Upgrading Cloud Infrastructure Made Easier and Safer Using Cloudflare Workers and Workers KV
This is a guest post by Ben Chartrand, who is a Development Manager at Timely. You can check out some of Ben's other Workers projects on his GitHub and his blog.
At Timely we started a project to migrate our web applications from legacy Azure services to a modern PaaS offering. In theory it meant no code changes.
We decided to start with our webhooks. All our endpoints can be grouped into four categories:
- Integration with internal tools i.e. HelpScout, monitoring endpoint for PagerDuty
- Payment confirmations
- Calendar integrations i.e. Google Calendar
- SMS confirmations
Despite their limited number, these are vitally important. We did a lot of testing but it was clear we’d only really know if everything was working once we had production traffic. How could we migrate traffic?
Option 1
Change the CNAME to point to the new hosting infrastructure. This is high risk. DNS takes time to propagate so, if we needed to roll back, it would take time. We would also be shifting over everything at once.
Option 2
Use a traffic manager to shift a percentage of traffic using Cloudflare Load Balancing. We could start at, say, 5% traffic to the new infrastructure Continue reading
io_submit: The epoll alternative you’ve never heard about

My curiosity was piqued by an LWN article about IOCB_CMD_POLL - A new kernel polling interface. It discusses an addition of a new polling mechanism to Linux AIO API, which was merged in 4.18 kernel. The whole idea is rather intriguing. The author of the patch is proposing to use the Linux AIO API with things like network sockets.
Hold on. The Linux AIO is designed for, well, Asynchronous disk IO! Disk files are not the same thing as network sockets! Is it even possible to use the Linux AIO API with network sockets in the first place?
The answer turns out to be a strong YES! In this article I'll explain how to use the strengths of Linux AIO API to write better and faster network servers.
But before we start, what is Linux AIO anyway?

Introduction to Linux AIO
Linux AIO exposes asynchronous disk IO to userspace software.
Historically on Linux, all disk operations were blocking. Whether you did open(), read(), write() or fsync(), you could be sure your thread would stall if the needed data and meta-data was not ready in disk cache. This usually isn't Continue reading
Un triste début d’année pour le Congo
À peine la page du calendrier tournée que nous constatons plus de troubles sur Internet.
Aujourd’hui, Cloudflare peut confirmer, chiffres à l’appui, qu’Internet a été coupé en République Démocratique du Congo, information précédemment révélée par de multiples organes de presse. Cette coupure a eu lieu alors que se déroulait l’élection présidentielle le 30 Décembre dernier, et perdure pendant la publication des résultats.
Tristement, cette situation est loin d’être une nouveauté. Nous avons fait état d'événements similaires par le passé, y compris lors d’une autre coupure d’Internet en RDC il y a moins d’un an. Une courbe malheureusement bien familière est aujourd’hui visible sur notre plateforme de gestion du réseau, montrant que le trafic dans le pays atteint péniblement un quart de son niveau habituel.

Notez que le diagramme est gradué en temps UTC, et que la capitale de la RDC Kinshasa est dans le fuseau horaire GMT+1.
La chute du trafic a démarré en milieu de journée le 31 Décembre 2018 (à environ 10h30 UTC, soit 11h30 heure locale à Kinshasa). Celà est d’autant plus frappant quand sont superposées toutes les courbes quotidiennes:

Ci-dessus, la courbe rouge représente le trafic du 31 Décembre, et les courbes grises celui des 8 Continue reading
Sad start to the new year in the Democratic Republic of the Congo
The calendar has barely flipped to 2019 and already we’re seeing Internet disruptions.
Today, Cloudflare can quantitatively confirm that Internet access has been shut down in the Democratic Republic of the Congo, information already reported by many press organisations. This shutdown occurred as the presidential election was taking place on December the 30th, and continues as the results are published.
Sadly, this act is far from unprecedented. We have published many posts about events like this in the past, including a different post about roughly three days of Internet disruption in the Democratic Republic of the Congo less than a year ago. A painfully familiar shape can be seen on our network monitoring platform, showing that the traffic in the country is barely reaching a quarter of its typical level:
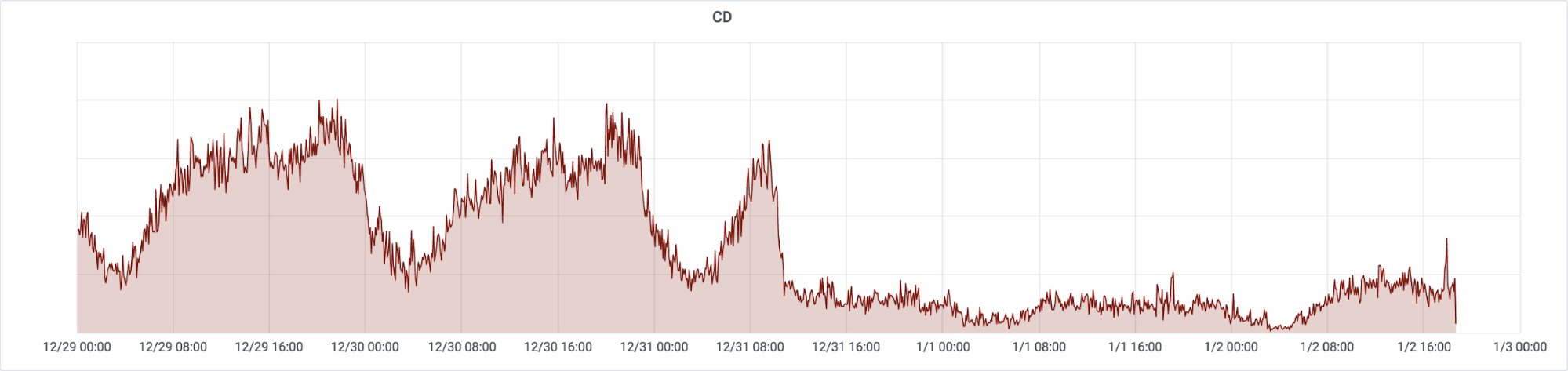
Note that the graph is based on UTC and Democratic Republic of the Congo’s capital Kinshasa has the timezone of GMT+1.
The drop in bandwidth started just before midday on 31 December 2018 (around 10:30 UTC, 11:30 local time in Kinshasa). This can be clearly seen if we overlay each 24 hour day over each other:
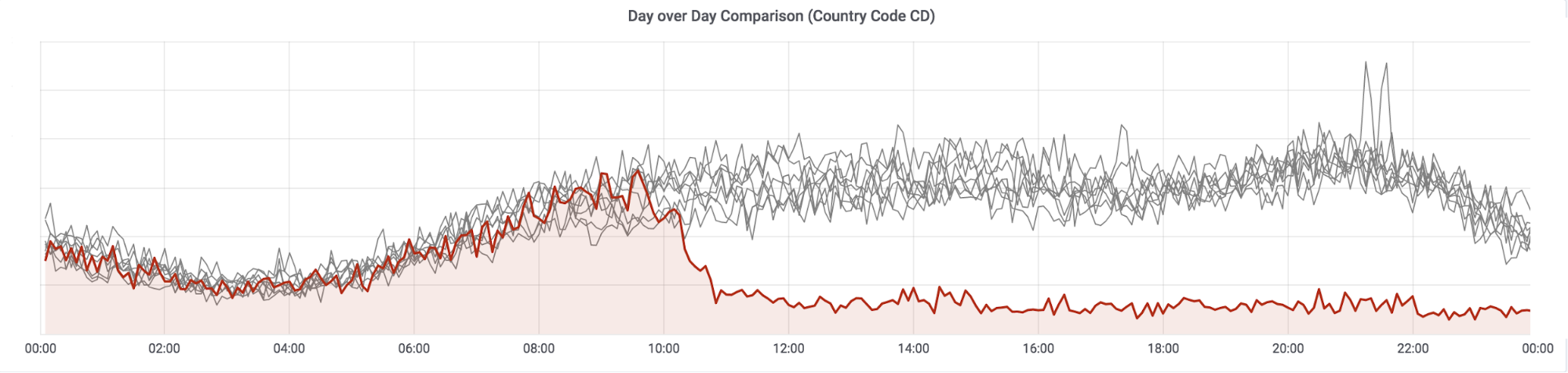
The red line is 31 December, the gray lines the previous eight days. Looking Continue reading
Improving request debugging in Cloudflare Workers
At Cloudflare, we are constantly looking into ways to improve development experience for Workers and make it the most convenient platform for writing serverless code.
As some of you might have already noticed either from our public release notes, on cloudflareworkers.com or in your Cloudflare Workers dashboard, there recently was a small but important change in the look of the inspector.
But before we go into figuring out what it is, let's take a look at our standard example on cloudflareworkers.com:
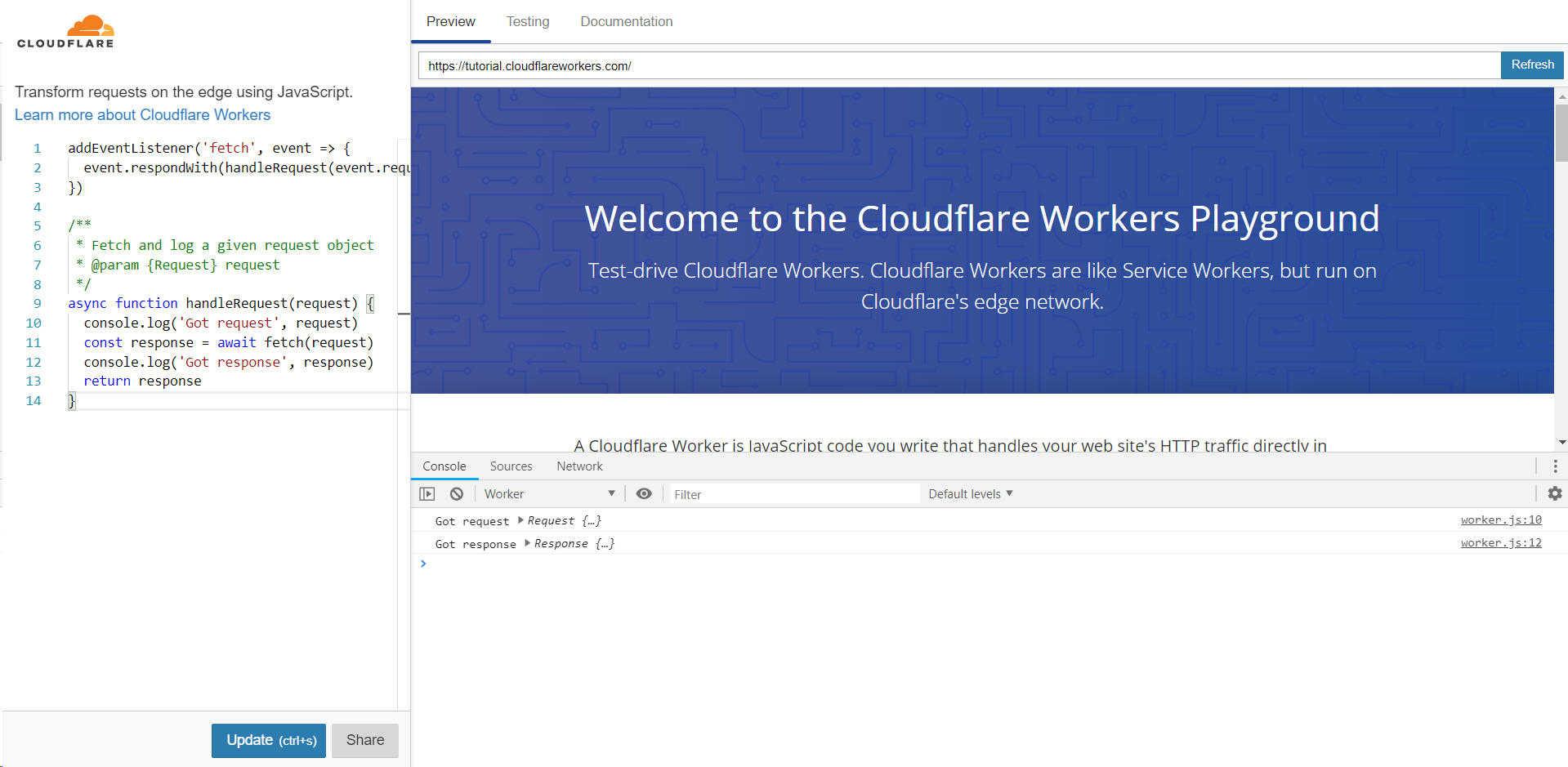
The example worker code featured here acts as a transparent proxy, while printing requests / responses to the console.
Commonly, when debugging Workers, all you could see from the client-side devtools is the interaction between your browser and the Cloudflare Worker runtime. However, like in most other server-side runtimes, the interaction between your code and the actual origin has been hidden.
This is where console.log comes in. Although not the most convenient, printing random things out is a fairly popular debugging technique.
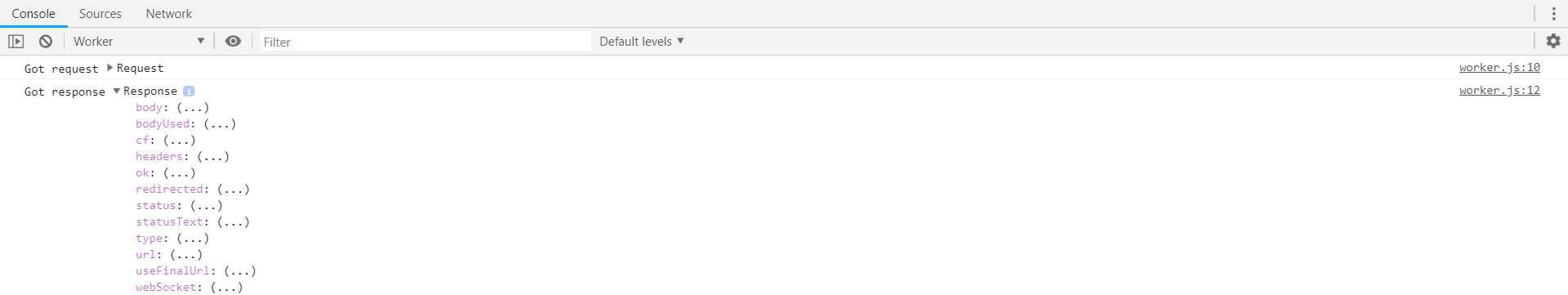
Unfortunately, its default output doesn't help much with debugging network interactions. If you try to expand either of request or response objects, all you can see is just a bunch of lazy accessors:
Happy Pink Dot SG from the Proudflare team!

Pink Dot SG is an event which takes place every June in Singapore to celebrate LGBTQIA+ pride! Cloudflare participated this year, on June 21st. We’re a little late, but wanted to share what we got up to. Pink Dot SG started in 2009, as a way for queer people and allies alike to demonstrate their belief that everyone deserves the “freedom to love.”
Proudflare at Pink Dot ‘18
Proudflare, Cloudflare's LGBTQIA+ employee resource group, finds ways to support and provide resources for the LGBTQIA+ community, both within Cloudflare and in the larger community.
Proudflare started in 2017 in our San Francisco headquarters and in 2018, the Proudflare Singapore chapter was formed. We were excited to participate in our first public-facing event and demonstrate Cloudflare’s commitment to equality and dignity for all people!
We took to the streets this year to celebrate, but more importantly demand equality for our community in Singapore. It was an exciting event, with heaps of buzz, cheer, and joy amongst the crowd! Pink Dot SG included LGBTQIA+-themed events, information tents, a concert, and onstage were 10 Declarations for Equality, a list of changes the LGBTQIA+ community and their allies are ready for and Continue reading
Concise Christmas Cryptography Challenges 2019

Last year we published some crypto challenges to keep you momentarily occupied from the festivities. This year, we're doing the same. Whether you're bored or just want to learn a bit more about the technologies that encrypt the internet, feel free to give these short cryptography quizzes a go.
We're withholding answers until the start of the new year, to give you a chance to solve them without spoilers. Before we reveal the answers; if you manage to solve them, we'll be giving the first 5 people to get the answers right some Cloudflare swag. Fill out your answers and details using this form so we know where to send it.
Have fun!
NOTE: Hints are below the questions, avoid scrolling too far if you want to avoid any spoilers.

Challenges
Client says Hello
Client says hello, as follows:
00000c07ac01784f437dbfc70800450000f2560140004006db58ac1020c843c
7f80cd1f701bbc8b2af3449b598758018102a72a700000101080a675bce16787
abd8716030100b9010000b503035c1ea569d5f64df3d8630de8bdddd1152e75f
528ae577d2436949ce8deb7108600004400ffc02cc02bc024c023c00ac009c0
08c030c02fc028c027c014c013c012009f009e006b0067003900330016009d
009c003d003c0035002f000a00af00ae008d008c008b010000480000000b
000900000663666c2e7265000a00080006001700180019000b0002010000
0d0012001004010201050106010403020305030603000500050100000000
001200000017000052305655494338795157524c656d6443436c5246574651
675430346754456c4f52564d674e434242546b51674e513d3d
[Raw puzzle without text wrap]
Time-Based One-Time Password
A user has an authenticator device to generate one time passwords for logins to their banking website. The implementation contains a fatal flaw.
At the following times, the following codes are generated (all in GMT/UTC):
- Friday, 21 December 2018 16:29:28 - Continue reading
Improving HTML Time to First Byte
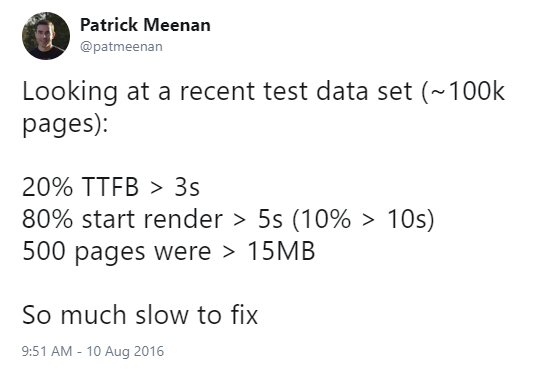
The Time to First Byte (TTFB) of a site is the time from when the user starts navigating until the HTML for the page they requested starts to arrive. A slow TTFB has been the bane of my existence for more than the ten years I have been running WebPageTest.
Looking at a recent test data set (~100k pages):
— Patrick Meenan (@patmeenan) August 10, 2016
20% TTFB > 3s
80% start render > 5s (10% > 10s)
500 pages were > 15MB
So much slow to fix
There is a reason why TTFB appears as one of the few “grades” that WebPageTest scores a site on and, specifically, why it is the first grade in the list.
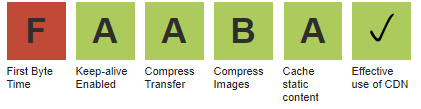
If the first byte is slow, EVERY other metric will also be slow. Improving it is one of the few cases where you can predict what the impact will be on every other measurement. Every millisecond improvement in the TTFB translates directly into a millisecond of savings in every other measurement (i.e. first paint will be 500ms faster if TTFB improves by 500ms). That said, a fast ttfb doesn't guarantee a fast experience but a slow ttfb does guarantee a slow Continue reading
The Internet Mince Pie Data Base: 2018 Edition

In December 2017 we unveiled the true potential of Cloudflare’s scale: to find the best commercially available mince pie and let the world know about it. In 2018 we’ve all been extremely busy helping Cloudflare & our customers and therefore we left it very late this year. Uncomfortably late.
If you want to know the best mince pie to buy in 2018 right now, skip straight to the bottom of this post where we reveal the winner. If you want to understand more about what makes a mince pie great and how we can learn this at Cloudflare’s scale - read on.
How do you review 42 varieties of mince pie in an hour?
With a very short amount of time to get this research out to a discerning and demanding public, we engaged the entire Cloudflare London team to help. Team members diligently went out and purchased mince pies from all over the South East of England for everyone to taste.

On Monday the team assembled for a “Mince Pie Jam”, where we would taste & consistently review each pie:

A quick refresher - what is a mince pie?

As we can see from even the most cursory Internet Continue reading
Athenian Project Turns One: Are Election Websites Safer?


One year ago, Cloudflare launched the Athenian Project to provide free Enterprise-level service to election and voter registration websites run by state and local governments in the United States. Through this project, we have helped over 100 entities in 24 states protect their websites from denial of service attacks, SQL injection, and other malicious efforts aimed at undermining the integrity of their elections. With the end of the year approaching, and the November 6th US midterm elections behind us, we wanted to look back at the project and what we have learned as we move towards 2020.
US Midterm Election Day
The morning of November 6th was full of anticipation for the Athenian Project team with the policy, engineering and support teams ready as polls opened in the East. Early in the day, we were notified by our partner at the CDT that some elections websites were experiencing downtime. Mobilizing to help these groups, we reached out to the website administrators and, through the course of the day, on-boarded over 30 new county-level websites to the Athenian Project and helped them manage the unpredictably large amounts of legitimate traffic.
This last-minute effort would not have been possible without the help Continue reading
Encrypting DNS end-to-end
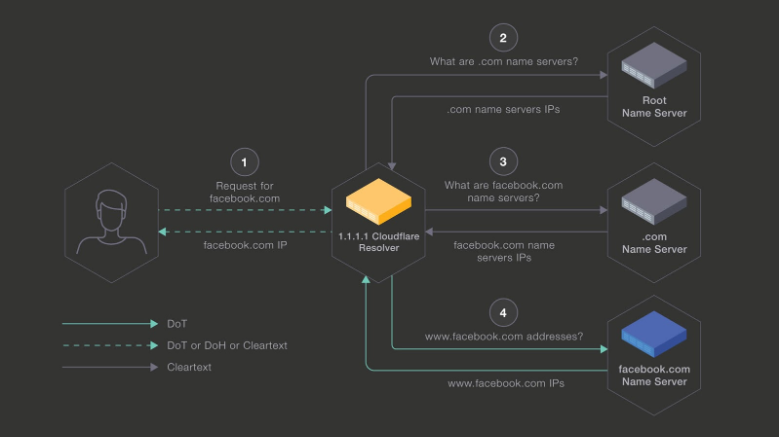
Over the past few months, we have been running a pilot with Facebook to test the feasibility of securing the connection between 1.1.1.1 and Facebook’s authoritative name servers. Traditionally, the connection between a resolver and an authoritative name server is unencrypted i.e. over UDP.
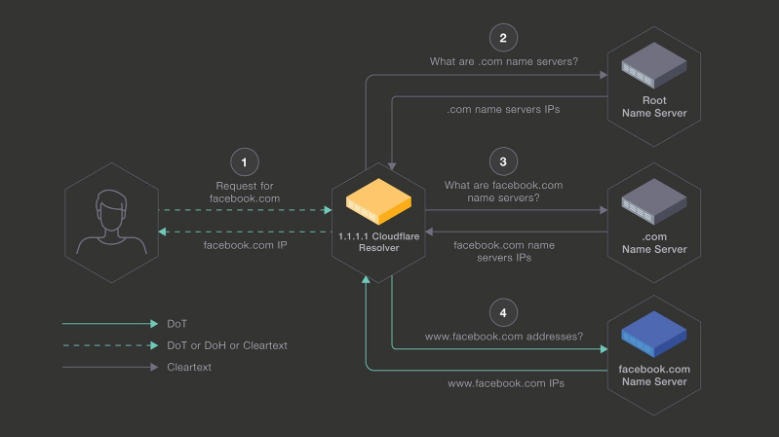
In this pilot we tested how an encrypted connection using TLS impacts the end-to-end latency between 1.1.1.1 and Facebook’s authoritative name servers. Even though the initial connection adds some latency, the overhead is amortized over many queries. The resulting DNS latency between 1.1.1.1 and Facebook’s authoritative name servers is on par with the average UDP connections.
To learn more about how the pilot went, and to see more detailed results, check out the complete breakdown over on Code, Facebook's Engineering blog.
Firewall Rules – Priority and Ordering


Firewall Rules are one of the best security features we released this year and have been an overwhelming success. Customers have been using Firewall Rules to solve interesting security related use cases; for example, advanced hotlink protection, restricting access to embargoed content (e.g. productId=1234), locking down sensitive API endpoints, and more.
One of the biggest pieces of feedback from the Cloudflare community, Twitter, and via customer support, has been around the order in which rules are actioned. By default, Firewall Rules have a default precedence, based on the actions set on the rule:

If two or more rules match a request, but have different actions, the above precedence will take effect. However, what happens if you've got a bad actor who needs to be blocked from your API, and you have other specific allow or challenge rules already created for their originating ASN or a perhaps one of your URLs? Once a Firewall Rule is matched, it will not continue processing other rule, unless you are using the Log action. Without a method of overriding the default precedence, you cannot easily achieve what's needed.
Today, we’re launching the ability for customers to change the ordering of their rules. Continue reading
Ten new data centers: Cloudflare expands global network to 165 cities


Cloudflare is excited to announce the addition of ten new data centers across the United States, Bahrain, Russia, Vietnam, Pakistan and France (Réunion). We're delighted to help improve the performance and security of over 12 million domains across these diverse countries that collectively represent about half a billion Internet users.
Our global network now spans 165 cities, with 46 new cities added just this year, and several dozen additional locations being actively worked on.
United States of America

Our expansion begins in the United States, where Cloudflare's 36th and 37th data centers in the nation serve Charlotte (North Carolina) and Columbus (Ohio) respectively. They are promising markets for interconnection, and join our existing deployments in Ashburn, Atlanta, Boston, Chicago, Dallas, Denver, Detroit, Houston, Indianapolis, Jacksonville, Kansas City, Las Vegas, Los Angeles, McAllen, Memphis, Miami, Minneapolis, Montgomery, Nashville, Newark, Norfolk, Omaha, Philadelphia, Portland, Richmond, Sacramento, Salt Lake City, San Diego, San Jose, Seattle, St. Louis, Tallahassee, and Tampa.
Bahrain

Cloudflare's Manama (Bahrain) data center, our 158th globally, further expands our Middle East coverage. A growing hub for cloud computing, including public sector adoption (with the Kingdom's "Cloud First" policy), Bahrain is attracting talent and investment in innovative companies.
Russia

Cloudflare's new Continue reading
Banking-Grade Credential Stuffing: The Futility of Partial Password Validation


Recently when logging into one of my credit card providers, I was greeted by a familiar screen. After entering in my username, the service asked me to supply 3 random characters from my password to validate ownership of my account.

It is increasingly common knowledge in the InfoSec community that this practice is the antithesis of, what we now understand to be, secure password management.
For starters; sites prompting you for Partial Password Validation cannot store your passwords securely using algorithms like BCrypt or Argon2. If the service provider is ever breached, such plain-text passwords can be used to login to other sites where the account holder uses the same password (known as a Credential Stuffing attack).
Increased difficulty using long, randomly-generated passwords from Password Managers, leads to users favouring their memory over securely generated unique passwords. Those using Password Managers must extract their password from their vault, paste it somewhere else and then calculate the correct characters to put in. With this increased complexity, it further incentivises users to (re-)use simple passwords they can remember and count off on their fingers (and likely repeatedly use on other sites).
This is not to distinct thinking that originally bought us complex Continue reading
Cloudworker – A local Cloudflare Worker Runner

This is a guest post by Hank Jacobs, who is the Lead Software Engineer for Platform Services & Tools at Dollar Shave Club. This post originally appeared on the DSC Engineering blog.

At Dollar Shave Club, we continuously look for ways to improve how we build and ship code. Improving the time it takes for engineers to ship code is key. Providing engineers with a development environment that closely mirrors production really helps.
Earlier this year, we began evaluating Cloudflare Workers as a replacement for our legacy edge routing and caching layers. Cloudflare Workers brings the power of Javascript to Cloudflare’s Edge. Developers can write and deploy Javacript that gets executed for every HTTP request that passes through Cloudflare. This capability excited us but a critical thing was missing — a way to run Worker code locally. We couldn’t find a suitable solution, so we started to build our own. Luckily, Workers uses the open Service Workers API so we had documentation to consult. Within a few weeks, Cloudworker was born.

Cloudworker
Cloudworker is a local Cloudflare Worker runtime. With it, you can run Cloudflare Worker scripts locally (or anywhere you can run a Docker image). Our primary goal with Continue reading
Real World Serverless: Serverless Use Cases and Best Practices

Cloudflare Workers has had a very busy 2018. Throughout the year, Workers moved from beta to general availability, continued to expand its footprint as Cloudflare grew to 155 locations, and added new features and services to help developers create increasingly advanced applications.
To cap off 2018 we decided hit the road (and then head to the airport) with our Real World Serverless event series in San Francisco, Austin, London, Singapore, Sydney, and Melbourne. It was a great time sharing serverless application development insights we’ve discovered over the past year as well as demonstrating how to build applications with new services like our key value store, Cloudflare Workers KV.
Below is a recording from our Singapore Real World Serverless event. It included three talks about Serverless technology featuring Tim Obezuk, Stanley Tan, and Remy Guercio from Cloudflare. They spoke about the fundamentals of serverless technology, twelve factors of serverless application development, and achieving no ops at scale with network-based serverless.
If you’d like to join us in person to talk about serverless, we’ll be announcing 2019 event locations starting in the new year.
About the talks
Fundamentals of Serverless Technology - Tim Obezuk (0:00-13:56)
Tim explores the anatomy of Continue reading
Managing DNS Records For The People With Cloudflare Apps

DNS records are hard. Many people, even the technically competent, don’t understand more than the basics.

I'll speak for myself — as someone who always learned just enough about DNS to get it working, then immediately forgot everything until the next time it broke. It was a vicious cycle until I convinced myself to learn it in depth. Meanwhile, non-technical folks wisely avoid meddling in such dangerous affairs all together.
Surely, there must be a better way (this is a blog post after all).
Every day, thousands of Cloudflare users add DNS records to their Internet properties to configure awesome tools like G Suite, Shopify, Wordpress, Ghost, and thousands of others. A new Cloudflare Apps feature allows apps to automatically set up and manage configurable DNS records on more than 12 million registered domains on the Cloudflare network. In short, Cloudflare Apps are here to alleviate the Internet’s collective DNS woes.
Gone are the days of tribulating over whether it’s A or CNAME you should set. Gone are the days of puzzling between A and AAAA records while wondering what the heck happened to AA and AAA records? Unload your DNS dysphoria onto highly trained developers experienced at explicating these Continue reading
Traffic Acceleration with Cloudflare Mobile SDK

We’re excited to announce early access for Traffic Acceleration with Cloudflare Mobile SDK. Acceleration uses novel transport algorithms built into the SDK to accelerate apps beyond the performance they would see with TCP. Enabling Acceleration through the SDK reduces latency, increases throughput, and improves app user experiences.
A year ago, we launched Cloudflare Mobile SDK with a set of free features focused on measuring mobile app networking performance. Apps are dependent on network connectivity to deliver their app’s user experiences, but developers have limited visibility into how network connectivity is impacting app performance. Integrating the Mobile SDK allows developers to measure and improve the speed of their app’s network interactions.
How it works
Mobile applications interact with the Internet to do everything — to fetch the weather, your email, to step through a check out flow. Everything that makes a smartphone magical is powered by a service on the Internet. How quickly those network interactions happen is dictated by two things: how large the payloads are for the given request/response, and what the available link bandwidth is.
Payload size is mostly application specific: a shopping app is going to request product images and similar medium sized assets, while a stock Continue reading
How my team wrote 12 Cloudflare apps with fewer than 20 lines of code
This is a guest post by Ben Ross. Ben is a Berkeley PhD, serial entrepreneur, and Founder and CTO and POWr.io, where he spends his days helping small businesses grow online.
I like my code the same way I like my team of POWr Rangers… DRY.
And no, I don’t mean dull and unexciting! (If you haven’t heard this acronym before, DRY stands for Don’t Repeat Yourself, the single most important principle in software engineering. Because, as a mentor once told me, “when someone needs to re-write your code, at least they only need to do it once.”)
At POWr, being DRY is not just a way to write code, it’s a way of life. This is true whether you’re an Engineer, a Customer Support agent, or an Office Manager; if you find you’re repeating yourself, we want to find a way to automate that repetition away. Our employees’ time is our company’s most valuable resource. Not to mention, who wants to spend all day repeating themselves?
We call this process becoming a Scaled Employee. A Scaled Employee leverages their time and resources to make a multifold impact compared to an average employee in their Continue reading
More consistent LuaJIT performance
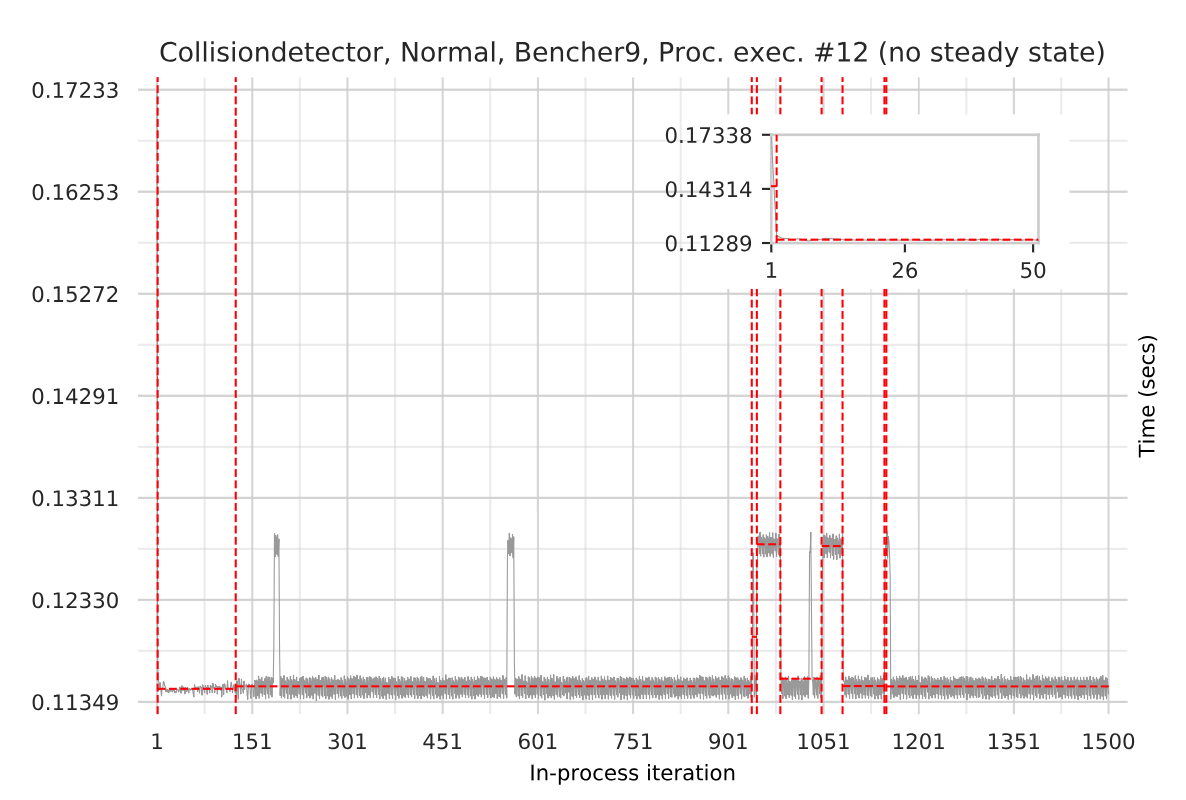
This is a guest post by Laurence Tratt, who is a programmer and Reader in Software Development in the Department of Informatics at King's College London where he leads the Software Development Team. He is also an EPSRC Fellow.
A year ago I wrote about a project that Cloudflare were funding at King's College London to help improve LuaJIT. Our twelve months is now up. How did we do?
The first thing that happened is that I was lucky to employ a LuaJIT expert, Thomas Fransham, to work on the project. His deep knowledge about LuaJIT was crucial to getting things up and running – 12 months might sound like a long time, but it soon whizzes by!
The second thing that happened was that we realised that the current state of Lua benchmarking was not good enough for anyone to reliably tell if they'd improved LuaJIT performance or not. Different Lua implementations had different benchmark suites, mostly on the small side, and not easily compared. Although it wasn't part of our original plan, we thus put a lot of effort into creating a larger benchmark suite. This sounds like a trivial job, but it isn't. Many programs make Continue reading