Author Archives: Stijn Vanveerdeghem
Author Archives: Stijn Vanveerdeghem
Helping organizations protect their assets and infrastructure from evolving attack tactics and techniques is a priority at VMware. API-focused ransomware attacks have become an all-too-common trend, and we recommend that customers take extra care to reduce their attack surface by deploying NSX Manager — and any other manager console — in a hardened manner.
Management infrastructure and common services typically allow broad access to other potentially more valuable resources within an organization, which in turn provides malicious actors with convenient platforms from which they can launch more damaging attacks. To manage that risk, VMware recommends the following steps to protect your management networks and services deployed within those networks:
With the launch of VMware NSX in 2013, VMware pioneered micro-segmentation. Back then our solution was based on stateful Layer 4 filtering. We’ve added in dynamic grouping, enabling policies based on VM context such as VM Name, Operating System or Security Tags. Using dynamic grouping, the life cycle of a Service-defined Firewall policy is directly tied to the life cycle of the workloads/application it’s protecting. This is radically different from traditional firewalls which use IP-address based policies.
Another addition to our Service-defined firewall is Layer 7 Application Identity. You may be familiar with the concept from the perspective of a perimeter firewall where it can be used to allow access to Facebook chat but block access to Facebook games. The data center is different and so are the use cases for layer 7 Application Identity.
In this blog I will cover why organizations should use Layer 7 Application Identity in their data center segmentation policies.
While stateful Layer 4 firewalls have significantly reduced both the complexity and security gaps that come with configuring stateless Access Control Continue reading
Most readers are already familiar with VMware NSX as a natural platform for intrinsic security in the data center. They understand that NSX’s service-defined firewall is enabling network and security operators to use a distributed software-based solution to replace centralized hardware-based deployments.
The intrusion detection and prevention system (IDS/IPS) functionality released with NSX-T 3.0 enhances the security capabilities of the service-defined firewall, enabling operators to address several additional use cases.
The COVID-19 pandemic has forced many organizations to shift their business online and their employees to work from home. As a result, business had to quickly adjust and scale up their infrastructure, sometimes with security as an afterthought.
Malicious actors are already taking advantage of this new reality by targeting the vulnerabilities commonly associated with employees connecting to corporate resources from their home environment. This includes social engineering and phishing campaigns, denial of service attacks, and exploiting vulnerabilities in home routers.
Providing employees working from home with secure and reliable access to their corporate resources and applications by the use of Virtual Desktop Infrastructure (VDI) helps our customers to reduce the impact on productivity and continuity as well as the risk associated with remote access to internal data.
In this blog post, I will cover a couple of use cases on how NSX can provide security for End User Compute and share some resources to help customers who are scaling up their VDI / remote desktop session host (RDSH) infrastructure to adapt to this new world in which vast numbers of employees are now working from home.
The initial target of Continue reading
With last’s week landmark release of NSX-T 2.4, and the RSA conference in full swing, this is the perfect time to talk about to some of the new security functionality we are introducing in NSX-T 2.4.
If you prefer seeing NSX-T in action, you can watch this demo which covers Layer 7 application identity, FQDN Filtering and Ientity Firewall. Or if you are around at RSAC in San Francisco this week, swing by the VMware booth.
Micro-segmentation has been one of the key reasons why our customers deploy NSX. With Micro-segmentation, NSX enables organizations to implement a zero-trust network security model in their on-premise datacenter as well as in the cloud and beyond. A key component making Micro-segmentation possible is the Distributed Firewall, which is deployed at the logical port of every workload allowing the most granular level of enforcement, regardless of the form factor of that workload – Virtual Machine – Container – Bare Metal Server or where that workload resides – On Premise – AWS -Azure – VMC.
NSX-T 2.4 provides significant new security features and functionality such as Context-aware Micro-segmentation, Network (and Security) Intrastructure as Code, E-W Service Insertion and Guest Continue reading
As you may have read earlier this month, NSX Data Center and NSX SD-WAN by VeloCloud are part of the expanded VMware NSX portfolio to enable virtual cloud networking. A Virtual Cloud Network provides end-to-end connectivity for applications and data, whether they reside in the data center, cloud or at the edge. I wanted to follow up, and walk through an example using NSX Data Center and NSX SD-WAN of how one could build an end to end segmentation model from the data center to the branch.
 NSX SD-WAN Segmentation
NSX SD-WAN SegmentationBeyond lowering cost and increasing agility and simplicity of branch connectivity, one of the key values provided by NSX SD-WAN by VeloCloud is enterprise segmentation, which provides isolated network segments across the entire enterprise, enabling data isolation or separation by user or line of business, support for overlapping IP addresses between VLANs and support for multiple tenants. NSX SD-WAN provides this segmentation using a VRF-like concept with simplified, per-segment topology insertion. This is accomplished by inserting a “Segment ID” into the SD-WAN Overlay header as traffic is carried from one NSX SD-WAN Edge device to another Edge. Networks on the LAN-side of an NSX SD-WAN Edge with different Continue reading
Summary: With Context-awareness, NSX for vSphere 6.4 enables customers to enforce policy based on Application and Protocol Identification and expands the Identity Firewall support to Multiple User Sessions.
A few weeks ago, VMware released version 6.4 of NSX for vSphere. The 6.4 release brings many new features, with Context-awareness being key from a security perspective. Micro-segmentation enables East-West security controls, and is a key building block to a secure datacenter. Context-awareness builds-on and expands Micro-segmentation by enabling customers even more fine-grained visibility and control. NSX has supported the use infrastructure or application-centric constructs such as Security Groups based on criteria like VM name or OS version, or Dynamic Security Tags describing things like the workload function, the environment it’s deployed in, or any compliance requirements the workload falls under, enabling fine-grained control and allowing customers to automate the lifecycle of a security policy from the time an application is provisioned to the time it’s decommissioned. Prior to 6.4, rules with infrastructure or application-centric grouping constructs on the Management plane, are eventually translated to 5-tuple based rules in the dataplane.
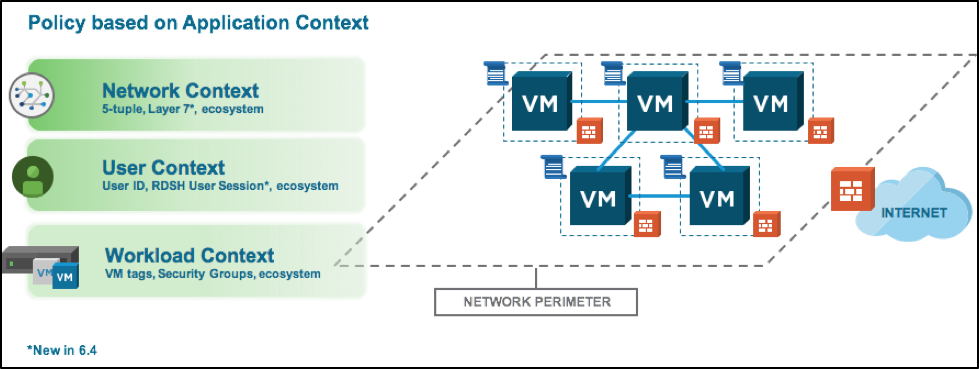 Figure: NSX drives policy based on Network, User and Workload Context
Figure: NSX drives policy based on Network, User and Workload Context
A crucial aspect of Context-awareness Continue reading
 Reimagining the edge While the importance of the cloud is obvious to anyone, the increasing importance of the edge is often overlooked. As digitization and the Internet of Things are leading to an exponential growth in the number of devices, the amount of data that is being generated by sensors in devices such as self-driving-cars, mobile endpoints... Read more →
Reimagining the edge While the importance of the cloud is obvious to anyone, the increasing importance of the edge is often overlooked. As digitization and the Internet of Things are leading to an exponential growth in the number of devices, the amount of data that is being generated by sensors in devices such as self-driving-cars, mobile endpoints... Read more →
While the importance of the cloud is obvious to anyone, the increasing importance of the edge is often overlooked. As digitization and the Internet of Things are leading to an exponential growth in the number of devices, the amount of data that is being generated by sensors in devices such as self-driving-cars, mobile endpoints and people tracking systems for retail is astronomical. Analyzing and turning that data into immediate actions is key to success in the era of digitization. The cloud enables massive data storage and processing, but it does not always lend itself to real time processing and immediate actions. Latency and the sheer amount of data to be transmitted are much less of a factor for the edge compared to the data center. In order to make instant decisions, some of the data processing needs to happen at the edge. At the same time, a large number of employees no longer work form the corporate HQ, but have ever increasing expectations with regards to application access regardless of their physical location. Distributed computing across the edge, along with high performance cloud access and distributed security enforcement give organizations “the edge”. Centralizing management and operations with distributed control and Continue reading

With the release of NSX for vSphere® 6.3, VMware has not only introduced several key security features such as Application Rule Manager and Endpoint Monitoring, which provide deep visibility into the application, and enable a rapid zero-trust deployment, but has also achieved Corporate Firewall Certification in independent testing performed by ICSA labs, a leading third-party testing and certification body and independent division of Verizon.
VMware NSX for vSphere 6.3 has been tested against an industry-accepted standard to which a consortium of firewall vendors, end users and ICSA labs contributed, and met all the requirements in the Baseline and Corporate module of the ICSA Module Firewall Certification Criteria version 4.2.
NSX is the only true micro-segmentation platform to achieve ICSA Firewall certification — with the NSX Distributed Firewall providing kernel-based, distributed stateful firewalling, and the Edge Services Gateway providing services such as North-South firewalling, NAT, DHCP, VPN, load balancing and high availability. VMware NSX provides security controls aligned to the application and enables a Zero-Trust model, independent of network topology.
The ICSA Firewall Certification criteria focus on several key firewall aspects, including stateful services, logging and persistence. ICSA also validates Continue reading
 Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
Welcome to part 3 of the Micro-Segmentation Defined – NSX Securing “Anywhere” blog series. This installment covers how to operationalize NSX Micro-Segmentation. Be sure to check out Part 1 on the definition of micro-segmentation and Part 2 on securing physical workloads with NSX.
This blog covers the following topics:
Micro-segmentation design patterns
Micro-segmentation can be implemented based on various design patterns reflecting specific requirements. The NSX Distributed Firewall (DFW) can be used to provide controlled communication between workloads independent of their network connectivity. These workloads can, for example, all connect to a single VLAN. Distributed logical switches and routers can be leveraged to provide isolation or segmentation between different environments or application tiers, regardless of the underlying physical network, as well as many other benefits. Furthermore, the NSX Edge Service Gateway (ESG) can provide additional functionality such as NAT or load balancing and the NSX Service Insertion framework enables partner services such as L7 firewalling, agent-less anti-virus or IPS/IDS applied to workloads that need additional security controls.
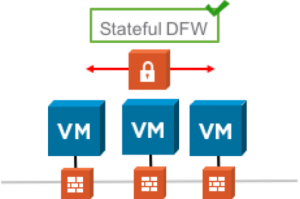
Figure 1: Leveraging the DFW to provide Continue reading