Towards a global framework for cross-border data flows and privacy protection


As our societies and economies rely more and more on digital technologies, there is an increased need to share and transfer data, including personal data, over the Internet. Cross-border data flows have become essential to international trade and global economic development. In fact, the digital transformation of the global economy could never have happened as it did without the open and global architecture of the Internet and the ability for data to transcend national borders. As we described in our blog post yesterday, data localization doesn’t necessarily improve data privacy. Actually, there can be real benefits to data security and - by extension - privacy if we are able to transfer data across borders. So with Data Privacy Day coming up tomorrow, we wanted to take this opportunity to drill down into the current environment for the transfer of personal data from the EU to the US, which is governed by the EU’s privacy regulation (GDPR). Looking to the future, we will make the case for a more stable, global cross-border data transfer framework, which will be critical for an open, more secure and more private Internet.
The privacy challenge to cross-border data flows
In the last decade, we have Continue reading
Navigating the changing data localization landscape with Cloudflare’s Data Localization Suite

This post is also available in Português.

At Cloudflare, we believe that deploying effective cybersecurity measures is the best way to protect the privacy of personal information and can be more effective than making sure that information stays within a particular jurisdiction. Yet, we hear from customers in Europe, India, Australia, Japan, and many other regions that, as part of their privacy programs, they need solutions to localize data in order to meet their regulatory obligations.
So as we think about Data Privacy Day, which is coming up on January 28, we are in the interesting position of disagreeing with those who believe that data localization is a proxy for better data privacy, but of also wanting to support our customers who have to comply with certain regulations.
For this reason, we introduced our Data Localization Suite (DLS) in 2020 to help customers navigate a data protection landscape that focuses more and more on data localization. With the DLS, customers can use Cloudflare’s powerful global network and security measures to protect their businesses, while keeping the data we process on their behalf local. Since its launch, we’ve had many customers adopt the Data Localization Suite. In this blog post we Continue reading
Investing in security to protect data privacy


If you’ve made it to 2023 without ever receiving a notice that your personal information was compromised in a security breach, consider yourself lucky. In a best case scenario, bad actors only got your email address and name – information that won’t cause you a huge amount of harm. Or in a worst-case scenario, maybe your profile on a dating app was breached and intimate details of your personal life were exposed publicly, with life-changing impacts. But there are also more hidden, insidious ways that your personal data can be exploited. For example, most of us use an Internet Service Provider (ISP) to connect to the Internet. Some of those ISPs are collecting information about your Internet viewing habits, your search histories, your location, etc. – all of which can impact the privacy of your personal information as you are targeted with ads based on your online habits.
You also probably haven’t made it to 2023 without hearing at least something about Internet privacy laws around the globe. In some jurisdictions, lawmakers are driven by a recognition that the right to privacy is a fundamental human right. In other locations, lawmakers are passing laws to address the harms their citizens Continue reading
Armed to Boot: an enhancement to Arm’s Secure Boot chain
Over the last few years, there has been a rise in the number of attacks that affect how a computer boots. Most modern computers use a specification called Unified Extensible Firmware Interface (UEFI) that defines a software interface between an operating system (e.g. Windows) and platform firmware (e.g. disk drives, video cards). There are security mechanisms built into UEFI that ensure that platform firmware can be cryptographically validated and boot securely through an application called a bootloader. This firmware is stored in non-volatile SPI flash memory on the motherboard, so it persists on the system even if the operating system is reinstalled and drives are replaced.
This creates a ‘trust anchor’ used to validate each stage of the boot process, but, unfortunately, this trust anchor is also a target for attack. In these UEFI attacks, malicious actions are loaded onto a compromised device early in the boot process. This means that malware can change configuration data, establish persistence by ‘implanting’ itself, and can bypass security measures that are only loaded at the operating system stage. So, while UEFI-anchored secure boot protects the bootloader from bootloader attacks, it does not protect the UEFI firmware itself.
Cloudflare Incident on January 24th, 2023


Several Cloudflare services became unavailable for 121 minutes on January 24th, 2023 due to an error releasing code that manages service tokens. The incident degraded a wide range of Cloudflare products including aspects of our Workers platform, our Zero Trust solution, and control plane functions in our content delivery network (CDN).
Cloudflare provides a service token functionality to allow automated services to authenticate to other services. Customers can use service tokens to secure the interaction between an application running in a data center and a resource in a public cloud provider, for example. As part of the release, we intended to introduce a feature that showed administrators the time that a token was last used, giving users the ability to safely clean up unused tokens. The change inadvertently overwrote other metadata about the service tokens and rendered the tokens of impacted accounts invalid for the duration of the incident.
The reason a single release caused so much damage is because Cloudflare runs on Cloudflare. Service tokens impact the ability for accounts to authenticate, and two of the impacted accounts power multiple Cloudflare services. When these accounts’ service tokens were overwritten, the services that run on these accounts began to experience Continue reading
Intelligent, automatic restarts for unhealthy Kafka consumers


At Cloudflare, we take steps to ensure we are resilient against failure at all levels of our infrastructure. This includes Kafka, which we use for critical workflows such as sending time-sensitive emails and alerts.
We learned a lot about keeping our applications that leverage Kafka healthy, so they can always be operational. Application health checks are notoriously hard to implement: What determines an application as healthy? How can we keep services operational at all times?
These can be implemented in many ways. We’ll talk about an approach that allows us to considerably reduce incidents with unhealthy applications while requiring less manual intervention.
Kafka at Cloudflare
Cloudflare is a big adopter of Kafka. We use Kafka as a way to decouple services due to its asynchronous nature and reliability. It allows different teams to work effectively without creating dependencies on one another. You can also read more about how other teams at Cloudflare use Kafka in this post.
Kafka is used to send and receive messages. Messages represent some kind of event like a credit card payment or details of a new user created in your platform. These messages can be represented in multiple ways: JSON, Protobuf, Avro and so on.
Internet disruptions overview for Q4 2022
Cloudflare operates in more than 250 cities in over 100 countries, where we interconnect with over 10,000 network providers in order to provide a broad range of services to millions of customers. The breadth of both our network and our customer base provides us with a unique perspective on Internet resilience, enabling us to observe the impact of Internet disruptions.
While Internet disruptions are never convenient, online interest in the 2022 World Cup in mid-November and the growth in online holiday shopping in many areas during November and December meant that connectivity issues could be particularly disruptive. Having said that, the fourth quarter appeared to be a bit quieter from an Internet disruptions perspective, although Iran and Ukraine continued to be hotspots, as we discuss below.
Government directed
Multi-hour Internet shutdowns are frequently used by authoritarian governments in response to widespread protests as a means of limiting communications among protestors, as well preventing protestors from sharing information and video with the outside world. During the fourth quarter Cuba and Sudan again implemented such shutdowns, while Iran continued the series of “Internet curfews” across mobile networks it started in mid-September, in addition to implementing several other regional Internet shutdowns.
Cuba
Introducing Waiting Room Bypass Rules


Leveraging the power and versatility of Cloudflare's Ruleset Engine, Waiting Room now offers customers more fine-tuned control over their waiting room traffic. Queue only the traffic you want to with Waiting Room Bypass Rules, now available to all Enterprise customers with an Advanced Purchase of Waiting Room.
Customers depend on Waiting Room for always-on protection from unexpected and overwhelming traffic surges that would otherwise bring their site down. Waiting Room places excess users in a fully customizable virtual waiting room, admitting new visitors dynamically as spots become available on a customer’s site. Instead of throwing error pages or delivering poorly-performing site pages, Waiting Room empowers customers to take control of their end-user experience during unmanageable traffic surges.
Additionally, customers use Waiting Room Event Scheduling to manage user flow and ensure reliable site performance before, during, and after online events such as product restocks, seasonal sales, and ticket sales. With Event Scheduling, customers schedule changes to their waiting rooms' settings and custom queuing page ahead of time, with options to pre-queue early arrivers and offload event traffic from their origins after the event has concluded.
As part of Continue reading
Three new winners of Project Jengo, and more defeats for the patent troll


Project Jengo is a Cloudflare effort to fight back against patent trolls by flipping the incentive structure that has encouraged the growth of patent trolls who extract settlements out of companies using frivolous lawsuits. We do this by asking the public to identify prior art that can invalidate any of the patents that a troll holds – not just the ones that are asserted against Cloudflare.
Since we launched Project Jengo over five years ago, we’ve given out over $135,000 to individuals who helped us find prior art to invalidate patents owned by patent trolls. By invalidating those patents – many of which are so blatantly marginal or broad that they never should have been granted in the first place – we hope to decrease the amount of harassment and frivolous lawsuits that patent trolls bring against innovative technology companies.
Today, we’re excited to announce three new Project Jengo winners. These individuals have helped us push forward our effort to take down patent trolls, and continue to fight trolling in favor of innovation.
The patent troll
The current case involves a patent troll called Sable Networks who asserted four patents that generally describe a flow-based router or a mechanism Continue reading
A debugging story: corrupt packets in AF_XDP; a kernel bug or user error?

panic: Invalid TCP packet: Truncated

A few months ago we started getting a handful of crash reports for flowtrackd, our Advanced TCP Protection system that runs on our global network. The provided stack traces indicated that the panics occurred while parsing a TCP packet that was truncated.
What was most interesting wasn’t that we failed to parse the packet. It isn’t rare that we receive malformed packets from the Internet that are (deliberately or not) truncated. Those packets will be caught the first time we parse them and won’t make it to the latter processing stages. However, in our case, the panic occurred the second time we parsed the packet, indicating it had been truncated after we received it and successfully parsed it the first time. Both parse calls were made from a single green thread and referenced the same packet buffer in memory, and we made no attempts to mutate the packet in between.
It can be easy to dread discovering a bug like this. Is there a race condition? Is there memory corruption? Is this a kernel bug? A compiler bug? Our plan to get to the root cause of this potentially complex issue was to identify symptom(s) Continue reading
Cloud CNI privately connects your clouds to Cloudflare

This post is also available in 简体中文, 日本語 and Español.

For CIOs, networking is a hard process that is often made harder. Corporate networks have so many things that need to be connected and each one of them needs to be connected differently: user devices need managed connectivity through a Secure Web Gateway, offices need to be connected using the public Internet or dedicated connectivity, data centers need to be managed with their own private or public connectivity, and then you have to manage cloud connectivity on top of it all! It can be exasperating to manage connectivity for all these different scenarios and all their privacy and compliance requirements when all you want to do is enable your users to access their resources privately, securely, and in a non-intrusive manner.
Cloudflare helps simplify your connectivity story with Cloudflare One. Today, we’re excited to announce that we support direct cloud interconnection with our Cloudflare Network Interconnect, allowing Cloudflare to be your one-stop shop for all your interconnection needs.
Customers using IBM Cloud, Google Cloud, Azure, Oracle Cloud Infrastructure, and Amazon Web Services can now open direct connections from their private cloud instances into Cloudflare. In this blog, we’re going Continue reading
CIO Week 2023 recap

This post is also available in 日本語, 简体中文, and Español.

In our Welcome to CIO Week 2023 post, we talked about wanting to start the year by celebrating the work Chief Information Officers do to keep their organizations safe and productive.
Over the past week, you learned about announcements addressing all facets of your technology stack – including new services, betas, strategic partnerships, third party integrations, and more. This recap blog summarizes each announcement and labels what capability is generally available (GA), in beta, or on our roadmap.
We delivered on critical capabilities requested by our customers – such as even more comprehensive phishing protection and deeper integrations with the Microsoft ecosystem. Looking ahead, we also described our roadmap for emerging technology categories like Digital Experience Monitoring and our vision to make it exceedingly simple to route traffic from any source to any destination through Cloudflare’s network.
Everything we launched is designed to help CIOs accelerate their pursuit of digital transformation. In this blog, we organized our announcement summaries based on the three feelings we want CIOs to have when they consider partnering with Cloudflare:
- CIOs now have a simpler roadmap to Zero Trust and SASE: We announced Continue reading
CIO Week 2023の要約


CIO Week 2023へようこその記事で、最高情報責任者が組織の安全性と生産性を維持するために行っている仕事を称えることで、1年をスタートさせたいという話をしました。
この一週間で、新サービス、ベータ版、戦略的パートナーシップ、サードパーティとの統合など、テクノロジースタックのあらゆる側面に関わる発表をご覧いただきました。この要約のブログでは、各発表を要約し、一般公開(GA)、ベータ版にある機能、またはロードマップ上に記載されている機能をラベル付けしています。
私たちは、さらに包括的なフィッシング対策機能やMicrosoftのエコシステムとのより深い統合機能など、お客様からご要望いただいた重要な機能を提供しました。今後については、Digital Experience Monitoringのような新しい技術カテゴリーのロードマップや、Cloudflareのネットワークを通じて任意のソースから任意の宛先へのトラフィックのルーティングを極めて簡単なものにするという私たちのビジョンについても説明しました。
私たちが立ち上げたものはすべて、CIOの方々へDXへの取り組みを加速していただくために設計されたものです。本ブログでは、CIOの方々がCloudflareとの提携を検討する際に抱いてほしい3つの感情を軸に、発表内容を整理しました。
- CIOの皆様によるZero TrustとSASEへのロードマップを策定がより簡単に:組織にZero Trustセキュリティベストプラクティスを採用し、Secure Access Service Edge(SASE)といった意欲的なアーキテクチャに移行しやすくする新機能と緊密な統合を発表しました。
- CIOの皆様が適切なテクノロジーとチャネルパートナーを見つけることを可能に:組織が適切な専門知識にアクセスして、すでに使用しているテクノロジーを使ってITとセキュリティを自分のペースで近代化するための統合とプログラミングを発表しました。
- CIOの皆様によるマルチクラウド戦略の合理化を簡単に:多様性を極めるクラウド環境間におけるトラフィックの接続、保護、高速化の新たな方法を発表しました。
Cloudflareが開催する多くの2023年イノベーションウィークの第1弾CIO Weekをご覧いただき、ありがとうございます。私たちのイノベーションのペースについていくのは時には難しいかもしれませんが、このブログを読み、私たちの要約のウェビナーに登録していただければ幸いです!
ITとセキュリティを近代化し、組織におけるごCIOの業務をより快適にする方法についてご相談されたい方は、こちらのフォームにご記入ください。
Zero TrustとSASEへの旅をシンプルに
アクセスの保護
これらのブログ記事では、Zero Trustの達成に必要な、よりきめ細かな制御と包括的な可視化により、すべてのユーザーがあらゆるアプリケーションに迅速、簡単、かつ安全に接続することに焦点を当てています。
| ブログ | まとめ |
|---|---|
| ベータ版: デジタルエクスペリエンスモニタリングのご紹介 | Cloudflare Digital Experience Monitoringは、CIOが重要なアプリケーションやインターネットサービスが企業ネットワーク全体でどのように機能しているかを理解するためのオールインワンダッシュボードですベータ版アクセスに登録する。 |
| ベータ版: WARP-to-WARPでCloudflare上のグローバルなプライベート仮想Zero Trustネットワーク構築を実現 | WARP(Cloudflareのデバイスクライアント)を実行している組織内のデバイスは、ワンクリックでWARPを実行している他のデバイスにプライベートネットワーク経由で到達することができます。ベータ版アクセスに登録する。 |
| 一般公開: Cloudflare Accessの「ブロックされた」メッセージをトラブルシューティングする新たな方法 | CloudflareのZero TrustプラットフォームでユーザIDのトラブルシューティングと同じレベルの容易さで、接続の経緯に基づいて、「許可」、または「ブロック」の決定を調査します。 |
| ベータ版: 社内およびSaaSアプリケーション向けのワンクリックデータセキュリティ | 分離されたブラウザでアプリケーションセッションを実行してユーザーが機密データを操作する方法を制御することで、機密データを保護しましょう – たったのワンクリックです。ベータ版アクセスに登録する。 |
| 一般公開: Cloudflare Access & Gatewayに対するSCIMの対応を発表 | CloudflareのZTNA(Access)およびSWG(Gateway)サービスは、System for Cross-domain Identity Management(SCIM)プロトコルをサポートするようになったことで、管理者はシステム間でIDレコードを管理しやすくなりました。 |
| 一般公開: Cloudflare Zero Trust:1983年以来最もエキサイティングなPingのリリース | Cloudflare Zero Trustの管理者は、ICMPプロトコルを使用する使い慣れたデバッグツール(Ping、Traceroute、MTRなど)を使用して、プライベートネットワークの宛先への接続をテストすることができます。 |
脅威防御
これらのブログ記事では、組織がフィッシング、ランサムウェア、その他のインターネットの脅威からユーザーを保護するために、トラフィックをフィルタリング、検査、分離することに焦点を当てています。
| ブログ | まとめ |
|---|---|
| 一般公開: メールリンク分離:最新のフィッシング攻撃に対するセーフティネット | 「メールリンク分離」は、ユーザーがクリックしてしまう可能性のある受信箱に届いた不審なリンクに対するセーフティネットです。この保護が追加されることで、Cloudflare Area 1は、フィッシング攻撃から守る最も包括的な電子メールセキュリティソリューションとなります。 |
| 一般公開: Cloudflare Gatewayに自社による証明書を導入 | 管理者は、独自のカスタム証明書を使用して、HTTP、DNS、CASB、DLP、RBI、その他のフィルタリングポリシーを適用することができます。 |
| 一般公開: カスタムDLPプロファイルを発表 | Cloudflareのデータ喪失防止(DLP)サービスは、カスタム検出を作成する機能を提供したことで、組織はトラフィックを検査して最も機密性の高いデータを検出できるようになりました。 |
| 一般公開: マネージドサービスプロバイダー向けCloudflare Zero Trust | 米国連邦政府をはじめとする大規模なマネージドサービスプロバイダ(MSP)が、CloudflareのテナントAPIを利用して、管理する組織全体にDNSフィルタリングなどのセキュリティポリシーを適用している事例をご紹介します。 |
セキュアなSaaS環境
これらのブログ記事では、SaaSアプリケーション環境において一貫したセキュリティと可視性を維持し、特に機密データの漏洩を防止することに焦点を当てています。
| ブログ | まとめ |
|---|---|
| ロードマップ: Cloudflare CASB とDLPが連携してデータを保護する仕組み | Cloudflare Zero Trustは、CASBサービスとDLPサービス間で、管理者がSaaSアプリケーションに保存されているファイルを覗き見して、その中の機密データを特定できる機能を導入する予定です。 |
| ロードマップ: Cloudflare Area 1 とDLPが連携してメール内のデータを保護する仕組み | Cloudflareでは、Area 1 Email Securityとデータ喪失防止(DLP)の機能を組み合わせ、企業のEメールに完全なデータ保護を提供します。 |
| 一般公開: Cloudflare CASB:SalesforceとBoxのセキュリティ上の問題をスキャン | Cloudflare CASBは、SalesforceおよびBoxと統合し、ITおよびセキュリティチームがこれらのSaaS環境に潜むセキュリティリスクのスキャンを可能にします。 |
接続の高速化と保護
Iこのセクションのブログ記事では、製品の機能に加えて、組織がCloudflareを利用して実現している速度やその他の戦略的なメリットについて紹介しています。
China Express: Cloudflare partners to boost performance in China for corporate networks


Cloudflare has been helping global organizations offer their users a consistent experience all over the world. This includes mainland China, a market our global customers cannot ignore but that continues to be challenging for infrastructure teams trying to ensure performance, security and reliability for their applications and users both in and outside mainland China. We are excited to announce China Express — a new suite of capabilities and best practices in partnership with our partners China Mobile International (CMI) and CBC Tech — that help address some of these performance challenges and ensure a consistent experience for customers and employees everywhere.
Cloudflare has been providing Application Services to users in mainland China since 2015, improving performance and security using in-country data centers and caching. Today, we have a presence in 30 cities in mainland China thanks to our strategic partnership with JD Cloud. While this delivers significant performance improvements, some requests still need to go back to the origin servers which may live outside mainland China. With limited international Internet gateways and restrictive cross-border regulations, international traffic has a very high latency and packet drop rate in and out of China. This results in inconsistent cached content within China and Continue reading
Cloudflare Application Services for private networks: do more with the tools you already love


Cloudflare’s Application Services have been hard at work keeping Internet-facing websites and applications secure, fast, and reliable for over a decade. Cloudflare One provides similar security, performance, and reliability benefits for your entire corporate network. And today, we’re excited to announce new integrations that make it possible to use these services together in new ways. These integrations unlock operational and cost efficiencies for IT teams by allowing them to do more with fewer tools, and enable new use cases that are impossible without Cloudflare’s “every service everywhere” architecture.
“Just as Canva simplifies graphic design, Cloudflare simplifies performance and security. Thanks to Cloudflare, we can focus on growing our product and expanding into new markets with confidence, knowing that our platform is fast, reliable, and secure.” - Jim Tyrrell, Head of Infrastructure, Canva
Every service everywhere, now for every network
One of Cloudflare’s fundamental architectural principles has always been to treat our network like one homogeneous supercomputer. Rather than deploying services in specific locations - for example, using some of our points of presence to enforce WAF policies, others for Zero Trust controls, and others for traffic optimization - every server runs a virtually identical stack of all of Continue reading
Cloudflare Zero Trust for managed service providers
As part of CIO week, we are announcing a new integration between our DNS Filtering solution and our Partner Tenant platform that supports parent-child policy requirements for our partner ecosystem and our direct customers. Our Tenant platform, launched in 2019, has allowed Cloudflare partners to easily integrate Cloudflare solutions across millions of customer accounts. Cloudflare Gateway, introduced in 2020, has grown from protecting personal networks to Fortune 500 enterprises in just a few short years. With the integration between these two solutions, we can now help Managed Service Providers (MSPs) support large, multi-tenant deployments with parent-child policy configurations and account-level policy overrides that seamlessly protect global employees from threats online.
Why work with Managed Service Providers?
Managed Service Providers (MSPs) are a critical part of the toolkit of many CIOs. In the age of disruptive technology, hybrid work, and shifting business models, outsourcing IT and security operations can be a fundamental decision that drives strategic goals and ensures business success across organizations of all sizes. An MSP is a third-party company that remotely manages a customer's information technology (IT) infrastructure and end-user systems. MSPs promise deep technical knowledge, threat insights, and tenured expertise across a variety Continue reading
Give us a ping. (Cloudflare) One ping only.


Ping was born in 1983 when the Internet needed a simple, effective way to measure reachability and distance. In short, ping (and subsequent utilities like traceroute and MTR) provides users with a quick way to validate whether one machine can communicate with another. Fast-forward to today and these network utility tools have become ubiquitous. Not only are they now the de facto standard for troubleshooting connectivity and network performance issues, but they also improve our overall quality of life by acting as a common suite of tools almost all Internet users are comfortable employing in their day-to-day roles and responsibilities.
Making network utility tools work as expected is very important to us, especially now as more and more customers are building their private networks on Cloudflare. Over 10,000 teams now run a private network on Cloudflare. Some of these teams are among the world's largest enterprises, some are small crews, and yet others are hobbyists, but they all want to know - can I reach that?
That’s why today we’re excited to incorporate support for these utilities into our already expansive troubleshooting toolkit for Cloudflare Zero Trust. To get started, sign up to receive beta access and start using the Continue reading
Announcing SCIM support for Cloudflare Access & Gateway
Today, we're excited to announce that Cloudflare Access and Gateway now support the System for Cross-domain Identity Management (SCIM) protocol. Before we dive into what this means, let's take a step back and review what SCIM, Access, and Gateway are.
SCIM is a protocol that enables organizations to manage user identities and access to resources across multiple systems and domains. It is often used to automate the process of creating, updating, and deleting user accounts and permissions, and to keep these accounts and permissions in sync across different systems.
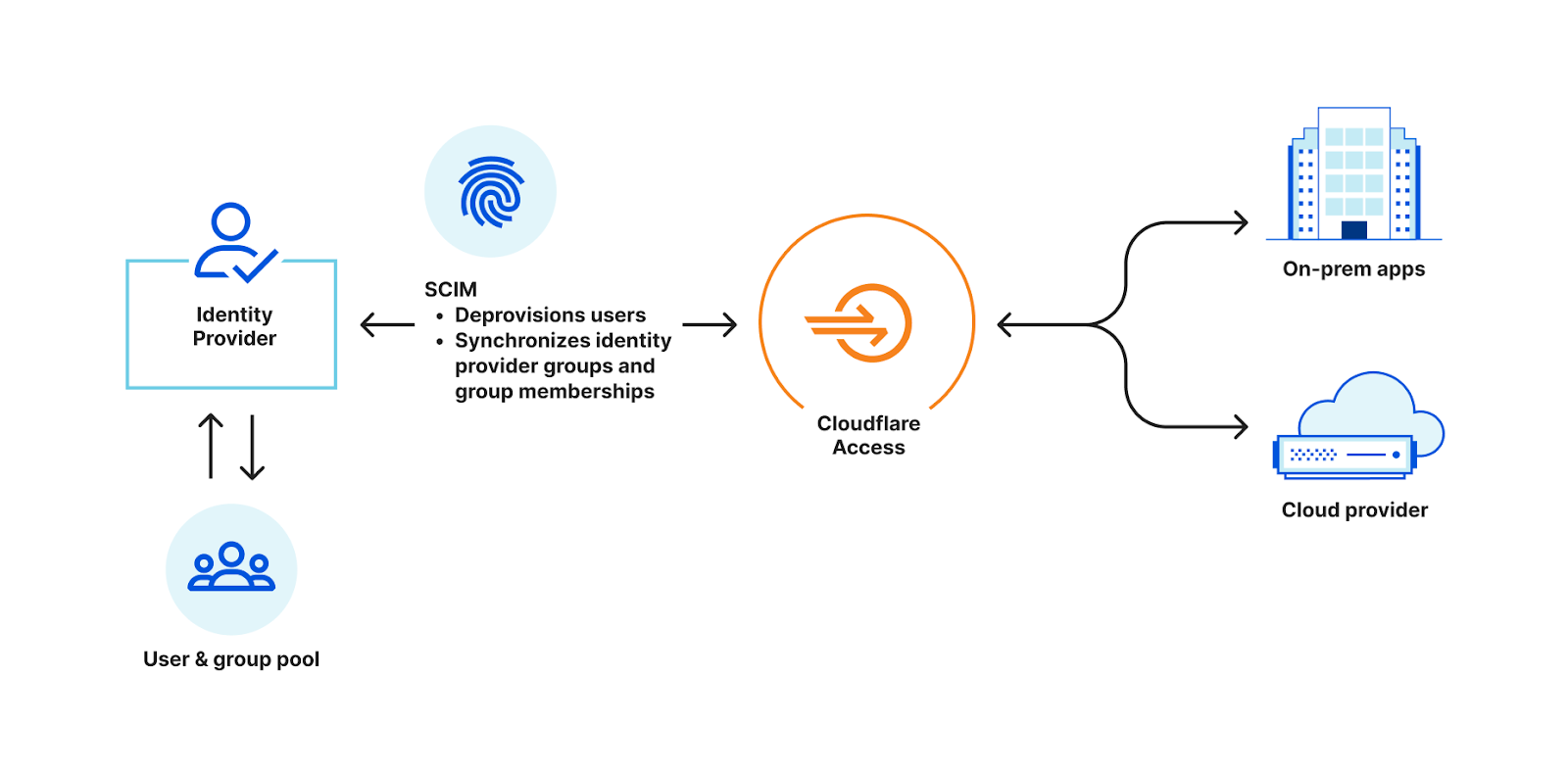
For example, most organizations have an identity provider, such as Okta or Azure Active Directory, that stores information about its employees, such as names, addresses, and job titles. The organization also likely uses cloud-based applications for collaboration. In order to access the cloud-based application, employees need to create an account and log in with a username and password. Instead of manually creating and managing these accounts, the organization can use SCIM to automate the process. Both the on-premise system and the cloud-based application are configured to support SCIM.
When a new employee is added to, or removed from, the identity provider, SCIM automatically creates an account for that employee in the Continue reading
Zone Versioning is now generally available


Today we are announcing the general availability of Zone Versioning for enterprise customers. Zone Versioning allows you to safely manage zone configuration by versioning changes and choosing how and when to deploy those changes to defined environments of traffic. Previously announced as HTTP Applications, we have redesigned the experience based on testing and feedback to provide a seamless experience for customers looking to safely rollout configuration changes.
Problems with making configuration changes
There are two problems we have heard from customers that Zone Versioning aims to solve:
- How do I test changes to my zone safely?
- If I do end up making a change that impacts my traffic negatively, how can I quickly revert that change?
Customers have worked out various ways of solving these problems. For problem #1, customers will create staging zones that live on a different hostname, often taking the form staging.example.com, that they make changes on first to ensure that those changes will work when deployed to their production zone. When making more than one change this can become troublesome as they now need to keep track of all the changes made to make the exact same set of changes on the Continue reading
API-based email scanning


The landscape of email security is constantly changing. One aspect that remains consistent is the reliance of email as the beginning for the majority of threat campaigns. Attackers often start with a phishing campaign to gather employee credentials which, if successful, are used to exfiltrate data, siphon money, or perform other malicious activities. This threat remains ever present even as companies transition to moving their email to the cloud using providers like Microsoft 365 or Google Workspace.
In our pursuit to help build a better Internet and tackle online threats, Cloudflare offers email security via our Area 1 product to protect all types of email inboxes - from cloud to on premise. The Area 1 product analyzes every email an organization receives and uses our threat models to assess if the message poses risk to the customer. For messages that are deemed malicious, the Area 1 platform will even prevent the email from landing in the recipient's inbox, ensuring that there is no chance for the attempted attack to be successful.
We try to provide customers with the flexibility to deploy our solution in whatever way they find easiest. Continuing in this pursuit to make our solution as turnkey as Continue reading