Research: Bridging the Air Gap
Way back in the old days, the unit I worked at in the US Air Force had a room with a lot of equipment used for processing classified information. Among this equipment was a Zenith Z-250 with an odd sort of keyboard and a very low resolution screen. A fine metal mesh embedded in a semi-clear substrate was glued to the surface of the monitor. This was our TEMPEST rated computer, on which we could type up classified memos, read classified email, and the like. We normally connected it to the STU-3 through a modem (remember those) to send and receive various kinds of classified information.
Elovici, Mordechai Guri, Yuval. “Bridgeware: The Air-Gap Malware.” Accessed May 13, 2018. https://cacm.acm.org/magazines/2018/4/226377-bridgeware/abstract.
The idea of TEMPEST begins way back in 1985, when a Dutch researcher demonstrated “reading” the screen of a computer using some relatively cheap, and easy to assemble, equipment, from several feet away. The paper I’m looking at today provides a good overview of the many ways which have been discovered since this initial demonstration to transfer data from one computer to another across what should be an “air gap.” For instance, the TEMPEST rated computer described Continue reading
End-to-End Segmentation with NSX SD-WAN and NSX Data Center
As you may have read earlier this month, NSX Data Center and NSX SD-WAN by VeloCloud are part of the expanded VMware NSX portfolio to enable virtual cloud networking. A Virtual Cloud Network provides end-to-end connectivity for applications and data, whether they reside in the data center, cloud or at the edge. I wanted to follow up, and walk through an example using NSX Data Center and NSX SD-WAN of how one could build an end to end segmentation model from the data center to the branch.
 NSX SD-WAN Segmentation
NSX SD-WAN Segmentation
Beyond lowering cost and increasing agility and simplicity of branch connectivity, one of the key values provided by NSX SD-WAN by VeloCloud is enterprise segmentation, which provides isolated network segments across the entire enterprise, enabling data isolation or separation by user or line of business, support for overlapping IP addresses between VLANs and support for multiple tenants. NSX SD-WAN provides this segmentation using a VRF-like concept with simplified, per-segment topology insertion. This is accomplished by inserting a “Segment ID” into the SD-WAN Overlay header as traffic is carried from one NSX SD-WAN Edge device to another Edge. Networks on the LAN-side of an NSX SD-WAN Edge with different Continue reading
Some notes on eFail
I've been busy trying to replicate the "eFail" PGP/SMIME bug. I thought I'd write up some notes.PGP and S/MIME encrypt emails, so that eavesdroppers can't read them. The bugs potentially allow eavesdroppers to take the encrypted emails they've captured and resend them to you, reformatted in a way that allows them to decrypt the messages.
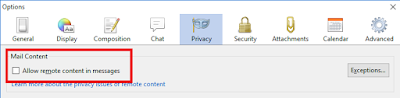
Disable remote/external content in email
The most important defense is to disable "external" or "remote" content from being automatically loaded. This is when HTML-formatted emails attempt to load images from remote websites. This happens legitimately when they want to display images, but not fill up the email with them. But most of the time this is illegitimate, they hide images on the webpage in order to track you with unique IDs and cookies. For example, this is the code at the end of an email from politician Bernie Sanders to his supporters. Notice the long random number assigned to track me, and the width/height of this image is set to one pixel, so you don't even see it:Such trackers are so pernicious they are disabled by default in most email clients. This is an example of the settings in Thunderbird:
The problem is Continue reading
Leaking securely, for White House staffers
Spencer Ackerman has this interesting story about a guy assigned to crack down on unauthorized White House leaks. It's necessarily light on technical details, so I thought I'd write up some guesses, either as a guide for future reporters asking questions, or for people who want to better know the risks when leak information.Symantec Cops to Internal Investigation, Sends Stock Crashing 35%
 The mysterious probe isn’t related to a breach or any security concern about its products.
The mysterious probe isn’t related to a breach or any security concern about its products.
Inaudible voice commands: the long-range attack and defense
Inaudible voice commands: the long-range attack and defense Roy et al., NSDI’18
Although you can’t hear them, I’m sure you heard about the inaudible ultrasound attacks on always-on voice-based systems such as Amazon Echo, Google Home, and Siri. This short video shows a ‘DolphinAttack’ in action:
To remain inaudible, the attack only works from close range (about 5ft). And it can work at up to about 10ft when partially audible. Things would get a whole lot more interesting if we could conduct inaudible attacks over a longer range. For example, getting all phones in a crowded area to start dialling your premium number, or targeting every device in an open plan office, or parking your car on the road and controlling all voice-enabled devices in the area. “Alexa, open my garage door…”. In today’s paper, Roy et al. show us how to significantly extend the range of inaudible voice command attacks. Their experiments are limited by the power of their amplifier, but succeed at up to 25ft (7.6m). Fortunately, the authors also demonstrate how we can construct software-only defences against the attacks.
We test our attack prototype with 984 commands to Amazon Echo and 200 commands to smartphones Continue reading
Protego Scores $2M in Seed Funds to Target Serverless Security
 A recent report found 21 percent of open source serverless projects contained at least one critical vulnerability or misconfiguration.
A recent report found 21 percent of open source serverless projects contained at least one critical vulnerability or misconfiguration.
Cycle Pedals Bare Metal Container Orchestrator as Kubernetes Alternative
 The barebones platform is available through Packet's bare metal compute, network, and storage resources.
The barebones platform is available through Packet's bare metal compute, network, and storage resources.
History Of Networking – Geoff Houston – BGP Security
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Geoff Houston – BGP Security appeared first on Network Collective.
NetApp Partners With Google, Ups the Ante in its Cloud-Connected Game
 Analysts praised the company for its ongoing effort to transition from a traditional storage vendor to a cloud data services company
Analysts praised the company for its ongoing effort to transition from a traditional storage vendor to a cloud data services company
RIPE NCC: The Future of BGP Security
I was recently invited to a webinar for the RIPE NCC about the future of BGP security. The entire series is well worth watching; I was in the final session, which was a panel discussion on where we are now, and where we might go to make BGP security better.
Masergy Picks Bitglass Cloud Security Tech for Managed CASB Service
 The managed security service provider tested Netskope’s and McAfee Skyhigh’s technology before choosing Bitglass.
The managed security service provider tested Netskope’s and McAfee Skyhigh’s technology before choosing Bitglass.
Aqua Security Sprinkles Support Over CRI-O Kubernetes Runtime Platform
 CRI-O was launched as a lighter alternative to using Docker as the runtime for Kubernetes.
CRI-O was launched as a lighter alternative to using Docker as the runtime for Kubernetes.
What is BGP Hijacking, Anyway?
Two weeks ago, we learned about yet another routing security incident, namely the hijack of BGP routes to the Amazon DNS infrastructure, used as a stepping stone to steal about $150,000 of Ethereum cryptocurrency from MyEtherWallet.com. We’ve been talking a lot lately about BGP hijacking, digging into the details of what happened in this post. But maybe we need to back up a minute and answer: What in the world is BGP hijacking, anyway, and why does it matter? Here, we’ll explain the basics and how network operators and Internet Exchange Points can join MANRS to help solve the problem.
What is BGP?
BGP, or Border Gateway Protocol, is used to direct traffic across the Internet. Networks use BGP to exchange “reachability information” – networks they know how to get to. Any network that is connected to the Internet eventually relies on BGP to reach other networks.
What is BGP Hijacking?
In short, BGP hijacking is when an attacker disguises itself as another network; it announces network prefixes belonging to another network as if those prefixes are theirs. If this false information is accepted by neighboring networks and propagated further using BGP, it distorts the “roadmap” of the Continue reading
Zero Trust. Maximize Network Virtualization and Micro-segmentation
It’s official: when it comes to security threats, the question IT teams should be asking is not if but when. VMware recently commissioned Forrester Consulting to evaluate how organizations are improving the security of their infrastructure through network virtualization and micro-segmentation. Analysis found that 92% of respondents reported having faced minor security incidents in the last 12 months alone, while 65% of respondents endured a major incident in the same time span. These figures seal the deal; the naïve days of preparing for potential issues are long gone. Cyber threats are real, imminent, and happen often.

Companies today attribute more of their security issues to improper network segmentation than to the volume of threats overall. In response, leaders across industries are turning to network virtualization – specifically the Zero Trust security model – as a key strategy in combating threats. This strategy posits that whether a network is labeled secure or insecure, both should be treated as equally vulnerable. Further, the Zero Trust model supports the argument that ”traditional, perimeter-based security configurations are no longer a sufficient measure for protecting the network, and highlights steps companies can take to better secure their network, starting with network virtualization Continue reading
Zero Trust. Maximize Network Virtualization and Micro-segmentation
 VMware recently commissioned Forrester Consulting to evaluate how organizations are improving the security of their infrastructure through network virtualization and micro-segmentation.
VMware recently commissioned Forrester Consulting to evaluate how organizations are improving the security of their infrastructure through network virtualization and micro-segmentation.
NetScout Revenue Sinks 27% in Q4 Fiscal 2018
 The company also reported more downward guidance for its upcoming fiscal year, but remains optimistic about its product revenue.
The company also reported more downward guidance for its upcoming fiscal year, but remains optimistic about its product revenue.
Carbon Black Stock Raises $125 Million in Public Debut
 The security company priced its IPO at the high end of its $17-$19 range.
The security company priced its IPO at the high end of its $17-$19 range.
Fortinet Quadruples Q1 Revenues, Posts Triple-Digit Cloud Growth
 Investors were not as impressed as the company's stock was trading down early Friday off of a recent 52-week high.
Investors were not as impressed as the company's stock was trading down early Friday off of a recent 52-week high.
Spectre Next Gen Bugs Hit Intel CPUs, Cisco Catches Cryptojacking Threats
 Intel classified four of the new flaws as “high risk” and four as “medium,” and it's working on patches.
Intel classified four of the new flaws as “high risk” and four as “medium,” and it's working on patches.
 NSX SD-WAN Segmentation
NSX SD-WAN Segmentation