Provisioning a headless Raspberry Pi
The typical way of installing a fresh Raspberry Pi is to attach power, keyboard, mouse, and an HDMI monitor. This is a pain, especially for the diminutive RPi Zero. This blogpost describes a number of options for doing headless setup. There are several options for this, including Ethernet, Ethernet gadget, WiFi, and serial connection. These examples use a Macbook as an example, maybe I'll get around to a blogpost describing this from Windows.Burning micro SD card
We are going to edit the SD card before booting, so for completeness, I thought I'd describe the process of burning an SD card.We are going to download the latest "raspbian" operating system. I download the "lite" version because I'm not using the desktop features. It comes as a compressed .zip file which we need to extract into an .img file. Just double-click on the .zip on Windows or Mac.
The next step is to burn the image to an SD card. On Windows I use Win32DiskImager. On Mac I use the following command-line steps:
$ sudo -s
# mount
# diskutil unmount /dev/disk2s1
# dd bs=1m if=~/Downloads/2018-06-27-raspbian-stretch-lite.img of=/dev/disk2 conv=sync
First, I need a root prompt. I then use the Continue reading
Deploying TLS 1.3
Last week saw the formal publication of the TLS 1.3 specification as RFC 8446. It’s been a long time coming – in fact it’s exactly 10 years since TLS 1.2 was published back in 2008 – but represents a substantial step forward in making the Internet a more secure and trusted place.
What is TLS and why is it needed?
Transport Layer Security (TLS) is widely used to encrypt data transmitted between Internet hosts, with the most popular use being for secure web browser connections (adding the ‘S’ to HTTP). It is also commonly (although less visibly) used to encrypt data sent to and from mail servers (using STARTTLS with SMTP and IMAP/POP etc..), but can be used in conjunction with many other Internet protocols (e.g. DNS-over-TLS, FTPS) where secure connections are required. For more information about how TLS works and why you should use it, please see our TLS Basics guide.
TLS is often used interchangeably with SSL (Secure Socket Layers) which was developed by Netscape and predates it as an IETF Standard, but many Certification Authorities (CAs) still market the X.509 certificates used by TLS as ‘SSL certificates’ due to their familiarity with Continue reading
How to Get to the Cloud Computing ‘Goldilocks Zone’
 Borrowing from the astrological meaning, the Goldilocks Zone refers to the space where organizations have the right amount of resources and combination of components to support network life.
Borrowing from the astrological meaning, the Goldilocks Zone refers to the space where organizations have the right amount of resources and combination of components to support network life.
Windmill Uses Blockchain to Solve IoT Security Issues
 The company’s open source blockchain-based security platform is working with enterprises to secure their IoT data and devices.
The company’s open source blockchain-based security platform is working with enterprises to secure their IoT data and devices.
Array Networks Says Its the Nutanix of Private Cloud Networking and Security
 Companies can run Array’s security and networking applications, open source applications, or those from third-party vendors like Cisco and F5 on the platform.
Companies can run Array’s security and networking applications, open source applications, or those from third-party vendors like Cisco and F5 on the platform.
VMware CEO Pat Gelsinger: NSX Is the Standard for SDN
 VMware’s NSX networking license bookings grew 40 percent year over year during the second quarter of fiscal 2019.
VMware’s NSX networking license bookings grew 40 percent year over year during the second quarter of fiscal 2019.
At VMworld, Get An Inside Look at a Modern Bank. Learn How Wells Fargo and Other Top Brands Reduce Risk While Fostering Innovation.
This blog was co-authored by Jared Ruckle and Jonathan Morin.
VMworld is one of the seminal weeks in enterprise IT. You gather with your peers to learn and discuss the challenges of the day. And what are those challenges? Three stand out:
- Rising consumer expectations. Your customers expect to interact with your brand on their terms. Self-service, mobility, and speed are table stakes. If you don’t deliver a responsive and engaging user experience, you’re irrelevant.
- Increased competition from startups and incumbents. Your competitors aren’t only your peers in the FORTUNE 500. Startups all over the world are looking to take your market share.
- Constantly evolving security threats from every direction. Speaking of table stakes: security. In an era where attacks can be launched for pennies – by anyone, from anywhere – you have take a different approach to InfoSec. You need to move faster. Speed and velocity aren’t just for development teams. It’s a crucial for a modern InfoSec mindset too.
Sound familiar? It should if you’re an IT leader. No matter where you are on your journey to get better at software, it’s always fun to learn from others. We want to highlight a few sessions Continue reading
Australia Bans Carriers from Using Huawei and ZTE Equipment for 5G
 The government argues that 5G blurs the line between the core network and the edge network, making security more challenging.
The government argues that 5G blurs the line between the core network and the edge network, making security more challenging.
Announcing the Online Trust Audit & Honor Roll Methodology for 2018
The Online Trust Alliance (OTA) is an Internet Society initiative that aims to enhance online trust, user empowerment, and innovation through convening multistakeholder initiatives and developing and promoting best practices, ethical privacy practices, and data stewardship. One of OTA’s major activities is the Online Trust Audit & Honor Roll, which promotes responsible online privacy and data security practices and recognizes leaders in the public and private sectors who have embraced them. This morning, we released the methodology we’ll use for this year’s audit.
The report will analyze more than 1,000 websites on consumer protection, site security, and responsible privacy practices. Based on a composite weighted analysis, sites that score 80 percent or better overall, without failing in any one category, will be recognized in the Honor Roll.
Building largely on past criteria, this year’s updates include GDPR compliance and other security and privacy standards and practices, as well as adding a healthcare sector. From the press release:
Key changes to this year’s Audit include:
- Consumer Protection (email authentication, domain security and anti-phishing technologies) – more granular assessment of Domain-based Message Authentication, Reporting and Conformance (DMARC) support, and increased weight for use of opportunistic Transport Layer Security (TLS), which Continue reading
There’s a Techlash. The G20 Should Listen.
The Internet is at risk. Once thought of as the global equalizer, opening doors for communication, work opportunities, commerce and more – the Internet is now increasingly viewed with skepticism and wariness. We are witnessing a trend where people fare feeling let down by the technology they use. Fueled by unease and uncertainty about the growing scope of threats to security and privacy that come with an always-on, tech-driven world, people are now looking for ways to disconnect and are placing greater emphasis on values and human interaction.
The way we live our lives is now inextricably linked to the Internet – which is estimated to contribute US$6.6 trillion a year, or 7.1 percent of total GDP in the G20 countries by 2020. In developing nations, that digital economy is growing steadily by 15 to 25 percent a year. Yet the Internet essentially is under attack. Large scale data breaches, uncertainties about how our data is being used and monetized, cybercrime, surveillance and other online threats are impacting Internet users’ trust. We are at an important crossroads for the Internet and its healthy development is at stake.
It is our collective duty to find a response to the Continue reading
Enabling SDN Based Multi-Access Edge Computing Systems
 While MEC is set to address the data demand of 5G networks, adding network programmability to MEC ameliorates the overall MEC solution.
While MEC is set to address the data demand of 5G networks, adding network programmability to MEC ameliorates the overall MEC solution.
Cisco Talos Smells a RAT
 The company selling the software claims it will only sell it for legal uses. But the RAT gives buyers everything they need to build a botnet.
The company selling the software claims it will only sell it for legal uses. But the RAT gives buyers everything they need to build a botnet.
Getting To The Root Of Security With Trusted Silicon
The increasingly distributed nature of computing and the rapid growth in the number of the small connected devices that make up the Internet of Things (IoT) are combining with trends like the rise of silicon-level vulnerabilities highlighted by Spectre, Meltdown, and more recent variants to create an expanding and fluid security landscape that’s difficult for enterprises to navigate. …
Getting To The Root Of Security With Trusted Silicon was written by Jeffrey Burt at .
Cohesity’s Helios Uses Machine Learning to Manage Secondary Data
 The cloud service gives companies visibility and mobility across all of their secondary data and applications from a single dashboard. It also uses machine learning and analytics to power a bunch of new infrastructure management features.
The cloud service gives companies visibility and mobility across all of their secondary data and applications from a single dashboard. It also uses machine learning and analytics to power a bunch of new infrastructure management features.
Foundries.io Tightens Edge, IoT Integration to Boost Security
 The firm sees constant and long-term updates as key to maintaining edge and IoT security.
The firm sees constant and long-term updates as key to maintaining edge and IoT security.
Arista Taps VMware, Zscaler to Create Consistent Cloud Security
 VMware’s software will bring common security policy enforcement to virtual and physical workloads. Zscaler brings its north-south traffic security.
VMware’s software will bring common security policy enforcement to virtual and physical workloads. Zscaler brings its north-south traffic security.
Microsoft Foils Russian Security Threat, Seizes Fake Political Websites
 Microsoft said it has used this approach 12 times in two years to shut down 84 fake websites associated with the state-sponsored hacking group called Fancy Bear.
Microsoft said it has used this approach 12 times in two years to shut down 84 fake websites associated with the state-sponsored hacking group called Fancy Bear.
DeGrasse Tyson: Make Truth Great Again
Neil deGrasse Tyson tweets the following:I’m okay with a US Space Force. But what we need most is a Truth Force — one that defends against all enemies of accurate information, both foreign & domestic.— Neil deGrasse Tyson (@neiltyson) August 20, 2018
A good start: The National Academy of Sciences, which “…provides objective, science-based advice on critical issues affecting the nation."— Neil deGrasse Tyson (@neiltyson) August 20, 2018
Truth vs. "Truth"
Securing The Server, Inside And Out
Computing is hard enough, but the sophistication and proliferation of attacks on IT infrastructure, from the firewall moat surrounding the corporate network all the way down into the guts of the operating system kernel and deep into the speculative execution units on the physical processor, make the task of computing – with confidence – doubly difficult. …
Securing The Server, Inside And Out was written by Timothy Prickett Morgan at .
How Cloudflare protects customers from cache poisoning
A few days ago, Cloudflare — along with the rest of the world — learned of a "practical" cache poisoning attack. In this post I’ll walk through the attack and explain how Cloudflare mitigated it for our customers. While any web cache is vulnerable to this attack, Cloudflare is uniquely able to take proactive steps to defend millions of customers.
In addition to the steps we’ve taken, we strongly recommend that customers update their origin web servers to mitigate vulnerabilities. Some popular vendors have applied patches that can be installed right away, including Drupal, Symfony, and Zend.
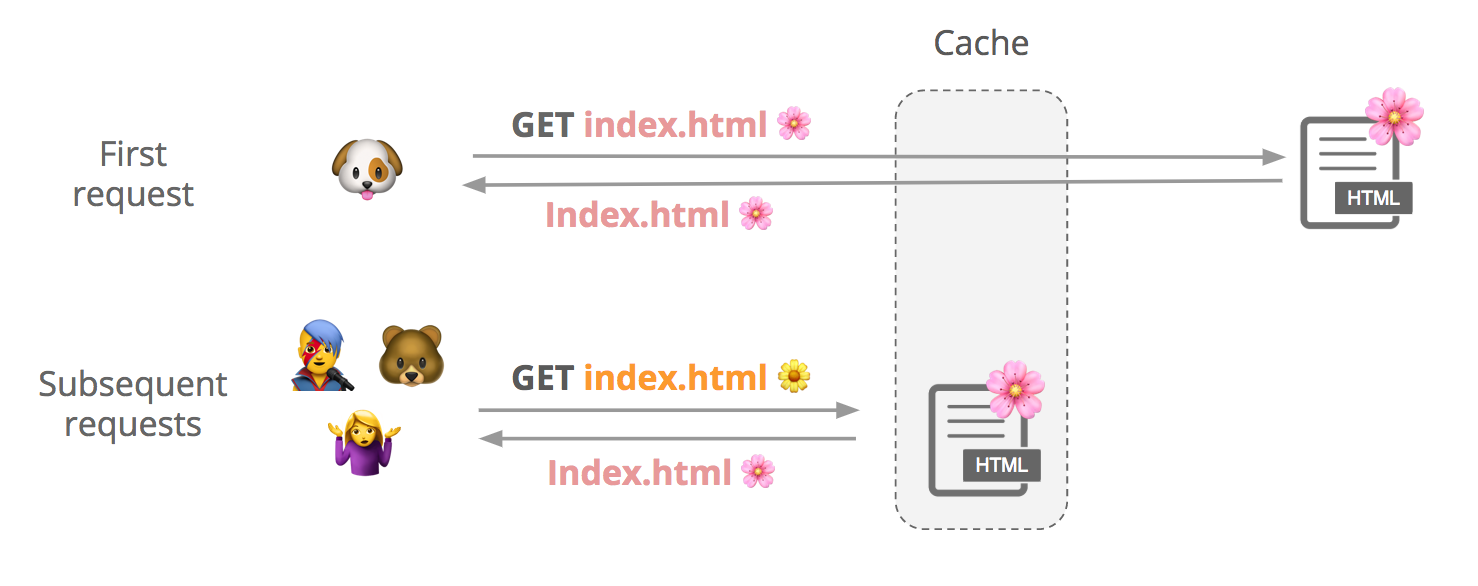
How a shared web cache works
Say a user requests a cacheable file, index.html. We first check if it’s in cache, and if it’s not not, we fetch it from the origin and store it. Subsequent users can request that file from our cache until it expires or gets evicted.
Although contents of a response can vary slightly between requests, customers may want to cache a single version of the file to improve performance:
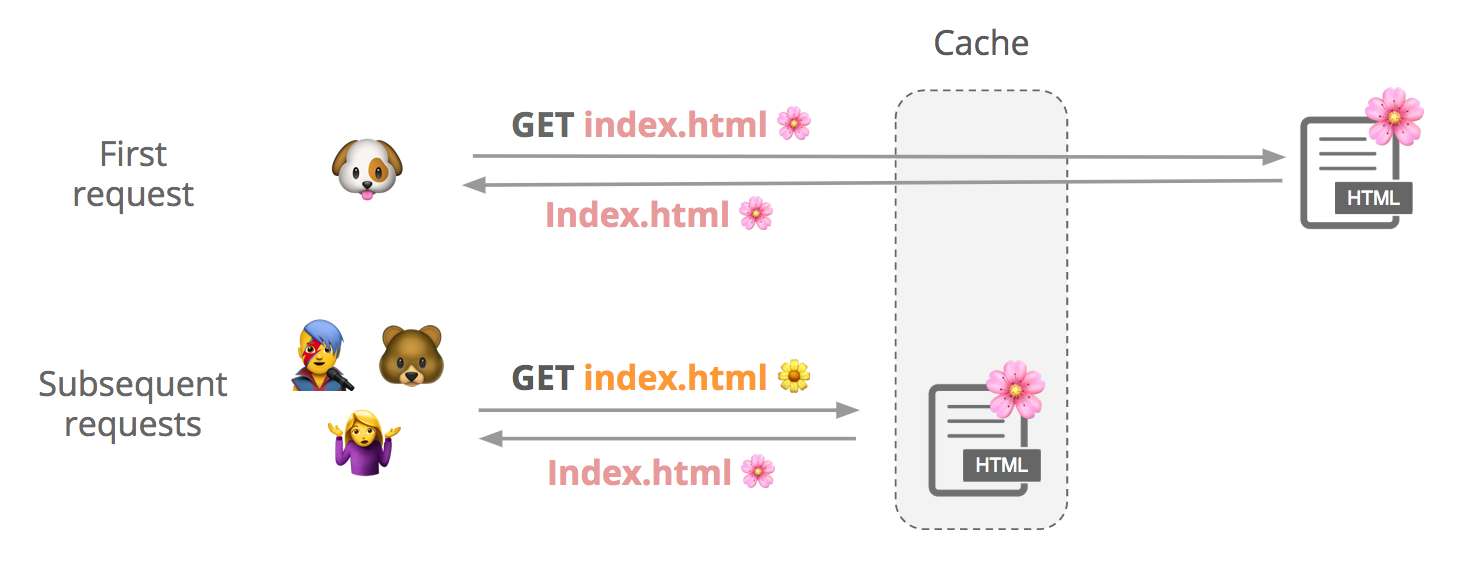
(See this support page for more info about how to cache HTML with Cloudflare.)
How do we know it’s the same file? We create something Continue reading