Ginseng: keeping secrets in registers when you distrust the operating system
Ginseng: keeping secrets in registers when you distrust the operating system Yun & Zhong et al., NDSS’19
Suppose you did go to the extreme length of establishing an unconditional root of trust for your system, even then, unless every subsequent piece of code you load is also fully trusted (e.g., formally verified) then you’re open to post-boot attacks. This is especially true in a context where lots of third-party application code (e.g. apps on a mobile phone) gets loaded.
Many mobile and IoT apps nowadays contain sensitive data, or secrets, such as passwords, learned models, and health information. Such secrets are often protected by encryption in the storage. However, to use a secret, an app must decrypt it and usually store it as cleartext in memory. In doing so, the app assumes that the operating system (OS) is trustworthy. OSes are complex software and have a large attack surface… Increasingly abundant evidence suggests that prudent apps should not trust the OS with their secrets.
Instead of trying to protect absolutely everything, Ginseng assumes that some data matters more than others. It arranges things such that this sensitive data is only ever in the clear in registers Continue reading
Establishing software root of trust unconditionally
Establishing software root of trust unconditionally Gligor & Woo, NDSS’19
The authors won a best paper award for this work at NDSS this year. The main result is quite something, but as you might expect the lines of argument are detailed and not always easy to follow (and certainly not critically!) for non-experts like me. I’ll use today’s write-up to convey the big ideas as I understand them. Close reading of the original paper (and it’s accompanying technical report) will be essential if you then want to dig deeper.
The problem: establishing a root of trust
Root of trust (RoT) establishment on an untrusted system ensures that a system state comprises all and only content chosen by the user, and the user’s code begins execution in that state. All implies that no content is missing, and only that no extra content exists. If a system state is initialized to content that satisfies security invariants and RoT establishment succeeds, a user’s code begins execution in a secure initial state.
That is to say, even in the presence of persistent malware e.g. in the firmware of peripheral controllers, network interface cards, disk and USB controllers, and so on, root of Continue reading
Automatic Clean-and-Updated Firewall Ruleset
This is a guest blog post by Andrea Dainese, senior network and security architect, and author of UNetLab (now EVE-NG) and Route Reflector Labs. These days you’ll find him busy automating Cisco ACI deployments.
Following the Ivan’s post about Firewall Ruleset Automation, I decided to take a step forward: can we always have up-to-date and clean firewall policies without stale rules?
The problem
We usually configure and manage firewalls using a process like this:
Read more ...Switzerland’s Leading Provider of Customized Financial Services for Dental Facilities Ensures the Safe Handling of Patient Records
The core business of Zahnärztekasse AG revolves around financial services for dentists and therefore secure patient records. The 33 employees look after the fee management of over 1,000 dental facilities in Switzerland. Recently, the company introduced a new level of security, because in the face of current threats and threats of cybercrime, sensitive data can fall into the wrong hands. The dental facilities often ask about the level of safety of the IT products and services offered. In addition, it is necessary to comply with the new federal law on data protection, the Swiss counterpart to GDPR. Therefore, IT security is very important. A digital transformation was necessary, because the systems in use were not completely protected against current threat scenarios. Furthermore, Zahnärztekasse was also striving for an ISO certification.
Interfaces and platforms already digitized
Digitalization is a major challenge for the conservative dental market. Zahnärztekasse has responded to this trend by digitizing its assets including interfaces, various platforms (www.debident.ch and www.zahngeld.ch) and the iOS app Crediflex, and is now considered to be a market leader and pioneer in the field. As early as 2010, Zahnärztekasse started virtualizing its systems and built on this trend Continue reading
The crux of voice (in)security: a brain study of speaker legitimacy detection
The crux of voice (in)security: a brain study of speaker legitimacy detection Neupane et al., NDSS’19
The key results of this paper are easy to understand, but the implications are going to take us a long time to unravel. Speech morphing (voice morphing) is the process of translating a speaker’s voice to sound like a given impersonation target. This capability is now available off-the-shelf —this paper uses the CMU Festvox voice converter— and is getting better all the time. Being able to impersonate someone’s voice takes things like social engineering attacks to a whole new level…
…voice imitation is an emerging class of threats, especially given the advancement in speech synthesis technology seen in a variety of contexts that can harm a victim’s reputation and her security/safety. For instance, the attacker could publish the morphed voice samples on social media, impersonate the victim in phone conversations, leave fake voice messages to the victim’s contacts, and even launch man-in-the-middle attacks against end-to-end encryption technologies that require users to verify the voices of the callers, to name a few instances of such attacks.
So voice should sit alongside images and video as a source we can’t trust in our new Continue reading
IoT Security, Privacy Vital from the Outset

For any new technology to be trusted, it must be secure. That is why privacy and security are essential to the development of new technologies from the outset. They must not be an afterthought.
This is especially so for the Internet of Things (IoT) and the plethora of devices that are now available. These devices are gradually being integrated into daily life as we enjoy the benefits they bring. In a number of cases, we are also increasing our dependence on them, such as fitness monitors and home automation.
But poorly-secured IoT devices and services can serve as entry points for cyber attacks, compromising sensitive data and potentially threatening the safety of individual users, as well others.
Attacks on infrastructure and other users, fueled by networks of poorly-secured IoT devices, can affect the delivery of essential services such as healthcare and basic utilities, put the security and privacy of others at risk, and threaten the resilience of the Internet globally.
As concerns mount about the need for regulating the ecosystem and policymakers around the world consider ways to secure it throughout its product lifecycles, it is important to consider the risks this fast-growing technology poses, as well as what steps Continue reading
Working Together the Internet Way to Build Success in North America

One of the most common lines you’ll hear in the virtual halls of the Internet Society is that the Internet’s success is due to its open, distributed, and global nature.
Think about it. A network of voluntarily-connected networks changed the course of history in a matter of decades because people agreed to work and innovate together. It’s a deeply profound source of inspiration about the power of humankind.
It practically begs the question: can we replicate even a portion of its success by embodying the “the Internet way” of working in North America?
The answer is yes.
As part of this, one thing is strikingly clear. Chapters and partners are the lifeblood of the organization. They are critical to working more closely with communities at the front lines of our work.
The Internet’s own globally-operable infrastructure proves the infinite potential of what can happen when people work together. In the same way, we will come together as a diverse community to help define future priorities.
We’ve already seen successes in the North American region that show how closer collaboration with Chapters and partners can help us reach new levels of success.
Enhancing IoT Security
Canada is changing how countries around Continue reading
Stateful Firewalls: When You Get to a Fork in the Road, Take It
If you’ve been in networking long enough you’d probably noticed an interesting pattern:
- Some topic is hotly debated;
- No agreement is ever reached even though the issue is an important one;
- The debate dies after participants diverge enough to stop caring about the other group.
I was reminded of this pattern when I was explaining the traffic filtering measures available in private and public clouds during the Designing Infrastructure for Private Clouds workshop.
Read more ...Preventing Request Loops Using CDN-Loop
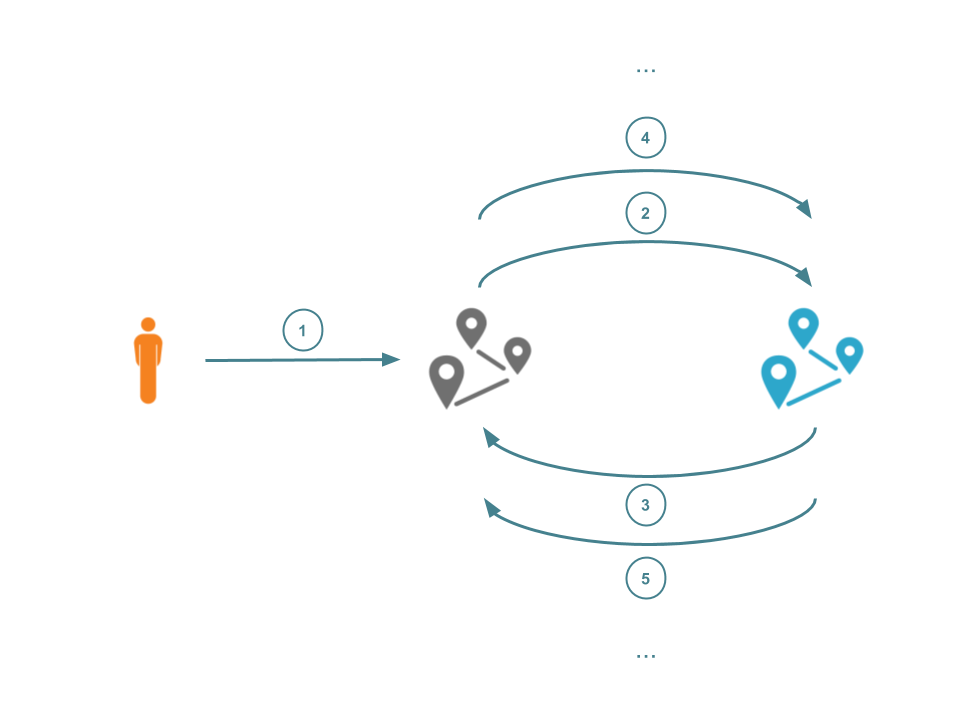
HTTP requests typically originate with a client, and end at a web server that processes the request and returns some response. Such requests may pass through multiple proxies before they arrive at the requested resource. If one of these proxies is configured badly (for instance, back to a proxy that had already processed it) then the request may be caught in a loop.
Request loops, accidental or malicious, can consume resources and degrade user's Internet performance. Such loops can even be observed at the CDN-level. Such a wide-scale attack would affect all customers of that CDN. It's been over three years since Cloudflare acknowledged the power of such non-compliant or malicious request loops. The proposed solution in that blog post was quickly found to be flawed and loop protection has since been implemented in an ad-hoc manner that is specific to each individual provider. This lack of cohesion and co-operation has led to a fragmented set of protection mechanisms.
We are finally happy to report that a recent collaboration between multiple CDN providers (including Cloudflare) has led to a new mechanism for loop protection. This now runs at the Cloudflare edge and is compliant with other CDNs, allowing us to Continue reading
BlueHat IL 2019 – Andrew “bunnie” Huang – Supply Chain Security

Must watch on supply chain and where our technology comes from
The post BlueHat IL 2019 – Andrew “bunnie” Huang – Supply Chain Security appeared first on EtherealMind.
Monsters in the Middleboxes: Introducing Two New Tools for Detecting HTTPS Interception


The practice of HTTPS interception continues to be commonplace on the Internet. HTTPS interception has encountered scrutiny, most notably in the 2017 study “The Security Impact of HTTPS Interception” and the United States Computer Emergency Readiness Team (US-CERT) warning that the technique weakens security. In this blog post, we provide a brief recap of HTTPS interception and introduce two new tools:
- MITMEngine, an open-source library for HTTPS interception detection, and
- MALCOLM, a dashboard displaying metrics about HTTPS interception we observe on Cloudflare’s network.
In a basic HTTPS connection, a browser (client) establishes a TLS connection directly to an origin server to send requests and download content. However, many connections on the Internet are not directly from a browser to the server serving the website, but instead traverse through some type of proxy or middlebox (a “monster-in-the-middle” or MITM). There are many reasons for this behavior, both malicious and benign.
Types of HTTPS Interception, as Demonstrated by Various Monsters in the Middle
One common HTTPS interceptor is TLS-terminating forward proxies. (These are a subset of all forward proxies; non-TLS-terminating forward proxies forward TLS connections without any ability to inspect encrypted traffic). A TLS-terminating forward proxy sits Continue reading
Cross-vCenter NSX at the Center for Advanced Public Safety
Jason Foster is an IT Manager at the Center for Advanced Public Safety at the University of Alabama. The Center for Advanced Public Safety (CAPS) originally developed a software that provided crash reporting and data analytics software for the State of Alabama. Today, CAPS specializes in custom software mostly in the realm of law enforcement and public safety. They have created systems for many states and government agencies across the country.
Bryan Salek, Networking and Security Staff Systems Engineer, spoke with Jason about network virtualization and what led the Center for Advanced Public Safety to choosing VMware NSX Data Center and what the future holds for their IT transformation.
The Need for Secure and Resilient Infrastructure
As part of a large modernize data center initiative, the forward-thinking CAPS IT team began to investigate micro-segmentation. Security is a primary focus at CAPS due to the fact that the organization develops large software packages for various state agencies. The applications that CAPS writes and builds are hosted together, but contain confidential information and need to be segmented from one another.
Once CAPS rolled out the micro-segmentation use-case, the IT team decided to leverage NSX Data Center for disaster recovery purposes as Continue reading
RFC8482 – Saying goodbye to ANY
Ladies and gentlemen, I would like you to welcome the new shiny RFC8482, which effectively deprecates the DNS ANY query type. DNS ANY was a "meta-query" - think of it as a similar thing to the common A, AAAA, MX or SRV query types, but unlike these it wasn't a real query type - it was special. Unlike the standard query types, ANY didn't age well. It was hard to implement on modern DNS servers, the semantics were poorly understood by the community and it unnecessarily exposed the DNS protocol to abuse. RFC8482 allows us to clean it up - it's a good thing.
But let's rewind a bit.
Historical context
It all started in 2015, when we were looking at the code of our authoritative DNS server. The code flow was generally fine, but it was all peppered with naughty statements like this:
if qtype == "ANY" {
// special case
}
This special code was ugly and error prone. This got us thinking: do we really need it? "ANY" is not a popular query type - no legitimate software uses it (with the notable exception of qmail).

ANY is Continue reading
DNS Privacy Frequently Asked Questions (FAQ)
We previously posted about how the DNS does not inherently employ any mechanisms to provide confidentiality for DNS transactions, and mentioned some of the protocols that have been recently developed to improve user privacy.
To complement this, we are publishing our DNS Privacy Frequently Asked Questions (FAQ). This highlights and provides answers to the most important aspects of DNS privacy.
Please also check our DNS Privacy page for more information!
Further Information
- Introduction to DNS Privacy
- DNS Privacy
- DNS Privacy Frequently Asked Questions (FAQ)
- DNS Privacy Project
The post DNS Privacy Frequently Asked Questions (FAQ) appeared first on Internet Society.
IPv6 Security for IPv4 Engineers

It is often argued that IPv4 practices should be forgotten when deploying IPv6, as after all IPv6 is a different protocol! But we think years of IPv4 operational experience should be leveraged as much as possible.
So we are publishing IPv6 Security for IPv4 Engineers as a roadmap to IPv6 security that is specifically aimed at IPv4 engineers and operators.
Rather than describing IPv6 in an isolated manner, it aims to re-use as much of the existing IPv4 knowledge and experience as possible, by highlighting the security issues that affect both protocols in the same manner, and those that are new or different for the IPv6 protocol suite. Additionally, it discusses the security implications arising from the co-existence of the IPv6 and IPv4 protocols.
Be sure also to check our IPv6 Security page as well!
Further Information
The post IPv6 Security for IPv4 Engineers appeared first on Internet Society.
Some notes on the Raspberry Pi
I keep seeing this article in my timeline today about the Raspberry Pi. I thought I'd write up some notes about it.The Raspberry Pi costs $35 for the board, but to achieve a fully functional system, you'll need to add a power supply, storage, and heatsink, which ends up costing around $70 for the full system. At that price range, there are lots of alternatives. For example, you can get a fully function $99 Windows x86 PC, that's just as small and consumes less electrical power.
There are a ton of Raspberry Pi competitors, often cheaper with better hardware, such as a Odroid-C2, Rock64, Nano Pi, Orange Pi, and so on. There are also a bunch of "Android TV boxes" running roughly the same hardware for cheaper prices, that you can wipe and reinstall Linux on. You can also acquire Android phones for $40.
However, while "better" technically, the alternatives all suffer from the fact that the Raspberry Pi is better supported -- vastly better supported. The ecosystem of ARM products focuses on getting Android to work, and does poorly at getting generic Linux working. The Raspberry Pi has the worst, most Continue reading
Research: Practical Challenge-Response for DNS
Because the speed of DNS is so important to the performance of any connection on the ‘net, a lot of thought goes into making DNS servers fast, including optimized software that can respond to queries in milliseconds, and connecting DNS servers to the ‘net through high bandwidth links. To set the stage for massive DDoS attacks based in the DNS system, add a third point: DNS responses tend to be much larger than DNS queries. In fact, a carefully DNS response can be many times larger than the query.
To use a DNS server as an amplifier in a DDoS attack, then, the attacker sends a query to some number of publicly accessible DNS servers. The source of this query is the address of the system to be attacked. If the DNS query is carefully crafted, the attacker can send small packets that cause a number of DNS servers to send large responses to a single IP address, causing large amounts of traffic to the system under attack.
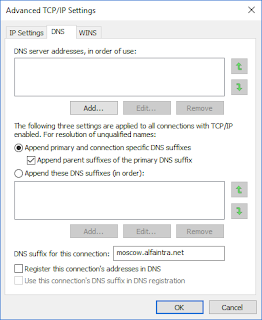
A quick lesson in confirmation bias
In my experience, hacking investigations are driven by ignorance and confirmation bias. We regularly see things we cannot explain. We respond by coming up with a story where our pet theory explains it. Since there is no alternative explanation, this then becomes evidence of our theory, where this otherwise inexplicable thing becomes proof.For example, take that "Trump-AlfaBank" theory. One of the oddities noted by researchers is lookups for "trump-email.com.moscow.alfaintra.net". One of the conspiracy theorists explains has proof of human error, somebody "fat fingered" the wrong name when typing it in, thus proving humans were involved in trying to communicate between the two entities, as opposed to simple automated systems.
But that's because this "expert" doesn't know how DNS works. Your computer is configured to automatically put local suffices on the end of names, so that you only have to lookup "2ndfloorprinter" instead of a full name like "2ndfloorprinter.engineering.example.com".
When looking up a DNS name, your computer may try to lookup the name both with and without the suffix. Thus, sometimes your computer looks up "www.google.com.engineering.exmaple.com" when it wants simply "www.google.com".
Apparently, Alfabank configures Continue reading
Stopping Drupal’s SA-CORE-2019-003 Vulnerability
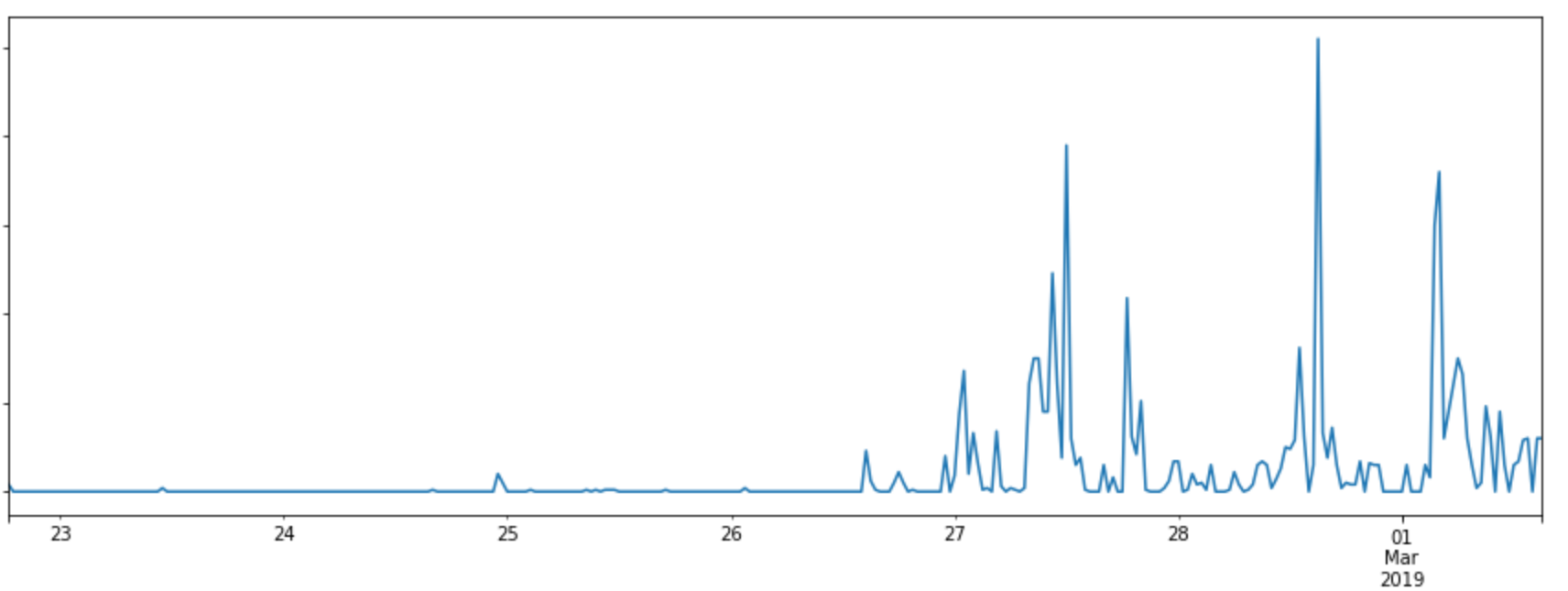
On the 20th February 2019, Drupal announced that they had discovered a severe vulnerability and that they would be releasing a patch for it the next day. Drupal is a Content Management System used by many of our customers, which made it important that our WAF protect against the vulnerability as quickly as possible.
As soon as Drupal released their patch, we analysed it to establish what kind of payloads could be used against it and created rules to mitigate these. By analysing the patch we were able to put together WAF rules to protect cloudflare customers running Drupal.
We identified the type of vulnerability we were dealing within 15 minutes. From here, we were able to deploy rules to block the exploit well before any real attacks were seen.
The exploit
As Drupal's release announcement explains, a site is affected if:
From looking at the patch we very quickly realised the exploit would be based on deserialization. The option ['allowed_classes' Continue reading