MEF Presses Managed Security in SD-WAN
“SD-WAN is the gateway for security,” MEF CTO Pascal Menezes said during his keynote at MEF...
IBM Boosts Open Tech With Cloud Pak for Security
The platform uses an open-source connector to integrate with IBM and other vendors’ security...
Even faster connection establishment with QUIC 0-RTT resumption

One of the more interesting features introduced by TLS 1.3, the latest revision of the TLS protocol, was the so called “zero roundtrip time connection resumption”, a mode of operation that allows a client to start sending application data, such as HTTP requests, without having to wait for the TLS handshake to complete, thus reducing the latency penalty incurred in establishing a new connection.
The basic idea behind 0-RTT connection resumption is that if the client and server had previously established a TLS connection between each other, they can use information cached from that session to establish a new one without having to negotiate the connection’s parameters from scratch. Notably this allows the client to compute the private encryption keys required to protect application data before even talking to the server.
However, in the case of TLS, “zero roundtrip” only refers to the TLS handshake itself: the client and server are still required to first establish a TCP connection in order to be able to exchange TLS data.
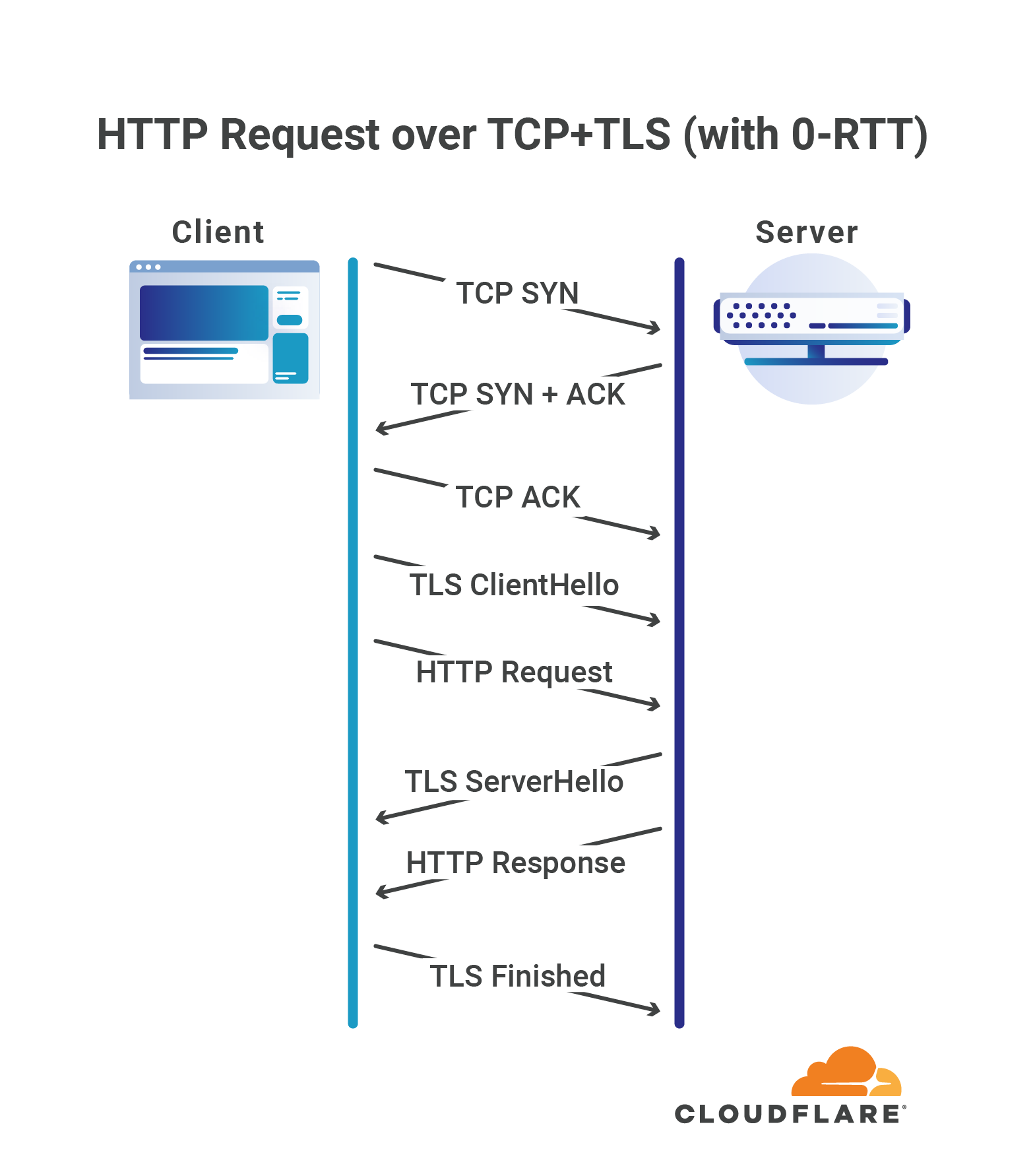
Zero means zero
QUIC goes a step further, and allows clients to send application data in the very first roundtrip of the connection, without requiring any other handshake to be Continue reading
Cloud Storage Startup Storj Hypes ‘Airbnb for Disk Drives’
The startup claims its decentralized storage costs less than half the price of AWS and cloud...
Orange, SoftBank Pick Fortinet SD-WAN
In addition to expanding its service provider reach, Fortinet announced an alliance with Siemens to...
Aryaka Breaks Out SD-WAN Into Smart Services Suite
Aryaka's restructured SmartServices product line breaks out many features previously only available...
Microsoft Drives Confidential Computing Into Kubernetes
The initiative taps into Intel’s Software Guard Extension platform to support confidential...
MEF Trumpets Progress on SD-WAN, Eyes Edge on 5G
MEF’s community has grown about 70% to more than 200 organizations during the last 18 months, and...
A10 Says Multi-Cloud Is Passé, Pushes Polynimbus
Polynimbus is essentially multi-cloud phase two, and it addresses how to manage and secure...
Facts and Fiction: BGP Is a Hot Mess
Every now and then a smart person decides to walk away from their competence zone, and start spreading pointless clickbait opinions like BGP is a hot mess.
Like any other technology, BGP is just a tool with its advantages and limitations. And like any other tool, BGP can be used sloppily… and that’s what’s causing the various problems and shenanigans everyone is talking about.
Just in case you might be interested in facts instead of easy-to-digest fiction:
Read more ...Log every request to corporate apps, no code changes required
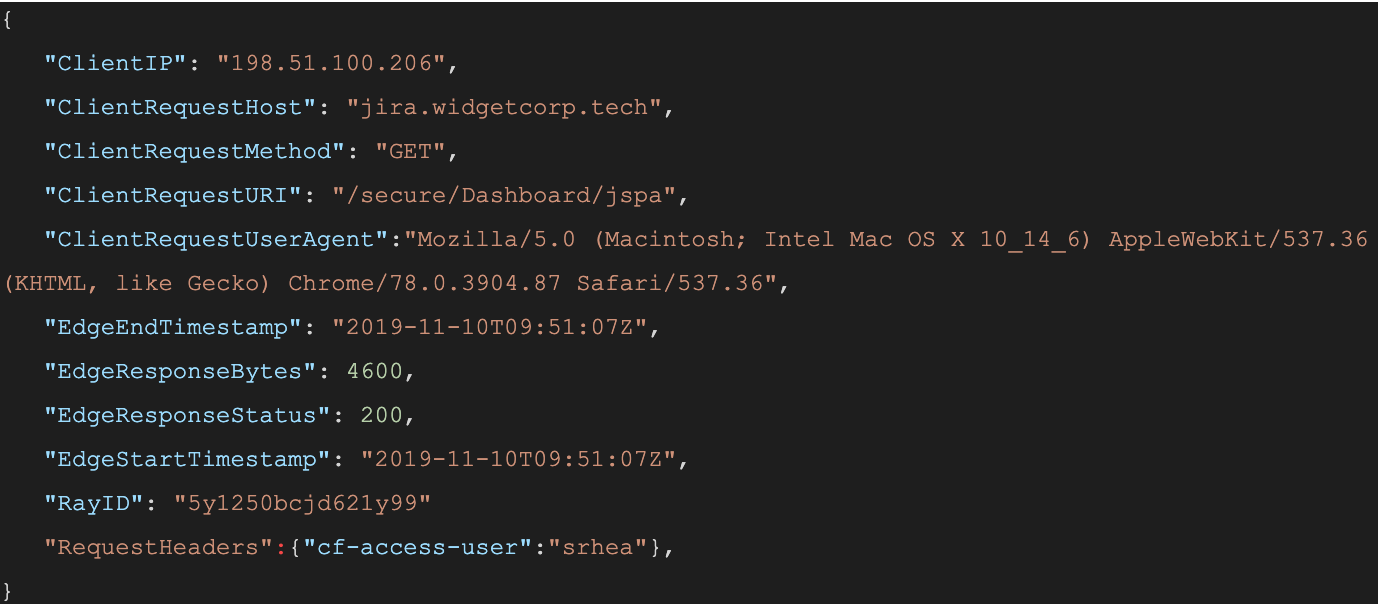
When a user connects to a corporate network through an enterprise VPN client, this is what the VPN appliance logs:
The administrator of that private network knows the user opened the door at 12:15:05, but, in most cases, has no visibility into what they did next. Once inside that private network, users can reach internal tools, sensitive data, and production environments. Preventing this requires complicated network segmentation, and often server-side application changes. Logging the steps that an individual takes inside that network is even more difficult.
Cloudflare Access does not improve VPN logging; it replaces this model. Cloudflare Access secures internal sites by evaluating every request, not just the initial login, for identity and permission. Instead of a private network, administrators deploy corporate applications behind Cloudflare using our authoritative DNS. Administrators can then integrate their team’s SSO and build user and group-specific rules to control who can reach applications behind the Access Gateway.
When a request is made to a site behind Access, Cloudflare prompts the visitor to login with an identity provider. Access then checks that user’s identity against the configured rules and, if permitted, allows the request to proceed. Access performs these checks on each request a user Continue reading
Dell Technologies CTO: Why AI Needs Empathy
If we want humans to trust artificial intelligence, then we need to teach the machines empathy,...
Palo Alto Networks Leaps Into SASE Market
Fulfilling Gartner's predictions, Palo Alto Networks announced its transition to a secure access...
Weekly Wrap: Juniper Guns for Cisco, Aruba With Mist AI
SDxCentral Weekly Wrap for Nov. 15, 2019: Juniper enhances its Mist AI platform and launches a new...
Librem13v2 TPM upgrade
I have upgraded my TPM firmware on my Librem13v2. Its keys are now safe. \o/
Back in 2017 we had the Infineon disaster (aka ROCA). I’ve written about it before about how bad it is and how to check if you’re affected with a simple tool.
I TAKE NO RESPONSIBILITY IF YOU BRICK YOUR DEVICE OR FOR ANYTHING ELSE BAD HAPPENING FROM YOU FOLLOWING MY NOTES.
Before the upgrade
$ tpm_version | grep Chip
Chip Version: 1.2.4.40 <--- Example vulnerable version
$ cbmem -c | grep Purism # I upgraded coreboot/SeaBIOS just before doing this.
coreboot-4.9-10-g123a4c6101-4.9-Purism-2 Wed Nov 13 19:54:43 UTC 2019 […]
[…]
Found mainboard Purism Librem 13 v2
Download upgrade tool
$ wget https://repo.pureos.net/pureos/pool/main/t/tpmfactoryupd/tpmfactoryupd_1.1.2459.0-0pureos9_amd64.deb
[…]
$ alien -t tpmfactoryupd_1.1.2459.0-0pureos9_amd64.deb
[…]
$ tar xfz tpmfactoryupd-1.1.2459.0.tgz
$ mv usr/bin/TPMFactoryUpd .
$ sudo systemctl stop trousers.service # Need to turn off tcsd for TPMFactoryUpd to work in its default mode.
[…]
$ ./TPMFactorUpd -info
**********************************************************************
* Infineon Technologies AG TPMFactoryUpd Ver 01.01.2459.00 *
**********************************************************************
TPM information:
----------------
Firmware valid : Yes
TPM family : 1.2
TPM firmware version Continue readingCisco Sinks on Rocky Q1, Dour Q2 Revenue Outlook
Service provider revenue dropped 13% year over year in Q1, while Cisco’s enterprise business...
How SD-Branch Enables Business Innovation
SD-branch can connect nearly any location, from a city office to a cabin in the woods. Here's how...
Money Moves: October 2019
Digital Reality dropped billions on European expansion; Ciena closed its acquisition of Centina;...
Beyond Thin Branch: Move Network Functions to Cloud
In-net SD-WAN allows maximum service delivery with minimum customer premises equipment (CPE)...
Aqua Buys CloudSploit, Moves Into Cloud Security Posture Management
Cloud security posture management includes processes and tools to avoid cloud misconfigurations...