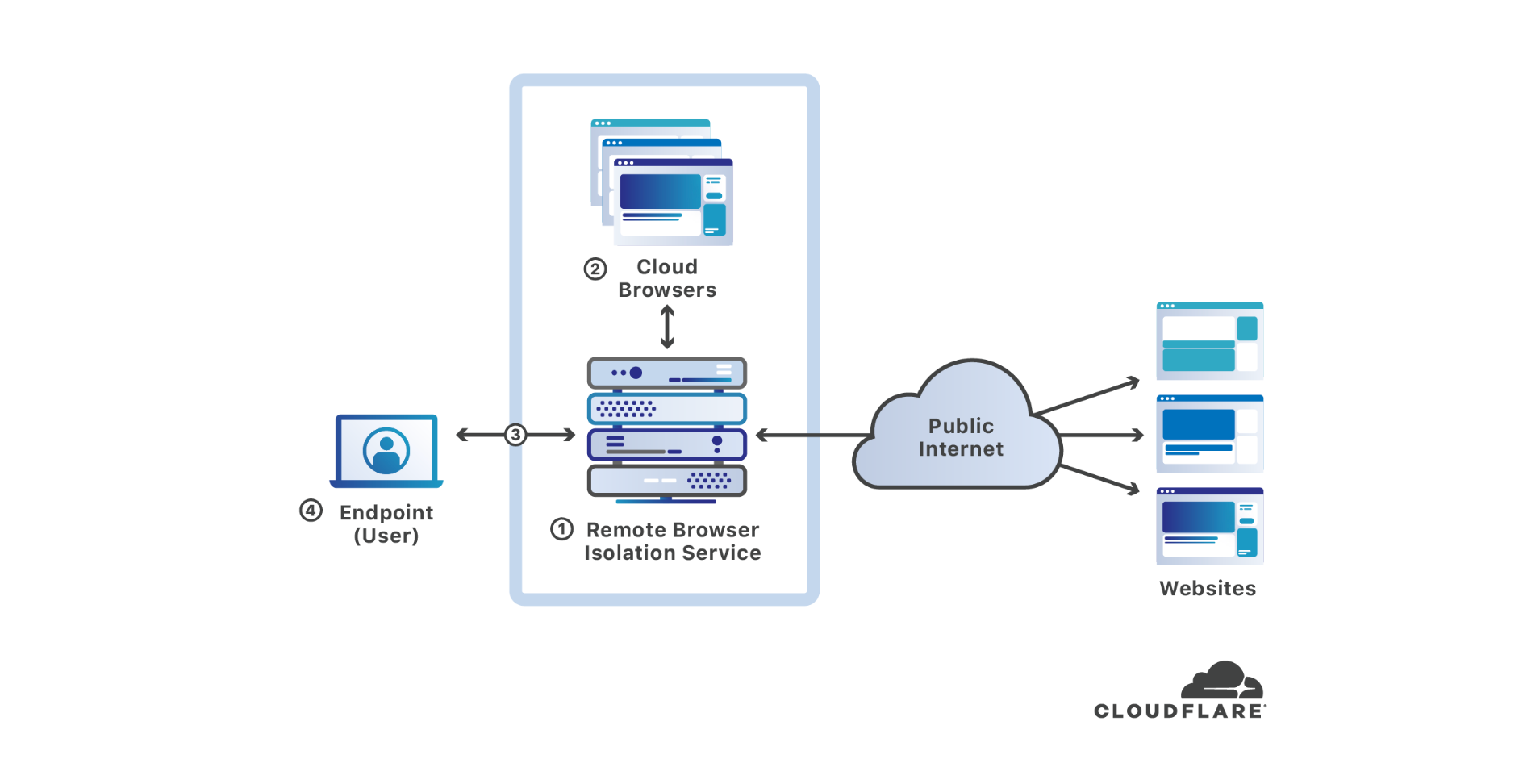
Cloudflare announced today that it has purchased S2 Systems Corporation, a Seattle-area startup that has built an innovative remote browser isolation solution unlike any other currently in the market. The majority of endpoint compromises involve web browsers — by putting space between users’ devices and where web code executes, browser isolation makes endpoints substantially more secure. In this blog post, I’ll discuss what browser isolation is, why it is important, how the S2 Systems cloud browser works, and how it fits with Cloudflare’s mission to help build a better Internet.
What’s wrong with web browsing?
It’s been more than 30 years since Tim Berners-Lee wrote the project proposal defining the technology underlying what we now call the world wide web. What Berners-Lee envisioned as being useful for “several thousand people, many of them very creative, all working toward common goals”[1] has grown to become a fundamental part of commerce, business, the global economy, and an integral part of society used by more than 58% of the world’s population[2].
The world wide web and web browsers have unequivocally become the platform for much of the productive work (and play) people do every day. However, as the pervasiveness Continue reading
Insight Scoops Up IoT Security Startup Armis for $1.1B
The deal marks the first cybersecurity acquisition of 2020, and it’s the largest-ever enterprise...
Cisco Patches More ‘Critical’ DCNM Flaws
The latest vulnerabilities are in the Data Center Network Manager authentication mechanism and...
Will Dell Technologies Fetch $3B for RSA?
Dell acquired the cybersecurity software company when it bought EMC in 2016. Since then it has...
Headcount: Firings, Hirings, and Retirings — December 2019
Juniper CTO Bikash Koley calls it quits; Larry Ellison says Oracle will not replace Hurd; plus the...
Security is a Glaring, Moving Target for IoT
“Security is one of the biggest factors limiting IoT expansion,” said Bill Curtis, resident...
How to Configure BurpSuite to use Tor as Proxy
BurpSuite is a manual toolkit for investigating web security. Burp Proxy allows manual testers to intercept all requests and responses between the browser and the target application, even when HTTPS is being used. The tutorial discusses configuration of Burp to use connection over Tor network. 1. BurpSuite Community Edition We can find BurpSuite Community Edition […]Continue reading...
Amazon Claims FedRAMP Compliance for a Spate of Services
Amazon claims to have bolstered its FedRAMP compliance by nearly 18% since the beginning of...
SDxCentral’s Top 10 Articles — December 2019
Aviatrix CEO: SD-WAN is dead. AWS killed it; Fortinet leapfrogs Cisco with 21,000 SD-WAN customers;...
Cisco’s 2019 was Flush With 5G, Security, and SD-WAN
The vendor used its clout over the past 12 months in continuing to bolster its position across...
Related Stories
Juniper SD-WAN Demo Lets Customers Try Before They Buy
The virtual tour will, however, require users to sign up for a 30-day trial of Juniper's Contrail...
SDxCentral’s Top 10 Articles of 2019
Aviatrix's CEO claimed SD-WAN is dead and that AWS killed it; VMware's CEO taunted IBM for paying...
So that tweet was misunderstood
I'm currently experiencing the toxic hell that is a misunderstood tweet going viral. It's a property of the social media. The more they can deliberately misunderstand you, the more they can justify the toxicity of their response. Unfortunately, I had to delete it in order to stop all the toxic crud and threats of violence.The context is how politicians distort everything. It's like whenever they talk about sea level rise, it's always about some city like Miami or New Orleans that is sinking into the ocean already, even without global warming's help. Pointing this out isn't a denial of global warming, it's pointing out how we can't talk about the issue without exaggeration. Mankind's carbon emissions are indeed causing sea level to rise, but we should be talking about how this affects average cities, not dramatizing the issue with the worst cases.
The same it true of health care. It's a flawed system that needs change. But we don't discuss the people making the best of all bad choices. Instead, we cherry pick those who made the worst possible choice, and then blame the entire bad outcome on the system.
My tweet is in response to this Elizabeth Warren Continue reading
Top 5 Cybersecurity Predictions for 2020
Grab your tinfoil hat and a champagne cocktail, snuggle up in front of a warm fireplace, and check...
‘What’s Dead May Never Die’ — SD-WAN’s Undying Story
Aviatrix CEO Steve Mullaney raised eyebrows earlier this month when he predicted the demise of the...
Huawei Battles Reigned in 2019
Huawei struck back at a report claiming the Chinese vendor benefitted from government subsidies...