Downloading YouTube Videos From Links Saved In Google Chrome Bookmarks
The Bash script youtube-bookmarks-mp3.sh is using Python youtube-dl script along with ffmpeg in order to download videos from YouTube service. It also enables youtube-dl to convert videos to mp3 audio format. The script exports YouTube links from Bookmarks and copy them into the file bookmarks.txt. Multiple videos are downloaded and converted simultaneously in the background by the script.
Note: According to YouTube Terms of Service, you shall not copy, reproduce, distribute, transmit, broadcast, display, sell, license, or otherwise exploit any Content for any other purposes without the prior written consent of YouTube or the respective licensors of the Content.
OpenSwitch Network Operating System

The Open Network Install Environment (ONIE) is an open source install environment that gives a switch user a choice to download ONIE compliant Network Operation System (NOS) to bare metal network switches. The OpenSwitch is community based, open source NOS that runs on hardware based on ONIE.
The goal of this article is to show how to build OpenSwitch Virtual Machine appliance, describe its capabilities and to introduce three methods for managing OpenSwitch. The OpenSwitch VM appliance was created by OpenSwitch project for training and testing purpose. It uses software data plane to forward the packets but it is not intended to be used as a virtual switch for connecting virtual machines. OpenSwitch supports many L2, L3 protocols such as STP, LACP, LLDP, OSPF, BGP, DHCP, TFTP, NTP, SSH, SNMP and others. These protocols run as separate daemons and they were integrated from another open-source projects.
For instance Quagga project provides L3 functionality to Openswitch. Quagga modules ops-ospf and ops-bgp update active routes in OpenvSwitch database (OVSDB). The module ops-zebra reads routes from OVSDB and install them to the kernel. Static routes are also stored in OVSDB, read by ops-zebra module and installed to the kernel. In order to use Continue reading
Syslog-ng Configuration For Newbies
Some time ago I was asked by my friend to recommend a cost-free solution that he could use for storing logs of his security device over network. The Linux OS with installed syslog-ng is perfectly suitable for this job because it can collect logs from any source, process them in near real-time and deliver them to a wide variety of destinations. However it was challenge to explain all the steps in an easy manner as he was a total newbie in a Linux world. For this reason I wrote a basic installation and configuration manual for him which I share with you. The manual helps you to setup syslog-ng on Ubuntu server and troubleshoot the possible issues.
1. Install Ubuntu 16.04 Server Edition
During Ubuntu installation you are asked to provide the username/password and IP settings. Once an installation process finishes, the system is rebooted. when you get your console again, login and install updates with the command:
$ sudo su
# apt-get update
# apt-get upgrade
2. Install and Configure Syslog-ng
# apt-get install syslog-ng
First, you need to download a simple configuration file that I created for you.
# cd /etc/syslog-ng/conf.d
# wget http://brezular.com/wp-content/uploads/2016/12/firewals.conf_.txt -O firewals.conf
# Continue reading
Reverese Shell on Linux
Reverse shell is technique when a client connects to a server and the client provides its shell to the server. Clients is typically a host hidden behind the NAT or a firewall having an access to the server but not vice versa. Thanks to a reverse shell the server controls a client's shell having an access to the client's network even the client is hidden behind the NAT. They are several methods how to create a reverse shell used depending on software available on the client. I will show how to create a reverse shell using SSH, Ncat and Bash.
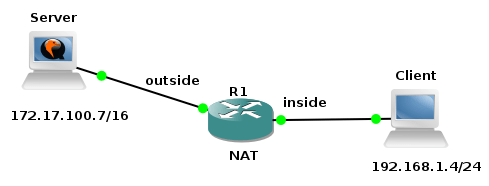
Picture 1 - Network Topology
Picture 1 shows our testing topology. The client (Ubuntu Server 16.04) is located behind the NAT with the IP address 192.168.1.4/24. The server (Kubuntu 16.04) has assigned the IP address 172.17.100.7/16.
1. Reverse Shell Using SSH Reverse Tunnel
This method is based on the fact that the client has knowledge of the server SSH login credentials and vice versa. SSH server must be running on both the server and client. Client must be allowed to access server through firewall.
Client:
$ ssh -R 10000:127.0.0.1:22 [email protected]. Continue reading
Bash Script for Converting Video To MP3 Audio
I like listening to video training on my smartphone while walking to work. To save the space on the memory card I convert videos to MP3 audio in advance. For this purpose I wrote a Bash script video_to_mp3.sh which helps me to manage a conversion job. The script uses ffmpeg for conversion and it creates parallel conversion tasks to speed up the conversion process. The script checks the CPU load and it creates a new background process only if the CPU load is under a particular limit entered by a user.
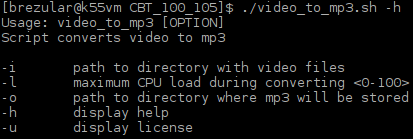
Picture 1 - Script Usage
Below is the output from the conversion process.
Picture 2 - Output From Conversion Process
The script creates a log file displaying info about the result of all conversion tasks. If the conversion fails for a particular video file, the script displays a return value of ffmpeg utility and the name of the file which is not successfully converted.
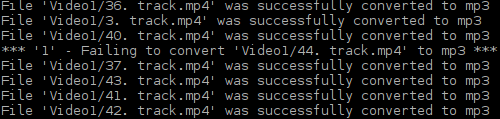
Picture 2 - Output from Log File
End.
GRE over IPSec Tunnel and NAT Between Cisco and VyOS
The goal of this tutorial is to provide a configuration for Cisco and VyOS network devices with configured PAT (Port Address Translation) that connect two remote sides A and B through point-to-point GRE tunnel encapsulated into a IPsec tunnel. In a previous tutorial we proved that GRE tunnels in conjunction with IPsec tunnels transmit multicast traffic while data integrity, authentication and confidentiality was in place. I also provided a simple configuration of GRE, IPsec tunnel and OSPF routing protocol on the Cisco and VyOS routers. In this tutorial I will go further and provide full configuration of the all network devices including PAT and access-lists. 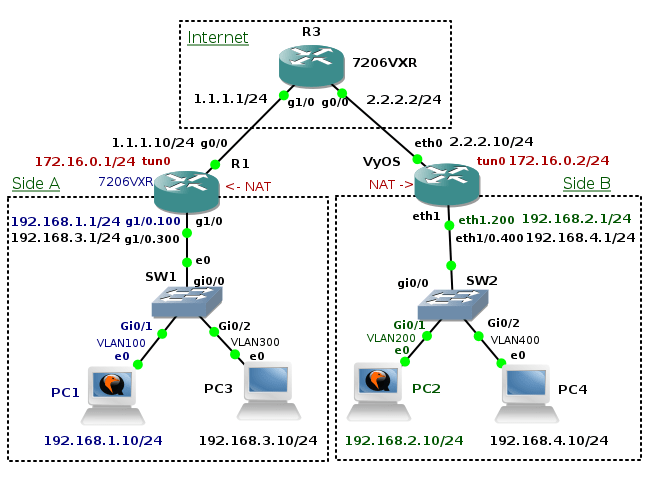
Picture 1 - Network Topology
Topology Description - Side A
Each side has a Layer 2 Cisco switch located in a LAN network. A switch connects hosts to its switchports. Each switchport is assigned to a particular VLAN. For instance, a host PC1 is connected to the switch SW1 and the switchport is assigned to a VLAN 100. Hosts in VLAN 100 (subnet 192.168.1.0/24) have guaranteed access to a remote subnet 192.168.2.0/24 via GRE/IPsec tunnel. A NAT access-list configured on a router R1 ensures that IP address of the host in VLAN 100 is not translated by PAT when a destination address is Continue reading
Scripts
This article contains a list of scripts that I created and that are somehow useful for me. You are free to download and modify them according to your needs. I do not take any responsibility for improper use or any damage caused by using them.
1. Networking & Servers
1.1 Automatic Deployment VyOS ISO on VMware VM
A Bash script deploy vyos.sh downloads the latest VyOS ISO image and an Expect script install vyos.exp installs VyOS ISO on VMware vmdk disk.
1.2 Automatic Deployment of DRBL (Clonezilla) Server
The script deploy drbl.sh installs and configure DRBL server on Ubuntu with a single Ethernet card. You have to provide the name of Ethernet interface as an argument. The script creates a virtual interface for you based on a physical interface. It also downloads a DRBL project public key, download and install drbl package from repository.
1.3 Secure Copy with Rsync from SSH server
The script copy.sh keeps copying files with rsync command while a return value of the rsync command is not zero. Just edit script and set server IP address and bothe remote and local directory.
1.4 Collecting MAC and IP addresses Continue reading
Hacking DRBL Client PXE Boot Password
In a previous tutorial I showed installation of Clonezilla Server Edition on Ubuntu using my own Bash script. We configured PXE (Pre eXecution Environment)) password for clients so when the clients booted a password had to be entered to startup. This tutorial explains two different ways how to get and crack the PXE boot password.
Picture 1 - Client Requires to Enter PXE Password During Startup
First, we should mention some facts. The PXE client password is stored in plain text in a configuration file /etc/drbl/drblpush.conf. The password is secretpassword and it can be found in a dictionary rockyout.txt.
![]()
Picture 2 - Plain Text PXE Client Boot Password
The same PXE client password is stored as a hash in a file /tftpboot/nbi_img/prelinux.cfg/default.
![]()
Picture 3 - PXE Client Boot SHA-1 Base64 Encoded Salted Hash
The hash is created by utility /usr/sbin/sha1pass on DRBL server. It is a Perl script which takes two arguments from STDIN - a password and salt and it creates SHA-1 base64 salted hash.
![]()
Picture 4 - Perl Script fo Generating Hash from Password and Salt
Explanation:
- $4$ - SHA-1 base64 encoded salted hash
- 2mNryVVj - salt
- WIWlkNc6cA9+eQqcf9xU0d5IvVQ - hash
They are several methods how to obtain PXE boot Continue reading
Clonezilla Server Edition Installation on Ubuntu

The tutorial describes installation steps for Clonezilla Server Edition (SE) on Ubuntu 16.04.1 LTS using a Bash script. Clonezilla is OpenSource Cloning System (OCS) and it is a partition and disk imaging/cloning program . It helps you to do system deployment, bare metal backup and recovery. Two types of Clonezilla are available, Clonezilla live and Clonezilla SE (server edition).
Clonezilla live is suitable for single machine backup and restore. Clonezilla SE is for massive deployment because it can clone many computers simultaneously. Clonezilla saves and restores only used blocks in the hard disk. It decreases time and saves the hard disk space and increases the clone efficiency.
Clonezilla is a part of DRBL (Diskless Remote Boot in Linux) which provides a diskless environment for client machines. Therefore we need to install and configure DRBL server first. I created DRBL deployment script deploy_drbl.sh that helps you to install DRBL and configure server on Ubuntu with a single Ethernet card. You have to provide only the name of Ethernet interface and the script creates virtual interface for you based on your physical interface. It also downloads a DRBL project public key, download and install drbl package from repository. The script starts interactive Bash and Perl scripts that come with Continue reading
Using Rsync to Copy Files From SSH Server
Recently I have come through an interesting problem. I needed to download a raw copy of the HDD image located on a remote server (about 180GB) connected via 1 Mbps link. Network connection dropped frequently so the requirement was to reestablish connection automatically, without my intervention.
Definition of Terms
Server - a remote computer with an IP address 172.17.100.5/16 which contains a raw copy of the HDD image - a file /root/ubuntu.iso.
Client - a local computer that copies a raw copy of the HDD image from the server.
Below is my how-to which helped me to fulfill a task. I hope it might be useful to you.
1. Create Multiple Archive Files
The idea is to create a compressed archive file and to split it to multiple sequential chunks in order to make transfer of files less depended on network outages due to an unreliable link.
$ tar cvf - ubuntu.iso | gzip -9 - | split -b 10M -d - ./disk/ubuntu.tar.gz.
The command tar creates a tar archive from a file ubuntu.iso and send it to a standard output instead to the file. The command gzip compress everything from a standard input using the best compression ratio (parameter -9) and send Continue reading
Quagga Routing Software with EIGRP Support
In May 2013, Cisco opened its proprietary EIGRP protocol and released an informational RFC 7868 - Cisco's Enhanced Interior Gateway Routing Protocol (EIGRP). It gives other vendors an opportunity to implement EIGRP protocol into their devices. A group students led by an assistant professor and Cisco CCIE Peter Paluch who is an instructor trainer at the Faculty of Management Science and Informatics, University of Zilina, Slovakia implemented EIGRP support into Quagga routing software.
The goal of this tutorial is to provide a VMware vmdk disk with installed Linux Core and Quagga which supports Cisco EIGRP protocol. The image can be used to test compatibility between EIGRP configured on native Cisco devices and an implementation of EIGRP daemon in Quagga . I also share my findings about issues that I have noticed during my tests.
Here you can download Linux Core vmdk disk with installed Quagga 0.99.24-rc1 which supports EIGRP.
How did I create Quagga Qemu Image with EIGRP Support
I installed Linux Core 7.2 to Qemu virtual machine and remastered Core for sending output to a serial port according to this tutorial. I download Quagga version which supports EIGRP from github and I installed it from source. Afterwards I created Linux Core Quagga extension. I did not submit Continue reading
Forensics Challenge for CSIRT Team – Part 2 Solution
The goal of the tutorial is to provide a solution to the forensic challenge game that I created for testing forensic skills of CSIRT team. Please be careful and run a suspicious binary file located inside a provided virtual machine only in a secured environment in order to avoid unwanted damage or loss.
As you can notice, some files are being encrypted right after boot of a virtual machine. All these files have suffix .enc001. You can easily located them with the command:
$ find / -name "*.enc001" -type f 2>/dev/null
There is also a file named encryption_warning.txt located in a home directory of an actual user and it contains a following warning message.
*** Your files have been encrypted! ***
*** To decrypt them, run '/usr/local/bin/ls %1a%your_decryption_key ***
Without any doubts a utility ls is not a cryptography tool so it is a good place where we can start our investigation. The command /usr/local/bin/ls -la shows files in a actual directory.
ubuntu@ubuntu:~$ /usr/local/bin/ls -la
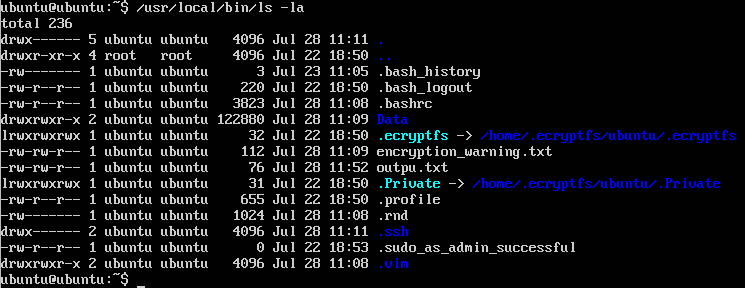
Picture 1 - Content of Actual Directory
The output looks good. But what does happen if we display a non-existing file kdkdkdkdk?
ubuntu@ubuntu:~$ /usr/local/bin/ls kdkdkdkdk
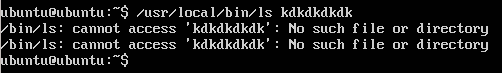
Picture 2 - Two Error Messages
They are two interesting facts shown in the output of the command /usr/local/bin/ls . Firstly, two Continue reading
Forensics Challenge for CSIRT Team – Part 1 Assignment
I have created a virtual machine that you can use to test your forensics analysis skills. Please, download the VM, solve an assignment below and share solutions with us.
1. Assignment
Your are a member of elite CSIRT team which is responsible for dealing with computer security incidents in your jurisdiction. You are asked to investigate a server that was previously administered by disgruntled administrator Mr. Abdullah Khan who was fired up. Although login credentials for server were changed after Khan's sacking from the company, it is believed he might insert malicious software into server before change of credentials. Your task is to ensure that a sever does not contain any malicious software and user data stored on the server are not compromised. You also need to prove your professional forensic skills and analyze a suspicious file in case you find it on the server. Based on your investigation you should find out how malware work and create detailed report for your boss.
The server is running Ubuntu 16.04.1 and it is primary used as a file server with configured SSH access. Unfortunately the backup of user files is damaged and cannot be used in case of data are lost during your investigation. The login/password is Continue reading
Forensic Lab Game Zero – Level 2 Results
Below are my solutions to the level 2 of the forensics lab game zero. The solutions to the level 1 of the game are posted here.
1. Find way to reset root's account password and retrieve flag from /root/flag.txt
Reboot the VM and press 'e ' edit inside the Grub menu screen. Add command init=/bin/bash at the end of the line starting with linux and press F10. Thne mount file system as read-write.
root@(none):/# mount -n -o remount,rw /
Change password for user root.
root@(none):/# passwd
root@(none):/# cat /root/flag.txt
8d55761dfafe912daa2fa6c38e05435093f7f636
root@(none):/# echo -n '8d55761dfafe912daa2fa6c38e05435093f7f636' | sha1sum
0166bc38c1165d0ba783ea722b84ed3a0d2547f8
Restart the virtual machine and switch to the root account.
2. There is a memory dump of the windows machine is stored in file /root/memdump.mem. Find the flag among commands executed on that machine
Find info about our memory dump with imageinfo plugin.
root@debian1989:/home/kassad# python /opt/tools/volatility-2.4/vol.py imageinfo -f /root/memdump.mem | grep Profile
Volatility Foundation Volatility Framework 2.4
Suggested Profile(s) : Win7SP0x86, Win7SP1x86
To avoid typing chosen profile --profile=Win7SP1x86 every time vol.py is called, export the profile.
root@debian1989:/home/kassad# export VOLATILITY_PROFILE=Win7SP1x86
To avoid typing path to memory dump file, export memory dump location so you do not need to add argument -f Continue reading
Forensic Lab Game Zero – Level 1 Results
The goal of the post is to provide solutions for the first level of the game for "hackers" created by forensic lab of CESNET association. With this game CESNET introduces a work of forensic analysts and test your knowledge of Linux OS. They are several assignments and practical tasks included inside Debian image which is available for download here. The question / answer sheet is located inside the home directory of user kassad.
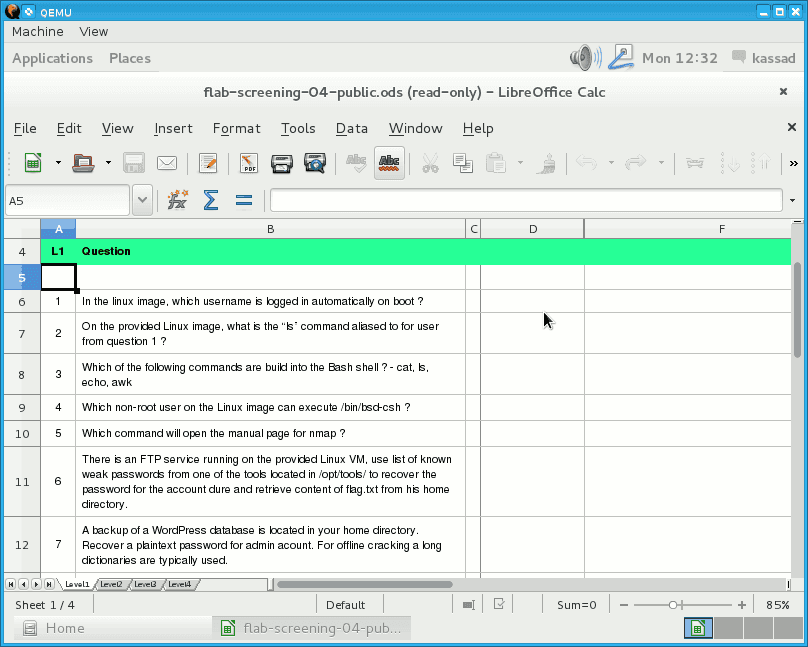
Picture 1 - Answer Sheet
1. In the Linux image, which username is logged in automatically on boot?
Check the desktop environment.
kassad@debian1989:~$ echo $DESKOP_SESSION
gnome-fallback
Check if automated login is enabled for Gnome desktop.
kassad@debian1989:~$ grep 'AutomaticLogin' /etc/gdm3/daemon.conf
AutomaticLoginEnable = true
AutomaticLogin = kassad
The automated login is enabled for the user kassad. Now we need to compute the sha1 hash for the result.
kassad@debian1989:~$ echo -n 'kassad' | sha1sum
fb1216c760d6c0996991108886d1797d8bd4ca27
2. On the provided Linux image, what is the “ls” command aliased to for user from question 1 ?
kassad@debian1989:~$ type ls
ls is aliased to `ls --color=auto'
We can get the result also by checking the content of the file /home/kassad/.bashrc.
kassad@debian1989:~$ grep 'alias ls' /home/kassad/.bashrc
alias ls='ls --color=auto'
kassad@debian1989:~$ echo -n 'ls --color=auto' Continue reading
Slovakia Wins Cyber Exercise Locked Shields 2016
Tallinn, April 22, 2016 - The team from Slovakia won Locked Shields 2016, the world’s largest and most advanced international live-fire cyber defence exercise. They were closely followed by the NCIRC team from NATO and Finland.
Read more here.
BASH Script for Dictionary Attack Against SSH Server
Although they are several dictionary password attack tools available for Linux such as Hydra, Ncrack, I have decided to practice BASH scripting and write a script getsshpass.sh that can perform dictionary attack against SSH server. The script reads usernames and passwords from dictionaries (the one for usernames and the one for passwords) and uses them one-by-one during its login attempt to remote SSH server. Once correct username and password are found, the script save them to the file result.txt and displays them on the desktop. Then it exits.
The script can be started either in a serial mode that opens only single SSH session to SSH server or in a parallel mode which allows multipe SSH sessions to be opened at the same time. Below are parameters of the script.

Picture 1 - Script Parameters
All parameters are self-explanatory. If a parameter -l is not entered the script is started in a default serial mode. In case of parallel mode is used (-l parameter) it is recommended to use -l parameter together with -n parameter. The -n parameter slows down generating SSH sessions by inserting fixed number of seconds before a new SSH session is generated. This helps the attack to be successful. According to my findings during Continue reading
Collecting MAC and IP Adresses of Hosts Connected to Cisco Switches Using SNMP
The goal of this article is to introduce a script that automates a process of collecting MAC and IP address of hosts connected to Cisco switches using Simple Network Management Protocol (SNMP). We will configure SNMP version 2c and 3 on Cisco switches and create a BASH script that collects required data for us. For this purpose I have created a test network lab using GNS3. The topology consists of three Cisco virtual switch appliances running vIOS-L2 and one network management station (NMS) based on Kali Linux. Network hosts are simulated by Core Linux appliances connected to Cisco vIOS-l2 switches.
1. GNS3 Lab
1.1 List of software used for creating GNS3 lab
- Host OS
x86-64 Linux Fedora with installed GNS3 1.3.11 and Qemu1.4.0 - Network Management Station
Linux Kali 3.18.0-kali3-amd64 - Swiches
Cisco vIOS l2 Software (vios_l2-ADVENTERPRISEK9-M), Version 15.2
Cisco Catalyst 3550 (C3550-IPSERVICESK9-M), Version 12.2(55)SE9 - Network Host (End device)
Linux Core 3.16.6-tinycore64
1.2 Network Topology Description
All virtual network and host devices are running inside GNS3 project and they are emulated by Qemu emulator and virtualizer. The only exception is a Cisco Catalyst 3550 switch that is connected to topology via GNS3 network Continue reading
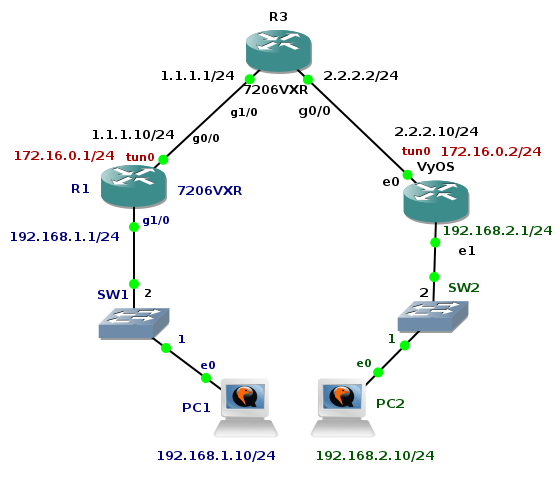
GRE over IPSec Tunnel Between Cisco and VyOS
The previous tutorial shown GRE tunnel configuration between Cisco router and Linux Core. The big advantage of GRE protocol is that it encapsulates L3 and higher protocols inside the GRE tunnel so routing updates and other multicast traffic can be successfully transferred over the tunnel. The main drawback of GRE protocol is the lack of built-in security. Data are transferred in plain-text over the tunnel and peers are not authenticated (no confidentiality). Tunneled traffic can be changed by attacker (no integrity checking of IP packets). For this reason GRE tunnel is very often used in conjunction with IPSec. Typically, GRE tunnel is encapsulated inside the IPSec tunnel and this model is called GRE over IPSec.
The tutorial shows configuration of OSPF routing protocol, GRE and IPSec tunnel on Cisco 7206 VXR router and appliance running VyOS network OS. Devices are running inside GNS3 lab an they are emulated by Dynamips (Cisco) and Qemu (VyOS).
Picture 1 - Topology
Note: VyOS installation is described here. You can easily build your own VyOS Qemu appliance using the Expect and Bash script shared in the article.
1. R3 Configuration
R3(config)# interface gigabitEthernet 1/0
R3(config-if)# ip address 1.1.1.1 255.255.255.0
R3(config-if)# no shutdown
R3(config-if)# interface gigabitEthernet 0/0
R3(config-if)# ip Continue reading
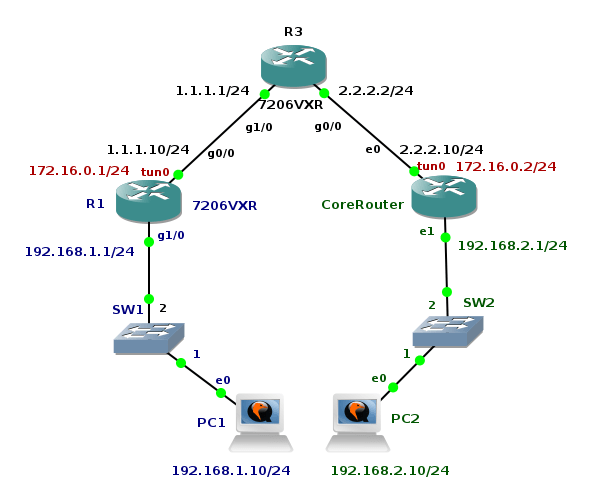
GRE Tunnel Between Cisco and Linux
Generic Routing Encapsulation - GRE is a tunneling protocol originally developed by Cisco that encapsulates various network protocols inside virtual point-to-point tunnel. It transports multicast traffic via GRE tunnel so it allows passing of routing information between connected networks. As it lacks of security it is very often used in conjunction IP SEC VPN that on the other hand is not capable to pass multicast traffic.
The goal of the tutorial it to show configuration of GRE tunnel on a Cisco router and a device with OS Linux. I have created GNS3 lab consisting of two local networks - 192.168.1.0/24 and 192.168.2.0/24 connected via GRE tunnel. GRE tunnel interface is configured on router R1 (Cisco 7206VXR) and Core Router (Core Linux with Quagga routing daemon installed). The both routers have their outside interfaces connected to a router R3 that is located in the "Internet". To prove that GRE tunnel is working and transporting multicast traffic, the OSPF routing protocol is started on R1 and Core routers and configured on tunnel interfaces and interfaces pointing to local networks.
Note: The Core Linux vmdk image is available for download here.
1. Initial Configuration
First we assign hostnames and Continue reading