Cisco Viptela drops the ball

In 2012, we saw the launch of Viptela, a pioneer in SDWAN network solutions. While they weren’t the first in SDWAN, I believe that badge goes to Talari; Viptela was the first company that caught my interest. I first saw what they were doing in 2015 on the Packet Pushers Podcast. Back then, the networking world was on fire with SDWAN offerings.
Sadly in 2017, Cisco purchased Viptela. I’m sure the leadership at Viptela was excited to be acquired by such a large networking company and hoped to develop Viptela to the pinnacle of their vision. But – despite calling themselves, and being repeatedly lamented for doing so, “a software company”, Cisco did what they so often do. They stopped platform development and tried to lower costs by integrating the vEdge software into their own. While I haven’t personally used the hybrid code, I haven’t heard good things from my coworkers. Eventually, we got the ISR1100 platform running Viptela code, but that was only a substitute for the vEdge 100 and 1000. We have still yet to see a replacement for the vEdge 2000.
May 9, 2023 – 6:57 AM UTC
certificate-status Installed
certificate-validity Not Valid – certificate has expired Continue reading
Will 2023 be the year of Artificial Intelligence for InfoSec?

Gartner has been saying that “next big thing” in network security is the increased use of artificial intelligence (AI) and machine learning (ML) technologies for years now… Mainly because these technologies have the potential to revolutionize the way that network security is managed by enabling systems to learn and adapt to new threats in real-time.
One of the main benefits of using AI and ML in network security is that they can help to identify and mitigate threats much faster than traditional methods. This is because they can analyze vast amounts of data in real-time, and detect patterns and anomalies that might indicate the presence of a threat. In addition, they can be programmed to take specific actions in response to these threats, such as blocking access to a particular network resource or alerting security personnel.
Another benefit of using AI and ML is that they can help to reduce the workload of security professionals. By automating many of the tasks currently carried out manually, such as analyzing logs and identifying potential threats, AI and ML technologies can free up time for security professionals to focus on more critical tasks.
However, it is essential to note that using AI and Continue reading
Introducing Graphiant: The Future of Network-as-a-Service

As businesses continue to shift towards remote and distributed work environments, the need for secure and reliable network infrastructure has never been greater. Enter Graphiant, a new network-as-a-service (NaaS) provider that offers edge-to-edge security and scalability for businesses of all sizes.
Graphiant offers a unique approach to networking, leveraging advanced technologies like software-defined networking (SDN) and network function virtualization (NFV) to provide a flexible and secure network experience. This focus on security is one of the key advantages of their NaaS offering.
As cyber-attacks target more and more companies, the need for robust security measures has become paramount. Graphiant’s edge-to-edge security approach ensures that data is protected at every stage, from the edge of the network to the cloud.
But security isn’t the only benefit of Graphiant’s NaaS offering. The company also provides a high level of scalability, allowing businesses to expand or contract their network as needed quickly. These features are particularly useful for networks that are growing fast or dealing with fluctuating demands.
In addition to Graphiant’s cutting-edge technology and focus on security, another critical factor in Graphiant’s success is the expertise of its team. Many members of the Graphiant team were also involved in founding Viptela, a Continue reading
Mandatory Cisco DNA Licensing – is this the Future??

With the release of the new 9200 series switches many enterprise organizations are starting to look towards the future. Cisco has also been looking towards the future… of their profit margin. With the 2960x platform is nearing it’s EOS/EOL announcement, Cisco has been working to promote the new hardware. And by now most Cisco enterprise customers have realized that DNA Center licensing is mandatory on your initial hardware purchase. This is certainly a deviation from Cisco’s normal à la carte licensing, but what do you think is the driving force behind all of this?
The era of SaaS and Subscription based licensing has been upon us for some time. Last year Gartner predicted, “By 2020, all new entrants and 80% of historical vendors will offer subscription-based business models”. These shifts to recurring-revenue models are the latest adaptation for companies like Cisco to continue to pad their bottom line with dollars their customers may not be ready to spend. After all, why would Cisco miss out on dollars left on the table?
When I started laying out the network hardware roadmap for the next 24-36 months, I quickly realized that costs for the Catalyst 9200 series will raise per port Continue reading
AIOps the next big thing for Enterprise IT?
 Out of everything I think will be big in 2019, AIOps is near the top of the list. My current prediction is Artificial Intelligence (AI) making big moves in the enterprise IT Infrastructure and Operations market. AI-based technology is a hot topic in the media these days, everyone is exploring its benefits in a wide range of markets. From self-driving cars and industrial automation to advertising and fraud prevention. It’s no surprise that 2018 was predicted to be a dominating year for AI in IT. While I believe 2018 was a key year for AI getting it’s foot in the door of IT Ops, the reality is lagging behind the hype. In IT we hear a lot about machine learning, and big data, but with the reality of how this data is organized in most enterprises, the onus is still on us to get that data laid out in an organized structure to extract the potential that AI promises.
Out of everything I think will be big in 2019, AIOps is near the top of the list. My current prediction is Artificial Intelligence (AI) making big moves in the enterprise IT Infrastructure and Operations market. AI-based technology is a hot topic in the media these days, everyone is exploring its benefits in a wide range of markets. From self-driving cars and industrial automation to advertising and fraud prevention. It’s no surprise that 2018 was predicted to be a dominating year for AI in IT. While I believe 2018 was a key year for AI getting it’s foot in the door of IT Ops, the reality is lagging behind the hype. In IT we hear a lot about machine learning, and big data, but with the reality of how this data is organized in most enterprises, the onus is still on us to get that data laid out in an organized structure to extract the potential that AI promises.
But how does all of this relate to IT Infrastructure and Operations? AIOps is the combination of AI and IT Operations. And while the IT community hears the AI related buzzwords, not many of us know where or how it can Continue reading
Gartner – more than a magic quadrant

In the past I have personally given a lot of flack towards Gartner, but that was when I was in a different stage of my career. Over the past two years I’ve transitioned into management, and with that had to learn several valuable lessons. The most important, for me, being expectation management, but that’s for another blog post. The second most important would have to be effectively leveraging resources across all channels. And that’s why I wanted to talk about Gartner.
As an engineer, I found them to be a bit pedantic. They wrote these long winded articles that seemed to never get to the point, i.e. does this product deliver what the company is selling? — A lot of the analysis I’ve seen from Gartner has gotten much better in the past 10-12 years, and while I appreciate that, I think we actually have to thank ourselves for that, rather than Gartner. The freely available content available on blogs, like RouterJockey, has forced anyone hoping to sell content to step up their game. But I digress. My engagements with Gartner always felt generic, I consistently had issues with the amount of knowledge the analyst on the phone had. Continue reading
PCAP PCAP PCAP – Changes to RJ Store
 I made a couple changes to the RouterJockey store this week and I wanted to make sure I got the word out. Previously the store worked in sprints that I tried to open up 2-3x a year. Instead of trying to manage these sprints, and keep the products updated, I’ve now made the store available year round. It still operates in sprints, but instead of being 2-3 weeks long, they’re only 3-4 days each.
I made a couple changes to the RouterJockey store this week and I wanted to make sure I got the word out. Previously the store worked in sprints that I tried to open up 2-3x a year. Instead of trying to manage these sprints, and keep the products updated, I’ve now made the store available year round. It still operates in sprints, but instead of being 2-3 weeks long, they’re only 3-4 days each.
On top of being more available, the store now has a few new products, nothing too exciting, but we do have a RJ phone case, a PCAP mug, and a couple stickers for sale. Teespring has recently added these products and as I get requests for other products I will be sure to add them. As usual, if you have any questions, hit me up on twitter or use the contact form.
Click here, or use the store item in the menu bar to visit my new storefront.
The post PCAP PCAP PCAP – Changes to RJ Store appeared first on Router Jockey.
IP Infusion powering the world from behind the scenes
 Founded by Kunihiro Ishiguro and Yoshinari Yoshikawa the founders of GNU Zebra, came together to form IP Infusion back in 1999 as a commercial-grade, hardware-independent networking software company. If you’re not familiar with Zebra, you probably know it’s little brother Quagga which powers everything from Cumulus Linux to Vyatta and even my old digs.. Imagestream routers. Ishiguro and Yoshikawa took Zebra, and built ZebOS, which has been working behind the scenes in products we all use every day for years. IP Infusion’s ZebOS powers everything from F5 LTM’s and Citrix Netscaler’s to Plexxi, SK Telecom, and Huawei networking products.
Founded by Kunihiro Ishiguro and Yoshinari Yoshikawa the founders of GNU Zebra, came together to form IP Infusion back in 1999 as a commercial-grade, hardware-independent networking software company. If you’re not familiar with Zebra, you probably know it’s little brother Quagga which powers everything from Cumulus Linux to Vyatta and even my old digs.. Imagestream routers. Ishiguro and Yoshikawa took Zebra, and built ZebOS, which has been working behind the scenes in products we all use every day for years. IP Infusion’s ZebOS powers everything from F5 LTM’s and Citrix Netscaler’s to Plexxi, SK Telecom, and Huawei networking products.
Today IP Infusion is selling two variants of ZebOS to OEMs, OcNOS and VirNOS. OcNOS is a full featured network OS built specifically for White Box OEMs looking for switching, routing, MPLS, and SDN support. It can support a hybrid, centralized, or distributed network framework which provides a scalable, modular, and robust framework that can be deployed on merchant silicon. VirNOS is their NFV solution that can be used for distributed or cloud based vCPE, vPE, or vRouters in your data center.
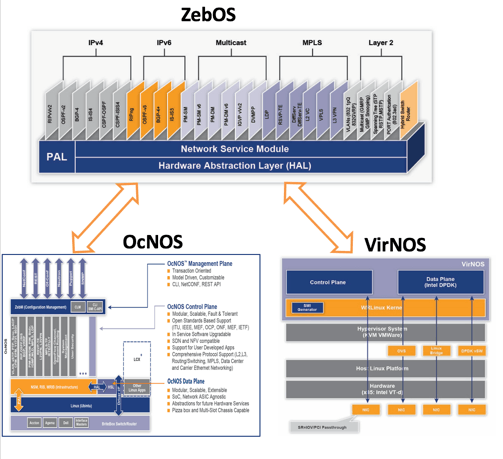
Whitebox networking is a really exciting market that I have been looking into since the SDN craze started. Continue reading
VMware NSX is something something awesome
 At times I have trouble focusing on writing articles for some of the presentations I am exposed to at Tech Field Day. Because of that, I really wanted to try something different. This article is more of my free-formed thoughts about NSX and why I’m excited to deploy it at my current $job. From the time I heard that the NSX team was going to be presenting at TFD15 for 4 hours, I knew that I would be writing this article because. Unfortunately it took me far too long to gather up this half formed thought.
At times I have trouble focusing on writing articles for some of the presentations I am exposed to at Tech Field Day. Because of that, I really wanted to try something different. This article is more of my free-formed thoughts about NSX and why I’m excited to deploy it at my current $job. From the time I heard that the NSX team was going to be presenting at TFD15 for 4 hours, I knew that I would be writing this article because. Unfortunately it took me far too long to gather up this half formed thought.
First things first – NSX and Micro-Segmentation
I love the concept of Micro-Segmentation that NSX enables. Think of NSX as a virtual distributed firewall that is integrated with your hypervisor, but it really is so much more. This allows you to connect a security policy directly to the vNIC of your guest VM’s. Attaching it to the VM allows that policy to follow the VM anywhere, and everywhere it goes. You don’t have to worry about inter- or intra-VLAN segmentation as all of that is done on each vNIC. On top of that, NSX’s firewall is PCI DSS 3.2 compliant! Another rather compelling Continue reading
PCAP t-shirts just in time for CLUS17
Hey guys, I just wanted to drop a quick note to let you know that I’ve relaunched my teespring shirt campaigns with enough time that you should get your orders before Cisco Live US 2017. I’ve got several types of clothing under each design, so make sure you look to see if I have what you’re looking for. This campaign is only open for 14 days – so get yours while you can!
As usual, send comments / suggestions / etc to @tonhe on twitter.
Thanks again, and I hope to see you at #CLUS17
Click below to enter my teespring storefront
The post PCAP t-shirts just in time for CLUS17 appeared first on Router Jockey.
PNDA provides scalable and reactive network analytics
 During Networking Field Day 15 our friends from the Linux Foundation, including Lisa Caywood, briefed us on a recent “acquisition” from Cisco. PNDA (Panda) is an open source Platform for Network Data Analytics, which aggregates data from multiple sources on a network including, real time performance indicators, logs, network telemetry, and other useful metrics… then in combination with Apache Spark, the data is analyzed to find useful patterns. None of this should be confused with Cisco’s recent announcement of the Tetration analytics platform. Tetration is a data center focused solution focused on a very particular space, where PNDA is more of a horizontally focused platform that is cross-vendor and cross-dataset. But this project is in no way a fork of the Cisco Tetration product as they evolved from completely separate code bases. Because PNDA is an open source initiative, it is able to take advantage of many existing projects, like Apache Spark, to build a robust analytics platform. Because of this, it allows them to remain extremely flexible. While PNDA’s focus is solely on network, but there are other projects out there that are utilizing it as a jumping off point to perform Continue reading
During Networking Field Day 15 our friends from the Linux Foundation, including Lisa Caywood, briefed us on a recent “acquisition” from Cisco. PNDA (Panda) is an open source Platform for Network Data Analytics, which aggregates data from multiple sources on a network including, real time performance indicators, logs, network telemetry, and other useful metrics… then in combination with Apache Spark, the data is analyzed to find useful patterns. None of this should be confused with Cisco’s recent announcement of the Tetration analytics platform. Tetration is a data center focused solution focused on a very particular space, where PNDA is more of a horizontally focused platform that is cross-vendor and cross-dataset. But this project is in no way a fork of the Cisco Tetration product as they evolved from completely separate code bases. Because PNDA is an open source initiative, it is able to take advantage of many existing projects, like Apache Spark, to build a robust analytics platform. Because of this, it allows them to remain extremely flexible. While PNDA’s focus is solely on network, but there are other projects out there that are utilizing it as a jumping off point to perform Continue reading
Networking Field Day 15 – A new delegate emerges
 Yet again I find myself honored, and questioning their selection methods, by being selected for a Networking Field Day event. Networking Field Day 15 kicks off April 6 and 7th in San Jose California. Each and every Tech Field Day event is always an amazing opportunity to engage with vendors and industry peers. But trust me, I’m using the term peer rather loosely… While we may work in the same industry, many of these folks are way smarter than me! It seems the delegate list for NFD15 is certainly no exception to that rule! While I’ve met and become friends with roughly 75% of the “team” I get to meet a couple new faces which is always exciting. At least one of these faces I’ve spent hours talking to on Skype, but never actually met in person. I’m looking at you Nicolas. ;)
Yet again I find myself honored, and questioning their selection methods, by being selected for a Networking Field Day event. Networking Field Day 15 kicks off April 6 and 7th in San Jose California. Each and every Tech Field Day event is always an amazing opportunity to engage with vendors and industry peers. But trust me, I’m using the term peer rather loosely… While we may work in the same industry, many of these folks are way smarter than me! It seems the delegate list for NFD15 is certainly no exception to that rule! While I’ve met and become friends with roughly 75% of the “team” I get to meet a couple new faces which is always exciting. At least one of these faces I’ve spent hours talking to on Skype, but never actually met in person. I’m looking at you Nicolas. ;)

I took a look at the vendor list for this as soon as I heard they needed another delegate. Looking at the current line-up I got pretty excited, everything seems rather relevant to things I want to see! Looks like we’re going to see presentations from Gigamon, which specializes in the network tap and visibility market. I Continue reading
Ixia Vision ONE – Tap the Planet
 Whenever I start talking about network visibility and aggreagation taps I can’t help but think of The Matrix. Millions of packets flowing through your network every minute of every day, tapping into that can be a daunting exercise. Luckily we have some new blood in this space, at least in my view, Ixia Vision ONE. For those of you that recognize the name, yes I’m talking about that Ixia.. previously one of the leaders in the load testing market, they’ve moved into the network packet broker space.
Whenever I start talking about network visibility and aggreagation taps I can’t help but think of The Matrix. Millions of packets flowing through your network every minute of every day, tapping into that can be a daunting exercise. Luckily we have some new blood in this space, at least in my view, Ixia Vision ONE. For those of you that recognize the name, yes I’m talking about that Ixia.. previously one of the leaders in the load testing market, they’ve moved into the network packet broker space.

Vision ONE is Ixia’s all-in-one product attempts to provide assurance that the network traffic you want to reach your monitoring and security tools is actually reaching your tools. Vision ONE is able to take the input from your device, and send it out in several directions, applying filters to the traffic as needed. This means that you can filter out specific traffic and send it to a monitoring / security tool with traffic it doesn’t need to process. All of this is managed through a clean, easy to user interface that displays the connections between the TAP’s physical ports, filters, and tool ports.
Take a look at the Vision One demo here.
My Continue reading
Forward Networks – A forward approach to formal verification
 Forward Networks has stepped out of the shadows to announce their Network Assurance platform, and I was fortunate enough to be a delegate for Networking Field Day 13 to see their first public briefing. We were all excited to set foot onto the Andressen Horowitz campus that day, but none of us were quite sure what exactly to expect.
Forward Networks has stepped out of the shadows to announce their Network Assurance platform, and I was fortunate enough to be a delegate for Networking Field Day 13 to see their first public briefing. We were all excited to set foot onto the Andressen Horowitz campus that day, but none of us were quite sure what exactly to expect.
Forward Networks was founded by David Erickson and Brandon Heller, PhD in Computer Science from Stanford University, who saw the great need for help in the networking market and decided to tackle a challenge that no one else recognized. They worked in Nick McKeown’s Lab at Stanford University back in 2006 before SDN was ever put on a Networking Bingo card, let alone even heard of. They helped create the standards and shape OpenFlow as it came into existence. Working on bleeding edge SDN networks they realized that the tools network engineers were dealing with were wholly insufficient to troubleshoot many advanced and complicated networks.
In 2013 they founded Forward networks with the goal of understanding how networks work at the functional level. They’ve written an algorithm that can take in large amounts of data from your devices and build a Continue reading
Intel Atom SoC bricking more than Cisco products
 Looks like the culprit in the recent Cisco debacle is the Intel Atom “System on Chip” (SoC) that Cisco used in it’s gear. My sources within Cisco won’t give up the goods, but many seem to be pointing to Cisco, although a single source at Cisco seemed to indicate there was another player included in this issue but wouldn’t comment. The real footing of these Intel accusations come from Intel itself. Back in Janurary 2017, they updated their spec document documenting an issue with the LPC clock on the Atom s2000, with no workaround and a system that is unable to boot, this depicts a grim outlook for our networking devices.
Looks like the culprit in the recent Cisco debacle is the Intel Atom “System on Chip” (SoC) that Cisco used in it’s gear. My sources within Cisco won’t give up the goods, but many seem to be pointing to Cisco, although a single source at Cisco seemed to indicate there was another player included in this issue but wouldn’t comment. The real footing of these Intel accusations come from Intel itself. Back in Janurary 2017, they updated their spec document documenting an issue with the LPC clock on the Atom s2000, with no workaround and a system that is unable to boot, this depicts a grim outlook for our networking devices.
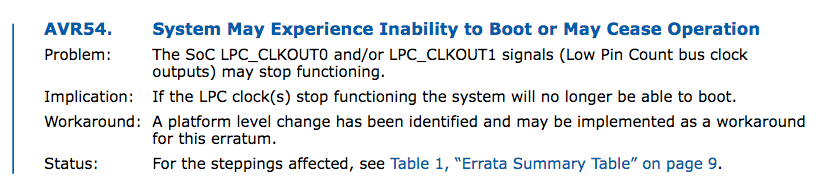
The news gets worse though, according to a recent article from The Register Cisco isn’t the only one experiencing issues.
People with Synology DS1815+ storage boxes have been reporting complete hardware failures; the DS1815+ is powered by an Intel Atom C2538. […]
Other vendors using Atom C2000 chips include Aaeon, HP, Infortrend, Lanner, NEC, Newisys, Netgate, Netgear, Quanta, Supermicro, and ZNYX Networks. The chipset is aimed at networking devices, storage systems, and microserver workloads.
For now, only time will tell what other devices are going to come out Continue reading
Cisco goes public with Clock Signal Component Issue

A couple months ago many engineers started hearing rumors regarding an ISR 4331 recall, and problems surrounding the device. Until this week, none of us had very good information, but it seems that today Cisco has officially released some information regarding the problem. Many of us have received phone calls at this time from our account managers… while some of us, myself included, have been left in the dark. This is troubling considering how many products are out in the field.
Recently, Cisco became aware of an issue related to a component manufactured by one supplier that affects some Cisco products. In some units, we have seen the clock signal component degrade over time. Although the Cisco products with this component are currently performing normally, we expect product failures to increase over the years, beginning after the unit has been in operation for approximately 18 months. Once the component has failed, the system will stop functioning, will not boot, and is not recoverable.
Cisco has identified the products that are affected by this issue and published an FAQ along with the Field Notices on their site. The list of products varies across the line and includes the following products that Continue reading
Networking Field Day 13 – Sneak Preview
This is going to be a busy week for the Tech Field Day family. They have delegates en-route to Tech Field Day 12 this morning, and Wednesday the crew for Network Field day 13 arrive. I can’t express how excited I am about going to Networking Field Day 13 this week. I haven’t been to an actual NFD event since NFD2, although I did get to go to the TFD9 event in Austin a couple years ago. I can’t wait to land in San Jose. For those new to this concept, Networking Field day is an event that is focused on bringing together IT product vendors and thought leaders in the industry to share information and opinions in a presentation and discussion format. Please be sure to read my disclaimer page on this topic. These events are streamed live, so if you want to listen in while we talk about the latest and greatest technologies from the vendors we’re meeting with, or if you just want to listen to us moan and groan at the occasional Gartner or NASCAR slides… you should tune in. On the menu for this week we have a number of exciting companies that I’d Continue reading
5 important reasons you should learn scripting
 Today’s IT landscape if full of software defined marketecture, and lore of a dystopian future full of network engineers that do nothing but write code. But in reality, there are plenty of actual reasons you should be learning programming, or at least some basic scripting. For many network engineers programming is not new, we have all been hacking together shell, Perl and Python for a VERY long time. While the requirements in the future may change, today it is not necessary to become half network engineer half software engineer, but learning the basics now will keep you in the know. Learning the basics of logic and loop statements will not only help you speed up day to day tasks, but it will help you understand other languages as you expand your knowledge in the future. So, here are my top 10 reasons I think you need to learn scripting.
Today’s IT landscape if full of software defined marketecture, and lore of a dystopian future full of network engineers that do nothing but write code. But in reality, there are plenty of actual reasons you should be learning programming, or at least some basic scripting. For many network engineers programming is not new, we have all been hacking together shell, Perl and Python for a VERY long time. While the requirements in the future may change, today it is not necessary to become half network engineer half software engineer, but learning the basics now will keep you in the know. Learning the basics of logic and loop statements will not only help you speed up day to day tasks, but it will help you understand other languages as you expand your knowledge in the future. So, here are my top 10 reasons I think you need to learn scripting.
1: Automation can save you time
Writing a script for common / repetitive tasks can save you a staggering amount of time. Over the years I have written hundreds of scripts to aide in everything from Data Center VLAN/SVI management to banning/unbanning MAC addresses from multiple wireless lan controllers.
2: Continue reading
The complexity required for robustness, often goes against robustness
In the past few months we have seen major outages from United Airlines, the NYSE, and the Wall Street Journal. With almost 5,000 flights grounded, and NYSE halting trading the cost of failure is high. When bad things happen IT personal everywhere look at increasing fault tolerance by adding redundancy mechanisms or protocols to increase robustness. Unfortunately the complexity that comes with these additional layers often comes with compromise.
The last thing your boss wants to hear is, “The network is down!”. Obviously it’s your job to prevent that from happening, but at what cost? Many of us enjoy twisting those nerd knobs, but that tends to only harbor an environment with unique problems. I too fear the current trend of adding layer after layer of network duct tape to add robustness, or worse, to try and fix shortcomings in applications. NAT, PBR, GRE, VXLAN, OTV, LISP, SDN… where does it end!?
The greater the complexity of failover, the greater the risk of failure. We often forget the lessons of our mentors, but keeping the network as simple as possible has always been best practice. As Dijkstra said, “Simplicity is a great virtue but it requires hard work Continue reading
Site Upgrades for September 2015
First, I want to apologize for not doing my job. Over the past couple years I’ve let this site become slightly stagnant. I won’t attempt to make excuses, but I will say that I’m in a much better place now. Hopefully inspiration will continue to strike, and I will continue to put pen to paper… or finger to keyboard?
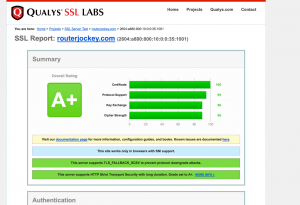 Over the past couple weeks I’ve put a fair amount of time and monetary resources into RouterJockey. I’ve fixed quite a few CSS bugs, without hopefully creating more. I purchased an SSL certificate and moved the site to HTTPS, which helps me more than it really does you… but in doing so, I’ve also enabled SPDY 3.1. SPDY should help load times, but Nginx was already doing a pretty good job. Oh, in order to get SPDY up to 3.1 I was forced to migrate away from the Ubuntu repo for Nginx.. but that’s not a huge deal.
Over the past couple weeks I’ve put a fair amount of time and monetary resources into RouterJockey. I’ve fixed quite a few CSS bugs, without hopefully creating more. I purchased an SSL certificate and moved the site to HTTPS, which helps me more than it really does you… but in doing so, I’ve also enabled SPDY 3.1. SPDY should help load times, but Nginx was already doing a pretty good job. Oh, in order to get SPDY up to 3.1 I was forced to migrate away from the Ubuntu repo for Nginx.. but that’s not a huge deal.
I’ve also spent some time redesigning the menu bar, adding new links, removing some useless ones, and writing an all new disclaimer. Please be sure to read and understand everything posted on that page before attempting to read any of my Continue reading