Short Take – IPv6 Security Considerations
It this Network Collective Short Take, Russ White discusses security considerations when deploying and operating IPv6.
The post Short Take – IPv6 Security Considerations appeared first on Network Collective.
Get IoT Smart: Homework for Many Indonesians

Today’s guest post is from Bhredipta Socarana, an Intellectual Property lawyer based in Indonesia and a Youth@IGF Fellow.
As one of the most populated countries, Indonesia has grown as one of the biggest markets for technology development. From the import of various over-the-top platforms to the implementation of Artificial Intelligence, technology has changed the Indonesian livelihood, including my own. This is also the case for Internet of Things (IoT).
As an emerging country, Indonesia admittedly has not been an advance player in responding to technology improvement. Despite the heavy invasion of technology-related products, many Indonesians have homework to do, especially for IoT. The business player needs to be aware of the responsibility of manufacturing and distributing IoT, while the public must also be aware of the various risks that they may be exposed to using IoT products.
Through the rapid development of technology and the intention of the Indonesian government to push the public to enter the “Industrial Revolution 4.0,” it will be mostly impossible to prevent penetration of IoT to our life. This leaves the public with the need to get smart with IoT.
Privacy and cybersecurity are among the issues revolving around IoT, and the need to have a Continue reading
Cloud Security Acquisitions, OneLogin $100M Funding Round Preview What’s In Store
 The opening days of 2019 also saw Sophos purchase cloud security startup Avid Secure and Akamai Technologies reach a deal to acquire Janrain.
The opening days of 2019 also saw Sophos purchase cloud security startup Avid Secure and Akamai Technologies reach a deal to acquire Janrain.
Martello Technologies Uses SD-WAN to Optimize IoT Systems
 The work is part of its participation in the Blackberry and L-Spark Accelerator Program, a program building network performance management technologies for IoT.
The work is part of its participation in the Blackberry and L-Spark Accelerator Program, a program building network performance management technologies for IoT.
Geo IP Databases are Highly Inaccurate

Lots of network monitoring platforms use GeoIP databases to track/monitor sources. These databases are, perhaps, 75% accurate (for some definition of accurate). This is your regular reminder to have a sense of caution about location based on public IP address. John S. and his mother Ann live in the house, which is in Pretoria, the […]
The post Geo IP Databases are Highly Inaccurate appeared first on EtherealMind.
Forget the uCPE, 2019 Will Usher in the uSD-WAN
 In 2019 SD-WAN solutions will converge toward a universal archetype.
In 2019 SD-WAN solutions will converge toward a universal archetype.
Enterprises Spent $125B on IT Infrastructure in 2018, Says Synergy Research
 While Cisco maintained its dominance in the enterprise infrastructure market, HPE beat out the vendor in the data center server segment of the market.
While Cisco maintained its dominance in the enterprise infrastructure market, HPE beat out the vendor in the data center server segment of the market.
What Makes IoT A Security Risk?

IoT security is a pretty hot topic in today’s world. That’s because the increasing number of smart devices is causing issues with security professionals everywhere. Consumer IoT devices are expected to top 20 billion by 2020. And each of these smart devices represents an attack surface. Or does it?
Hello, Dave
Adding intelligence to a device increases the number of ways that it can compromised. Take a simple thermostat, for example. The most basic themostat is about as dumb as you can get. It uses the expansion properties of metal to trigger switches inside of the housing. You set a dial or a switch and it takes care of the rest. Once you start adding things like programmability or cloud connection, you increase the number of ways that you can access the device. Maybe it’s a webpage or an app. Maybe you can access it via wireless or Bluetooth. No matter how you do it, it’s more available than the simple version of the thermostat.
What about industrial IoT devices? The same rule applies. In this case, we’re often adding remote access to Supervisory Control And Data Acquistion (SCADA) systems. There’s a big market from enterprise IT providers to create Continue reading
Consensys and AMD Build Blockchain-Based Cloud Infrastructure
 The new company, called W3bcloud, is developing data center products to support blockchain-based workloads and applications.
The new company, called W3bcloud, is developing data center products to support blockchain-based workloads and applications.
Radware Snaps Up ShieldSquare for New Bot Management Product Line
 ShieldSquare provides an API-based service that leverages machine learning to detect and eliminate “bad bots” from a variety of applications.
ShieldSquare provides an API-based service that leverages machine learning to detect and eliminate “bad bots” from a variety of applications.
ZTE Taps Former Senator Joe Lieberman to ‘Lobby’ on Its Behalf
 William Plummer, Huawei’s former VP of external affairs, said that company needs to diversify its leadership and not solely rely on Chinese nationals in its relations with the U.S.
William Plummer, Huawei’s former VP of external affairs, said that company needs to diversify its leadership and not solely rely on Chinese nationals in its relations with the U.S.
Ryuk Ransomware Takes Down Cloud Hosting Provider’s Systems
 Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
Threat researchers linked Ryuk to the North Korean state-sponsored Lazarus Group believed to be behind the WannaCry attack.
SDxCentral’s Top 10 Articles of 2018
 Cisco lays off hundreds in California; Cisco updates its routers with SD-WAN; and all the details of Verizon's outsourcing deal.
Cisco lays off hundreds in California; Cisco updates its routers with SD-WAN; and all the details of Verizon's outsourcing deal.
Who Went Where: The Top Personnel Changes of 2018
 From Hans Vestberg’s quick rise at Verizon to Google Cloud’s leadership shakeup, this year was full of personnel changes that turned heads.
From Hans Vestberg’s quick rise at Verizon to Google Cloud’s leadership shakeup, this year was full of personnel changes that turned heads.
DNS-over-TLS in Linux (systemd)

Whilst we were putting together some content about DNS privacy recently, we learned that recent distributions of Linux ship with support or this. We therefore decided to give Ubuntu 18.10 a try on a laptop.
More recent versions of Ubuntu employ a special service for name resolution called ‘system-resolved.service(8)’. The configuration file ‘resolved.conf(5)’ specifies most of the details for name resolution, including which protocols and resolvers should be employed, whilst the ‘/etc/systemd/network/*.network’ configuration files (see ‘systemd.network(5)’ for details) of the ‘systemd-networkd.service(8)’ specify any per-link specific settings.
The default configuration of ‘systemd-resolved’ is selected at compile time, and ‘/etc/systemd/resolved.conf’ normally contains commented-out lines describing such defaults. For example, the contents of the aforementioned file on a fresh Ubuntu 18.10 installation are:
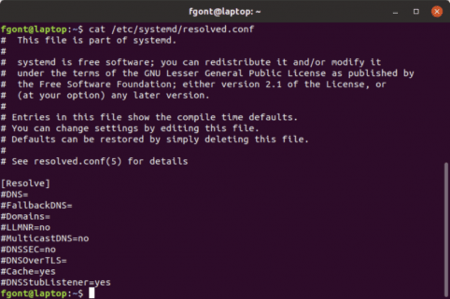
As may be inferred from the file, DNS-over-TLS (DoT) is supported, but disabled by default. At the time of writing, only opportunistic DoT is supported according to the manual, which means that the resolver will first try resolution using DoT before falling back to traditional DNS in the event of failure – thus allowing for downgrade attacks where an attacker intentionally causes a DoT failure in order to cause name resolution to downgrade Continue reading
Trump Considers New Attack on Huawei, ZTE
 But Huawei may be getting the best kind of revenge. The company says its revenues in 2018 grew 21 percent over the previous year.
But Huawei may be getting the best kind of revenge. The company says its revenues in 2018 grew 21 percent over the previous year.
2018 Is a Year Huawei Would Like to Forget
 Can it get much worse than having its CFO arrested and being accused of violating sanctions?
Can it get much worse than having its CFO arrested and being accused of violating sanctions?
Related Stories
DNS-over-HTTPS (DoH) Support in Mozilla Firefox
Recent releases of Firefox have introduced the concept of DNS privacy under the name “Trusted Recursive Resolver”. Although Firefox ships with DNS-over-HTTPS (DoH) disabled by default, there has been some discussion within the Mozilla developer community about changing the default to “enabled”.
Although DoH is somewhat controversial because it moves control plane (signalling) messages to the data plane (data forwarding), and can thereby bypass local network policies, DoH advocates argue that it makes it harder to block or monitor DNS queries which is a commonly used method for restricting access to the Internet and/or monitoring user behaviour.
But putting these arguments aside, if you want to try out DoH then the DNS privacy (or “TRR” in Firefox speak) configuration in Firefox can be accessed as follows:
- Enter “about:config” in the address box of the browser
- Search for “trr” (without quotes)
A sample output of DNS privacy configuration in Mozilla Firefox is as follows:
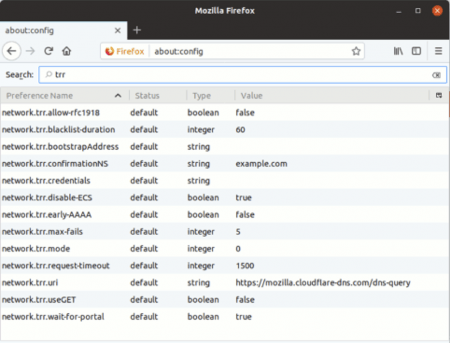
Firefox offers its technical users quite a few settings to play with, but the most important options (along with their recommended settings) for TRR are:
- trr.bootstrapAddress:(empty)
- trr.mode: 3
- trr.uri: https://mozilla.cloudflare-dns.com/dns-query
“network.trr.bootstrapAddress” specifies the IP address of a recursive resolver that should Continue reading
Concise Christmas Cryptography Challenges 2019

Last year we published some crypto challenges to keep you momentarily occupied from the festivities. This year, we're doing the same. Whether you're bored or just want to learn a bit more about the technologies that encrypt the internet, feel free to give these short cryptography quizzes a go.
We're withholding answers until the start of the new year, to give you a chance to solve them without spoilers. Before we reveal the answers; if you manage to solve them, we'll be giving the first 5 people to get the answers right some Cloudflare swag. Fill out your answers and details using this form so we know where to send it.
Have fun!
NOTE: Hints are below the questions, avoid scrolling too far if you want to avoid any spoilers.

Challenges
Client says Hello
Client says hello, as follows:
00000c07ac01784f437dbfc70800450000f2560140004006db58ac1020c843c
7f80cd1f701bbc8b2af3449b598758018102a72a700000101080a675bce16787
abd8716030100b9010000b503035c1ea569d5f64df3d8630de8bdddd1152e75f
528ae577d2436949ce8deb7108600004400ffc02cc02bc024c023c00ac009c0
08c030c02fc028c027c014c013c012009f009e006b0067003900330016009d
009c003d003c0035002f000a00af00ae008d008c008b010000480000000b
000900000663666c2e7265000a00080006001700180019000b0002010000
0d0012001004010201050106010403020305030603000500050100000000
001200000017000052305655494338795157524c656d6443436c5246574651
675430346754456c4f52564d674e434242546b51674e513d3d
[Raw puzzle without text wrap]
Time-Based One-Time Password
A user has an authenticator device to generate one time passwords for logins to their banking website. The implementation contains a fatal flaw.
At the following times, the following codes are generated (all in GMT/UTC):
- Friday, 21 December 2018 16:29:28 - Continue reading
The Wired Nursery

This month, we’ve asked parents to share their experiences of raising kids in the tech age. Today’s guest author is Kimberly Rae Miller, author of Beautiful Bodies and the bestselling memoir Coming Clean.
Being a parent means living with constant, underlying anxiety over just about everything from how to slice hot dogs, to the age old winter jacket vs. car seat conundrum, to whether all the tech used to keep kids alive/make life with them easier is actually going to screw them up/destroy your life.
The latter takes a fair bit of cognizant dissonance. Most of us know at least some of the pitfalls of our wired life. After all, the digital assistant in my living room knew that I was pregnant again about five seconds after I did (and yes, there are Bluetooth-enabled home pregnancy tests), and voila, almost immediately targeted ads for diapers and nursery furniture started showing up when I shopped online. Most of the time I brush aside how uncomfortable it all makes me, because the gizmos and gadgets that make momming slightly easier are maybe worth the invasion of privacy.
When I was pregnant with my now two-year-old son, I knew that I didn’t know Continue reading



