Emergency Directive 19-01, DNS 2FA suggested

Check your domain registration and protect those logins
The post Emergency Directive 19-01, DNS 2FA suggested appeared first on EtherealMind.
Cohesity Fights Ransomware, Dips Its Toes Into Security
 The vendor added new capabilities to its data backup platform that prevent, detect, and respond to ransomware attacks.
The vendor added new capabilities to its data backup platform that prevent, detect, and respond to ransomware attacks.
Tracing Soon-to-Expire Federal .gov Certificates with CT Monitors

As of December 22, 2018, parts of the US Government have “shut down” because of a lapse in appropriation. The shutdown has caused the furlough of employees across the government and has affected federal contracts. An unexpected side-effect of this shutdown has been the expiration of TLS certificates on some .gov websites. This side-effect has emphasized a common issue on the Internet: the usage of expired certificates and their erosion of trust.
For an entity to provide a secure website, it needs a valid TLS certificate attached to the website server. These TLS certificates have both start dates and expiry dates. Normally certificates are renewed prior to their expiration. However, if there’s no one to execute this process, then websites serve expired certificates--a poor security practice.
This means that people looking for government information or resources may encounter alarming error messages when visiting important .gov websites:
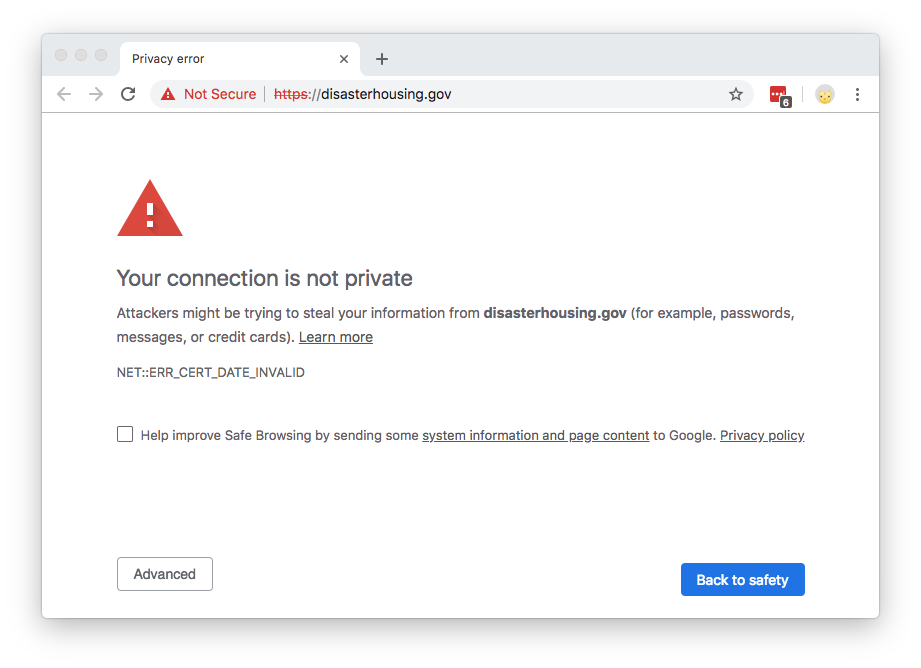
The content of the website hasn’t changed; it’s just the cryptographic exchange that’s invalid (an expired certificate can’t be validated). These expired certificates present a trust problem. Certificate errors often dissuade people from accessing a website, and imply that the site is not to be trusted. Browsers purposefully make it difficult to continue to Continue reading
Canonical Brings IoT Security to Ubuntu Core
 Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs.
Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs.
Security VC Funding Hit Record $5.3 Billion in 2018
 But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
Microsoft Adds AzureDevOps Bug Bounty, Offers $20K Rewards
 This isn’t Microsoft’s first bounty program. Its largest reward offers up to $250,000 for finding critical flaws in its Hyper-V hypervisor.
This isn’t Microsoft’s first bounty program. Its largest reward offers up to $250,000 for finding critical flaws in its Hyper-V hypervisor.
Consumer Electronics Show: Everything’s Connected, But What About Security and Privacy?

We spent last week at the Consumer Electronics Show (aka CES) in Las Vegas, with over 180,000 of our closest friends. And with 4,500 exhibitors present, you’d have less than 30 seconds at each booth if you wanted to talk to all of them. Many articles have covered the cool new things, so in this blogpost we are going to discuss our overall impressions as they relate to our work on consumer IoT security and privacy.
Not surprisingly, there were many interesting conference sessions and a wide variety of innovative products on display, including some that seemed to push the bounds of credibility in their claims. Integration of devices with voice-driven and other platforms was everywhere – Amazon Alexa, Google Assistant, Apple HomeKit, and Samsung SmartThings being the most widely adopted to date. 5G was a hot topic, especially for its improved speeds and flexibility, though specifics about its availability are still hard to pin down.
Everything these days is getting connected to the Internet – from cat toys to sports simulators to home automation. One area that seems to be gaining more traction because it has gone beyond the “gadget” stage and is solving real problems is health and Continue reading
Huawei Takes 5G Supremacy Shot at ZTE
 Huawei and ZTE are vying for supremacy in China’s 5G R&D trials against the backdrop of an increasingly hostile international environment.
Huawei and ZTE are vying for supremacy in China’s 5G R&D trials against the backdrop of an increasingly hostile international environment.
Short Take – HTTPS Interception
HTTPS was created to ensure end to end encryption of web traffic but both good guys and attackers circumvent this with man-in-the-middle interception. In this Short Take, Russ talks about some of the mechanics of HTTPS interception as well as some implications of doing it intentionally.
The post Short Take – HTTPS Interception appeared first on Network Collective.
New Malware Uninstalls Cloud Security Products, Unit 42 Researchers Say
 The new code can uninstall agent-based security software by Tencent Cloud and Alibaba Cloud, the top two cloud providers in China.
The new code can uninstall agent-based security software by Tencent Cloud and Alibaba Cloud, the top two cloud providers in China.
Will Germany be Next to Block Huawei From 5G Networks?
 The German government is said to be planning measures that would basically block Huawei from participating in future 5G networks.
The German government is said to be planning measures that would basically block Huawei from participating in future 5G networks.
Race to Operationalize Cloud Native Applications Underway
 IT operations teams need to get ahead of Kubernetes deployments that will soon span the extended enterprise.
IT operations teams need to get ahead of Kubernetes deployments that will soon span the extended enterprise.
Internet Society Delhi Chapter and CCAOI Organize Webinar on India’s Draft Intermediary Rules

On 10 January, the Internet Society Delhi Chapter and CCAOI jointly organised an interactive webinar on the draft Information Technology [Intermediary Guidelines (Amendment) Rules] 2018 (“the draft Intermediary Rules”) to improve understanding of it and to encourage members and other Indian stakeholders to submit their comments to the Ministry of Electronics and Information Technology (MeitY) during their public comment period. The draft Intermediary Rules seeks to modify Section 79(2)(c) of the Information Technology Act, 2000 (the IT Act). Section 79 of the IT Act introduces obligations for intermediaries to meet to gain exemption from liability over the third-party information that they “receive, store, transmit, or provide any service with respect to.” These proposed changes were developed by MeitY to try to address misinformation and harmful content on social media, which have been connected with lynching and other recent violent acts of vigilantism.
The session was moderated by Subhashish Panigrahi, chapter development manager for Asia-Pacific at the Internet Society, and Amrita Choudhury, treasurer of the Internet Society Delhi Chapter and director of the CCAOI.
The changes to the IT Act proposed in the draft Intermediary Rules would require intermediaries to provide monthly notification to users on content they should not share; ensure that the originator Continue reading
Vodafone, IBM Launch $550 Million Multi-Cloud Joint Venture
 The new organization, co-led by Vodafone and IBM, will provide European companies with technologies that integrate and manage multiple clouds.
The new organization, co-led by Vodafone and IBM, will provide European companies with technologies that integrate and manage multiple clouds.
Cybeats Releases IoT Security, Monitoring App on Palo Alto Networks Framework
 The Cybeats IoT Radar app provides internal defense, monitoring, and lifecycle management directly to IoT devices.
The Cybeats IoT Radar app provides internal defense, monitoring, and lifecycle management directly to IoT devices.
VMware PKS Update Embraces Azure, Kubernetes Security
 VMware CEO Patrick Gelsinger told attendees at a recent investor conference that the company was “seeing [a] good uptick” in adoption of PKS.
VMware CEO Patrick Gelsinger told attendees at a recent investor conference that the company was “seeing [a] good uptick” in adoption of PKS.
One-Click DNSSEC with Cloudflare Registrar


When you launch your domain to the world, you rely on the Domain Name System (DNS) to direct your users to the address for your site. However, DNS cannot guarantee that your visitors reach your content because DNS, in its basic form, lacks authentication. If someone was able to poison the DNS responses for your site, they could hijack your visitors' requests.
The Domain Name System Security Extensions (DNSSEC) can help prevent that type of attack by adding a chain of trust to DNS queries. When you enable DNSSEC for your site, you can ensure that the DNS response your users receive is the authentic address of your site.
We launched support for DNSSEC in 2014. We made it free for all users, but we couldn’t make it easy to set up. Turning on DNSSEC for a domain was still a multistep, manual process. With the launch of Cloudflare Registrar, we can finish the work to make it simple to enable for your domain.
You can now enable DNSSEC with a single click if your domain is registered with Cloudflare Registrar. Visit the DNS tab in the Cloudflare dashboard, click "Enable DNSSEC", and we'll handle the rest. If you are Continue reading
Update on Latin America and Caribbean Workshop for Chapter Leaders

In July 2018, the Internet Society’s Latin America and Caribbean Bureau held another edition of the Workshop for Chapter Leaders. Besides discussing the challenges and opportunities of participation in their respective chapters, the 34 attendees began the implementation of several projects related to our 4 key issues of 2018. Starting 2019, I am glad to share with you the main results of these projects.
Participation showed a strong preference for Internet access issues. As a result, 10 of the 23 projects implemented were focused on Community Networks. Following our vocation in favor of the multistakeholder approach and the participation of the community, 8 of the projects took Internet Governance as a central theme. The remaining 5 projects focused on trust and security by focusing on Internet of Things (IoT) and Internet routing security through MANRS.
The results are inspiring, since they reflect the diversity of the Latin American and Caribbean region. In Community Networks, projects include a broad spectrum of related topics, ranging from the deployment and implementation of networks to the analysis and mapping of regulatory conditions to ensure such deployment. In addition, some of the projects focused on capacity building through webinars.
In terms of Internet Governance, awareness Continue reading
Huawei’s Got 99 Problems and Futurewei’s One
 And Poland arrested a Chinese Huawei employee and charged him with spying for Beijing.
And Poland arrested a Chinese Huawei employee and charged him with spying for Beijing.



