Author Archives: Dhiraj Sehgal
Author Archives: Dhiraj Sehgal
As Kubernetes becomes the backbone of modern cloud native applications, organizations increasingly seek to consolidate workloads and resources by running multiple tenants within the same Kubernetes infrastructure. These tenants could be:
While multitenancy offers cost efficiency and centralized management, it also introduces security and operational challenges:
To address these concerns, practitioners have three primary options for deploying multiple tenants securely on Kubernetes.
Namespaces are Kubernetes’ built-in mechanism for logical isolation. This approach uses:
Advantages:
In the rapidly evolving landscape of IT infrastructure, enterprises are increasingly moving away from traditional virtualization platforms due to rising licensing costs and the limitations these older systems impose on modern cloud-native application needs. The shift towards Kubernetes, which can manage diverse workloads such as containers, virtual machines (VMs), and bare metal environments, accelerates the migration from traditional virtualization platforms.
Traditionally, enterprises have segmented their virtualized environments using VLANs and logical switches to create distinct virtual networks and security zones. This segmentation was primarily static VM environments. However, this traditional approach to network segmentation is ill-equipped to handle the dynamic nature of Kubernetes environments, where workloads are frequently created and destroyed, leading to rapidly changing network configurations and policies.
Calico is designed to address the shortcomings of traditional network segmentation in the age of Kubernetes and container-based architectures. Calico provides a robust, dynamic, and high-performance network policy engine that supports a diverse range of workloads and scales across environments.
In the rapidly evolving landscape of IT infrastructure, enterprises are increasingly moving away from traditional virtualization platforms due to rising licensing costs and the limitations these older systems impose on modern cloud-native application needs. The shift towards Kubernetes, which can manage diverse workloads such as containers, virtual machines (VMs), and bare metal environments, accelerates the migration from traditional virtualization platforms.
Traditionally, enterprises have segmented their virtualized environments using VLANs and logical switches to create distinct virtual networks and security zones. This segmentation was primarily static VM environments. However, this traditional approach to network segmentation is ill-equipped to handle the dynamic nature of Kubernetes environments, where workloads are frequently created and destroyed, leading to rapidly changing network configurations and policies.
Calico’s microsegmentation capabilities are designed to address the shortcomings of traditional network segmentation in the age of Kubernetes and container-based architectures. Calico provides a robust, dynamic, and high-performance network policy engine that supports a diverse range of workloads and scales across environments.
Misconfigurations and container image vulnerabilities are major causes of Kubernetes threats and risks. According to Gartner, more than 90% of global organizations will be running containerized applications in production by 2027. This is a significant increase from fewer than 40% in 2021. As container adoption soars, Kubernetes remains the dominant container orchestration platform.
Realizing the full benefits of Kubernetes requires implementing processes and solutions to fight vulnerabilities, threats and risks, including issues stemming from human error such as misconfigurations, and inherent vulnerabilities like those from container images. DevOps and security teams need the right solutions to mitigate the risks and enjoy the full benefits of Kubernetes.
While container adoption has taken off, the industry still lacks skilled Kubernetes experts. Kubernetes is a complex platform, and personnel without the right skillset inadvertently — and frequently—make mistakes that create misconfigurations.
In the Red Hat State of Kubernetes Security Report 2023, more than 50% of respondents said they were concerned about misconfigurations and vulnerabilities. And with good reason: The simplest way for attackers to get to a company’s data, applications or code is through a misconfigured Kubernetes cluster. A bad actor needs just one small misconfiguration Continue reading
For DevOps and platform teams working with containers and Kubernetes, reducing downtime and improving security posture is crucial. A clear understanding of network topology, service interactions, and workload dependencies is required in cloud-native applications. This is essential for securing and optimizing the Kubernetes deployment and minimizing response time in the event of failure.
Network observability can highlight gaps in network policies for applications that require network policy controls to reduce the risk of attack from unsecured egress access or lateral movement of threats within the Kubernetes cluster. However, visualizing workload communication, service dependencies, and active and inactive network security policies presents significant challenges due to the distributed and dynamic nature of Kubernetes workloads.
Kubernetes scales up and scales out pods and creates and destroys services depending on real-time business requirements, resulting in dynamic network connections for each workload instance. Network access policies defined for each workload further impact these connections.
In such a scenario, capturing an accurate and up-to-date representation of network traffic, service dependencies, and network policies is difficult. The default Kubernetes implementation provides limited network traffic visibility and policy information, making it challenging for teams to troubleshoot connectivity issues, improve Continue reading
Whether an enterprise is migrating its legacy application to a cloud-native architecture or deploying a new cloud-native application, it will face the challenge of integrating with security tools such as firewalls that rely on a stable network identity for security configuration. This is due to the fact that cloud-native workloads aren’t guaranteed to have a fixed network identity. The juxtaposition of dynamic, modern workloads alongside traditional applications that rely on fixed network identifiers presents a unique set of challenges.
This is particularly pertinent for DevOps and platform teams tasked with ensuring seamless communication and security between these disparate environments. It becomes crucial for DevOps, platforms, and network security teams to ensure seamless communication and secure traffic flow as organizations balance innovation (cloud-native applications) and harness existing investments (traditional firewalls and data sources).
One of the key challenges in integrating cloud-native workloads with legacy applications behind a firewall is securing and identifying traffic from specific workloads running in the cluster. Many applications, such as databases, are protected by firewalls that need a stable IP address to enable access to these applications. Teams want to ensure that only authorized traffic from specific workloads Continue reading
Microsegmentation represents a transformative approach to enhancing network security within Kubernetes environments. This technique divides networks into smaller, isolated segments, allowing for granular control over traffic flow and significantly bolstering security posture. At its core, microsegmentation leverages Kubernetes network policies to isolate workloads, applications, namespaces, and entire clusters, tailoring security measures to specific organizational needs and compliance requirements.
The fundamental advantage of microsegmentation through network policies lies in its scalability and flexibility. Kubernetes’ dynamic, label-based selection process facilitates the addition of new segments without compromising existing network infrastructure, enabling organizations to adapt to evolving security landscapes seamlessly.
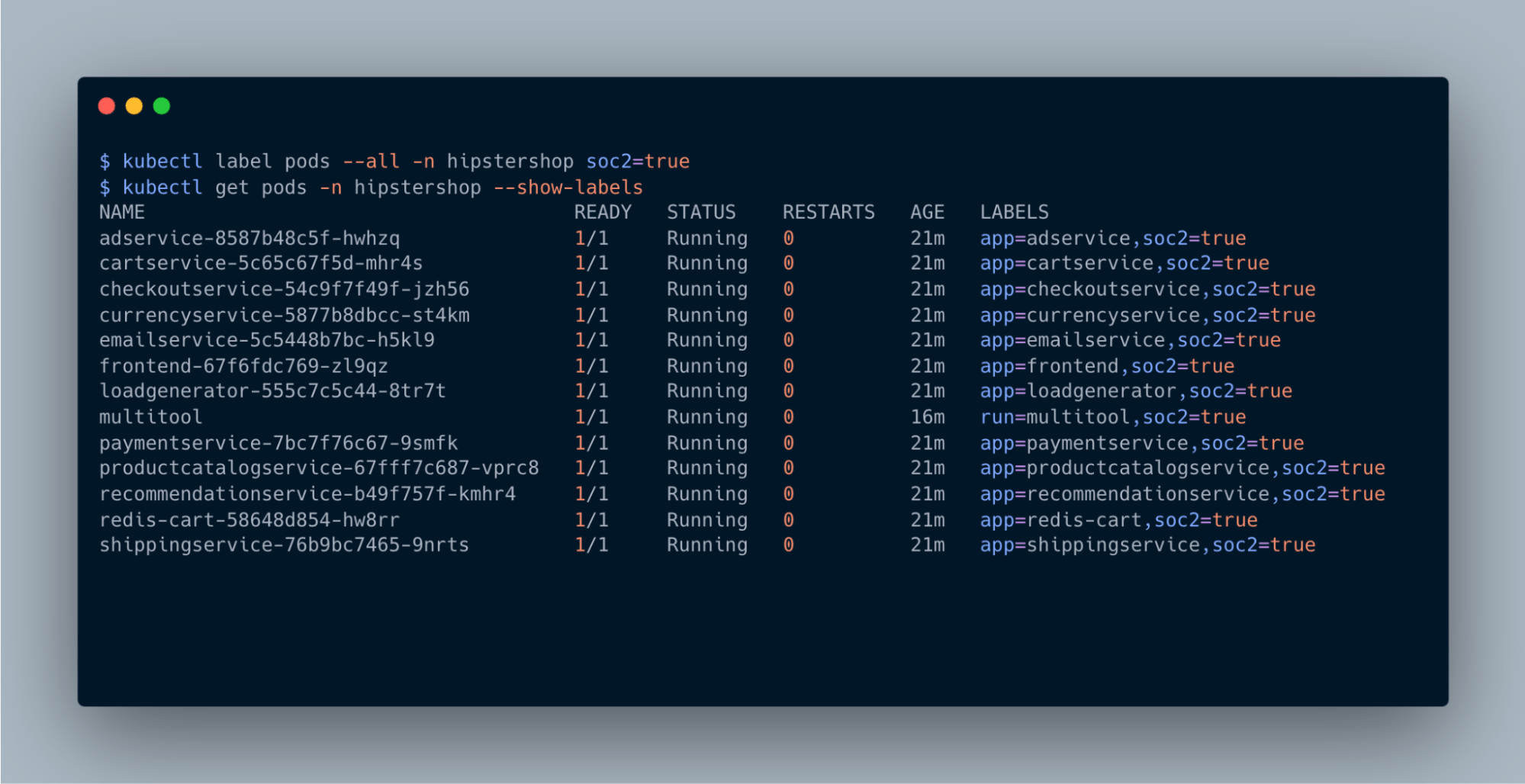
Workload isolation, a critical component of microsegmentation, emphasizes the importance of securing individual microservices within a namespace or tenant by allowing only required and approved communication. This minimizes the attack surface and prevents unauthorized lateral movement.
Namespace isolation further enhances security by segregating applications into unique namespaces, ensuring operational independence and reducing the impact of potential security breaches. Similarly, tenant isolation addresses the needs of multi-tenant environments by securing shared Kubernetes infrastructure, thus protecting tenants from each other Continue reading
We are excited to announce CalicoCon 2024, an in-person learning event for Project Calico, taking place March 19th, 2024 as a co-located event with KubeCon + CloudNativeCon Europe 2024.
As Kubernetes continues to expand its presence in both enterprises and small-to-medium businesses, understanding container networking and security in managed or self-managed Kubernetes environments becomes crucial. Organizations are now presented with choices for dataplanes, such as eBPF, Windows HNS, and Linux IP tables, multi-cloud and Kubernetes distributions as they scale their applications and make them more performance-efficient. Additionally, the process of creating new cloud-native applications or modernizing legacy applications also presents Kubernetes users with a selection of cutting-edge and mature container networking and security technologies.
To make these decisions to leverage their existing investments and future-proofing, users require guidance on developing and implementing scalable network security policies, selecting dataplanes, achieving low latency, optimizing resources, and integrating with bare metal and VM workloads.
At CalicoCon, we will provide KubeCon Paris 2024 attendees with an opportunity to actively participate in a full-day event where they will:
This blog is written by Dhiraj Sehgal and Mike Bookham.
Dhiraj Sehgal is the Director of Technical Marketing at Tigera, where he helps customers learn more about Calico and provides best practices for securing cloud-native environments. He is passionate about everything cloud native, from Kubernetes to cloud security and observability.
Mike Bookham is a Channel Solutions Engineer at Cockroach Labs. As part of Mike’s role, he helps a range of different types of partner organizations get familiar with CockroachDB from a technical perspective. Mike has worked with cloud-native technologies for a number of years and specializes in Kubernetes and the surrounding ecosystem.
With the rapid adoption of Kubernetes in organizations and the push to standardize the orchestration of resources with this approach, databases are now also being deployed into Kubernetes. Historically, persistent workloads like databases were not recommended for their deployment into Kuberntes as it was complex to manage how data would be stored. This was a result of Kubertnes originally being designed for non persistent microservice architectures. However, in more recent times new database vendors are emerging with software built from the ground up to run in this environment.
Kubernetes mandates how the networking is deployed and configured in Continue reading
We are excited to introduce the early preview releases for Calico Enterprise 3.17. This release focuses on helping enterprises have a strong security posture for their containers and Kubernetes clusters. Let’s go through some of the highlights of this release.
Namespace isolation with automatic Security Policy Recommendations
Calico will now automatically generate security policies based on workload dependencies and incoming and outgoing traffic to isolate namespaces in your Kubernetes cluster.
WireGuard support for AKS and EKS with Calico CNI
Users can now protect data-in-transit data in Microsoft AKS and Amazon EKS clusters by enabling WireGuard encryption with the Calico CNI.
Improved management of Workload-based WAF
Secure specific workload-to-workload communications at the application level with Calico’s workload-based web application firewall (WAF) by selecting and deselecting specific services.
Policy-based routing for egress gateways
Define policies on which egress gateway to use (or none at all) depending on the destination of egress traffic.
We hope you’ll enjoy these product upgrades and enhancements. We will continue to deliver new releases with innovative solutions to solve container and Kubernetes security challenges. Watch this space for future updates and details about how to leverage these features in your environment.
Check out our self-paced workshops for Continue reading
Companies are increasingly adopting managed Kubernetes services, such as Microsoft Azure Kubernetes Service (AKS), to build container-based applications. Leveraging a managed Kubernetes service is a quick and easy way to deploy an enterprise-grade Kubernetes cluster, offload mundane operations such as provisioning new nodes, upgrading the OS/Kubernetes, and scaling resources according to business needs.
AKS also provides a fault-tolerant Kubernetes control plane endpoint and automates the worker node maintenance and deployment process. With regards to networking within the cluster, AKS provides an integrated CNI to address basic Kubernetes networking requirements, such as configuring network interfaces and providing connectivity between pods. However, the basic container networking in Microsoft AKS comes with a limited set of IP addresses. As businesses grow, so does application usage. Having a limited set of IPs can cause scale, availability, and manageability challenges for Microsoft AKS users.
In this blog post, I will discuss IP address exhaustion on Microsoft AKS and how Calico can solve this issue. I will also explore how Calico can address scalability challenges and provide resources that can quickstart your journey in using Calico to solve IP address exhaustion on AKS.
Earlier this year, Microsoft AKS introduced the ability to bring Continue reading
As more enterprises adopt containers, microservices, and Kubernetes for their cloud-native applications, they need to be aware of the vulnerabilities in container images during build and runtime that can be exploited. In this blog, I will demonstrate how you can implement vulnerability management in CI/CD pipelines, perform image assurance during build time, and enforce runtime threat defense to protect your workloads from security threats.
The majority of images in CI/CD pipelines have vulnerabilities, misconfigurations, or both. An active cloud-native application protection platform (CNAPP) should scan, identify, and list vulnerabilities in container images based on databases such as NIST and NVD. The active CNAPP should then help teams build security policies to determine which images should be deployed or blocked based on several factors such as severity, last scan timestamp, and organizational exceptions. Given the sheer amount of vulnerabilities that appear daily, users will be easily overwhelmed if they have to address all existing vulnerabilities. Security teams will have to build a deploy/block criteria to prioritize vulnerabilities that they will address first—a workflow that is easy to start but difficult to manage and operate long-term. Hence, security teams should look for a security Continue reading
Cloud-native applications running on Kubernetes rely on container network plugins to establish workload communication. While Azure Kubernetes Service (AKS) provides several supported networking options (kubenet and Azure CNI) that address the needs of most deployments, Microsoft recently introduced the ability to bring your own networking solution, called BYOCNI, to help users address more advanced networking requirements. This new feature enables AKS customers to run Calico networking on AKS.
This blog will walk you through some exciting capabilities you can unlock with Calico running in your AKS deployments.
Calico is the most widely adopted container networking and security solution for Kubernetes. Powering more than 100M containers across 2M+ nodes in 166 countries, Calico is supported across all major cloud providers and Kubernetes distributions. Calico gives you a choice of data planes, including eBPF, standard Linux networking, and Windows HNS-based workloads running in public clouds and/or on-prem, on a single node, or across a multi-thousand-node cluster. Whether you need to scale to thousands of microservices with eBPF, or add Windows workloads to your Kubernetes deployments, Calico has you covered.
Calico’s core design principles leverage cloud-native design best practices, combined with proven, standards-based network protocols trusted by Continue reading
Calico Cloud has just celebrated its 1-year anniversary! And what better way to celebrate than to launch new features and capabilities that help users address their most urgent cloud security needs.
Over the past year, the Tigera team has seen rapid adoption of Calico Cloud for security and observability of cloud-native applications. With this new release, Calico Cloud becomes the first in the industry to offer the most comprehensive active cloud-native application security that goes beyond detecting threats to limit exposure and automatically mitigate risks in real time.
With news of new zero-day threats emerging almost every day (e.g. Argo CD, Chrome Browser), the current security approach needs to evolve. We need active build, deploy, and runtime security, all together, instead of using a siloed approach. Security threats, vulnerabilities, and risks for all three areas should be addressed together, by the same security platform, rather than using multiple disjointed tools. Calico Cloud does just that!
With Calico Cloud, you can reduce your cloud-native application’s attack surface, harness machine learning to combat runtime security risks from known and unknown zero-day threats, enable continuous compliance, and prioritize and mitigate the risks from vulnerabilities and attacks.
Let’s take a look Continue reading
Cloud-native transformations come with many security and troubleshooting challenges. Real-time intrusion detection and the prevention of continuously evolving threats is challenging for cloud-native applications in Kubernetes. Due to the ephemeral nature of pods, it is difficult to determine source or destination endpoints and limit their blast radius.
Traditional perimeter-based firewalls are not ideal fit for Kubernetes and containers. Firewalls have traditionally been used to block attacks at the perimeter, but if the perimeter is breached, there’s no protection from within the cluster. The dynamic nature of Kubernetes requires a specialized approach to intrusion detection and prevention for containers, Kubernetes, and cloud.
Threat intelligence feeds, which record and track the IP addresses of known bad actors, are a critical part of modern cloud-native security. Calico Cloud now provides threat intelligence feeds, such as AlienVault, as part of its default security policies. This means that traffic to suspicious IPs is blocked from day one without the need for any extra configuration. Additionally, an anomaly detection dashboard in Calico’s UI shows full context, including which pod(s) was involved so you can analyze and remediate.
Another advanced method for intrusion detection and prevention introduced in Calico Cloud is deep packet inspection (DPI). DPI inspects, Continue reading
Calico Cloud is an industry-first security and observability SaaS platform for Kubernetes, containers, and cloud. Since its launch, we have seen customers use Calico Cloud to address a range of security and observability problems for regulatory and compliance requirements in a matter of days and weeks. In addition, they only paid for the services used, instead of an upfront investment commitment, thus aligning their budgets with their business needs.
We are excited to announce recent Calico Cloud enhancements. Highlights include:
We are excited to announce Calico Enterprise 3.9, which provides faster and simpler live troubleshooting using Dynamic Packet Capture for organizations while meeting regulatory and compliance requirements to access the underlying data. The release makes application-level observability resource-efficient, less security intrusive, and easier to manage. It also includes pod-to-pod encryption with Microsoft AKS and AWS EKS with AWS CNI.
Enterprises that want to carry out live troubleshooting in their production environments face the following challenges when doing packet capture at an organizational scale:
With Dynamic Packet Capture, organizations can enable DevOps, SREs, service owners to collect the data that they need when they need it. They can filter the data based on protocol and port to fine-tune their capture for faster debugging and subsequent analysis for shorter time-to-resolution. With just-in-time data collection and built-in smart correlation, Continue reading
Kubernetes workloads are highly dynamic, ephemeral, and are deployed on a distributed and agile infrastructure. Application developers, DevOps teams, and site reliability engineers (SREs) often require better visibility of their different microservices, what their dependencies are, how they are interconnected, and which other clients and applications access them. This makes Kubernetes observability challenges unique. While Kubernetes helps to meet the needs of deploying and managing distributed applications, its observability challenges require a Kubernetes-native approach.
Traditional monitoring and observability solutions create data silos by collecting data at different levels (e.g. infrastructure, cluster, and application levels), or from a large number of ephemeral objects that generate data across a distributed environment. Traditional monitoring and observability solutions then stitch this data together to provide a near real-time snapshot view. This approach is not scalable given the high volume of granular data generated at each level, as well as Kubernetes’ distributed nature. It also starts to become expensive and budget unfriendly to run traditional monitoring solutions, as they require higher resource consumption (high-performance memory, more compute, and higher bandwidth).
In contrast, a Kubernetes-native observability solution can visualize all information with all relationship context intact and provide a high-fidelity view of the environment. This Continue reading