Google Cloud CEO: Enterprise Table Stakes and Cutting Edge
 At the annual Google Next conference the company launched an integrated portfolio of cloud services that combine open source projects with Google’s cloud infrastructure and security services.
At the annual Google Next conference the company launched an integrated portfolio of cloud services that combine open source projects with Google’s cloud infrastructure and security services.
Going Proactive on Security: Driving Encryption Adoption Intelligently
It's no secret that Cloudflare operates at a huge scale. Cloudflare provides security and performance to over 9 million websites all around the world, from small businesses and WordPress blogs to Fortune 500 companies. That means one in every 10 web requests goes through our network.
However, hidden behind the scenes, we offer support in using our platform to all our customers - whether they're on our free plan or on our Enterprise offering. This blog post dives into some of the technology that helps make this possible and how we're using it to drive encryption and build a better web.
Why Now?
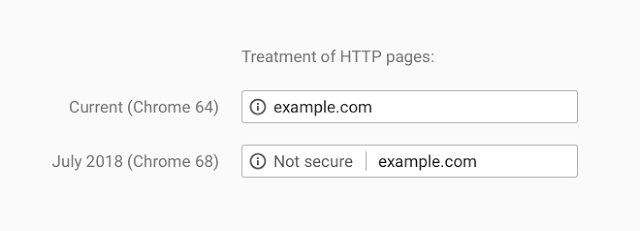
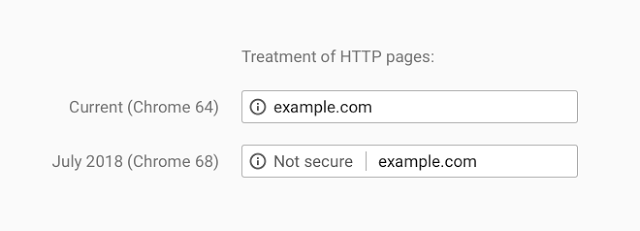
Recently web browser vendors have been working on extending encryption on the internet. Traditionally they would use positive indicators to mark encrypted traffic as secure; when traffic was served securely over HTTPS, a green padlock would indicate in your browser that this was the case. In moving to standardise encryption online, Google Chrome have been leading the charge in marking insecure page loads as "Not Secure". Today, this UI change has been pushed out to all Google Chrome users globally for all websites: any website loaded over HTTP will be marked as insecure.
That's not all though; Continue reading
James Feger Ditches CenturyLink for F5 Networks
 Adding Feger is the latest in a number of hires by F5 as it shifts its business model to prepare for 5G, IoT, and the cloud.
Adding Feger is the latest in a number of hires by F5 as it shifts its business model to prepare for 5G, IoT, and the cloud.
Cloudflare Access: Now teams of any size can turn off their VPN

Using a VPN is painful. Logging-in interrupts your workflow. You have to remember a separate set of credentials, which your administrator has to manage. The VPN slows you down when you're away from the office. Beyond just inconvenience, a VPN can pose a real security risk. A single infected device or malicious user can compromise your network once inside the perimeter.
In response, large enterprises have deployed expensive zero trust solutions. The name sounds counterintuitive - don’t we want to add trust to our network security? Zero trust refers to the default state of these tools. They trust no one; each request has to prove that itself. This architecture, most notably demonstrated at Google with Beyondcorp, has allowed teams to start to migrate to a more secure method of access control.
However, users of zero trust tools still suffer from the same latency problems they endured with old-school VPNs. Even worse, the price tag puts these tools out of reach for most teams.
Here at Cloudflare, we shared those same frustrations with VPNs. After evaluating our options, we realized we could build a better zero trust solution by leveraging some of the unique capabilities we have here at Cloudflare:
Our Continue reading
Gigamon Dives Deeper Into Security Space With Icebrg Acquisition
 Gigamon will combine its network traffic visibility capabilities with Icebrg’s security platform and allow SOC teams to deploy new security technologies as “security applications” on top of it.
Gigamon will combine its network traffic visibility capabilities with Icebrg’s security platform and allow SOC teams to deploy new security technologies as “security applications” on top of it.
Today, Chrome Takes Another Step Forward in Addressing the Design Flaw That is an Unencrypted Web

The following is a guest post by Troy Hunt, awarded Security expert, blogger, and Pluralsight author. He’s also the creator of the popular Have I been pwned?, the free aggregation service that helps the owners of over 5 billion accounts impacted by data breaches.
I still clearly remember my first foray onto the internet as a university student back in the mid 90's. It was a simpler online time back then, of course; we weren't doing our personal banking or our tax returns or handling our medical records so the whole premise of encrypting the transport layer wasn't exactly a high priority. In time, those services came along and so did the need to have some assurances about the confidentiality of the material we were sending around over other people's networks and computers. SSL as it was at the time was costly, but hey, banks and the like could absorb that given the nature of their businesses. However, at the time, there were all sorts of problems with the premise of serving traffic securely ranging from the cost of certs to the effort involved in obtaining and configuring them through to the performance hit on the Continue reading
IBM-Led Nabla Container Platform Touts Isolation for Its Security Posture
 The design differs from traditional Docker-based containers that allow for a host kernel to be shared by running containers, which leads to more interaction between the host and container pods.
The design differs from traditional Docker-based containers that allow for a host kernel to be shared by running containers, which leads to more interaction between the host and container pods.
Xage Scores $12M Series A for Blockchain-Based IoT Security
 The company’s platform uses blockchain to connect industrial IoT devices and synchronize and store credentials, certificates, policies, and data between edge and data center locations.
The company’s platform uses blockchain to connect industrial IoT devices and synchronize and store credentials, certificates, policies, and data between edge and data center locations.
Research: Even Password Complexity is a Tradeoff
Stronger passwords are always better—at least this is the working theory of most folks in information technology, security or otherwise. Such blanket rules should raise your suspicions, however; the rule11 maxim if you haven’t found the tradeoff, you haven’t looked hard enough should apply to passwords, too.
Begin with this simple assertion: complex passwords are primarily a guard against password guessing attacks. Further, while the loss of a single account can be tragic for the individual user (and in some systems, the loss of a single password can have massive consequences!), for the system operator, it is the overall health of the system that matters. There is, in any system, a point at which enough accounts have been compromised that the system itself can no longer secure any information. This not only means the system can no longer hide information, it also means transactions within the system can no longer be trusted.
The number of compromised accounts varies based on the kind of system in view; effectively breaching Continue reading
Tech Heavyweights Create Open Source Project to Transfer Data
 Google, Facebook, Twitter, and Microsoft are behind the initiative. So far, Amazon and Apple are not part of the group.
Google, Facebook, Twitter, and Microsoft are behind the initiative. So far, Amazon and Apple are not part of the group.
Where in the World is NSX?
VMware NSX is going worldwide! We’ll be out and about through the end of the year, spreading networking and security love across America, Asia Pacific, and Europe. Our goal is to help agile organizations move toward a Virtual Cloud Network with consistent connectivity, branch optimization, and security across all infrastructure.
Whether we’ll be at a booth, product demo, talk, or otherwise – we want to connect! Join us at any of the major conferences and NSX upcoming events listed below to chat with our product experts. And, if you think you’ll be in attendance, be sure to tweet at us to let us know!

NSX Upcoming Events
Checkpoint CPX – 2/4
When: February 2 – 4, 2019
Where: Las Vegas, NV
Click here to learn more
Networking Field Day – 2/13
When: February 13 – 15, 2019
Where: Palo Alto, CA
Click here to learn more
Mobile World Congress – 2/25
When: February 25 – 28, 2019
Where: Barcelona, Spain
Click here to learn more
RSAC – 3/4
When: March 4 – 8, 2019
Where: San Francisco, CA
Click here to learn more
Cisco Live APJ– 3/5
When: March 5 Continue reading
Securing U.S. Democracy: Athenian Project Update


Last December, Cloudflare announced the Athenian Project to help protect U.S. state and local election websites from cyber attack.
Since then, the need to protect our electoral systems has become increasingly urgent. As described by Director of National Intelligence Dan Coats, the “digital infrastructure that serves this country is literally under attack.” Just last week, we learned new details about how state election systems were targeted for cyberattack during the 2016 election. The U.S. government’s indictment of twelve Russian military intelligence officers describes the scanning of state election-related websites for vulnerabilities and theft of personal information related to approximately 500,000 voters.
This direct attack on the U.S. election systems using common Internet vulnerabilities reinforces the need to ensure democratic institutions are protected from attack in the future. The Athenian Project is Cloudflare’s attempt to do our part to secure our democracy.
Engaging with Elections Officials
Since announcing the Athenian Project, we’ve talked to state, county, and municipal officials around the country about protecting their election and voter registration websites. Today, we’re proud to report that we have Athenian Project participants in 19 states, and are in talks with many more. We have also strategized with civil Continue reading
Rethink Your Security Infrastructure
 A software-driven approach to security makes advanced capabilities possible even on a tight budget.
A software-driven approach to security makes advanced capabilities possible even on a tight budget.
IPv6 in China

Photo by chuttersnap / Unsplash
At the end of 2017, Xinhua reported that there will be 200 Million IPv6 users inside Mainland China by the end of this year. Halfway into the year, we’re seeing a rapid growth in IPv6 users and traffic originating from Mainland China.
Why does this matter?
IPv6 is often referred to the next generation of IP addressing. The reality is, IPv6 is what is needed for addressing today. Taking the largest mobile network in China today, China Mobile has over 900 Million mobile subscribers and over 670 Million 4G/LTE subscribers. To be able to provide service to their users, they need to provide an IP address to each subscriber’s device. This means close to a billion IP addresses would be required, which is far more than what is available in IPv4, especially as the available IP address pools have been exhausted.
What is the solution?
To solve the addressability of clients, many networks, especially mobile networks, will use Carrier Grade NAT (CGN). This allows thousands, possibly up to hundreds of thousands, of devices to be shared behind a single internet IP address. The CGN equipment can be very expensive to scale and further, given the Continue reading
Containers-as-a-Service is a Fresh Battleground for Cloud Giants
 Half of container users started less than 12 months ago, providing new blood for AWS, Azure, Google, Docker, VMware, Red Hat to fight over.
Half of container users started less than 12 months ago, providing new blood for AWS, Azure, Google, Docker, VMware, Red Hat to fight over.
Commercial Kubernetes Services: There’s an App for That
 The Google Cloud Platform Marketplace updates its previously launched Cloud Launcher service and offers applications that are tested and vetted to work on Kubernetes.
The Google Cloud Platform Marketplace updates its previously launched Cloud Launcher service and offers applications that are tested and vetted to work on Kubernetes.
Security Vendor Claims 98 Percent of Serverless Deployments at Risk
 The company scanned thousands of serverless-based apps running in production on AWS, with 16 percent of those at risk considered "serious."
The company scanned thousands of serverless-based apps running in production on AWS, with 16 percent of those at risk considered "serious."
Clark County Embraces Intrinsic Security with VMware NSX Data Center
Allen Tyson is a Senior Network Analyst at Clark County, located in the State of Nevada. Clark County encompasses the City of Las Vegas, and sees 47 million visitors each year. With roughly 10,000 employees and 38 departments, Allen has a large network to maintain.
Alex Berger, Networking and Security Product Marketing Manager, spoke with Allen about software-defined networking (SDN), and what led Clark County to choosing VMware NSX Data Center.
The Power of Social Media Communities
When a forward-thinking Deputy Chief Information Officer began talking about SDN, Allen did his due diligence to decide on the best option for Clark County. He took to social media to determine whether that choice would be NSX Data Center or Cisco ACI.
“First thing I did was I got on Twitter,” Allen explains. “It seemed like NSX was capable of doing a little bit more [than Cisco ACI] and it also seemed like the communities behind NSX and the people who were using NSX and the ability that I had to get a response from people was greater on the NSX side. And so, I started looking more into NSX.”
Allen was looking for stories from other customers with similar Continue reading
Corelight and Databricks Combine Forces for Threat Detection, Remediation, and Analytics
 Both Corelight and Databricks are based on open source technologies — Corelight on Bro and Databricks on Apache Spark. While the open source technologies have been combined, this is the first time the companies' commercial versions of software will integrate.
Both Corelight and Databricks are based on open source technologies — Corelight on Bro and Databricks on Apache Spark. While the open source technologies have been combined, this is the first time the companies' commercial versions of software will integrate.


