Why Lenovo’s One to Watch in 2019
The data center server vendor made several smart partnerships around HCI and cloud last year, and now it’s moving into edge and IoT.
Dell Four-Way Endpoint Security Play Targets the Mid-Market
 There are two strategic elements to the platform: One is that Dell considers mid-market security to be an underserved market. The other is that endpoints are particularly vulnerable.
There are two strategic elements to the platform: One is that Dell considers mid-market security to be an underserved market. The other is that endpoints are particularly vulnerable.
Extreme Networks CEO: Huawei Security Concerns Play Out in Data Center Networking, Too
 Ed Meyercord noted a customer win against Huawei and said security concerns about the Chinese vendor are “creating an opportunity for us in the marketplace.”
Ed Meyercord noted a customer win against Huawei and said security concerns about the Chinese vendor are “creating an opportunity for us in the marketplace.”
Fortanix Raises $23M Series B Led by Intel
 “We joke that our goal is to have the CIA run sensitive applications in China on Ali Cloud,” using Fortanix security software, CEO Ambuj Kumar says.
“We joke that our goal is to have the CIA run sensitive applications in China on Ali Cloud,” using Fortanix security software, CEO Ambuj Kumar says.
Symantec Taps Acquisitions to Bolster Endpoint Security
 The products are focused on managed endpoint detection and response, enhanced EDR 4.0, endpoint protection, and hardening capabilities.
The products are focused on managed endpoint detection and response, enhanced EDR 4.0, endpoint protection, and hardening capabilities.
Cisco Boosts IoT Management, Security With New Dev Tools and Hardware
 One analyst called the announcement “brilliant” because it is designed to help enterprise IT shops deal with “IoT havoc as the network edge is now stretched to the last connected device.”
One analyst called the announcement “brilliant” because it is designed to help enterprise IT shops deal with “IoT havoc as the network edge is now stretched to the last connected device.”
Juniper CEO ‘Disappointed’ With Q4 Revenue, Weak Cloud Sales Persist
 Rami Rahim said new products, including an MX line card targeting carrier 5G deployments, a new 400G platform, and silicon photonics capabilities, will return Juniper to growth during the second half of the year.
Rami Rahim said new products, including an MX line card targeting carrier 5G deployments, a new 400G platform, and silicon photonics capabilities, will return Juniper to growth during the second half of the year.
IBM and Google Create New Certifications for Data Scientist and Cloud Skills
 Job site Indeed found that listings for “data scientist" have surged 344 percent over the past five years.
Job site Indeed found that listings for “data scientist" have surged 344 percent over the past five years.
Cumulus and Nutanix Integrate HCI, Open Networking
 The partnership also allows Cumulus to battle Cisco. “That’s what we do everyday, and having a better story for Nutanix customers is just one more way to do that,” Cumulus CEO Josh Leslie says.
The partnership also allows Cumulus to battle Cisco. “That’s what we do everyday, and having a better story for Nutanix customers is just one more way to do that,” Cumulus CEO Josh Leslie says.
Cisco Pushes ACI to AWS and Azure, Embraces ‘Data Center Anywhere’ Strategy
 It sounds similar to VMware’s “NSX everywhere” push, which seeks to stretch that vendor’s networking and security capabilities from data centers to clouds and the edge.
It sounds similar to VMware’s “NSX everywhere” push, which seeks to stretch that vendor’s networking and security capabilities from data centers to clouds and the edge.
Passwords in a file
My dad is on some sort of committee for his local home owners association. He asked about saving all the passwords in a file stored on Microsoft's cloud OneDrive, along with policy/procedures for the association. I assumed he called because I'm an internationally recognized cyberexpert. Or maybe he just wanted to chat with me*. Anyway, I thought I'd write up a response.The most important rule of cybersecurity is that it depends upon the risks/costs. That means if what you want to do is write down the procedures for operating a garden pump, including the passwords, then that's fine. This is because there's not much danger of hackers exploiting this. On the other hand, if the question is passwords for the association's bank account, then DON'T DO THIS. Such passwords should never be online. Instead, write them down and store the pieces of paper in a secure place.
OneDrive is secure, as much as anything is. The problem is that people aren't secure. There's probably one member of the home owner's association who is constantly infecting themselves with viruses or falling victim to scams. This is the person who you are giving OneDrive access to. This is fine for the Continue reading
Cisco Issues Patches for Several SD-WAN Software Vulnerabilities
 Cisco discovered a number of vulnerabilities affecting devices that connect to its SD-WAN software. This includes one critical security flaw to its vController software.
Cisco discovered a number of vulnerabilities affecting devices that connect to its SD-WAN software. This includes one critical security flaw to its vController software.
ExtraHop CEO Sets His Sights on Becoming a Half-Billion-Dollar Security Firm
 ExtraHop CEO Arif Kareem is also positioning the software provider for an IPO in the next 24 months. But he’s quick to add, “that’s not our end goal.”
ExtraHop CEO Arif Kareem is also positioning the software provider for an IPO in the next 24 months. But he’s quick to add, “that’s not our end goal.”
5G SA Core, Handset Deployments to be Delayed, Dell’Oro Says
 The one-year delay is because initial 5G network launches are using the non-standalone architecture that relies on already deployed 4G LTE evolved packet core technology.
The one-year delay is because initial 5G network launches are using the non-standalone architecture that relies on already deployed 4G LTE evolved packet core technology.
McAfee Cuts 200 Employees as Buyout Rumors Persist
 Thoma Bravo, the private equity firm rumored to want to buy McAfee, spent billions scooping up security companies in 2018. It also approached Symantec about acquiring that company.
Thoma Bravo, the private equity firm rumored to want to buy McAfee, spent billions scooping up security companies in 2018. It also approached Symantec about acquiring that company.
Carbon Black Reports 1 Million-Plus Security Attacks Daily
 China and Russia were responsible for almost half of the incident response episodes.
China and Russia were responsible for almost half of the incident response episodes.
Netskope IDs New Google Cloud Attack, McAfee Finds Ransomware
 Threat researchers at Netskope and McAfee this week described new and potentially dangerous networking vulnerabilities.
Threat researchers at Netskope and McAfee this week described new and potentially dangerous networking vulnerabilities.
Linux Foundation Launches LF Edge Group With 5 Projects
 The new group’s list of founding members reads like a who’s who of chipmakers, telecommunications companies, cloud providers, edge infrastructure vendors, and others.
The new group’s list of founding members reads like a who’s who of chipmakers, telecommunications companies, cloud providers, edge infrastructure vendors, and others.
HTTP/3: From root to tip
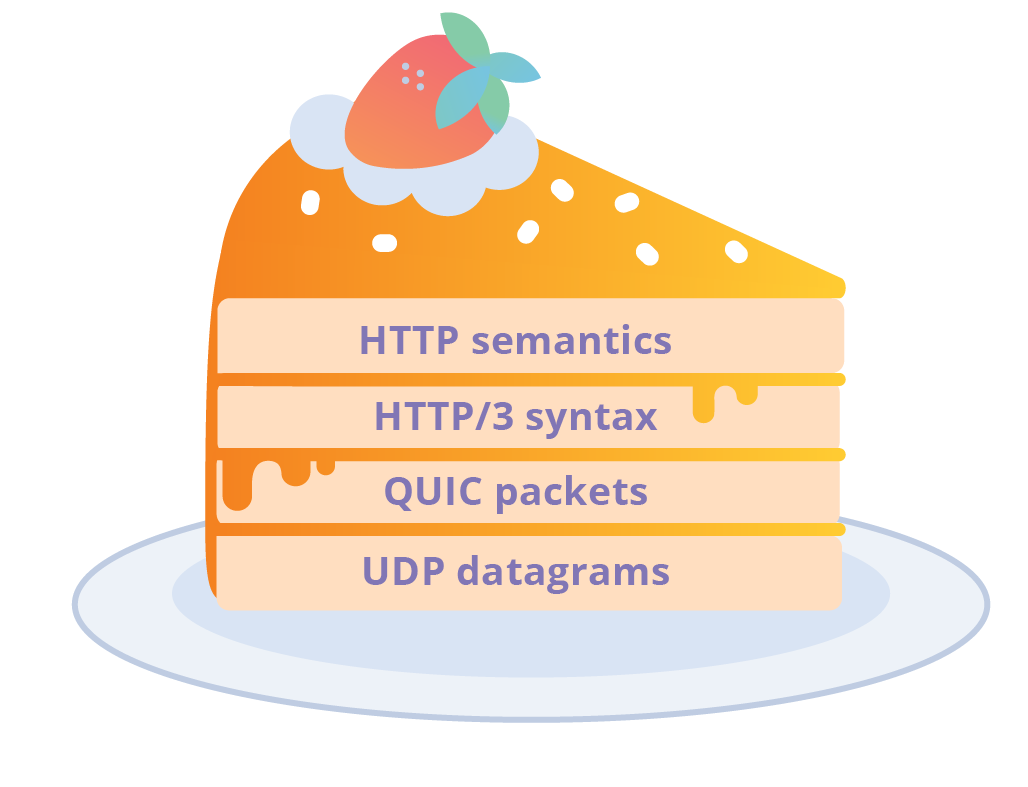
HTTP is the application protocol that powers the Web. It began life as the so-called HTTP/0.9 protocol in 1991, and by 1999 had evolved to HTTP/1.1, which was standardised within the IETF (Internet Engineering Task Force). HTTP/1.1 was good enough for a long time but the ever changing needs of the Web called for a better suited protocol, and HTTP/2 emerged in 2015. More recently it was announced that the IETF is intending to deliver a new version - HTTP/3. To some people this is a surprise and has caused a bit of confusion. If you don't track IETF work closely it might seem that HTTP/3 has come out of the blue. However, we can trace its origins through a lineage of experiments and evolution of Web protocols; specifically the QUIC transport protocol.
If you're not familiar with QUIC, my colleagues have done a great job of tackling different angles. John's blog describes some of the real-world annoyances of today's HTTP, Alessandro's blog tackles the nitty-gritty transport layer details, and Nick's blog covers how to get hands on with some testing. We've collected these and more at https://cloudflare-quic.com. And if that tickles your fancy, be sure Continue reading
StackRox Extends Its Container Security Platform
 StackRox updated its container security platform with additional visibility, profiling, and network management features.
StackRox updated its container security platform with additional visibility, profiling, and network management features.