Parallel streaming of progressive images


Progressive image rendering and HTTP/2 multiplexing technologies have existed for a while, but now we've combined them in a new way that makes them much more powerful. With Cloudflare progressive streaming images appear to load in half of the time, and browsers can start rendering pages sooner.
In HTTP/1.1 connections, servers didn't have any choice about the order in which resources were sent to the client; they had to send responses, as a whole, in the exact order they were requested by the web browser. HTTP/2 improved this by adding multiplexing and prioritization, which allows servers to decide exactly what data is sent and when. We’ve taken advantage of these new HTTP/2 capabilities to improve perceived speed of loading of progressive images by sending the most important fragments of image data sooner.
This feature is compatible with all major browsers, and doesn’t require any changes to page markup, so it’s very easy to adopt. Sign up for the Beta to enable it on your site!
What is progressive image rendering?
Basic images load strictly from top to bottom. If a browser has received only half of an image file, it can show only the top Continue reading
Better HTTP/2 Prioritization for a Faster Web


HTTP/2 promised a much faster web and Cloudflare rolled out HTTP/2 access for all our customers long, long ago. But one feature of HTTP/2, Prioritization, didn’t live up to the hype. Not because it was fundamentally broken but because of the way browsers implemented it.
Today Cloudflare is pushing out a change to HTTP/2 Prioritization that gives our servers control of prioritization decisions that truly make the web much faster.
Historically the browser has been in control of deciding how and when web content is loaded. Today we are introducing a radical change to that model for all paid plans that puts control into the hands of the site owner directly. Customers can enable “Enhanced HTTP/2 Prioritization” in the Speed tab of the Cloudflare dashboard: this overrides the browser defaults with an improved scheduling scheme that results in a significantly faster visitor experience (we have seen 50% faster on multiple occasions). With Cloudflare Workers, site owners can take this a step further and fully customize the experience to their specific needs.
Background
Web pages are made up of dozens (sometimes hundreds) of separate resources that are loaded and assembled by the browser into the final displayed content. This includes the Continue reading
Argo and the Cloudflare Global Private Backbone


Welcome to Speed Week! Each day this week, we’re going to talk about something Cloudflare is doing to make the Internet meaningfully faster for everyone.
Cloudflare has built a massive network of data centers in 180 cities in 75 countries. One way to think of Cloudflare is a global system to transport bits securely, quickly, and reliably from any point A to any other point B on the planet.
To make that a reality, we built Argo. Argo uses real-time global network information to route around brownouts, cable cuts, packet loss, and other problems on the Internet. Argo makes the network that Cloudflare relies on—the Internet—faster, more reliable, and more secure on every hop around the world.
We launched Argo two years ago, and it now carries over 22% of Cloudflare’s traffic. On an average day, Argo cuts the amount of time Internet users spend waiting for content by 112 years!
As Cloudflare and our traffic volumes have grown, it now makes sense to build our own private backbone to add further security, reliability, and speed to key connections between Cloudflare locations.
Today, we’re introducing the Cloudflare Global Private Backbone. It’s been in operation for a while now and links Continue reading
Welcome to Speed Week!


Every year, we celebrate Cloudflare’s birthday in September when we announce the products we’re releasing to help make the Internet better for everyone. We’re always building new and innovative products throughout the year, and having to pick five announcements for just one week of the year is always challenging. Last year we brought back Crypto Week where we shared new cryptography technologies we’re supporting and helping advance to help build a more secure Internet.
Today I’m thrilled to announce we are launching our first-ever Speed Week and we want to showcase some of the things that we’re obsessed with to make the Internet faster for everyone.
How much faster is faster?
When we built the software stack that runs our network, we knew that both security and speed are important to our customers, and they should never have to compromise one for the other. All of the products we’re announcing this week will help our customers have a better experience on the Internet with as much as a 50% improvement in page load times for websites, getting the most out of HTTP/2’s features (while only lifting a finger to click the button that enables them), finding the optimal route across Continue reading
eBPF can’t count?!
It is unlikely we can tell you anything new about the extended Berkeley Packet Filter, eBPF for short, if you've read all the great man pages, docs, guides, and some of our blogs out there.
But we can tell you a war story, and who doesn't like those? This one is about how eBPF lost its ability to count for a while1.
They say in our Austin, Texas office that all good stories start with "y'all ain't gonna believe this… tale." This one though, starts with a post to Linux netdev mailing list from Marek Majkowski after what I heard was a long night:
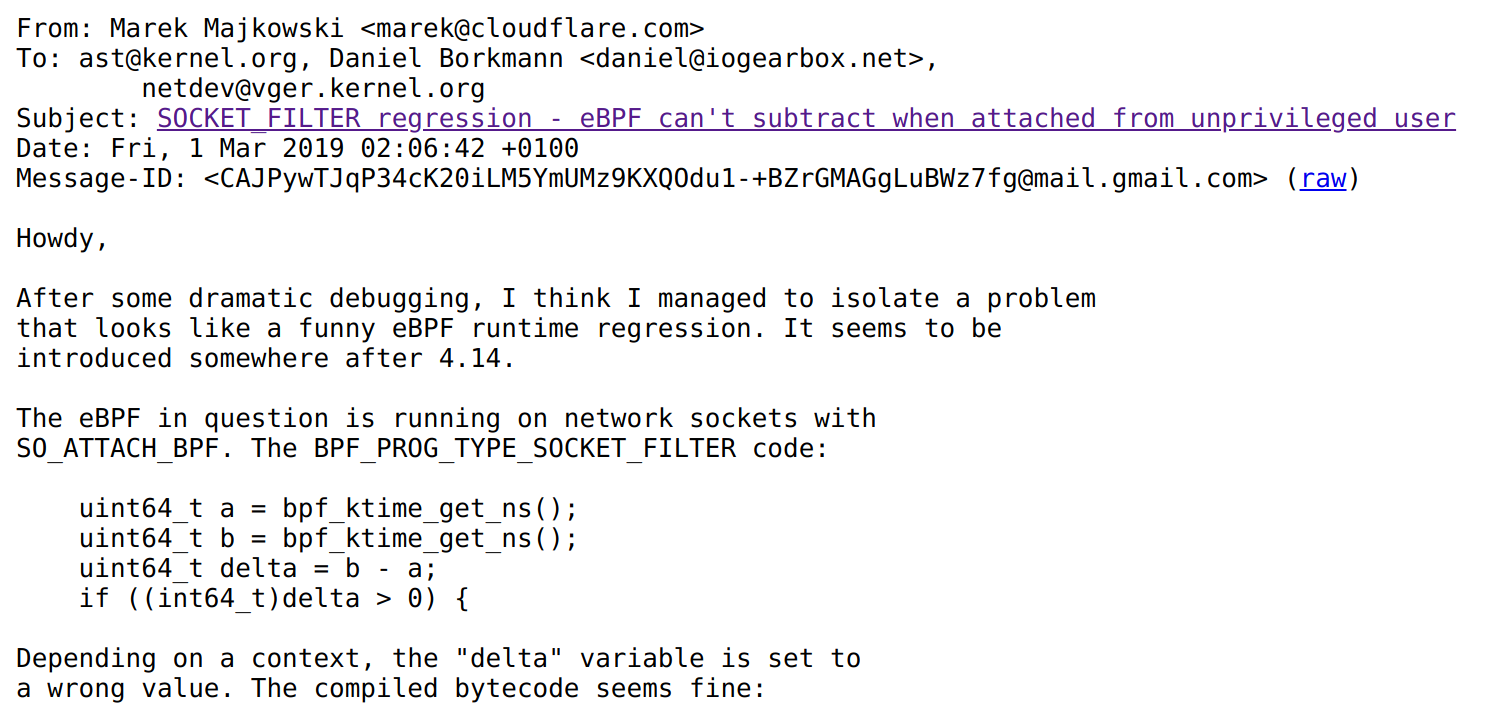
Marek's findings were quite shocking - if you subtract two 64-bit timestamps in eBPF, the result is garbage. But only when running as an unprivileged user. From root all works fine. Huh.
If you've seen Marek's presentation from the Netdev 0x13 conference, you know that we are using BPF socket filters as one of the defenses against simple, volumetric DoS attacks. So potentially getting your packet count wrong could be a Bad Thing™, and affect legitimate traffic.
Let's try to reproduce this bug with Continue reading
Unit Testing Workers, in Cloudflare Workers


We recently wrote about unit testing Cloudflare Workers within a mock environment using CloudWorker (a Node.js based mock Cloudflare Worker environment created by Dollar Shave Club's engineering team). See Unit Testing Worker Functions.
Even though Cloudflare Workers deploy globally within seconds, software developers often choose to use local mock environments to have the fastest possible feedback loop while developing on their local machines. CloudWorker is perfect for this use case but as it is still a mock environment it does not guarantee an identical runtime or environment with all Cloudflare Worker APIs and features. This gap can make developers uneasy as they do not have 100% certainty that their tests will succeed in the production environment.
In this post, we're going to demonstrate how to generate a Cloudflare Worker compatible test harness which can execute mocha unit tests directly in the production Cloudflare environment.
Directory Setup
Create a new folder for your project, change it to your working directory and run npm init to initialise the package.json file.
Run mkdir -p src && mkdir -p test/lib && mkdir dist to create folders used by the next steps. Your folder should look like this:
.
./dist
./src/worker.js
./test
./test/lib
. Continue readingThe Serverlist Newsletter: A big week of serverless announcements, serverless Rust with WASM, cloud cost hacking, and more

Check out our fourth edition of The Serverlist below. Get the latest scoop on the serverless space, get your hands dirty with new developer tutorials, engage in conversations with other serverless developers, and find upcoming meetups and conferences to attend.
Sign up below to have The Serverlist sent directly to your mailbox.
Rapid Development of Serverless Chatbots with Cloudflare Workers and Workers KV

I'm the Product Manager for the Internal Tools team here at Cloudflare. We recently identified a need for a new tool around service ownership. As a fast growing engineering organization, ownership of services changes fairly frequently. Many cycles get burned in chat with questions like "Who owns service x now?
Whilst it's easy to see how a tool like this saves a few seconds per day for the asker and askee, and saves on some mental context switches, the time saved is unlikely to add up to the cost of development and maintenance.
= 5 minutes per day
x 260 work days
= 1300 mins
/ 60 mins
= 20 person hours per year
So a 20 hour investment in that tool would pay itself back in a year valuing everyone's time the same. While we've made great strides in improving the efficiency of building tools at Cloudflare, 20 hours is a stretch for an end-to-end build, deploy and operation of a new tool.
Enter Cloudflare Workers + Workers KV
The more I use Serverless and Workers, the more I'm struck with the benefits of:
1. Reduced operational overhead
When I upload a Worker, it's automatically distributed to 175+ data Continue reading
We want to host your technical meetup at Cloudflare London

Cloudflare recently moved to County Hall, the building just behind the London Eye. We have a very large event space which we would love to open up to the developer community. If you organize a technical meetup, we'd love to host you. If you attend technical meetups, please share this post with the meetup organizers.

About the space
Our event space is large enough to hold up to 280 attendees, but can also be used for a small group as well. There is a large entry way for people coming into our 6th floor lobby where check-in may be managed. Once inside the event space, you will see a large, open kitchen area which can be used to set up event food and beverages. Beyond that is Cloudflare's all-hands space, which may be used for your events.
We have several gender-neutral toilets for your guests' use as well.
Lobby
You may welcome your guests here. The event space is just to the left of this spot.

Event space
This space may be used for talks, workshops, or large panels. We can rearrange seating, based on the format of your meetup.

Food & Continue reading
xdpcap: XDP Packet Capture

Our servers process a lot of network packets, be it legitimate traffic or large denial of service attacks. To do so efficiently, we’ve embraced eXpress Data Path (XDP), a Linux kernel technology that provides a high performance mechanism for low level packet processing. We’re using it to drop DoS attack packets with L4Drop, and also in our new layer 4 load balancer. But there’s a downside to XDP: because it processes packets before the normal Linux network stack sees them, packets redirected or dropped are invisible to regular debugging tools such as tcpdump.
To address this, we built a tcpdump replacement for XDP, xdpcap. We are open sourcing this tool: the code and documentation are available on GitHub.
xdpcap uses our classic BPF (cBPF) to eBPF or C compiler, cbpfc, which we are also open sourcing: the code and documentation are available on GitHub.

Tcpdump provides an easy way to dump specific packets of interest. For example, to capture all IPv4 DNS packets, one could:
$ tcpdump ip and udp port 53
xdpcap reuses the same syntax! xdpcap can write packets to a pcap file:
$ xdpcap /path/to/hook capture.pcap Continue readingThe Climate and Cloudflare


Power is the precursor to all modern technology. James Watt’s steam engine energized the factory, Edison and Tesla’s inventions powered street lamps, and now both fossil fuels and renewable resources power the trillions of transistors in computers and phones. In the words of anthropologist Leslie White: “Other things being equal, the degree of cultural development varies directly as the amount of energy per capita per year harnessed and put to work.”
Unfortunately, most of the traditional ways to generate power are simply not sustainable. Burning coal or natural gas releases carbon dioxide which directly leads to global warming, and threatens the habitats of global ecosystems, and by extension humans. If we can’t minimize the impact, our world will be dangerously destabilized -- mass extinctions will grow more likely, and mass famines, draughts, migration, and conflict will only be possible to triage rather than avoid.
Is the Internet the primary source of this grave threat? No: all data centers globally accounted for 2-3% of total global power use in recent years, and power consumption isn’t the only contributor to human carbon emissions. Transportation (mostly oil use in cars, trucks, ships, trains, and airplanes) and industrial processing (steel, chemicals, heavy manufacturing, Continue reading
Eating Dogfood at Scale: How We Build Serverless Apps with Workers


You’ve had a chance to build a Cloudflare Worker. You’ve tried KV Storage and have a great use case for your Worker. You’ve even demonstrated the usefulness to your product or organization. Now you need to go from writing a single file in the Cloudflare Dashboard UI Editor to source controlled code with multiple environments deployed using your favorite CI tool.
Fortunately, we have a powerful and flexible API for managing your workers. You can customize your deployment to your heart’s content. Our blog has already featured many things made possible by that API:
These tools make deployments easier to configure, but it still takes time to manage. The Serverless Framework Cloudflare Workers plugin removes that deployment overhead so you can spend more time working on your application and less on your deployment.
Focus on your application
Here at Cloudflare, we’ve been working to rebuild our Access product to run entirely on Workers. The move will allow Access to take advantage of the resiliency, performance, and flexibility of Workers. We’ll publish a more detailed post about that migration once complete, but the experience required that we retool some of our Continue reading
Announcing AMP Real URL


The promise of the AMP (Accelerated Mobile Pages) project was that it would make the web, and, in particular, the mobile web, much more pleasant to surf. The AMP HTML framework was designed to make web pages load quickly, and not distract the user with extraneous content that took them away from focusing on the web page’s content.
It was particularly aimed at publishers (such as news organizations) that wanted to provide the best, fastest web experience for readers catching up on news stories and in depth articles while on the move. It later became valuable for any site which values their mobile performance including e-commerce stores, job boards, and media sites.
As well as the AMP HTML framework, AMP also made use of caches that store copies of AMP content close to end users so that they load as quickly as possible. Although this cache make loading web pages much, much faster they introduce a problem: An AMP page served from Google’s cache has a URL starting with https://google.com/amp/. This can be incredibly confusing for end users.
Users have become used to looking at the navigation bar in a web browser to see what web site Continue reading
China | Silicon Valley | China: A path less traveled
“Real knowledge is to know the extent of one's ignorance.”
― Confucius
Blueprint:

Don’t tell our CEO, Matthew Prince, but the first day I interviewed at Cloudflare I had a $9.00 phone in my pocket, a knock-off similar to a Nokia 5140, but the UI was all in Chinese characters—that phone was a fitting symbol for my technical prowess. At that time in my career I could send emails and use Google, but that was about the extent of my tech skill set. The only code I’d ever seen was in the Matrix, Apple computers confused me, and I was working as a philosophy lecturer at The University of California, Santa Cruz. So, you know, I was pretty much the ideal candidate for a deeply technical, Silicon Valley startup.
This was in 2013. I had just returned from two years of Peace Corps service in the far Southwest of China approaching the Himalayan plateau. That experience gave me the confidence to walk into Cloudflare’s office knowing that I would be good for the job despite the gaps in my knowledge. My early training in philosophy plus my Peace Corps service gave me a blueprint for learning and Continue reading
Help us update the Cloudflare Blog!


As you’ve probably noticed over the years, we’re always evolving and improving the look and feel of different aspects of the Cloudflare experience. Sometimes it’s more about function, other times it’s more about form, and most of the time it’s a combination of both. But there’s one area of the site that many users visit even more frequently than they visit the homepage or their dashboard, and strangely enough it hasn’t really seen any major updates in years. And if you’re reading this, that means you're looking at it.
With more than 150 current contributors, and more than 1,000 posts, we have a lot of people dedicating a lot of their time to writing blog posts. And based on the responses I see in the comments, and on Twitter, there are a lot of people who really like to read what these authors have to say (whether it has much to do with Cloudflare or not).
Well, we’d like to finally give some love to the blog. And we really want to know what you, our loyal (or even occasional) readers, think. There are two options to choose from. Continue reading
Introducing Warp: Fixing Mobile Internet Performance and Security


April 1st is a miserable day for most of the Internet. While most days the Internet is full of promise and innovation, on “April Fools” a handful of elite tech companies decide to waste the time of literally billions of people with juvenile jokes that only they find funny.
Cloudflare has never been one for the traditional April Fools antics. Usually we just ignored the day and went on with our mission to help build a better Internet. Last year we decided to go the opposite direction launching a service that we hoped would benefit every Internet user: 1.1.1.1.
The service's goal was simple — be the fastest, most secure, most privacy-respecting DNS resolver on the Internet. It was our first attempt at a consumer service. While we try not to be sophomoric, we're still geeks at heart, so we couldn't resist launching 1.1.1.1 on 4/1 — even though it was April Fools, Easter, Passover, and a Sunday when every media conversation began with some variation of: "You know, if you're kidding me, you're dead to me."
No Joke
We weren't kidding. In the year that's followed, we've been overwhelmed by the response. Continue reading
Transgender Day of Visibility

My name is Kas. I’m a Cloudflare employee and I wanted to share my story with you on International Transgender Day of Visibility.
I've been different for as long as I can remember. I've been the odd one out not just for the time I've spent in tech, but most of my life.
I'm transgender in that I am gender non-binary. I'm working with the word 'agender' right now, as it is the word that describes me best: I'm not a woman, or a man, just a human. I don't really have a gender, and I certainly don't identify with either binary label.
Being transgender in tech is difficult. There are many times where we have to work harder, smarter, and give up so much to stay afloat. Times where you have to weigh the benefits of correcting your pronouns against the title of the person who is to be corrected (are they a customer? Your bosses' bosses' boss?). Times where you don't know if you can even be 'out' with your coworkers, because you just don't know if, or how, they'll treat you differently, or fairly.
Being agender or outside the Continue reading
? The Wrangler CLI: Deploying Rust with WASM on Cloudflare Workers


Today, we're open sourcing and announcing wrangler, a CLI tool for building, previewing, and publishing Rust and WebAssembly Cloudflare Workers.
If that sounds like some word salad to you, that's a reasonable reaction. All three of the technologies involved are relatively new and upcoming: WebAssembly, Rust, and Cloudflare Workers.
Why WebAssembly?
Cloudflare's mission is to help build a better Internet. We see Workers as an extension of the already incredibly powerful Web Platform, where JavaScript has allowed users to go from building small bits of interactivity, to building full applications. Node.js first extended this from the client to the server- unifying web application development around a single language – JavaScript. By choosing to use V8 isolates (the technology that powers both Node.js and the most popular browser, Chrome), we sought to make its Workers product a fully compatible, new platform for the Web, eliding the distinction between server and client. By leveraging its large global network of servers, Workers allows users to run code as close as possible to end users, eliminating the latency associated server-side logic or large client-side bundles.
But not everyone wants to write Continue reading
When I Knew Cloudflare Was the Right Place For Me

Let’s be honest, interviewing for a new job can be a long, difficult process. Not only is it emotionally draining to handle multiple rejections, slow responses, and prolonged processes, it can be physically exhausting to sit through hours of stale interviews. A former colleague of mine compared interviewing to navigating a jungle; one misstep here, one wrong answer there, and you barely make it out alive. I once had an interviewer set out a 200-piece puzzle for me to complete in order to “evaluate my problem solving skills”. Basically, when it comes to interviews, you never know what you are going to get. As you may be able to tell, my feelings towards finding a new job this past fall were grim, until I interviewed with Cloudflare.
If you truly want to be impressed by Cloudflare, interview with them. Every employee knows the process is deliberate, thoughtful, and diverse in taking the time to get to know a candidate while the candidate gets to know Cloudflare. It is humbling to realize that any employee interviewing has also passed through this challenging process. It all starts with a phone call, as most interviews do, and the process is fairly standard until Continue reading
BoringTun, a userspace WireGuard implementation in Rust
Today we are happy to release the source code of a project we’ve been working on for the past few months. It is called BoringTun, and is a userspace implementation of the WireGuard® protocol written in Rust.

A Bit About WireGuard
WireGuard is relatively new project that attempts to replace old VPN protocols, with a simple, fast, and safe protocol. Unlike legacy VPNs, WireGuard is built around the Noise Protocol Framework and relies only on a select few, modern, cryptographic primitives: X25519 for public key operations, ChaCha20-Poly1305 for authenticated encryption, and Blake2s for message authentication.
Like QUIC, WireGuard works over UDP, but its only goal is to securely encapsulate IP packets. As a result, it does not guarantee the delivery of packets, or that packets are delivered in the order they are sent.
The simplicity of the protocol means it is more robust than old, unmaintainable codebases, and can also be implemented relatively quickly. Despite its relatively young age, WireGuard is quickly gaining in popularity.
Starting From Scratch
While evaluating the potential value WireGuard could provide us, we first considered the existing implementations. Currently, there are three usable implementations
- The WireGuard kernel module - written in C, it Continue reading