Storage Market: Out With The Old, In With The New
SSDs are on the rise as HDDs and traditional arrays decline in a turbulent market.
SSDs are on the rise as HDDs and traditional arrays decline in a turbulent market.
IT leaders need to fully understand costs and business need of the DIY model when considering cloud.
The post BGP and equal-cost multipath (ECMP) appeared first on Noction.
In this post I’m going to talk about how to use Docker Machine to build a Docker Swarm cluster on Amazon Web Services (AWS). This post is an adaptation of this Docker documentation post that shows how to build a Swarm cluster using VirtualBox.
This post builds on the earlier post I wrote on using Docker Machine with AWS, so feel free to refer back to that post for more information or more details anywhere along the way.
At a high level, the process looks like this:
Let’s take a look at these steps in a bit more detail.
There’s at least a couple ways to do this, but they pretty much all involve a Linux VM using the Swarm Docker image. It’s up to you exactly how you want to do this—you can use a local VM, or you can use an AWS instance. The Docker documentation tutorial uses a local VM with the VirtualBox driver:
docker-machine create -d virtualbox local
env $(docker-machine env local)
docker run swarm create
The first command above creates a VirtualBox VM (named “local”) and Continue reading
I’ve worked on many large-scale MPLS VPN solutions, some with as many as 20k-30k managed CPEs, and as everybody knows – where you run BGP with this sort of setup. It’s almost always eBGP with a single AS across all sites using AS-override, or each site gets a different AS number, to get around the age-old eBGP loop prevention mechanisms which tend to get in the way when we use L3VPNs.
Recently I came across RFC 6368 which describes how iBGP can actually be used as a PE-CE protocol, in order to make the provider network more transparent from a BGP perspective. Usually there’s no problem running eBGP and 99% of networks seem to operate perfectly fine with it, however if the customer CE routers have a large BGP element behind them, the provider’s AS numbers and interactions with the BGP updates can in some cases cause problems.
Recently Cisco added support to run iBGP for PE-CE with the addition of a new command placed under the VRF – “neighbor <x.x.x.x> internal-vpn-client” in JUNOS the command is “independent-domain” which goes under the routing-options for the routing-instance.
For this configuration, consider the following basic topology:
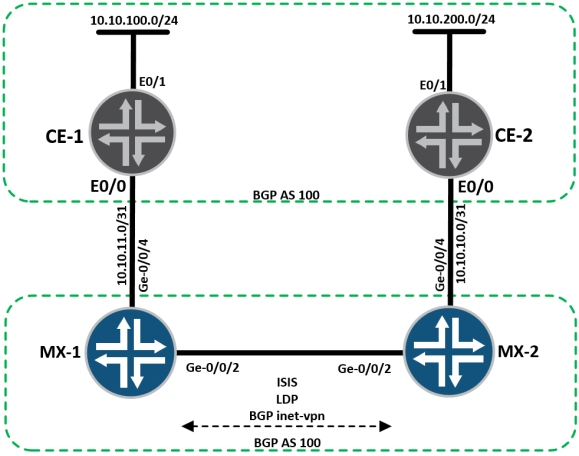
CE-1 and CE-2 Continue reading
 Kubernetes 1.2 can now handle 1,000 nodes and 30,000 pods.
Kubernetes 1.2 can now handle 1,000 nodes and 30,000 pods.
 Oracle is moving into the enterprise data center with a subscription-based cloud offering.
Oracle is moving into the enterprise data center with a subscription-based cloud offering.
 The threat of white box switches has cast a shadow over big network equipment vendors for years, as the combination of Moore’s Law and economies of scale provides merchant switch silicon an overwhelming price/performance advantage over proprietary platforms.
The threat of white box switches has cast a shadow over big network equipment vendors for years, as the combination of Moore’s Law and economies of scale provides merchant switch silicon an overwhelming price/performance advantage over proprietary platforms.
 Both Microsoft and HPE are customers as well.
Both Microsoft and HPE are customers as well.