VMware on White House Cybersecurity: ‘The Night’s Watch Is Very Thin’
An internal memo warns that “the White House is posturing itself to be electronically compromised...
What to Look for When Choosing a VPN

We welcome this guest post from Top10VPN.com, an Organization Member of the Internet Society.
The search for online privacy has driven a quarter of the world’s Internet users to download a Virtual Private Network (VPN). VPN services are now an important tool for anyone concerned about security and privacy on public networks.
There’s a world of difference between VPNs, though. Without clear and unbiased information many users are forced to navigate their choice of VPN without much clarity.
Why is choosing the right VPN provider so important?
Whenever you switch on a VPN you are entrusting its provider with your personal data, browsing activity, and sometimes even your security. For this reason, VPN providers must be held to a higher standard than most products. It’s important you do your due diligence when making a decision.
What should I look out for?
A good VPN will ensure that no one – even the VPN itself – can see what the user is doing online. Consider the following qualities:
Technical Security
The most secure VPN services will be transparent about the measures they have in place to safeguard their users and their business.
Any VPN worth its salt will offer Continue reading
Nokia VP: 5G Security Risks Are Huge
5G's impacts on society will be immense, and so will its security implications, said Mary O'Neill,...
BlackBerry CTO: ‘More Security, Less Friction Is The Dream’
BlackBerry has invested billions in security technologies and acquisitions in its quest to replace...
5G Spectrum Crunch Drives Conversation at MWC LA 2019
FCC Chairman Ajit Pai echoed other speakers sentiments about the need for more low-, mid-, and...
Microsoft Moves on Mover Months After Movere Move
Mover supports the migration of files from more than a dozen cloud providers, including Box,...
GSMA Warns Industry About Threatening Challenges
Challenges include the loss of trust in global supply chains, the loss of trust in the protection...
Splunk Buys Another Startup, Launches Mission Control
CTO Tim Tully kicked off the annual user conference by announcing Splunk reached a deal to buy open...
Your Day with Encryption

How often do you use encryption? It seems like the stuff of spy films, but you might be surprised to find out how often it touches your daily life.
Encryption is the process of scrambling or enciphering data, and only someone with the key can read or access it. You can use it for things like shopping online, using mobile banking, or using secure messaging apps. So while you may not be smuggling encrypted government secrets across borders, you do rely on it, along with your passwords and settings, to keep your data secure and private.
Learn about all of the ways you use encryption.
07:21

Your alarm vibrates. You reach for your phone, ready to snooze before you think better of it. You’ve got a big presentation at work and you’re going to need every minute today. There’s a message from your friend in Australia wishing you luck. How thoughtful! Even more thoughtful: your friend used an end-to-end encrypted messaging app. Sure, they saved on international phone charges, but the added security is nice too.
08:13

You’re ready to go, but before heading out, you check a news website for the traffic report. There’s a lock icon on the Continue reading
Designing Docker Hub Two-Factor Authentication

We recognize the central role that Docker Hub plays in modern application development and are working on many enhancements around security and content. In this blog post we will share how we are implementing two-factor authentication (2FA).
Using Time-Based One-Time Password (TOTP) Authentication
Two-factor authentication increases the security of your accounts by requiring two different forms of validation. This helps ensure that you are the rightful account owner. For Docker Hub, that means providing something you know (your username and a strong password) and something you have in your possession. Since Docker Hub is used by millions of developers and organizations for storing and sharing content – sometimes company intellectual property – we chose to use one of the more secure models for 2FA: software token (TOTP) authentication.
TOTP authentication is more secure than SMS-based 2FA, which has many attack vectors and vulnerabilities. TOTP requires a little more upfront setup, but once enabled, it is just as simple (if not simpler) than text message-based verification. It requires the use of an authenticator application, of which there are many available. These can be apps downloaded to your mobile device (e.g. Google Authenticator or Microsoft Authenticator) or it can Continue reading
What’s So Sassy About SASE
SASE combines elements of SD-WAN and network security into a single cloud-managed package.
Docker Attack Worm Mines for Monero
The worm has been named “Graboid” in honor of the 1990’s movie “Tremors.”
Ex-Cisco Execs Launch Pensando, Target Amazon
“Our chip enables other cloud vendors to compete against Amazon in a much better way,” Pensando...
Google Fuses Security Analytics in Cloud Wars Quest
The new security tool follows a slew of product upgrades and acquisitions as Google tries to...
“I was told to buy a software or lose my computer: I ignored it.” A study of ransomware
“I was told to buy a software or lose my computer. I ignored it”: a study of ransomware Simoiu et al., SOUPS 2019
This is a very easy to digest paper shedding light on the prevalence of ransomware and the characteristics of those most likely to be vulnerable to it. The data comes from a survey of 1,180 US adults conducted by YouGov, an online global market research firm. YouGov works hard to ensure respondent participation representative of (in this case) the general population in the U.S., but the normal caveats apply.
We define ransomware as the class of malware that attempts to defraud users by restricting access to the user’s computer or data, typically by locking the computer or encrypting data. There are thousands of different ransomware strains in existence today, varying in design and sophistication.
The survey takes just under 10 minutes to complete, and goes to some lengths to ensure that self-reporting victims really were victims of ransomware (and not some other computer problem).

For respondents that indicated they had suffered from a ransomware attack, data was collected on month and year, the name of the ransomware variant, the ransom demanded, the payment method, Continue reading
Forcepoint Web Security Footprint Spans 160 Global PoPs
The vendor rolled out its Web Security platform across 160 points of presence as it builds out a...
Toshiba Taps Cybera’s SD-WAN for Retail Terminals
Under the agreement, Cybera becomes Toshiba's preferred SD-WAN vendor in the Asia-Pacific...
Overcoming the Barriers to Micro-segmentation
It should come as no surprise how much emphasis organizations place on security today. Threats are becoming more and more sophisticated and the number of threats grow to uncontrollable rates every day.
One of the biggest downsides is that the rising cost of data breaches in 2019 alone, a global average of $3.92 million as reported by the Ponemon Institute and IBM Security July 2019 report, is enough to cause organizations to rethink or increase emphasis on their security strategies and how they can help secure their most important assets by improving the cyber hygiene in their organizations.
What is Cyber Hygiene?
Cyber hygiene refers to what an organization can do to improve their security postures around physical hardware, software, and applications. If you’ve seen Pat Gelsinger’s keynote from 2017, he goes into the 5 pillars of good cyber hygiene and what organizations can do to improve basic and fundamental security for their business.
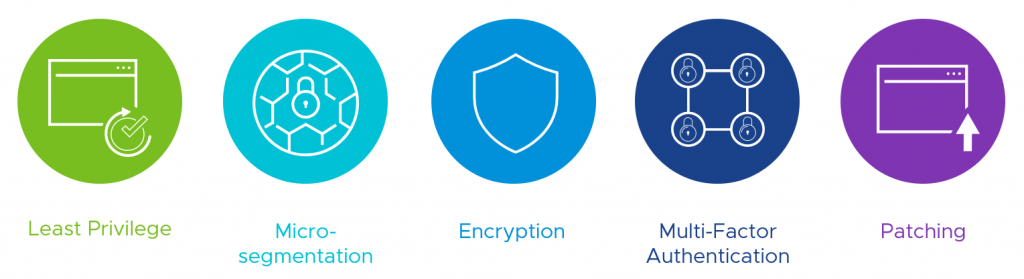
Over the last several years, VMware has been focusing on helping organizations move to Software-Defined Data Centers (SDDC) to improve their agility and meet the speed of business. As more organizations adopted the SDDC model, VMware found itself in a unique position Continue reading
Invisible mask: practical attacks on face recognition with infrared
Invisible mask: practical attacks on face recognition with infrared Zhou et al., arXiv’18
You might have seen selected write-ups from The Morning Paper appearing in ACM Queue. The editorial board there are also kind enough to send me paper recommendations when they come across something that sparks their interest. So this week things are going to get a little bit circular as we’ll be looking at three papers originally highlighted to me by the ACM Queue board!
‘Invisible Mask’ looks at the very topical subject of face authentication systems. We’ve looked at adversarial attacks on machine learning systems before, including those that can be deployed in the wild, such as decorating stop signs. Most adversarial attacks against image recognition systems require you to have pixel-level control over the input image though. Invisible Mask is different, it’s a practical attack in that the techniques described in this paper could be used to subvert face authentication systems deployed in the wild, without there being any obvious visual difference (e.g. specially printed glass frames) in the face of the attacker to a casual observer. That’s the invisible part: to the face recognition system it’s as if you are wearing a mask, Continue reading
Huawei Dodges German 5G Ban Despite US-Led Campaign
Germany today declined to ban any vendors from participating in the design and buildout of 5G...