Insider Threat Management Startup ObserveIT Closes $33M Series B
 One-quarter of all security incidents involve insiders, according to Verizon’s annual Data Breach Investigations Report.
One-quarter of all security incidents involve insiders, according to Verizon’s annual Data Breach Investigations Report.
Smart Shopping Starts Today!
Let’s face it – things are different now than when we were kids.
I grew up with technology. My weekends consisted of frantically switching out floppy disks while on 13-inch-green-screen missions to destroy cubism-esque dragons, orcs and whatever else I could with my wizard powers. It taught me critical reasoning, innovative thinking, and gave me the courage to try new things.
Now that I’m a mom, I’m an advocate for my kids to use tech. But today’s tech is different. Now the Internet is everywhere and it’s a part of our everyday lives, in everyday things. Coffeemakers, toothbrushes, toasters, televisions and, yes – even teeth.
Did you ever think we’d have connected homes, let alone bras that might detect breast cancer?
These everyday things are known as the Internet of Things – IoT for short. It’s already everywhere.
Manufacturers are building connected things faster than most of us can keep up. While that means there’s lots of cool things hitting the shelves, many haven’t been built with our security or privacy in mind. That’s why we hear stories ranging from the somewhat humorous to the terrifying.
But we’re hungry for IoT devices – buying them as fast as manufacturers can Continue reading
Cloud, Container, and Serverless Developers Are In Big Demand
 Sylabs is offering $2,500 to any non-employee that refers a developer that is eventually hired by the company.
Sylabs is offering $2,500 to any non-employee that refers a developer that is eventually hired by the company.
The Week in Internet News: Startup Finds a Way to Glue Fiber to Roadways
Why don’t we glue it in the road? A technology startup has patented a way to integrate broadband fiber to blacktop, reports Motherboard. The patented technique, inspired by dentistry, uses a blend of resins to stick fiber optic cables to roads.
Major spending to fix IoT security: The Internet of Things security market will grow to US$6 billion by 2023, with spending to rise 300 percent between 2018 and 2023, according to Juniper Research. However, poor long-term device support and little fear of ramifications will keep security spending on connected homes lagging behind other markets, the research firm says.
Data breaches cost big bucks: The average cost of a data breach is $3.86 million, up more than 6 percent from last year, according to a study from IBM and the Ponemon Institute. Compromised organizations took 197 days to identify a breach and an additional 69 days to contain it, reports IT Pro. A data breach cost organizations an average of $148 per lost or stolen record.
AI takes over the world: About three-quarters of all consumers have interacted with artificial intelligence systems, reports ComputerWeekly.com. A Capgemini survey of 10,000 consumers found, however, that more than half of consumers prefer Continue reading
IETF 102, Day 1: IETF arrive à Montréal
Tomorrow sees kickoff of the Working Groups sessions at IETF 102 in Montreal, Canada, we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Monday is an important day, with meetings of the TLS, 6MAN and SIDROPS Working Groups, along with two other IoT related groups.
6MAN commences at 09.30 EDT/UTC-4, and has six new drafts up for discussion covering IPv6 Neighbor Discovery Extensions for Prefix Delegation, IPv6 VPNs, ICMPv6, OAM in Segment Routing Networks with an IPv6 Data plane, allowing low or zero valid lifetimes to be accepted in Router Advertisement Prefix Information Options where it’s known that there can only be one router on the link; as well as introducing a new IPv6 ‘unrecognised’ option for ICMPv6 that conveys whether an underlying network can transmit IPv6 packets.
There are also three working group sponsored drafts, adopted from the last meeting. Privacy Extensions for Stateless Address Autoconfiguration in IPv6 describes an extension that causes nodes to generate global scope addresses from interface identifiers that change over time; IPv6 Segment Routing Header specifies how a node can steer a packet through a controlled set of instructions (segments) by prepending an SR header Continue reading
DNS-Over-TLS Built-In & Enforced – 1.1.1.1 and the GL.iNet GL-AR750S
 GL.iNet GL-AR750S in black, same form-factor as the prior white GL.iNet GL-AR750. Credit card for comparison.
GL.iNet GL-AR750S in black, same form-factor as the prior white GL.iNet GL-AR750. Credit card for comparison.
Back in April, I wrote about how it was possible to modify a router to encrypt DNS queries over TLS using Cloudflare's 1.1.1.1 DNS Resolver. For this, I used the GL.iNet GL-AR750 because it was pre-installed with OpenWRT (LEDE). The folks at GL.iNet read that blog post and decided to bake DNS-Over-TLS support into their new router using the 1.1.1.1 resolver, they sent me one to take a look at before it's available for pre-release. Their new router can also be configured to force DNS traffic to be encrypted before leaving your local network, which is particularly useful for any IoT or mobile device with hard-coded DNS settings that would ordinarily ignore your routers DNS settings and send DNS queries in plain-text.
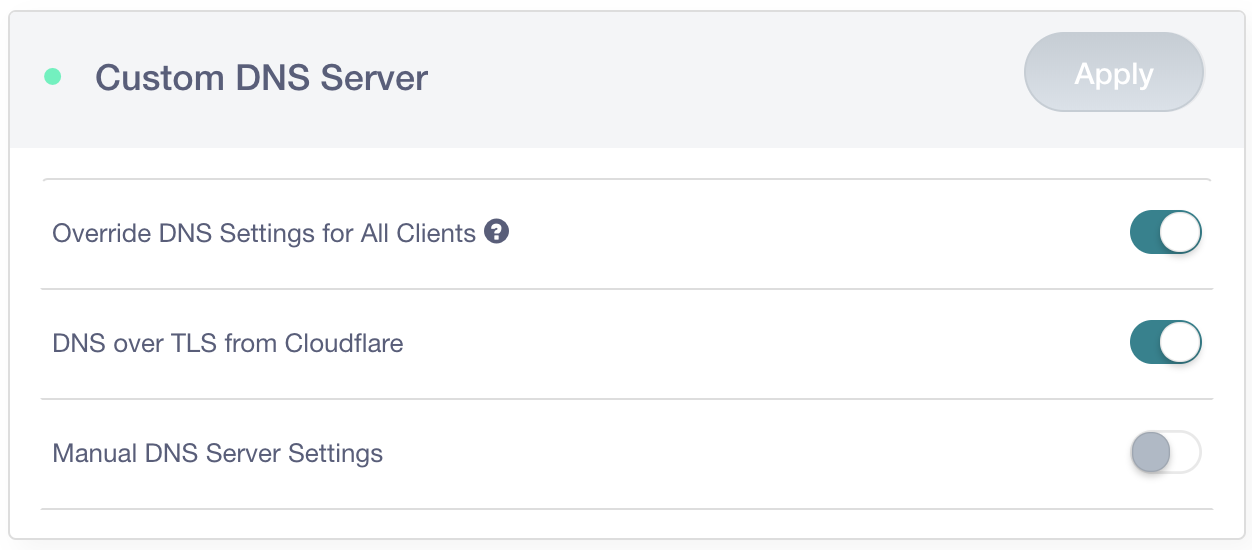
In my previous blog post I discussed how DNS was often the weakest link in the chain when it came to browsing privacy; whilst HTTP traffic is increasingly encrypted, this is seldom the case for DNS traffic. This makes it relatively trivial for an intermediary to work out what site you're sending Continue reading
ISOC’s Hot Topics at IETF 102
The 102nd meeting of the IETF starts tomorrow in Montreal, Canada. This is will be the third time that an IETF has been held in the city, and tenth time in Canada – the first being way back in 1990.
The ISOC Internet Technology Team is as always highlighting the latest IPv6, DNSSEC, Securing BGP, TLS and IoT related developments, and we discuss these in detail in our Rough Guide to IETF 102. But we’ll also be bringing you daily previews of what’s happening each day as the week progresses.
Below are the sessions that we’ll be covering in the coming week. Note this post was written in advance so please check the official IETF 102 agenda for any updates, room changes, or final details.
Monday, 16 July 2018
- IPv6 Maintenance (6man) – Laurier @ 09.30-12.00 UTC-4
- Authentication and Authorization for Constrained Environments (ace) – Viger @ 09.30-12.00 UTC-4
- IP Wireless Access in Vehicular Environments (ipwave) – Laurier @ 13.30-15.30 UTC-4
- SIDR Operation (sidrops) – Viger @ 13.30-15.30 UTC-4
- Transport Layer Security (tls) – Place du Canada @ 13.30-15.30 UTC-4
Tuesday, 17 July 2018
- Distributed Mobility Management (dmm) – Van Horne @ 09.30-12.00 UTC-4
- Continue reading
Security Vendor Fortinet Sells SD-WAN Directly to Customers
 According to Gartner research, there are more than 60 SD-WAN vendors, and 90 percent of them offer little or no security. Fortinet’s SD-WAN has a single controller to manage both the security and the other SD-WAN features.
According to Gartner research, there are more than 60 SD-WAN vendors, and 90 percent of them offer little or no security. Fortinet’s SD-WAN has a single controller to manage both the security and the other SD-WAN features.
Bug Bounties Jump 33% With $11.7M Paid to Hackers Last Year
 Some companies and governments are now offering as much as $250,000 to find and fix security flaws, according to the Hacker-Powered Security Report.
Some companies and governments are now offering as much as $250,000 to find and fix security flaws, according to the Hacker-Powered Security Report.
Your IoT security concerns are stupid
Lots of government people are focused on IoT security, such as this recent effort. They are usually wrong. It's a typical cybersecurity policy effort which knows the answer without paying attention to the question. Government efforts focus on vulns and patching, ignoring more important issues.Check Point: Cryptominers Oust Ransomware as Most Prominent Malware
 Check Point’s mid-year report on cyber attack trends found that in 2018 new (and old) strains of malware are attacking cloud environments, mobile devices, and other burgeoning technologies.
Check Point’s mid-year report on cyber attack trends found that in 2018 new (and old) strains of malware are attacking cloud environments, mobile devices, and other burgeoning technologies.
Netskope Scoops Up Sift Security for More Cloud Threat Protection
 Sift’s product, Cloud Hunter, uses machine learning, analytics, and graph visualization capabilities to detect and respond to threats across infrastructure-as-a-service platforms.
Sift’s product, Cloud Hunter, uses machine learning, analytics, and graph visualization capabilities to detect and respond to threats across infrastructure-as-a-service platforms.
Huawei Faces Scrutiny Over Claims It Infiltrated a Closed Facebook TIP Meeting
 A former Huawei employee says he was fired for refusing to use a fake company name to gain access to the private TIP gathering. Huawei says this is just a labor dispute, and the claims are groundless.
A former Huawei employee says he was fired for refusing to use a fake company name to gain access to the private TIP gathering. Huawei says this is just a labor dispute, and the claims are groundless.
What Do VCs Want in Security Startups? Dell Tech Capital Dishes
 Dell Technologies’ venture arm invests about $100 million annually in technology startups, and about a quarter of that goes to security companies.
Dell Technologies’ venture arm invests about $100 million annually in technology startups, and about a quarter of that goes to security companies.
The VMware NSX® Roadshow is Coming to a City Near You
VMware NSX enterprise-grade solutions support your path toward network virtualization, micro-segmentation, application availability, IT automation, and cross-cloud architecture. And while we mostly live in the cloud, we’re coming back to Earth and taking our proverbial show on the road with the VMware NSX® Roadshow. It all goes down this summer, in a city near you!
VMware NSX® Roadshow workshops are designed specifically for networking and security professionals and delivered in a casual, interactive setting. Each participant gets the chance to engage one-on-one with VMware NSX product experts to ask questions, get hands-on help, and network with other people interested in, well, networks!
When you sign up, you’ll learn how agile organizations are using a Virtual Cloud Network as a north star to guide them toward creating a network built on best practice pillars like consistent connectivity, branch optimization, and security across all infrastructure.

Upcoming Events
Join us to talk shop, meet and greet, get deep drives on hot topics, product demos, and guided one-on-ones with product experts in one of the following cities:
Detroit – 7/17
When: July 17, 2018, from 1:00 P.M. to 4:30 P.M.
Where: Westin Southfield Detroit
1500 Town Center
Southfield, Continue reading
Dark Web Sells Airport Network Access For Cheap, McAfee Says
 Threat researchers discovered that access to multiple U.S. government systems are being sold worldwide on these shops for as little as $10.
Threat researchers discovered that access to multiple U.S. government systems are being sold worldwide on these shops for as little as $10.
The Next Evolution of SD-WAN
 In this eBrief from SDxCentral, we take an in-depth look at some of the latest developments in SD-WAN and how the technology promises to provide better security, as well as new features.
In this eBrief from SDxCentral, we take an in-depth look at some of the latest developments in SD-WAN and how the technology promises to provide better security, as well as new features.
Security Is the Top Concern for Enterprises as They Select a Data Center Switch Vendor, Says IHS Markit
 Cisco, Dell, HPE, Juniper, and Huawei were identified as the top five data center Ethernet switch vendors by enterprises.
Cisco, Dell, HPE, Juniper, and Huawei were identified as the top five data center Ethernet switch vendors by enterprises.
AT&T Beefs Up Security With AlienVault Acquisition
 AT&T says it will continue to invest in the Open Threat Exchange, an open threat intelligence community started by AlienVault.
AT&T says it will continue to invest in the Open Threat Exchange, an open threat intelligence community started by AlienVault.
Cool Hacks Spotlight: DART
Docker container platforms are being used to support mission-critical efforts all over the world. The Planetary Defense Coordination Office out of NASA is using Docker’s platform to support a critical mission that could potentially affect everyone on the planet! The office is responsible for tracking near-earth asteroids, characterizing them and determining how to deflect them if one were to find its way to earth.
DART, led by the Johns Hopkins Applied Physics Laboratory by way of NASA, is the Double Asteroid Redirection Test. The team has chosen a potentially hazardous asteroid to hit in order to measure the impact and determine how effective this type of mission would be.
Developing the software for this mission is no easy feat, because space is hard! The team has one shot to make this mission work, there’s no rebooting in space. Space physics constraints lead to very low bandwidth, and low density memory due to the turbulent effects of radiation. So what did the software team want to solve for using Docker? Hardware scarcity. The development systems used in this project are very expensive ($300K), so not every developer is going to get their own system. This led to a time constraint, Continue reading