2,600 meters closer to the stars: Cloudflare Data Center #149 in Bogotá, Colombia


At 2625 meters (8612 feet) above sea level, Bogotá (Colombia) is one of the four highest capital cities in the world. Now, it is also home to Cloudflare's 149th data center.
This is the 29th city to be added just in March, and joins our existing Colombia datacenter in Medellín, launched four years ago.
 CC BY-SA 2.0 image by nigel_sb
CC BY-SA 2.0 image by nigel_sb
Bogotá is the third largest city in South America after São Paulo (Brazil) and Lima (Peru). Bogotanos affectionately known as Rolos are proud of their city with its rich cultural heritage, and its modern transportation systems (Ciclovias, Transmilenio) despite the heavy traffic. Whether you are visiting the world famous gold museum or savoring the mouthwatering Ajiaco soup, Bogotá has something for everyone, and visitors are always warmly received by the locals.
 CC BY-SA 2.0 image by krossbow
CC BY-SA 2.0 image by krossbow
Bogotá is our 11th deployment in the Latin America and Caribbean Region, and is located at a Tier III facility in the Bogota Free Trade Zone specially developed to attract ICT Investments. We'll continue our expansions in the Latin America and Caribbean region (and around the world!).
Come meet the Cloudflare team at the LACNIC29 Meeting in end April Continue reading
Three more US data centers! Jacksonville, Memphis and Tallahassee


Good things come in threes! Following the launch of three data centers each in the Baltics (Riga, Tallinn, Vilnius) and in the Canadian Prairies (Calgary, Saskatoon, Winnipeg), we're thrilled to announce three new data centers in the Southern United States!
Located in Jacksonville (Florida), Memphis (Tennessee), and Tallahassee (Florida), they represent the 146th, 147th and 148th cities across our growing global network, and our 40th, 41st and 42nd cities just in North America. They join existing Cloudflare facilities in the US, including other Florida / Tennessee deployments such as Miami, Tampa and Nashville. Just in March, we've added deployments in 28 new cities worldwide, which help reduce latency to millions of Internet properties using Cloudflare, while expanding our capacity to withstand new and familiar attacks.
 Photo of Jacksonville Beach by Lance Asper / Unsplash
Photo of Jacksonville Beach by Lance Asper / Unsplash
Whether you're doing the Memphis Main Street Crawl, experiencing history through a visit to Tallahassee's Mission San Luis de Apalachee, or just relaxing by the stunning beaches of Jacksonville, you'll be close to the nearest Cloudflare data center.
The Cloudflare Global Anycast Network
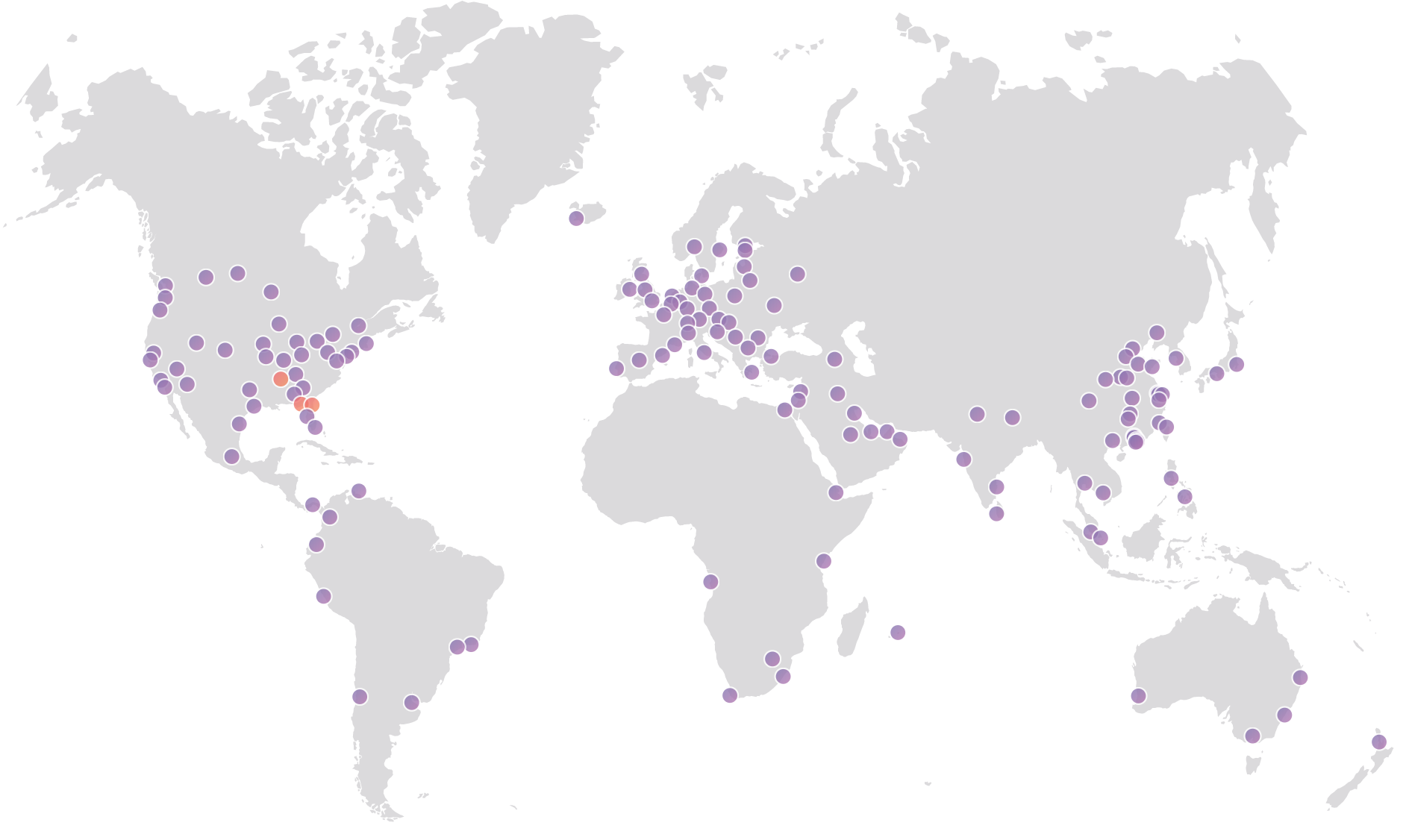
This map reflects the network as of the publish date of this blog post. For the most up to date directory Continue reading
Cloudflare Arrives in the Canadian Prairies! Welcome Calgary, Saskatoon and Winnipeg


We just turned up Calgary, Saskatoon and Winnipeg - Cloudflare’s 143rd, 144th, and 145th data centers. This brings our Canadian presence to six cities, joining Toronto, Montreal and Vancouver. I grew up just outside of Saskatoon, so I couldn’t be happier that Cloudflare’s network has expanded to the Canadian Prairies. My parents still live there and I just booked flights to go and visit them this summer. When I tell people that I grew up in Saskatchewan, most people don’t know a lot about the region, so I wanted to share some of my favorite things about the region, starting from west to east:
- Calgary was home to the 1988 Winter Olympics and is a 90 minute drive from Banff, an incredible National Park that is absolutely worth visiting. Calgary has grown quickly over the last twenty years because of all the natural resources, including oil and gas. They host a famous rodeo, Calgary Stampede, for 10 days every summer. Definitely something to add to your bucket list. With Cloudflare’s new deployment in Calgary, we’ll make the Internet even faster for visitors. Hello Calgary!
-
About 1 million people live in the province of Saskatchewan. Saskatoon is the Continue reading
Riga, Tallinn and Vilnius: Launching three new European Cloudflare data centers


Cloudflare announces the turn up of our newest data centers located in Riga (Latvia), Tallinn (Estonia) and Vilnius (Lithuania). They represent the 140th, 141st and 142nd cities across our growing global network, and our 37th, 38th, 39th cities in Europe. We are very excited to help improve the security and performance of over 7 million Internet properties across 72 countries including the Baltic states.
We will be interconnecting with local networks over multiple Internet exchanges: Baltic Internet Exchange (BALT-IX), Lithuanian Internet eXchange Point (LIXP), LITIX, Tallinn Internet Exchange (TLLIX), Tallinn Governmental Internet Exchange (RTIX), Santa Monica Internet Local Exchange (SMILE-LV), and potentially, the Latvian Internet Exchange (LIX-LV).
If you are an entrepreneur anywhere in the world selling your product in these markets, or a Baltic entrepreneur reaching a global audience, we've got your back.
Baltic Region
Photo by Siim Lukka / Unsplash
Latvia, Estonia and Lithuania join the list of other countries with shorelines along the Baltic Sea and Cloudflare data centers. That list includes Denmark, Finland, Germany, Poland, Russia and Sweden.
Of the five countries that in the drainage basin but do not border the sea, Cloudflare has deployments Continue reading
eBPF, Sockets, Hop Distance and manually writing eBPF assembly
A friend gave me an interesting task: extract IP TTL values from TCP connections established by a userspace program. This seemingly simple task quickly exploded into an epic Linux system programming hack. The result code is grossly over engineered, but boy, did we learn plenty in the process!

CC BY-SA 2.0 image by Paul Miller
Context
You may wonder why she wanted to inspect the TTL packet field (formally known as "IP Time To Live (TTL)" in IPv4, or "Hop Count" in IPv6)? The reason is simple - she wanted to ensure that the connections are routed outside of our datacenter. The "Hop Distance" - the difference between the TTL value set by the originating machine and the TTL value in the packet received at its destination - shows how many routers the packet crossed. If a packet crossed two or more routers, we know it indeed came from outside of our datacenter.
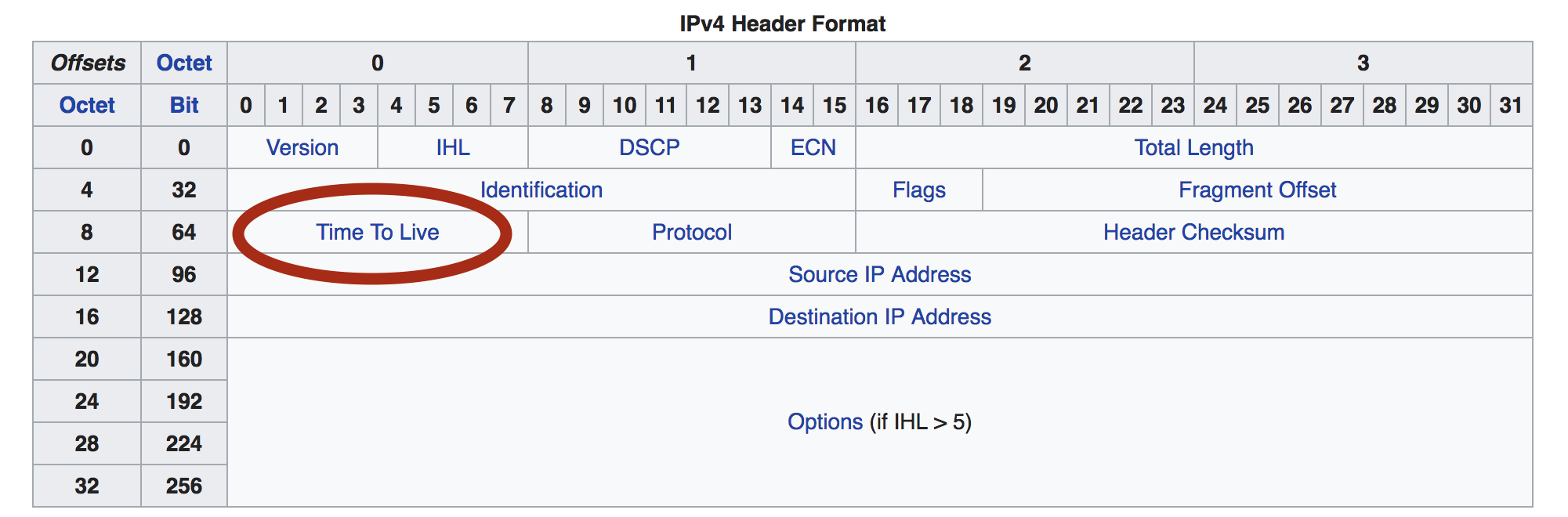
It's uncommon to look at TTL values (except for their intended purpose of mitigating routing loops by checking when the TTL reaches zero). The normal way to deal with the problem we had would be to blacklist IP ranges of our servers. But it’s not that Continue reading
Cloudflare is adding Drupal WAF Rule to Mitigate Critical Drupal Exploit
Drupal has recently announced an update to fix a critical remote code execution exploit (SA-CORE-2018-002/CVE-2018-7600). In response we have just pushed out a rule to block requests matching these exploit conditions for our Web Application Firewall (WAF). You can find this rule in the Cloudflare ruleset in your dashboard under the Drupal category with the rule ID of D0003.
Drupal Advisory: https://www.drupal.org/sa-core-2018-002
Cloudflare is adding Drupal WAF Rule to Mitigate Critical Drupal Exploit
Drupal has recently announced an update to fix a critical remote code execution exploit (SA-CORE-2018-002/CVE-2018-7600). This patch is to disallow forms and form fields from starting with the “#” character which results in remote code execution.
We have also in accordance, just pushed out a rule to block requests matching these exploit conditions for our Web Application Firewall (WAF). You can find this rule in the Cloudflare ruleset in your dashboard under the Drupal category with the rule ID of D0003.
Drupal Advisory: https://www.drupal.org/sa-core-2018-002
A Solution to Compression Oracles on the Web

This is a guest post by Blake Loring, a PhD student at Royal Holloway, University of London. Blake worked at Cloudflare as an intern in the summer of 2017.
Compression is often considered an essential tool when reducing the bandwidth usage of internet services. The impact that the use of such compression schemes can have on security, however, has often been overlooked. The recently detailed CRIME, BREACH, TIME and HEIST attacks on TLS have shown that if an attacker can make requests on behalf of a user then secret information can be extracted from encrypted messages using only the length of the response. Deciding whether an element of a web-page should be secret often depends on the content of the page, however there are some common elements of web-pages which should always remain secret such as Cross-Site Request Forgery (CSRF) tokens. Such tokens are used to ensure that malicious webpages cannot forge requests from a user by enforcing that any request must contain a secret token included in a previous response.
I worked at Cloudflare last summer to investigate possible solutions to this problem. The result is a project called cf-nocompress. The Continue reading
London & Barcelona developers, we want to meet you this week


Are you based in London or Barcelona? Drop by the Cloudflare London office to meet Kenton Varda, lead architect of Cloudflare Workers, front end developers Marta Bondyra and David Sancho from Typeform, or drop by the Typeform office in Barcelona to hear from Jason Harmon, Typeform’s Chief Platform Officer. My Developer Relations teammates and I are visiting these cities over the next two weeks. We’d love to meet you and invite you to the three events we’re hosting.
Our first stop is the Cloudflare London office. Developers from our Cloudflare Apps partner, Typeform, are leading a talk on Tuesday, March 27th. The lead architect of Cloudflare Workers, Kenton Varda, is going to lead a follow-up talk about edge computing on Wednesday, March 28th.
Event #1: Building for a tech audience: Great dev lessons for adventurous makers
Tuesday, March 27th: 18:00-20:00
Location: Cloudflare London - 25 Lavington St, Second floor | SE1 0NZ London
Creating software from scratch, although fun, can be time consuming and expensive. Marta and David, both developers at Typeform, will tell you why their teams built tools to make the lives of developers a little easier and what they learned along the way.
A tour through Merkle Town, Cloudflare’s Certificate Transparency dashboard

For a quick primer on Certificate Transparency, please read my colleague Nick Sullivan’s post from earlier today. The discussion below expands on that post and details how Cloudflare monitors the health and performance of Certificate Transparency (CT) logs.

The success of Certificate Transparency rests on the existence of a robust ecosystem of logs and log operators. Without logs that CAs can depend on, it’s not practical for browsers to require that SSL certificates have been logged to be trusted—as Chrome plans to do on April 30. With this deadline fast approaching and others browsers likely to follow suit, it’s critical that the CT ecosystem continues to strengthen and expand with new log operators.
As we wrote about earlier today, Cloudflare recently joined this group of trusted log operators, helping strengthen this critical ecosystem. Now, we’d like to take you on a quick guide through our new publicly accessible tool that tracks the health of all trusted logs. In addition to basic uptime and response times, Merkle Town, provides statistics on the type and frequency of certificates issued, the top issuers, and the inter-dependencies CAs have on existing logs and each other. Click here to jump right into our Continue reading
Introducing Certificate Transparency and Nimbus


Certificate Transparency (CT) is an ambitious project to help improve security online by bringing accountability to the system that protects HTTPS. Cloudflare is announcing support for this project by introducing two new public-good services:
- Nimbus: A free and open certificate transparency log
- Merkle Town: A dashboard for exploring the certificate transparency ecosystem
In this blog post we’ll explain what Certificate Transparency is and how it will become a critical tool for ensuring user safety online. It’s important for website operators and certificate authorities to learn about CT as soon as possible, because participating in CT becomes mandatory in Chrome for all certificates issued after April 2018. We’ll also explain how Nimbus works and how CT uses a structure called a Merkle tree to scale to the point of supporting all trusted certificates on the Internet. For more about Merkle Town, read the [follow up post] by my colleague Patrick Donahue.
Trust and Accountability
Everything we do online requires a baseline level of trust. When you use a browser to visit your bank’s website or your favorite social media site, you expect that the server on the other side of the connection is operated by the organization indicated in Continue reading
Edinburgh: 139th Cloudflare city


Our newest data center in Edinburgh expands our current total to 139 cities globally with a Cloudflare deployment. It also brings our UK total to 3 cities, after London and Manchester.
The city
Edinburgh is the capital of Scotland, located in the Lothian region. It has been recognised as the capital since the 15th century, and is the home of the Scottish government, parliament and supreme courts. It is a city of many hills, with important landmarks such as Edinburgh Castle being built at the top of a hill.
Photo by Nicola Gadler / Unsplash
Culture
One of the most famous events held each year in Edinburgh is the Fringe Festival, which is reported to be the world's largest arts festival. Many famous comedians have made their big break at this very festival.
Building a community
The internet community in the UK is very well established, but mostly concentrated on London and Manchester, with a heavy emphasis on London. By deploying in Edinburgh we're encouraging ISPs to regionalise their traffic, away from just London. We're connected to IXScotland, and are actively seeking to peer with other connected networks, to help build the peering community.
Regional expansion
Can Continue reading
Cebu City, Philippines: Cloudflare’s 138th Data Center


Cebu City, the second most populous metro area, but oldest city in the Philippines is the home of Cloudflare’s newest Data Center.
Located centrally in the Philippines, Cebu has had a long standing tradition of trade and business activity, the word itself “Cebu” meaning trade. It’s central location brings excellent coverage to central and southern Philippines, while our existing location in Manila, serving the Manila Metro and northern Philippines.
Photo by Zany Jadraque / Unsplash
Cebu’s history covers hundreds of years, with rich local culture and international influence dating back from the first Spanish visitors to modern trade and shipping. One of the more popular dishes is Lechon.
Cebu has infamous white sand beaches, in-between making millions of websites and applications faster and more secure for the Philippine internet users, we hope our servers can get some excellent R&R on the famous beaches.
Data-driven development with Cloudflare Mobile SDK


If your app loads critical resources over the network, it's relying on your user's mobile network connection to deliver an engaging experience. Network errors occur in 3 to 12% of app sessions depending on infrastructure reliability and user geography.
How much engagement are you losing in your app to network errors? Chances are, you don't know.
We didn't either, until we built a free tool that helps Android and iOS developers visualize and understand their mobile app's network utilization.
Introducing Cloudflare Mobile SDK
Our SDK helps you identify slowdowns caused by balky or too frequent network calls, so you can focus your development effort on optimizing the lowest-hanging fruit.
Modern app developers already heavily instrument their apps to identify UX impacting events: they measure and collect launch time, session length, crash rates, conversion events, and lots more, using a multitude of different metrics packages and services.
Web developers look at similar data. They also pay tons of attention to their resource waterfall, mapping their critical rendering path, and understanding which resource loads are synchronous, which are not, and which block rendering. JavaScript even exposes an API to collect waterfalls in the browser programmatically.
It's time to bring the same visibility Continue reading
Cloudflare Global Network Spans 137 Cities: Launching Durban and Port Louis Data Centers


Our newest data centers in Durban (South Africa) and Port Louis (Mauritius) expand the Cloudflare network to 137 cities globally. We are delighted to reach this special milestone, and even more excited to help improve the performance and security of over 7 million Internet properties (and growing!) across 69 countries.
Just in March, so far, we've launched new data centers across Beirut, Phnom Penh, Kathmandu, Istanbul, Reykjavík, Riyadh, Macau, Baghdad, Houston, Indianapolis, Montgomery, Pittsburgh, Sacramento, Mexico City and Tel Aviv!
Growing Africa network
Just three years (and about 100 cities ago!), we launched our very first Africa deployment in Johannesburg (South Africa). It was an exciting day for members of our team to facilitate an especially substantial latency improvement for our customers.
Since then, we’ve turned up additional deployments in Cairo (Egypt), Cape Town (South Africa), Djibouti (Djibouti), Luanda (Angola), and Mombasa (Kenya).
Durban is our third deployment in South Africa, where mobile adoption continues to drive traffic growth amongst 20 million Internet users. Other countries with three (or more) Cloudflare data centers are Australia, Canada, China, Germany and United States (with two European states joining this list very Continue reading
IBM Cloud Security Beefs Up Protection for Apps, Containers
 IBM partnered with Cloudflare to offer cloud-based security services.
IBM partnered with Cloudflare to offer cloud-based security services.
Tel Aviv, Israel: Cloudflare’s 135th Data Center Now Live!


Our newest data center is now live in Tel Aviv, Israel! This expands our global network even further to span 135 cities across 68 countries.
High-Tech in Israel
Although Israel will only be turning 70 this year, it has a history so rich we’ll leave it to the textbooks. Despite its small size, and young age, Israel is home to one of the largest tech scenes, often referred to as Start-up Nation.
Haifa’s Matam technology park houses a few tech giants’ offices including Intel, Apple, Elbit, Google, IBM, Microsoft, Yahoo, Philips and more. Meanwhile, Tel Aviv serves a true hipster capital, with a high concentration of great coffee shops to serve its many startup employees and founders.
Some brag-worthy Israeli inventions include flash drives, Waze and cherry tomatoes. This is due to Israel’s excellent education. Israel is home of the top universities in the world, bringing Israel to be one of the top five nations in scientific publication per capita output. Israel also has one of the highest PhD and MD degrees per capita, and among of the highest nobel laureates per capita as well. Israeli mothers, your nagging has paid off.
CC BY-SA 4.0 image by Rita Kozlov Continue reading
Mexico City, Mexico: Cloudflare Data Center #134


¡Mexicanos! ¡Viva México! ¡Viva México! ¡Viva México! No, no es el 16 de septiembre (Día de la Independencia de México). Sin embargo aquí en Cloudflare celebramos la introducción de nuestro Datacenter #134 en la Ciudad De México. Este Datacenter marca nuestra entrada en la nación Azteca. Anteriormente el tráfico de México era servido desde algunos de nuestros otros Datacenters (principalmente McAllen, TX, Dallas, TX y Los Angeles, CA).
Mexicans! Long Live Mexico! Long Live Mexico! Long Live Mexico! No, its not the 16th of September (Mexico Independence Day). However at Cloudflare we are proud to introduce our Datacenter #134 located in Mexico City Mexico. This data center marks our entrance into the Aztec Nation. Prior to this, traffic to Mexico was served from some of our other datacenters (Primarily Mcallen, TX, Dallas, TX and Los Angeles, CA).
El área metropolitana de México cuenta con mas de 21 millones de habitantes quienes desde hoy podrán difrutar más rápido acesso a más de 7 millones de Sitios y aplicaciones en Internet servidos por Cloudflare. Este sera nuestro décimo centro de datos en la region de América Latina y El Caribe.
The Mexico City Metropolitan Areas have Continue reading
Five new Cloudflare data centers across the United States
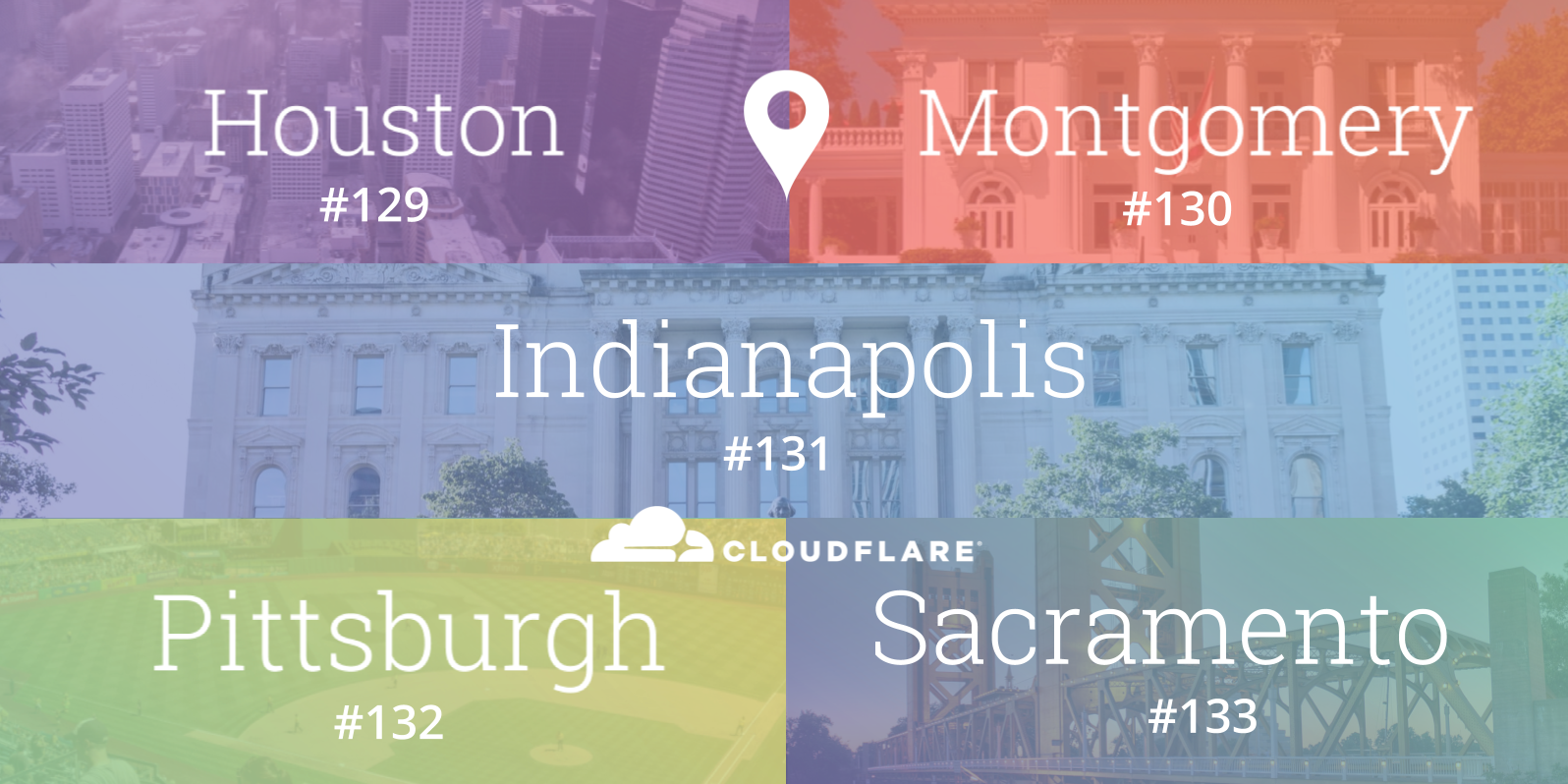
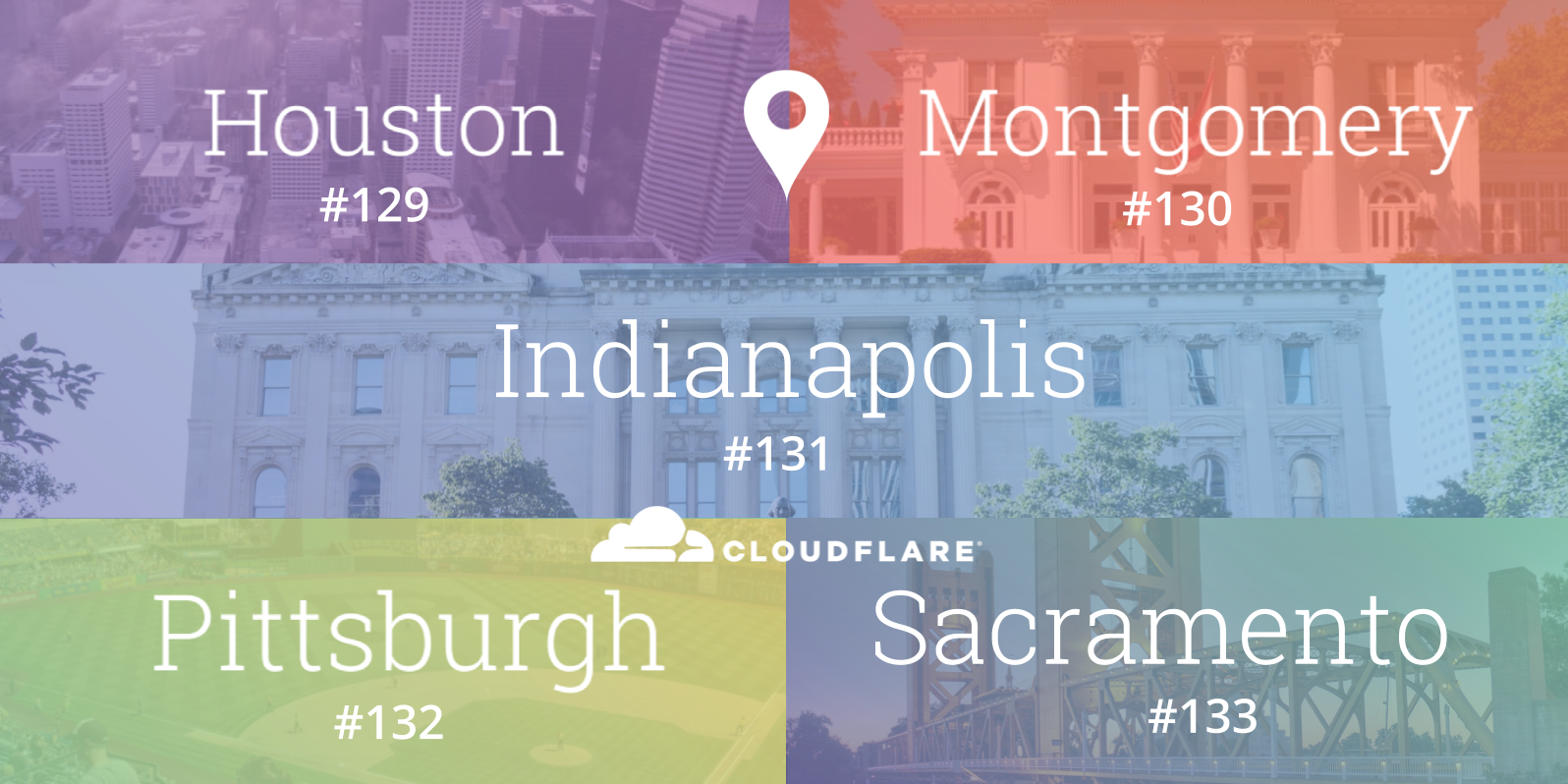
When Cloudflare launched, three of the original five cities in our network - Chicago, Ashburn and San Jose - were located in the United States. Since then, we have grown the breadth of the global network considerably to span 66 countries, and even added expanded the US footprint to twenty five locations. Even as a highly international business, the United States continues to be home to a number of our customers and the majority of Cloudflare employees.
Today, we expand our network in the United States even further by adding five new locations: Houston (Texas), Indianapolis (Indiana), Montgomery (Alabama), Pittsburgh (Pennsylvania) and Sacramento (California) as our 129th, 130th, 131st, 132nd and 133rd data centers respectively. They represent states that collectively span nearly 100 million people. In North America alone, the Cloudflare network now spans 37 cities, including thirty in the US.
In each of these new locations, we connect with at least one major local Internet service provider and also openly peer using at least one major Internet exchange. We are participants at CyrusOne IX Houston, Midwest IX Indianapolis, Montgomery IX, Pittsburgh IX, and the upcoming Sacramento IX.
These deployments improves performance, security and reliability Continue reading
Baghdad, Iraq: Cloudflare’s 128th Data Center


Cloudflare's newest data center is located in Baghdad, Iraq, in the region often known as the cradle of civilization. This expands our growing Middle East presence, while serving as our 45th data center in Asia, and 128th data center globally.
Even while accelerating over 7 million Internet properties, this deployment helps our effort to be closer to every Internet user. Previous, ISPs such as Earthlink were served from our Frankfurt data center. Nearly 40 million people live in Iraq.
Rich Cuisine
One of the world's largest producers of the sweet date palm, Iraq's cuisine dates back over 10,000 years and includes favorites such as,
- Kleicha: Date-filled cookies flavored with cardamom, saffron and rose water
- Mezza: a selection of appetizers to begin the meal
- Iraqi Dolma: stuffed vegetables with a tangy sauce
- Iraqi Biryani: cooked rice with spices, beans, grilled nuts and meat / vegetables
- Masgouf: whole baked fish marinated in oil, salt, pepper, turmeric and tamarind
New data centers
Baghdad is the first of eight deployments joining the Cloudflare global network just this week. Stay tuned!
The Cloudflare Global Anycast Network
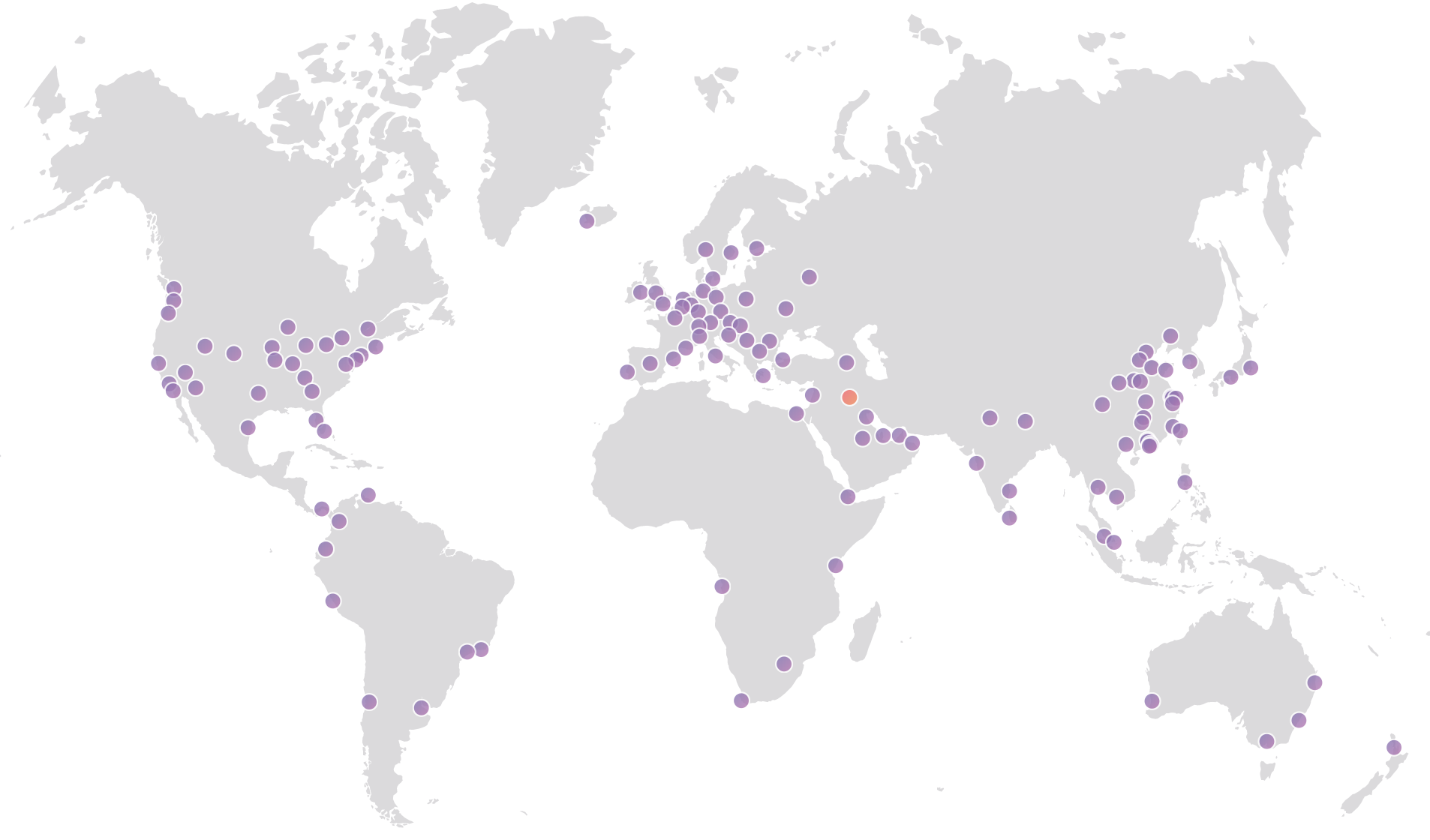
This map reflects the network as of the publish date of this blog Continue reading





