Single Sign-On for Kubernetes: Dashboard Experience
Over my last two posts (part 1 and part 2), I have investigated user authentication in Kubernetes and how to create a single sign-on experience within the Kubernetes ecosystem. So far I have explained how Open ID Connect (OIDC) works, how to get started with OIDC and how to perform a login from the command line.
The final piece of this puzzle is the Kubernetes dashboard, often used by our engineers alongside kubectl. To complete our move to SSO, we wanted to ensure that, when using the Dashboard, our engineers logged in to the same account they used for kubectl.
Since Kubernetes version 1.7.0, the dashboard has had a login page. It allows users to upload a kubeconfig file or enter a bearer token. If you have already logged into the command line, this allows you to copy the OIDC id-token from your kubeconfig file into the bearer token field and login. There are, however, a couple of problems with this:
- The login page has a skip button — If you aren’t using any authorization (RBAC) then this would permit anyone to access the dashboard with effective admin rights.
- Copy and pasting a token from a Continue reading
Can McAfee Sell Its Security Story In a World Without Firewalls?
The vendor kicked off its annual Mpower Cybersecurity Summit with a new analytics tool that aims to...
Kubernetes Latest Flaw a ‘Billion Laughs’ … Not
The vulnerability can allow someone to launch a denial-of-service attack against a Kubernetes API...
SDxCentral’s Top 10 Articles — September 2019
VMware CEO: IBM Paid Too Much for Red Hat; AT&T, Sprint, & Cisco Execs Dump Cold Water on...
Celebrating National Cybersecurity Awareness Month

Every October, we mark National Cybersecurity Awareness Month. From the U.S. Department of Homeland Security website, “Held every October, National Cybersecurity Awareness Month (NCSAM) is a collaborative effort between government and industry to raise awareness about the importance of cybersecurity and to ensure that all Americans have the resources they need to be safer and more secure online.”
We believe in an Internet that is open, globally connected, secure, and trustworthy. Our work includes improving the security posture of producers of Internet of Things (IoT) devices, ensuring encryption is available for everyone and is deployed as the default, working on time security, routing security through the MANRS initiative, and fostering collaborative security.
The Online Trust Alliance’s IoT Trust Framework identifies the core requirements manufacturers, service providers, distributors/purchasers, and policymakers need to understand, assess, and embrace for effective security and privacy as part of the Internet of Things. Also check out our Get IoT Smart pages for get more consumer-friendly advice on IoT devices.
Much of OTA’s work culminates in the Online Trust Audit & Honor Roll, which recognizes excellence in online consumer protection, data security, and responsible privacy practices. Since that report’s release in April Continue reading
In-toto: providing farm-to-table guarantees for bits and bytes
in-toto: providing farm-to-table guarantees for bits and bytes Torres-Arias et al., USENIX Security Symposium 2019
Small world with high risks did a great job of highlighting the absurd risks we’re currently carrying in many software supply chains. There are glimmers of hope though. This paper describes in-toto, and end-to-end system for ensuring the integrity of a software supply chain. To be a little more precise, in-toto secures the end-to-end delivery pipeline for one product or package. But it’s only a small step from there to imagine using in-toto to also verify the provenance of every third-party dependency included in the build, and suddenly you’ve got something that starts to look very interesting indeed.
In-toto is much more than just a research project, it’s already deployed and integrated into a number of different projects and ecosystems, quietly protecting artefacts used by millions of people daily. You can find the in-toto website at https://in-toto.io.
In-toto has about a dozen different integrations that protect software supply chains for millions of end-users.
- If you install a Debian package using apt, in-toto is protecting it.
- If you use
kubesecto analyze your Kubenetes configurations, in-toto is protecting it - If you use the Continue reading
Talking 5G and the Next Big Networking Revolution with Claus Pedersen, Hewlett Packard Enterprise
Hear from Claus Pedersen, Vice President of Telco Infrastructure Solutions at HPE as he talks 5G,...
Small world with high risks: a study of security threats in the npm ecosystem
Small world with high risks: a study of security threats in the npm ecosystem Zimmermann et al., USENIX Security Symposium 2019
This is a fascinating study of the npm ecosystem, looking at the graph of maintainers and packages and its evolution over time. It’s packed with some great data, and also helps us quantify something we’ve probably all had an intuition for— the high risks involved in depending on a open and fast-moving ecosystem. One the key takeaways for me is the concentration of reach in a comparatively small number of packages and maintainers, making these both very high value targets (event-stream, it turns out, wouldn’t even have made the top-1000 in a list of ranked targets!), but also high leverage points for defence. We have to couple this of course with an exceedingly long tail.
The npm ecosystem
As the primary source of third-party JavaScript packages for the client-side, server-side, and other platforms, npm is the centrerpiece of a large and important software ecosystem.
Npm is an open ecosystem hosting a collection of over 800,000 packages as of February 2019, and it continues to grow rapidly.

To share a package on npm, a maintainer creates Continue reading
Serverless Security Threats Loom as Enterprises Go Cloud Native
As enterprises increase their usage of serverless functions, companies must understand serverless...
Cloudflare’s protection against a new Remote Code Execution vulnerability (CVE-2019-16759) in vBulletin
Cloudflare has released a new rule as part of its Cloudflare Specials Rulesets, to protect our customers against a high-severity vulnerability in vBulletin.
A new zero-day vulnerability was discovered for vBulletin, a proprietary Internet forum software. By exploiting this vulnerability, bad actors could potentially gain privileged access and control to the host servers on which this software runs, through Remote Code Execution (RCE).
Implications of this vulnerability
At Cloudflare, we use three key indicators to understand the severity of a vulnerability 1) how many customers on Cloudflare are running the affected software 2) the Common Vulnerability Scoring System (CVSS) score, and 3) the OWASP Top 10, an open-source security framework.
We assess this vulnerability to be very significant as it has a CVSS score of 9.8/10 and affects 7 out of the 10 key risk areas of the OWASP 2017 Top 10.
Remote Code Execution is considered a type of injection, which provides the capability to potentially launch a catastrophic attack. Through RCE an attacker can gain privileged access to the host server that might be running the unpatched and vulnerable version of this software. With elevated privileges the attacker could perform malicious activities including discovery of additional Continue reading
Birthday Week 2019 Wrap-up


This week we celebrated Cloudflare’s 9th birthday by launching a variety of new offerings that support our mission: to help build a better Internet. Below is a summary recap of how we celebrated Birthday Week 2019.
Cleaning up bad bots
Every day Cloudflare protects over 20 million Internet properties from malicious bots, and this week you were invited to join in the fight! Now you can enable “bot fight mode” in the Firewall settings of the Cloudflare Dashboard and we’ll start deploying CPU intensive code to traffic originating from malicious bots. This wastes the bots’ CPU resources and makes it more difficult and costly for perpetrators to deploy malicious bots at scale. We’ll also share the IP addresses of malicious bot traffic with our Bandwidth Alliance partners, who can help kick malicious bots offline. Join us in the battle against bad bots – and, as you can read here – you can help the climate too!
Browser Insights
Speed matters, and if you manage a website or app, you want to make sure that you’re delivering a high performing website to all of your global end users. Now you can enable Browser Insights in the Speed section of the Continue reading
Weekly Wrap: Ericsson Bribery Scandal Cuts Deep, Surpassing $1B Penalty
Weekly Wrap for Sept. 27, 2019: Stateless launches Luxon platform; Kubernetes sinks Containership;...
Wireless attacks on aircraft instrument landing systems
Wireless attacks on aircraft instrument landing systems Sathaye et al., USENIX Security Symposium 2019
It’s been a while since we last looked at security attacks against connected real-world entities (e.g., industrial machinery, light-bulbs, and cars). Today’s paper is a good reminder of just how important it is becoming to consider cyber threat models in what are primary physical systems, especially if you happen to be flying on an aeroplane – which I am right now as I write this!
The first fully operational Instrument Landing System (ILS) for planes was deployed in 1932. But assumptions we’ve been making since then (and until the present day, it appears!) no longer hold:
Security was never considered by design as historically the ability to transmit and receive wireless signals required considerable resources and knowledge. However, the widespread availability of powerful and low-cost software-defined radio platforms has altered the threat landscape. In fact, today the majority of wireless systems employed in modern aviation have been shown to be vulnerable to some form of cyber-physical attacks.
Both sections 1 and 6 in the paper give some eye-opening details of known attacks against aviation systems, but to date no-one Continue reading
CrowdStrike-Ukraine Explained
Trump's conversation with the President of Ukraine mentions "CrowdStrike". I thought I'd explain this.What was said?
This is the text from the conversation covered in this
“I would like you to find out what happened with this whole situation with Ukraine, they say Crowdstrike... I guess you have one of your wealthy people... The server, they say Ukraine has it.”Personally, I occasionally interrupt myself while speaking, so I'm not sure I'd criticize Trump here for his incoherence. But at the same time, we aren't quite sure what was meant. It's only meaningful in the greater context. Trump has talked before about CrowdStrike's investigation being wrong, a rich Ukrainian owning CrowdStrike, and a "server". He's talked a lot about these topics before.
Who is CrowdStrike?
They are a cybersecurity firm that, among other things, investigates hacker attacks. If you've been hacked by a nation state, then CrowdStrike is the sort of firm you'd hire to come and investigate what happened, and help prevent it from happening again.
Why is CrowdStrike mentioned?
Because they were the lead investigators in the DNC hack who came to the conclusion that Russia was responsible. The pro-Trump crowd believes this conclusion is Continue reading
Cisco Warns of ‘Continued Attempts’ to Exploit Critical Bug
Cisco disclosed more than two dozen vulnerabilities in its network automation software and one...
Deep Dive: How Do Banks Score on Privacy and Security?

In April 2019 the Internet Society’s Online Trust Alliance published its 10th annual Online Trust Audit & Honor Roll assessing the security and privacy of 1,200 top organizations. The Banking sector includes the top 100 banks in the U.S., based on assets according to the Federal Deposit Insurance Corporation (FDIC). Banks had a standout year, with a dramatic increase in scores across the board. Let’s take a closer look.
Overall, 73% of banks made the Honor Roll, putting the banking sector 4th behind the News and Media (78%), Consumer Services (85%), and the U.S. Federal Government (91%) sectors. In the previous Audit, only 27% made the grade. This large jump is due to improvements in all three scoring categories: email authentication, site security, and privacy.
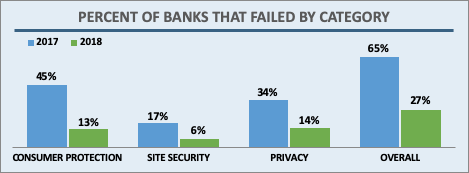
Banks, like most sectors, came close to 100% adoption in the two main email security technologies studied in the Audit: SPF (93%) and DKIM (87%). In addition, banks saw a marked improvement in how many sites implemented both both technologies at 87% in 2018, up from 60% in 2017. This puts banks among the most improved sectors in this area.
DMARC builds on SPF and DKIM results, provides a means for Continue reading
HTTP/3: the past, the present, and the future

During last year’s Birthday Week we announced preliminary support for QUIC and HTTP/3 (or “HTTP over QUIC” as it was known back then), the new standard for the web, enabling faster, more reliable, and more secure connections to web endpoints like websites and APIs. We also let our customers join a waiting list to try QUIC and HTTP/3 as soon as they became available.

Since then, we’ve been working with industry peers through the Internet Engineering Task Force, including Google Chrome and Mozilla Firefox, to iterate on the HTTP/3 and QUIC standards documents. In parallel with the standards maturing, we’ve also worked on improving support on our network.
We are now happy to announce that QUIC and HTTP/3 support is available on the Cloudflare edge network. We’re excited to be joined in this announcement by Google Chrome and Mozilla Firefox, two of the leading browser vendors and partners in our effort to make the web faster and more reliable for all.
In the words of Ryan Hamilton, Staff Software Engineer at Google, “HTTP/3 should make the web better for everyone. The Chrome and Cloudflare teams have worked together closely to bring HTTP/3 and QUIC from nascent standards to widely Continue reading
50 ways to leak your data: an exploration of apps’ circumvention of the Android permissions system
50 ways to leak your data: an exploration of apps’ circumvention of the Android permissions system Reardon et al., USENIX Security Symposium 2019
The problem is all inside your app, she said to me / The answer is easy if you take it logically / I’d like to help data in its struggle to be free / There must be fifty ways to leak their data.
You just slip it out the back, Jack / Make a new plan, Stan / You don’t need to be coy, Roy / Just get the data free.
Hop it on the bus, Gus / You don’t need to discuss much / Just drop off the key, Lee / And get the data free…
— Lyrics adapted from “50 ways to leave your lover” by Paul Simon (fabulous song btw., you should definitely check it out if you don’t already know it!).
This paper is a study of Android apps in the wild that leak permission protected data (identifiers which can be used for tracking, and location information), where those apps should not have been able to see such data due to a lack of granted permissions. By detecting Continue reading
Broadcom Targets 5G Networks, Hyperscale Security
Broadcom released a dual 400G MACSec PHY device to support increasing bandwidth demands and...