Upcoming Changes to the AWX Project
By Matthew Jones, Chief Architect, Ansible Automation at Red Hat
Back in 2013, a small team of engineers worked for over a year to make the first commercial release of Ansible Tower (before we expanded and evolved to Ansible Automation Platform) and during that time we put down the foundation of an application that I’m immensely proud of.
We, the original architects of Tower, were trying to find the best way to create a system that would allow running Ansible at scale for hundreds of thousands of servers. We wanted there to be a way to not just manage those servers but store the results of that automation and provide auditability and traceability. It needed to make Ansible functional for large teams and it succeeded.
Today, we’re not just talking about hundreds of thousands. We’re thinking in the millions and tens of millions, we’re managing automation for some of the largest IT organizations in the world. And we’re not just managing servers. In the intervening years we’ve been automating containers, cloud platforms, network devices, storage, IoT devices and PLCs (among other things). One of the main challenges that we’re facing is that some of the architectural decisions we made Continue reading
Mastering AWS with amazon.aws 7.0: A Dive into New Modules for Enhanced Security and Seamless Migrations
As the technology landscape continues to evolve, the latest release of the Red Hat Ansible Certified Content Collection for amazon.aws introduces a suite of powerful modules that redefine the boundaries of automation within Amazon Web Services (AWS) while redefining how organizations approach security deployments and seamless migrations within the AWS ecosystem.
In our previous blog post, "What's New: Cloud Automation with amazon.aws 7.0.0," we presented the latest release, outlining the changes, new features and newly supported modules. In this blog post, we embark on an exploration of two interesting use cases that highlight the capabilities of these new Ansible-supported modules included in the amazon.aws 7.0 release. Let’s dive into it!
|
|
Use Case #1: Implementing Security Best Practices and Access Control for AWS Resources
Security in AWS is more critical than ever before, and the collection for AWS, amazon.aws 7.0, is up to the challenge with a host of new Identity and Access Continue reading
What’s New: Cloud Automation with amazon.aws 7.0.0
When it comes to Amazon Web Services (AWS) infrastructure automation, the latest release of the certified amazon.aws Ansible Content Collection for Red Hat Ansible Automation Platform brings a number of enhancements to improve the overall user experience and speed up the process from development to production.
This blog post goes through changes and highlights what’s new in the 7.0.0 release of this Ansible Content Collection. We have included numerous features, plugins, bug fixes, and code quality improvements that further enhance the amazon.aws collection. Let's go through some of them!
|
|
Forward-looking Changes
Much of our work in the 7.0.0 release has been focused on the following areas:
- Enhancing several modules from the upstream community.
- Promoting modules to being formally supported by Red Hat.
- Improving the overall quality of the collection code.
- Releasing various new enhancements and clarifying support policies.
New Modules
This release brings with it a number of new supported modules that have been Continue reading
While you sleep, Automate resolving Dynatrace problem alerts and report them to ServiceNow!
Integrating observability tools with automation is paramount in the realm of modern IT operations, as it fosters a symbiotic relationship between visibility and efficiency. Observability tools provide deep insights into the performance, health, and behavior of complex systems, enabling organizations to proactively identify and rectify issues before they escalate.
When seamlessly integrated with automation frameworks, these tools empower businesses to not only monitor but also respond to dynamic changes in real time. This synergy between observability and automation enables IT teams to swiftly adapt to evolving conditions, minimize downtime, and optimize resource utilization. By automating responses based on observability data, organizations can enhance their agility, reduce manual intervention, and maintain a robust and resilient infrastructure. In essence, using observability with automation is indispensable for achieving a proactive, responsive, and streamlined operational environment in the fast-paced and complex landscape of today’s technology.
In this blog post, we will look at a common use case involving the monitoring of processes on both bare metal and virtual machines. Our exploration will focus on utilizing Dynatrace's OneAgent, a deployed binary file on hosts that encompasses a suite of specialized services meticulously configured for environment monitoring. These services actively gather telemetry metrics, capturing insights into Continue reading
Agentless configuration drift detection and remediation
Over time, application owners find themselves compelled to continuously refine their applications and the underlying infrastructure to enhance the products they deliver, whether to internal or external customers. These modifications inevitably lead to changes in the configuration of both applications and infrastructure. While some of these changes may be benign, others can unintentionally steer the systems away from their securely configured state, a phenomenon commonly referred to as "configuration drift." Left unaddressed, the extent of this drift can introduce substantial risks to the organization.
Traditionally, agent-based automation configuration management tools have been favored as the primary solution for tackling configuration drift.
However, is this approach genuinely the most effective strategy?
According to AWS's well-architected framework, the concept of a Fault Isolation Zone (FIZ) is crucial, characterized by isolation boundaries like Availability Zones (AZ), Regions, control planes, and data planes. While this concept is centered in a cloud context, the principles behind FIZ remain relevant in traditional data centers and at the network edge. The core idea is to minimize the impact of errors, particularly human misconfigurations, that can propagate beyond a defined Fault Isolation Zone.
Are misconfigurations resulting from human error still a matter of concern?
5 use cases for automating your infrastructure with Ansible Automation Platform
Infrastructure automation is an area where systems administrators and IT operations teams can see some of the biggest benefits from automation, including time savings, reducing tedious manual work, and improving the overall health of their systems. In this blog, I've identified the top 5 infrastructure automation use cases for Ansible Automation Platform that you can deploy in your own environment, and I've incorporated new capabilities like Event-Driven Ansible to make managing your infrastructure even easier.
- Provisioning Red Hat Enterprise Linux with Ansible Automation Platform
Before you get started with any automation project, we typically recommend using automation analytics to plan and predict the potential cost savings to help prioritize which automation projects will deliver the biggest time and cost savings.
Then you can use Ansible Automation Platform to create a workflow to build or configure a cloud or datacenter instance for RHEL, while using surveys to gather additional user input to enable further customization to meet any system requirements. You can even introduce an IT service management ticketing option, then review the job success and confirm service availability.
Watch this video to see it in action:
- Managing Configuration and Drift with Ansible Automation Platform
Ongoing Continue reading
Fact-Gathering with Event-Driven Ansible for Microsoft Windows ITSM
The use of Event-Driven Ansible to enable fact gathering from events is considered a “Getting Started” type of use case, but it can be extremely powerful. This use case is simple and it is what we consider a “Read Only” type of action, meaning that we are not making any changes, but we are using the event to trigger a fact gathering process which we can later publish to the IT Service Management system.
The benefit with this is we are able to provide consistent automated troubleshooting and fact gathering which is used to enrich the ticketing systems, so when our engineers have a look at the incident, they have all the information they need to decide on the next steps to resolve the issue or situation. This can potentially save many hours of toil and ultimately save an organization money from reduced down time and faster resolutions. But, we are assuming that our technical teams will know what to do with this event data.
What if we could assist with filling the gap when an incident takes place, and we could receive information or even options on how to resolve the issues? This is where we could use Continue reading
Ansible can help with the Cisco IOS XE Software Web UI Privilege Escalation Vulnerability
CVE-2023-20198
Reference: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
Overview
Cisco recently published an advisory pertaining to an active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
Recommendations using Red Hat Ansible Automation Platform
In this blog, I will discuss a simple playbook that can help network admins quickly identify and remediate affected devices. To add additional capabilities for a large production environment, Red Hat Ansible Automation Platform could enhance the playbook run with additional capabilities (ticketing integrations, roles based access, workflow, self service, etc.).
Vulnerable Products
All Cisco IOS-XE based products are potentially at risk. The example playbook is located here.
In the example playbook we will explore its functionality using one of the Cisco Sandbox always-on routers
Determine the HTTP Server Configuration
The following portion of the playbook will determine the HTTP Server Configuration and print the results.
Cisco strongly recommends that customers disable the HTTP Continue reading
NEW!!! Getting started landing page for Ansible Automation Platform on Azure
This blog is co-authored by Tomas Znamenacek and Hicham (he-sham) Mourad
Introduction
We’re so excited to introduce you to the newest addition to Red Hat Ansible Automation Platform on Microsoft Azure – The new landing page! Now with new deployments, a single web page that consolidates all you need to know about Ansible Automation Platform on Azure, how to get started, as well as links to the Ansible Automation Platform applications, is now accessible.
Upon arriving at this getting started landing page, you will see three tiles on the overview page. You have the ability to launch each of the following Ansible applications from the tiles: automation controller, private automation hub, and automation analytics, as well as a direct link to the managed Azure product documentation.
The bottom portion of the overview page sets you up for success by providing links to all the enablement content you need. It specifically provides links to Ansible Automation Platform on Azure Knowledge Base articles, documentation, and how to contact and request support.
Another important area is the “Managed Azure Maintenance and Feature Updates” that provides the link to the maintenance updates and feature releases to Ansible Automation Platform on Azure. Stay Continue reading
Red Hat Insights Collection for Event-Driven Ansible

Event-Driven Ansible became generally available in Ansible Automation Platform 2.4. As part of the release, Red Hat Insights and Ansible teams collaborated to implement and certify a Red Hat Insights collection integrating Insights events as a source of events for Ansible Automation Platform. This provides a consistent way to receive and handle events triggered from Insights to drive and track automation within the Ansible Automation Platform. The collection is available for installation on Ansible automation hub.
In this article, we explore how to get, configure and use the Red Hat Insights collection for Event-Driven Ansible, and provide an end-to-end example of an automation flow using Ansible Automation Platform and its Event-Driven Ansible functionality. Our goal is to automate the creation of a ServiceNow incident ticket with all relevant information when malware is detected by Insights on one of our Red Hat Enterprise Linux (RHEL) systems. We show how we can track and audit all automation from the Event-Driven Ansible controller as part of Ansible Automation Platform.
Introducing a new certified collection for Event-Driven Ansible
In a previous article, we looked at exposing and consuming Insights events to drive automation with Event-Driven Ansible. We validated that events triggered Continue reading
Seeding Ansible Automation Platform Content At Installation Time
In a previous blog, I announced the tech preview of containerized Red Hat Ansible Automation Platform. With that we introduced a new feature to enable you to pre-seed configuration and content at installation time. This blog will take you through how that works.
At Red Hat, we are very lucky to have some super talented people. Some of these great folks have worked tirelessly on producing Ansible Content Collections for managing configuration within the platform. Using this as the foundation, we have wrapped enablement around that to provide a fully automated way of doing this, in a seamless fashion.
The Benefits
Many people today already use a configuration-as-code (CaC) approach to managing the platform and laying down standards for their users. If that’s your case, then this simply extends and simplifies this capability.
If this is a new concept to you, then these examples may be of interest:
- Standardize your user’s out of the box (OOTB) experience, in one go, at installation time.
- Are there platform artifacts that you always need to apply to each and every installation? Define those as code and simply point the installation at that code and it will pre-configure the platform
- The ability Continue reading
Importing Ansible Validated Content into Private Automation Hub
Introduction
Ansible validated content is a set of collections containing pre-built YAML content (such as playbooks or roles) to address the most common automation use cases. You can use Ansible validated content out-of-the-box or as a learning opportunity to develop your automation skills. It's a trusted starting point to bootstrap your automation: use it, customize it and learn from it!
This content is curated by experts like the Red Hat Automation Community of Practice so:
- Use cases are based on successfully deployed customer examples
- Content creators are trusted and verified subject matter experts
- Content itself adheres to the latest best practices and guidelines issued by Red Hat’s engineering team
- Ansible validated content is tested against supported versions of Red Hat Ansible Automation Platform
Ansible Automation Platform is a trusted delivery system to access and leverage Ansible validated content in your organization.
How can I get this Ansible validated content into my Ansible Automation Platform on clouds (AWS, Azure, Google Cloud) deployment?
To do this there are a few short steps. Let’s walk through these together.
As part of your Ansible Automation Platform on cloud, you will also have a private automation hub. This is your own internal automation content Continue reading
Now serving: Event-Driven Ansible with a dash of durability
In the realm of automation, the ability to respond to events in real-time is a game-changer. At Red Hat, we've been pioneering in this space with Event-Driven Ansible, which can consume messages from various sources like AWS Simple Queue Service (SQS), Azure Service Bus, and Kafka to trigger automated actions. Today, we're excited to delve into a powerful integration pattern involving AWS Lambda, AWS SQS, and Event-Driven Ansible.
Imagine this: A SaaS application sends a webhook POST request. This request triggers a Lambda function, which validates an API key or other payload data, filters the payload, and sends a message to SQS. Event-Driven Ansible subscribes to the queue, consumes the message and triggers an automated action. Let's explore this workflow in detail.
The Workflow
Here's a visual representation of the workflow with AWS Lambda and AWS SQS:
Ideally, in this model, webhook POSTs should selectively be sent to the SQS queue. Rulebooks within Event-Driven Ansible have the ability to validate that a key within the header contains the specified value – but that means the message is already on my queue. I want to stop that from happening. In this case, my Lambda function should be able to validate Continue reading
Ansible Contributor Summit, Durham 2023
Ansible Contributor Summit, Durham 2023

The Ansible Contributor Summit is a full day working session for community contributors to interact with one another and meet with the Ansible development teams behind the projects like AWX, Galaxy NG, Molecule, Ansible Lint and Event-Driven Ansible. We will discuss important issues affecting the Ansible Community and help shape the future of collaboration.
We are happy to have the opportunity to do a second Contributor Summit this year, and this time it will be part of DjangoCon US 2023 in Durham, NC. Our previous experience co-locating the Contributor Summit with another related event was in February in Ghent, Belgium as part of CfgMgmtCamp 2023. It was so successful, we wanted to do it again with another great match.
Hello, Durham!
We will be meeting in the "Bull City", the home of Ansible itself and the inspiration for our beloved mascot, Ansibull. In case you didn't know, the Ansible office overlooks the Durham Bulls Athletic Park, and this mixed with Ansible word play is why you might see mentions of bulls and Ansibulls in Ansible land.
If you can't attend the event in person in Durham, worry not! Ansible Contributor Summit is a hybrid event, Continue reading
Announcing Containerized Ansible Automation Platform
Everything you know and love about Ansible Automation Platform in containerized form
We’re excited to announce something that we’ve been working on for a while now, the technical preview of a containerized Red Hat Ansible Automation Platform solution.
Currently, this will allow you to install and run containerized automation controller, Ansible automation hub, and the Event-Driven Ansible controller services on just one or more underlying RHEL hosts on x86_64 and ARM64 architectures. This does not require a kubernetes-based platform, as it just uses native RHEL podman on top of a RHEL host.
The rationale behind containerized Ansible Automation Platform
As Ansible Automation Platform evolved, we added more services and components into the stack. Over time, the increasing complexity and inter-dependencies between these components have introduced new challenges in terms of maintenance, installation, and support. They have also opened up opportunities for growth and innovation.
Containerized Ansible Automation Platform is the first step towards a more streamlined and improved platform management experience, incorporating our future vision and strategy.
The benefits
Just containerizing existing services was not enough for us, so we set some goals to provide:
- a slimmed down installation experience
- a layered installation approach
- a containerized Continue reading
New Ansible Galaxy
For awhile, the Red Hat Ansible team behind the components Ansible automation hub and Ansible cloud automation hub at console.redhat.com have been on a special ops mission to enhance the galaxy_ng code base that serves the aforementioned components to also serve galaxy.ansible.com, with the intention of replacing galaxy.ansible.com with a fresh code base.
Galaxy, a legacy far far away…
The current Galaxy service has been running at galaxy.ansible.com for many years and is hugely successful in the community. It drives and nurtures Ansible adoption by sharing prebuilt Ansible content that solves many automation challenges.
One of the statistics we are most proud of are the contributions of 33,965 individual automation answers by the community in either Ansible Content Collections or Ansible Roles. Some of the top ranking automation content includes AWS, VMware, Linux, and Windows. Community users are able to download content for free, self-supported and interact with authors via GitHub for any further help or enhancements.
- We are excited to announce that the galaxy.ansible.com code base is being updated with a host of exciting new features that the Ansible community can look forward to. Brought to Continue reading
New Ansible Galaxy
New Ansible Galaxy
For awhile, the Red Hat Ansible team behind the components Ansible automation hub and Ansible cloud automation hub at console.redhat.com have been on a special ops mission to enhance the galaxy_ng code base that serves the aforementioned components to also serve galaxy.ansible.com, with the intention of replacing galaxy.ansible.com with a fresh code base.
Galaxy, a legacy far far away…
The current Galaxy service has been running at galaxy.ansible.com for many years and is hugely successful in the community. It drives and nurtures Ansible adoption by sharing prebuilt Ansible content that solves many automation challenges.
One of the statistics we are most proud of are the contributions of 33,965 individual automation answers by the community in either Ansible Content Collections or Ansible Roles. Some of the top ranking automation content includes AWS, VMware, Linux, and Windows. Community users are able to download content for free, self-supported and interact with authors via GitHub for any further help or enhancements.
- We are excited to announce that the galaxy.ansible.com code base is being updated with a host of exciting new features that the Ansible community can look forward to. Brought to Continue reading
Ansible Contributor Summit, Durham 2023
The Ansible Contributor Summit is a full day working session for community contributors to interact with one another and meet with the Ansible development teams behind the projects like AWX, Galaxy NG, Molecule, Ansible Lint and Event-Driven Ansible. We will discuss important issues affecting the Ansible Community and help shape the future of collaboration.
We are happy to have the opportunity to do a second Contributor Summit this year, and this time it will be part of DjangoCon US 2023 in Durham, NC. Our previous experience co-locating the Contributor Summit with another related event was in February in Ghent, Belgium as part of CfgMgmtCamp 2023. It was so successful, we wanted to do it again with another great match.
Hello, Durham!
We will be meeting in the "Bull City", the home of Ansible itself and the inspiration for our beloved mascot, Ansibull. In case you didn't know, the Ansible office overlooks the Durham Bulls Athletic Park, and this mixed with Ansible word play is why you might see mentions of bulls and Ansibulls in Ansible land.
If you can't attend the event in person in Durham, worry not! Ansible Contributor Summit is a hybrid event, so you will Continue reading
Welcome to the new Ansible Community Forum
Today, we're delighted to announce the launch of the new Ansible Community Forum - a single starting point for questions and help, development discussions, events, and much more. Everyone is invited, whether you are an Ansible user, contributor or developer, we are all community! Register here to join us!
Hello Discourse!
Screenshot of the forum's main page
For those who are familiar with forums, we hope you'll feel right at home. For those who may be new, please don't worry! We have a list of tips & tricks here, and you're always welcome to check the guides and post in the feedback section to help us shape our online community.
Forums are only successful if they are used. To make that happen, the Ansible Community Team is looking to make this the real home of the Ansible Community - a place for users to get help, to find an event or local meetup, and a jumping-off point for development and contribution discussions. That means we need you to come and participate! Tell us what you're up to, post your thoughts or your questions, sign up for an event or two.
The Ansible Community is global, Continue reading
Welcome to the new Ansible Community Forum
Welcome to the new Ansible Community Forum
Today, we're delighted to announce the launch of the new Ansible Community Forum - a single starting point for questions and help, development discussions, events, and much more. Everyone is invited, whether you are an Ansible user, contributor or developer, we are all community! Register here to join us!
Hello Discourse!
Here is a screenshot of the forum's main page:
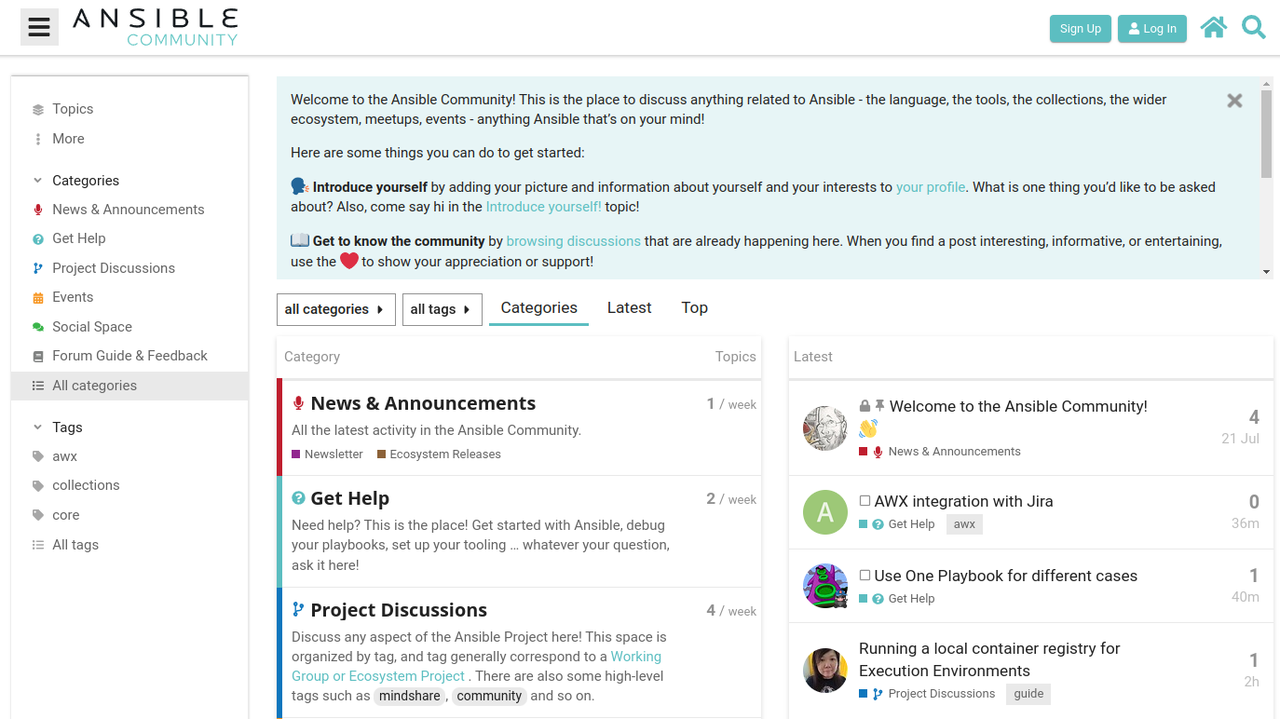
For those who are familiar with forums, we hope you'll feel right at home. For those who may be new, please don't worry! We have a list of tips & tricks here, and you're always welcome to check the guides and post in the feedback section to help us shape our online community.
Forums are only successful if they are used. To make that happen, the Ansible Community Team is looking to make this the real home of the Ansible Community - a place for users to get help, to find an event or local meetup, and a jumping-off point for development and contribution discussions. That means we need you to come and participate! Tell us what you're up to, post your thoughts or your questions, sign up for an Continue reading