KRACK WPA2 Vulnerability Announced – Upgrade Now
If you haven’t already heard about the KRACK (Key Reinstallation Attack) vulnerability announced today, head over to the information page at https://www.krackattacks.com/ as quick as your fingers will take you because Mathy Vanhoef of imec-DistriNet has found a vulnerability in the WPA2 protocol which has a very wide impact.
 KRACK Attack
KRACK Attack
The challenge here is that for this isn’t a bug in any particular implementation or commonly-used library; rather, it’s a vulnerability in the protocol itself which means that any correct implementation of the protocol is vulnerable. This also does not just apply to wireless access points; remember that most cell phones can also act as wireless APs for purposes of wireless tethering, so they may be vulnerable too.
Impressively, a number of vendors have released code which has been patched for the vulnerability today, and a number of vendors included fixes before today’s public announcement. However, those are useless if people don’t install the upgrades. I strongly advise going now and finding what your wireless vendor has done, and installing any available patched code.
Ubiquiti Update
Since I know you’re all following my Ubiquiti experiences, I’ll note that UBNT released code Continue reading
iTerm2 Tip: Repeating Commands Using a Coprocess
iTerm2 is a great terminal for MacOS; far better than Apple’s built-in Terminal app, and it’s my #1 recommendation for Mac-based network engineers. One of the many reasons I like it is that it has a feature that solves a really annoying problem.
It’s tedious having to issue a command repeatedly so that you can see when and if the output changes. I’ve had to do this in the past, repeating commands like show ip arp so that I can spot when an entry times out and when it it refreshes. The repeated sequence of up arrow, Enter, up arrow, Enter, up arrow, Enter
drives me mad.
Some vendors offer assistance; A10 Networks for example has a repeat
command in the CLI specifically to help with show commands:
a10-vMaster[2/2]#repeat 5 show arp Total arp entries: 25 Age time: 300 secs IP Address MAC Address Type Age Interface Vlan --------------------------------------------------------------------------- 10.1.1.65 0000.5e00.01a1 Dynamic 17 Management 1 10.1.1.67 ac4b.c821.57d1 Dynamic 255 Management 1 10.1.1.97 001f.a0f8.d901 Dynamic 22 Management 1 Refreshing command every 5 seconds. (press ^C to quit) Elapsed Time: 00:00:00 Total arp entries: 25 Age time: Continue reading
Microburst: Update on the HTML Home Network Diagram

Last week I published an article called Making a Clickable HTML Network Diagram using OmniGraffle. One of the questions I was asked was whether I’d tried doing the same in draw.io or Gliffy. I have not, although I do use Gliffy a fair amount, and I have dabbled with draw.io.
Thankfully, Keith Miller (@packetologist) is on hand to provide the answer! Keith has put together an article mirroring a similar process using the free (and platform-agnostic) draw.io. Definitely worth a read, and a great example of a free tool making our lives way easier.
Link: CLICKABLE HTML NETWORK DIAGRAMS WITH DRAW.IO
Thanks, Keith for the excellent demonstration!
If you liked this post, please do click through to the source at Microburst: Update on the HTML Home Network Diagram and give me a share/like. Thank you!
Traceroute Lies! A Typical Misinterpretation Of Output
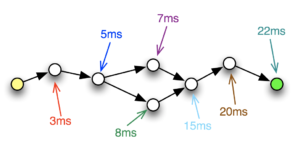
Sometimes a user with performance issues will proudly present me with a traceroute and point to a particular hop in the network and accuse it of being the problem because of high latency on the link. About 1 time in 1000 they are correct and the link is totally saturated. The other 999 times, well, let me explain.
Traceroute Output
Here’s a typical traceroute I might be sent by a user (IPs and hostnames are altered to protect the innocent):
$ traceroute www-europe traceroute to www-europe (18.9.4.17), 64 hops max, 52 byte packets 1 gateway (57.239.196.133) 11.447 ms 18.371ms 25.057 ms 2 us-atl-edge (137.16.151.202) 13.338 ms 20.070 ms 19.119 ms 3 us-ga-core (57.239.129.37) 103.789 ms 105.998 ms 103.696 ms 4 us-nyc-core (57.239.128.189) 107.601 ms 103.116 ms 103.934 ms 5 us-east-core (57.239.13.42) 103.099 ms 104.215 ms 109.042 ms 6 us-east-bb1 (57.239.111.58) 107.824 ms 104.463 ms 103.482 ms 7 uk-south-bb1 (57.240.117.81) 106.439 ms 111.156 ms 104.761 ms Continue reading
Microburst: A New Post Type on MovingPackets.Net
A problem I frequently face is that I want to share thoughts and comments on something, but I don’t have the time free to write up a full post. The solution, I hope, is a new post type which I’m calling a Microburst.

A Microburst could be anything from one line to a few paragraphs; basically enough for me to convey a thought without having to go into as much depth as I would usually like to do. For that reason in particular, I think it’s important that I can distinguish my regular, shallow posts from these special, short, shallow posts. Handy, right?
The first Microburst appeared a few days ago, and more will be coming soon. Gird your loins, etc.
If you liked this post, please do click through to the source at Microburst: A New Post Type on MovingPackets.Net and give me a share/like. Thank you!
Not Your Mama’s Security Architecture (Thwack)
It puts a firewall at the edge of the network or it gets the hose again. Think that’s still how security works? I don’t think so, my friend.
On the Solarwinds Thwack Geek Speak blog I look at how security architectures have changed from when our Mama used to create them, and I even take a moment to mention Greg Ferro (because, well, why not). Please do take a trip to Thwack and check out my post, “Not Your Mama’s Security Architecture“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at Not Your Mama’s Security Architecture (Thwack) and give me a share/like. Thank you!
Your Network: The Glue Holding the Business Together (Thwack)
TCP congestion control, buffer bloat and micro bursting are just a few of the things that can ruin your network and, as a consequence, your business.
On the Solarwinds Thwack Geek Speak blog I looked at these issues and more, examining the elements that make up network performance. Please do take a trip to Thwack and check out my post, “Your Network: The Glue Holding the Business Together“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at Your Network: The Glue Holding the Business Together (Thwack) and give me a share/like. Thank you!
Microburst: Intent-Washing (See Apstra Fight Back!)
Apstra – the intent-based networking company – was thrilled, perhaps in a somewhat ironic sense, when Cisco announced just before Cisco Live 2017 US that the future was intent-based networking. I hear informally that their appointment book for meetings at Cisco Live was positively spilling over within just a couple of days. Intent-based networking had just been validated by the big guy in the room!

A few months later, and the evidence of intent-washing
is all too clear, as some other vendors have begun labeling their SDN products intent-based
so they can claim table stakes in the next big thing. In fact, I’m sure from Asptra’s perspective, Cisco was, and is, stepping on their toes too, and doing its own intent-washing to stay on message. If I were Apstra, I’d be none pleased to see my message devalued like this, but what can a company in this position do?
Apstra can fight back with a video featuring the bearded legend himself, Derick Winkworth (@cloudtoad), that’s what they can do. This is not to be missed:
This is pure gold. We shall never forget.
If you liked this post, please do click through to the source at Microburst: Intent-Washing Continue reading
Ok, I’m Giving Ubiquiti Networks Another Chance
After quite a few discussions resulting from my Epic Evaluation: Ubiquiti ERPro-8 vs Play-Doh where (spoiler alert!) the Play-Doh™ won hands down after an exhaustive six-month test, I’ve been persuaded to give Ubiqiuti Networks (aka UBNT) another chance. Another two chances, in fact.

Ubiqitui Networks Products
As I said in the evaluation post, I was hesitant about recommending against UBNT products not least because I owned four other UBNT devices (three wireless access points and a 48-port switch). Despite being persuaded to try UBNT again, I strongly maintain my previous recommendation to avoid the ERPro-8 like a wedding invitation from Walder Frey. For the rest of the product range I’ve decided to suspend my previous “NO BUY” verdict and reserve my final judgement while I try out some new additions to my home network and see if they can restore balance to the nerd universe.
I would also like to add that while Ubiquiti’s official Support and RMA channels were no help to me whatsoever when my ERPro-8 was behaving badly, I did appreciate one employee reaching out privately and trying to help. The conclusion for now is that flash itself has indeed become irrecoverably corrupted and the device Continue reading
You Need Configuration Management. Really. (Thwack)
Oops, lost a network device. I sure hope we have a configuration backup…
On the Solarwinds Thwack Geek Speak blog I looked at how configuration management can help not just with total loss scenarios, but also with audit and compliance issue. Please do take a trip to Thwack and check out my post, “You Need Configuration Management. Really“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at You Need Configuration Management. Really. (Thwack) and give me a share/like. Thank you!
The Value of Configuration Consistency (Thwack)
It’s one thing to have a stable network, but it’s another to have consistency in device configurations across the network. Does that even matter?
On the Solarwinds Thwack Geek Speak blog I looked at some reasons why it might be important to maintain certain configuration standards across all devices. Please do take a trip to Thwack and check out my post, “The Value of Configuration Consistency“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at The Value of Configuration Consistency (Thwack) and give me a share/like. Thank you!
New Coder: Stop What You’re Doing!
Let’s get coding! We’ve selected a language, we’ve done some online training, and we’re ready to get coding and automate the first thing we stumble across. How exciting! Aaaaannnnnd STOP.
On the Solarwinds Thwack Geek Speak blog I looked at the “80:20” rule and how to use it to guide where to get the biggest return on investment when spending time coding, then I gave some advice on how to select a task to automate. Please do take a trip to Thwack and check out my post, “New Coder: Stop What You’re Doing“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at New Coder: Stop What You’re Doing! and give me a share/like. Thank you!
New Coder: Getting Started and Finding Your Path
Having decided it’s time to learn how to code, and having chosen the right language to use, the next step is to find some resources and start programming that masterpiece. But what’s the best way to learn that language?
On the Solarwinds Thwack Geek Speak blog I spoke about how I started learning to code, and look at some of the different resources out there to kickstart your programming mastery. Please do take a trip to Thwack and check out my post, “New Coder: Getting Started and Finding Your Path“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at New Coder: Getting Started and Finding Your Path and give me a share/like. Thank you!
Epic Evaluation: Ubiquiti ERPro-8 vs Play-Doh
It’s the bake off you’ve been waiting for; a five-month real life test of a Ubiquiti ERPro-8 (EdgeRouter Pro) and a tub of Play-Doh™! Over a period of five months I carefully evaluated these two very useful items and discovered their good and bad points. But after five months, which will I choose as the ultimate winner?
The Rules
- Each of the two competing items will be utilized over a period of five months for the purpose for which they were intended.
- At the end of the five month test period, the performance of both items will be evaluated, and a winner chosen entirely subjectively based on:
- Suitability for intended purpose during the test
- Condition at the end of the test
- Performance of intended purpose at the end of the test
The Tub of Play-Doh™
Product Specifications
The first item to be evaluated is the tub of Play-Doh™. I didn’t skimp on quality, and bought genuine Play-Doh™ as part of a set which included tubs of both light blue and red. Accessories in the box included a roller, a plastic cutting knife, four shaped cutters and an extruder with four built-in shapes as well as four interchangeable extrusion heads.
The entire kit Continue reading
Dell EMC and The Amazing Internet Of Things
While at Dell EMC World 2017 I had a very interesting chat with Jason Shepherd, Dell EMC’s Director of IoT Strategy & Partnerships. To be clear, I’m not an expert on the Internet of Things (IOT), and our discussion was a useful reminder how much difference perspective makes when evaluating a technology.

Internet Of Things: Use Cases
When I think about IOT the first thing that comes to mind — naturally enough — are the items most applicable to me, like a smart thermostat, smart door locks, smart light bulbs, and so forth. I work in an enterprise, so I also think about building management in the enterprise, to include things like smart lighting, HVAC, presence sensors, temperature monitoring and more. Both of these environments are ripe for IOT functionality, and are the ones that most of us are likely to encounter on a daily basis.
However, it’s probably obvious that there are many more use cases for IOT devices, including for example:
- industrial (monitoring critical equipment like motors, valves, temperatures, flow meters)
- metropolitan (city-wide automotive/pedestrian traffic monitoring, traffic flows)
- agricultural (monitoring water levels, animal health, production volumes, environmental)
- automotive (monitoring the car’s engine, location, mechanical and electronic Continue reading
Pockethernet – A Smartphone-Enabled Cable/Link/IP Tester
I saw an advertisement for Pockethernet a few months ago and it looked pretty impressive; €167.23 (~$179 based on xe.com‘s published exchange rates at the time of writing) for a 200 gram rechargeable device offering 10/100/1000 Ethernet and cable testing features such as:
- A cable tester (wiremapping, TDR fault detection, PoE testing, BER and an analog toner)
- Link analyzer (speed, duplex, VLAN tags, CDP/LLDP, traffic detection)
- IP analyzer (DHCP, DNS, HTTP, ICMP ping)
- Report generation
Over all, Pockethernet sounded like something I needed to look into more closely.

Pockethernet
Pockethernet started off with the assistance of a crowdfunding campaign on Indiegogo, raising $185,000 of their $50,000 target. Unusually for an electronic device, Pockethernet is manufactured in Hungary, which was nice to see. Unboxing the Pockethernet I was surprised (but pleased) to discover that the device is packaged in a soft, zipped carry case.

The box also contains a small User Guide, and inside the case is the Pockethernet tester, an adaptor, a short Ethernet cable and a short USB charging cable. There’s also a strip of blue velcro which will be useful to hold the tester in place if needed.

As it turns out, keeping the Pockethernet Continue reading
John’s Network Oops – As Seen On Reuters
In my response to The Network Collective’s group therapy session where the participants ‘fessed up to engineering sins, I promised to share my own personal nightmare story, as seen on Reuters. Grab a bag of popcorn, a mug of hot chocolate and your best ghost story flashlight
, and I will share a tale which will haunt you for years to come. If you have small children in the room, this may be a good time to send them outside to play.

At one point in my career I was a network engineer for a national mobile provider in the USA. The mobility market is a high-stakes environment, perhaps more so than most industry outsiders might expect. Users have surprisingly high expectations and are increasingly reliant on the availability of the network at all times of day or night.
High-Stakes Networking
Mobile networks are typically not just for consumers but are also used by a large number of private entities including fleet management companies, fire/burglar alarm systems, shipping companies and emergency services, so even a minor outage can potentially be a problem. These commercial organizations all had customized private connectivity to the mobile provider and thankfully we had a contractually-identified Continue reading
Response: The Network Collective, Episode 1
The end of March brought with it the first episode of a neat new project called The Network Collective, a video roundtable for networking engineers. The hosts and co-founders of this escapade are Jordan Martin (@BCJordo), Eyvonne Sharp (@SharpNetwork) and Phil Gervasi (@Network_Phil).
Top 10 Ways To Break Your Network
Episode 1 brought three guests to the virtual table: Carl Fugate, Mike Zsiga and Jody Lemoine, the latter of whom (top right on the YouTube video) is actually blurry in real life, and this is not a video artifact. The topic for discussion was the Top 10 Ways To Break Your Network.
Thankfully, the show didn’t actually provide tips on how to break your network — as if we need any help doing that — but instead looked at the shameful ways in which each participant had managed to cause network destruction in the past, and what lessons could be learned.
The fact that five of six experienced professionals are willing to own up to their blunders (one brought a colleague’s mistake to put up on the chopping block) actually signals one of the most important lessons that the episode highlighted, which is Continue reading
Taking A Stand Against Corruption
Over the last few months, I’ve noticed that some pages on this site have been returning what appear to be corrupted pages, looking something like this:

Or like this:
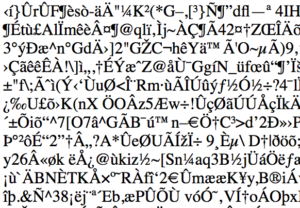
Pretty, aren’t they? Typically if the user hits refresh the page will come back as it should have done first time. I’ve been working for many weeks now to track down why this was happening. One thing I noted is that the corrupted files were smaller than the non-corrupted equivalent, suggesting that the file was either truncated or, more likely, compressed. Opening a downloaded file in a text editor showed that the header of these corrupted pages begins like this:

Some of you are probably feeling smug right now because you know that the first three bytes of a gzip file are 1F 8B 08. The ASCII code for 0x1F is Ctrl-_; there’s no code for 0x8B; ASCII 0x08 is the same as Ctrl-H (i.e. backspace). This should look familiar in the image above: ^_ <8B> ^H. In other words, the client is receiving a GZIPped version of the page but presumably was told that the mime type was text/html. The end result is the garbled mess we saw above. So now Continue reading
Using DCNM to Automate Cisco FabricPath Operations
In my final post on Cisco’s Data Center Network Manager (DCNM), I’m taking a look at the deployment capabilities and templating features which allow configuration to be deployed automatically to multiple devices. In its simplest case, this might be used to set a new local username / password on all devices in the fabric, but in theory it can be used for much more.
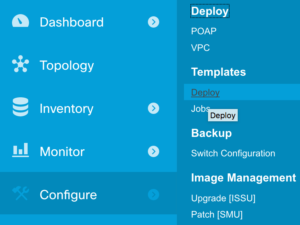
DCNM Scripting
Let’s get one thing straight right out of the gate: this ain’t no Jinja2 templating system. While DCNM’s templates support the use of variables and some basic loop and conditional structures, the syntax is fairly limited and the only real-time interaction with the device during the execution of the template amounts to a variable containing the output of the last command issued. There are also very few system variables provided to tell you what’s going on. For example I couldn’t find a variable containing the name of the current device; I had to issue a hostname command and evaluate the response in order to confirm which device I was connecting to. That said, with a little creativity and a lot of patience, it’s possible to develop scripts which do useful things to the fabric.