Get Started with CloudFlare ServerShield for Plesk
 ServerShield makes it easy to activate CloudFlare and StopTheHacker.
ServerShield makes it easy to activate CloudFlare and StopTheHacker.
CloudFlare has partnered with Parallels, the leading hosting solutions provider, to make server protection, content acceleration and malware removal easier than ever. We recently launched CloudFlare ServerShield® to all Plesk 12 users as an extension. ServerShield combines the performance and security features of CloudFlare with the malware scanning and removal solution of StopTheHacker. Whether you are a hosting provider looking to offer additional services to your customers, or a Plesk server user, you can access ServerShield with two easy clicks.
Already, a number of hosters and agencies have found ServerShield a key addition to their tools to help their customer sites’ security and performance. Rafal Kukla of Kukla Studio, a UK based design agency, has this to say:
“ServerShield made it straightforward to give my customers industry leading security and performance as well as reputation monitoring. Running a busy agency, I am focused on my customers' site design, ServerShield allows me to do that without sacrificing the fundamentals of site functionality. With one single click I can enable CloudFlare among all my customers instead of spending time configuring each site separately.”
We believe that this extension is incredibly timely Continue reading
AnsibleFest London Presentations
-1.png)
We had our biggest and best AnsibleFest last week in London! This was our 1st Ansible event outside of the United States and due to the amazing turnout and great crowd we will definitely include at least one stop overseas in 2016.
If you were not able to attend, or just wanted to see the presentations, we’ve compiled all of them here:
How to automate Big Data with Ansible - Marius Boeru, BigStep
Ansible and Vagrant - Sebastian Göttschkes, wogibtswas.at
The Devs Are Opsing (And It Isn’t Painful) - Ali Asad Lotia, Blue Newt
Ansible, Windows, and Powershell - Jon Hawkesworth, M Modal
How Rackspace Is Deploying OpenStack With Ansible - Walter Bentley, Rackspace
What's New in V2 - James Cammarata, Ansible
Ansible Internals - Brian Coca, Ansible
We’ll be announcing the next stop in the AnsibleFest tour soon (hint: It is New York City) so follow us on Twitter to find out all of the details first!
View our Ansible Tower Video here to learn all about the great features available in Ansible Tower.
Cutting The Cord – Ditching the CableTV Bundle!
I finally did it! I cut the cord on cable today (2/7/15). I have been considering cutting the cord for about a year or so now, but never was really motivated to cut it. My cable bill was high (over $200/mo), but I was in a bundled package with my cable, internet, and phone – […]
The post Cutting The Cord – Ditching the CableTV Bundle! appeared first on Fryguy's Blog.
Let’s Meet in Zurich or Heidelberg
I’ll be speaking at two conferences in March: SDN event in Zurich organized by fantastic Gabi Gerber, and the best boutique security conference – Troopers 15 in Heidelberg. If you’ll be attending one of these events, just grab me, drag me to the nearest coffee table, and throw some interesting questions my way ;) … and if you happen to be near one of these locations, let me know and we might figure out how to meet somewhere.
Read more ...Blessay: Enterprise IT Comes Last In Technology Innovation
There was a time when Enterprise IT defined the future of computing. Laptops were designed for corporate consumption first and the best software was sold to enterprise for business use. The other markets for computers was “home users” who were offered cheap, low quality and low performance versions of corporate computers. IT was critical to the […]
The post Blessay: Enterprise IT Comes Last In Technology Innovation appeared first on EtherealMind.
Friends May Come and Go…
We overuse the word “friend” in our world — especially the technical world. We tend to call anyone we’ve ever met a friend. In this environment, friends come and go almost constantly, flowing through our lives like the leaves in a brisk fall wind. The depth to which Facebook and LinkedIn dive into our personal relationships — reminding us of birthdays, telling us who’s having a work anniversary, telling us when we should say the right thing at the right time to keep the “friendship” alive and current. But this somehow robs the concept of friendship out of, well, friendship. There’s no sacrifice, not even any effort — you have to question the value of “friendship” on these terms. It almost seems that social networking has made us less social, and less attuned to real friendship.
How do we live in this world?
I would first suggest reviving the concept of being intentional about friendship. Rather than just letting people fall into and out of our lives, we need, particularly as engineers, to decide to hold on to some friends, to intentionally make these people a fixture in our lives. We need to be careful not to make these choices Continue reading
Remote-to-remote data copy
Ever wanted to do this?Installing Golang IDE Support in Intellij
I have always preferred Intellij Community Edition IDE for Java, Bash, Python, Node and anything else I have needed, including recently C/C++ which is pretty slick. The plus is I can hang on to key-mappings, syntax color and general workflow all in a ubiquitous dev environment. There are some good IDE options for Go and of course support for the ... The post Installing Golang IDE Support in Intellij appeared first on NetworkStatic | Brent Salisbury's Blog....
Reverse Proxy + Cache for Minecraft
Reverse Proxy + Cache for Minecraft
One of the things that I like to play from time to time is Minecraft, however one of things ( at least with me this is ) is that Minecraft is best played with other people, This however means you have to go throu
Nested Virtualization
A typical Network Virtualization demo is difficult as you need quite some hypervisor hosts to run some VMs on and interconnect them using Overlays. I solve this using nested virtualization. This means that I run a hypervisor running on another. This gives me the flexibility that my physical nodes, or “hypervisor underlay” if you will, can scale easily and I’m independent of them.
My physical cluster consists of 2 nodes running ESXi with vCenter. On top of that I’m running 4 other ESXi hosts divided in 2 “virtual” clusters and 4 KVM hosts as Contrail Compute Nodes.
How does this work?
This technology works using Intel’s VT-x (which is hardware assisted virtualization) and EPT (to virtualise memory allocations). This combination works since the “Nehalem” arch itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).
itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).
Memory is the biggest burden in these Continue reading
Notes from NANOG 63
This is a selected summary of the recent NANOG 63 meeting, held in early February, with some personal views and opinions thrown in.Cisco Live in San Diego – Will You Make It?
“Make it” was one of the first singles released by the the band Aerosmith. Since then these guys have been rocking away for about 40 years. What does this have to do with Cisco Live? Aerosmith will be the band playing at the Customer Appreciation Event (CAE). A good time is pretty much guaranteed. Aerosmith knows how to entertain a crowd.
The CAE will take place at Petco Park, the home of the San Diego Padres. This photo shows the arena in the evening, looks quite spectacular to me.
Cisco Live is much more than just having fun though. If you want to make it in the IT industry, there is a lot to gain by going to Cisco Live. Here are some of my reason why I want to go:
- Stay on top of new technologies – Where is ACI going?
- Dip my toes into other technologies that I find interesting
- Gain deep level knowledge of platforms or features that will benefit me and my customers
- Go to sessions that will aid me on my certification path
- Connect with people!
- Learn a lot while having fun at the same time!
- Learn from the experience of others
When you are Continue reading
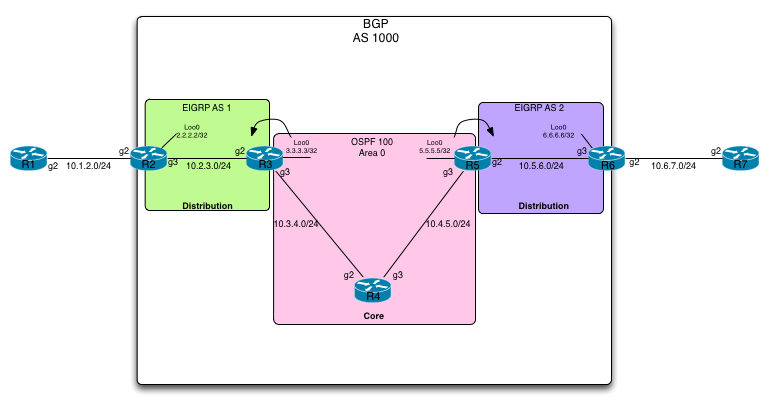
Unified/Seamless MPLS
In this post I would like to highlight a relative new (to me) application of MPLS called Unified MPLS.
The goal of Unified MPLS is to separate your network into individual segments of IGP’s in order to keep your core network as simple as possible while still maintaining an end-to-end LSP for regular MPLS applications such as L3 VPN’s.
What we are doing is simply to put Route Reflectors into the forwarding path and changing the next-hop’s along the way, essentially stiching together the final LSP.
Along with that we are using BGP to signal a label value to maintain the LSP from one end of the network to the other without the use of LDP between IGP’s.
Take a look at the topology that we will be using to demonstrate this feature:
In this topology we have a simplified layout of a service provider. We have a core network consisting of R3, R4 and R5 along with distribution networks on the right and left of the core. R2 and R3 is in the left distribution and R5 and R6 is in the right hand side one.
We have an MPLS L3VPN customer connected consisting of R1 in one site Continue reading
STP Notes for CCDE
These are my study notes for CCDE based on “CCIE Routing and Switching v5.0 Official Cert Guide, Volume 1, Fifth Edition” and “Designing Cisco Network Service Architectures (ARCH) Foundation Learning Guide: (CCDP ARCH 642-874), Third Edition“, “INE – Understanding MSTP” and “Spanning Tree Design Guidelines for Cisco NX-OS Software and Virtual PortChannels“. This post is not meant to cover STP and all its aspects, it’s a summary of key concepts and design aspects of running STP.
STP
STP was originally defined in IEEE 802.1D and improvements were defined in amendments to the standard. RSTP was defined in amendment 802.1w and MSTP was defined in 802.1s. The latest 802.1D-2004 standard does not include “legacy STP”, it covers RSTP. MSTP was integrated into 802.1Q-2005 and later revisions.
STP has two types of BPDUs: Configuration BPDUs and Topology Change Notification BPDUs. To handle topology change, there are two flags in the Configuration BPDU: Topology Change Acknowledgment flag and Topology Change flag.
MessageAge is an estimation of the age of BPDU since it was generated by root, root sends it with an age of 0 and other switches increment this Continue reading
Away from WordPress to Jekyll on Github
Recently I seriously considered shutting down the blog. I wasn't writing as often as I wanted. It was costing money to keep up, the free services...[[ Summary content only, you can read everything now, just visit the site for full story ]]
IT Security Skills Anyone Can and Should Learn
I’ve been teaching IT security awareness for several years and I try to get those in attendance of the classes to learn some basic IT security skills. These basic skills build on each other and there is some cross over, but ultimately this blended set of security skills can help anyone stay safe online. As with any sport you always start by learning the fundamentals, and while no one skill can get you into the game or keep you safe online, they can definitely make you ready for either.
Physical Security
With free Wi-Fi available in coffee shops and many fast food restaurants I constantly see people leaving their devices unattended and this lapse can allow someone to walk off with the device unnoticed. Think about your device and the amount of data it may contain. The device may have your whole world stored on it! If someone takes your laptop, tablet, or phone it is so much more than having the device stolen, but the data it contains. Besides this Wi-Fi example other scenarios to pay attention to your device is when going through airport security or leaving the device in plain site while stored in the car. Continue reading