0
Network edge automation challenges
As organizations grow and expand geographi cally, they start extending their IT infrastructure into the distributed and far edge layers through opening new branch offices.
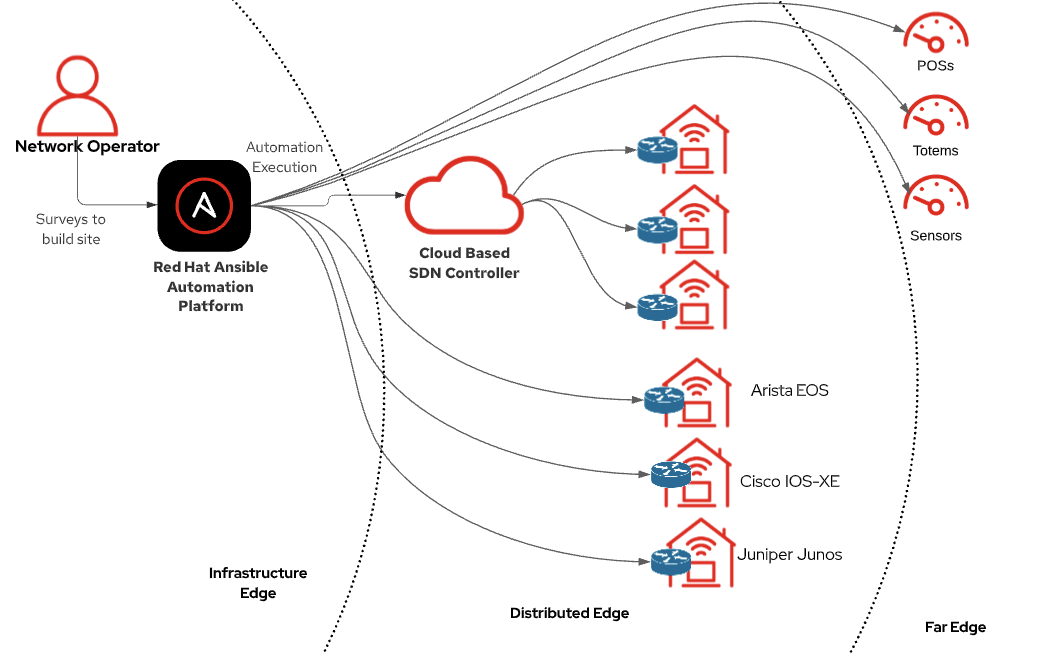
Restaurants, retail stores, and other customer-centric businesses provide differentiated wireless access for their employees, contractors and customers to interconnect within their designated areas.
Configuring and managing multiple wireless settings via Red Hat Ansible Automation Platform simplifies the deployments at scale.
Network administrators can use GitOps practices to automate wireless infrastructure as a code (IaC).
This case covers a sample use case for a company that uses an SDN (software-defined network) controller with a large network infrastructure, including access points, switches, and firewalls/routers to provide connectivity for thousands of branches across multiple countries. We will show you step by step how to automate wireless network access point settings at scale through a SD-WAN controller, which will be Cisco Meraki for purposes of this demo.
Considerations about using a source of control. Why not scripts?
Typically an SDN controller has an API. Having access to an SDN API is an advantage, since we have a single point of contact with the controller, and we can operate the whole network Continue reading



 Quick 5 mins on silicon manufacture
Quick 5 mins on silicon manufacture



