DDoS attack trends for 2022 Q2


Welcome to our 2022 Q2 DDoS report. This report includes insights and trends about the DDoS threat landscape — as observed across the global Cloudflare network. An interactive version of this report is also available on Radar.
In Q2, we’ve seen some of the largest attacks the world has ever seen including a 26 million request per second HTTPS DDoS attacks that Cloudflare automatically detected and mitigated. Furthermore, attacks against Ukraine and Russia continue, whilst a new Ransom DDoS attack campaign emerged.
The Highlights
Ukrainian and Russian Internet
- The war on the ground is accompanied by attacks targeting the spread of information.
- Broadcast Media companies in the Ukraine were the most targeted in Q2 by DDoS attacks. In fact, all the top five most attacked industries are all in online/Internet media, publishing, and broadcasting.
- In Russia on the other hand, Online Media drops as the most attacked industry to the third place. Making their way to the top, Banking, Financial Services and Insurance (BFSI) companies in Russia were the most targeted in Q2; almost 45% of all application-layer DDoS attacks targeted the BFSI sector. Cryptocurrency companies in Russia were the second most attacked.
Read more about what Cloudflare is doing Continue reading
2022年第2四半期におけるDDoS攻撃の傾向


2022年第2四半期DDoSレポートへようこそ。このレポートには、グローバルなCloudflareネットワークで観測されたDDoS脅威の状況についてのインサイトと動向が含まれています。また、本レポートのインタラクティブ版はRadarでご覧いただけます。
毎秒2600万件のリクエストのHTTPS DDoS攻撃をCloudflareが自動的に検出して軽減するなど、第2四半期には、これまでにない大規模な攻撃が発生しています。さらに、ウクライナとロシアに対する攻撃は続いており、新しいランサムDDoS攻撃キャンペーンも出現しています。
ハイライト
ウクライナおよびロシアのインターネット
- 地上での戦争は、情報の拡散を狙った攻撃を伴います。
- 第2四半期に主なDDoS攻撃の標的となったのは、ウクライナの放送メディア企業でした。実際、最も攻撃されている上位6業種は、すべてオンライン/インターネットメディア、出版、放送のものです。
- 一方、ロシアでは、オンラインメディアが最も攻撃されている業界として第3位に転落しました。トップに向かって進んでいる企業であるため、第2四半期に最も標的とされたのは、ロシアの銀行、金融サービス、保険(BFSI)企業で、アプリケーション層DDoS攻撃全体の約50%がBFSIセクターを標的としていました。ロシアの暗号通貨関連企業は2番目に最も攻撃されました。
オープンインターネットのロシアへの流入を続けるため、攻撃を防ぐためにCloudflareが行っていることをご覧ください。
ランサムDDoS攻撃
- Fancy Lazarusを名乗るエンティティによるランサムDDoS攻撃の新たな波が来ています。
- 2022年6月にはランサム攻撃がピークに達し、これまでの1年間で最高となりました。DDoS攻撃を経験した調査回答者の5人に1人が、ランサムDDoS攻撃などの脅威を受けたと回答しています。
- 第2四半期全体では、ランサムDDoS攻撃の割合が前四半期比で11%増となりました。
アプリケーション層DDoS攻撃
- 2022年第2四半期、アプリケーション層DDoS攻撃は前年比で44%増となりました。
- 米国の組織が最も狙われ、次いでキプロス、香港、中国と続きます。キプロスにおける組織への攻撃は前四半期比で171%増となりました。
- 第2四半期に最も標的にされたのは航空・宇宙業界、次いでインターネット業界、銀行・金融サービスおよび保険、そして4位はゲーミング/ギャンブルとなっています。
ネットワーク層DDoS攻撃
- 2022年第2四半期、ネットワーク層DDoS攻撃は前年比で75%増となりました。100Gbps以上の攻撃は前四半期比で19%増、3時間以上継続する攻撃は前四半期比で9%増となりました。
- 攻撃された上位の業種は、電気通信、ゲーミング/ギャンブル、情報技術およびサービス業界でした。
- 米国の組織が最も標的にされ、次いでシンガポール、ドイツ、中国と続いています。
本レポートは、CloudflareのDDoS Protectionシステムによって自動的に検知・軽減されたDDoS攻撃に基づいています。この仕組みの詳細については、詳しく書かれたこちらのブログ記事をご覧ください。
当社ネットワークで観測されたDDoS攻撃の測定方法についての特記事項
攻撃の傾向を分析するために、当社のグローバルネットワーク、特定の場所、または特定のカテゴリ(業界や請求先の国など)で観測された総トラフィック(攻撃+クリーン)に占める攻撃トラフィックの割合である「DDosの活動」レートを計算します。割合を測定することで、データポイントを正規化し、例えば総トラフィックが多く、攻撃回数も多いと思われるCloudflareデータセンターに対する絶対数に反映される数値の偏りを回避することができます。
ランサム攻撃
当社のシステムはトラフィックを常時分析し、DDoS攻撃を検知すると自動的に被害軽減措置を適用するシステムです。DDoSの被害に遭われたお客様には、攻撃の性質や軽減措置の効果をよりよく理解するために、自動化されたアンケートをお願いしています。
Cloudflareは2年以上前から、攻撃を受けたお客様を対象にアンケートを実施しています。アンケート項目の1つに、DDoS攻撃を中止する代わりに脅威や支払いを要求する身代金請求書を受け取ったかどうかというものがあります。
第2四半期に脅威や身代金要求メッセージがあったという回答は、前四半期比、前年比ともに11%増となりました。当四半期は、高度で継続的な脅威(APT)グループ、「Fancy Lazarus」を名乗るエンティティが仕掛けたランサムDDoS攻撃を軽減しています。金融機関や暗号通貨企業などを中心にキャンペーンを展開しています。

第2四半期に掘り下げると、6月には回答者の5人に1人がランサムDDoS攻撃や脅威を受けたと報告しています。これは2022年で最も高い月で、2021年12月以降最高となりました。

アプリケーション層DDoS攻撃
アプリケーション層DDoS攻撃(具体的にはHTTP DDoS攻撃)は通常、正当なユーザーリクエストを処理できないようにしてWebサーバーを停止させることを目的とします。処理能力を超えるリクエストが殺到すると、サーバーは正当なリクエストをドロップするか、場合によってはクラッシュし、その結果、正当なユーザーに対するパフォーマンスの低下や障害がに繋がります。
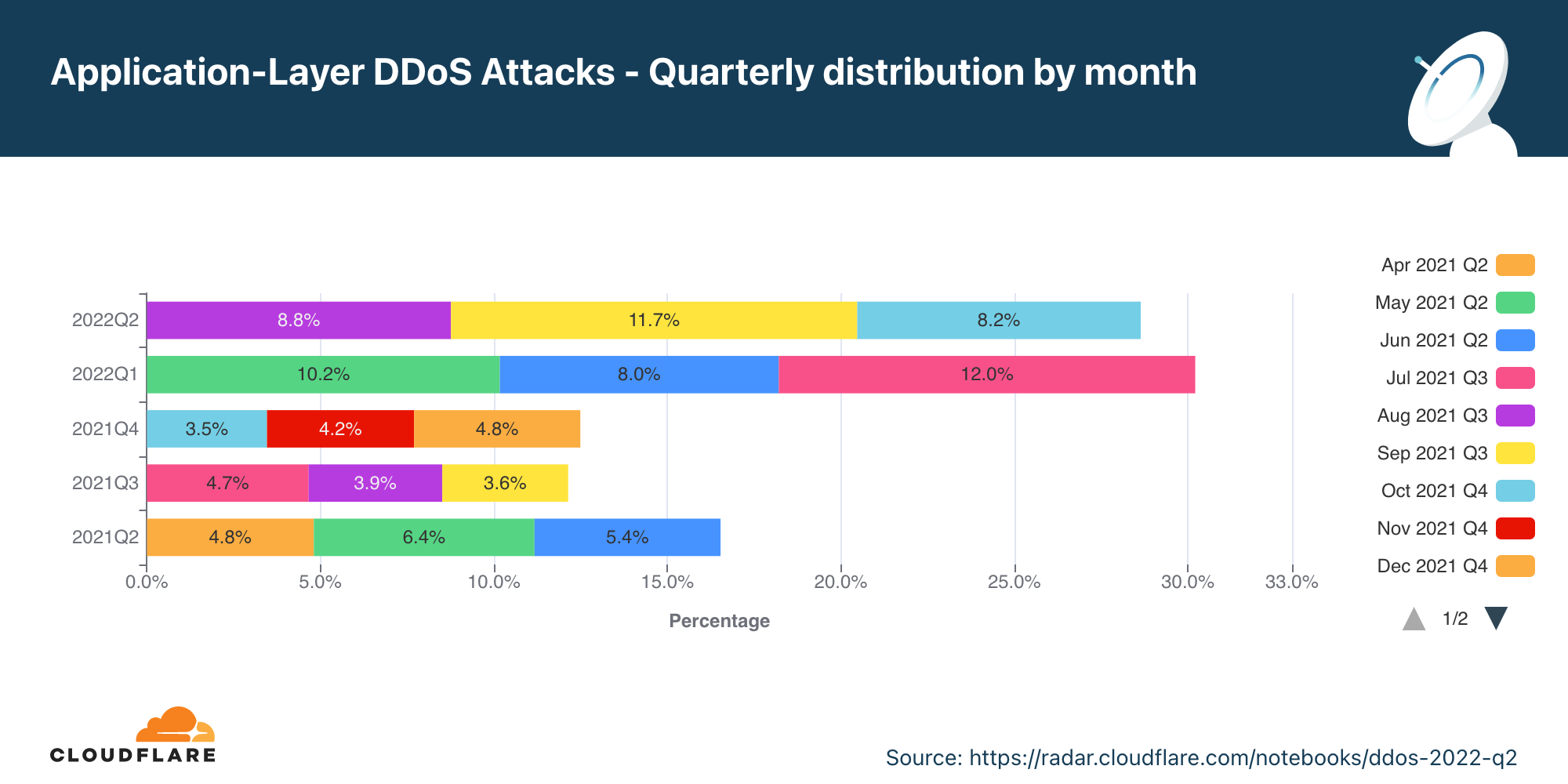
アプリケーション層DDoS攻撃の月別推移
第2四半期のアプリケーション層DDoS攻撃は、前年比で44%増となりました。
全体として、第2四半期のアプリケーション層DDoS攻撃の量は、前年比で44%増となりましたが、前四半期比では16%減となりました。5月は当四半期で最も忙しい月でした。アプリケーション層DDoS攻撃は、全体の約47%が5月に発生したのに対し、6月に起きた攻撃数は最も少ないものでした(18%)。
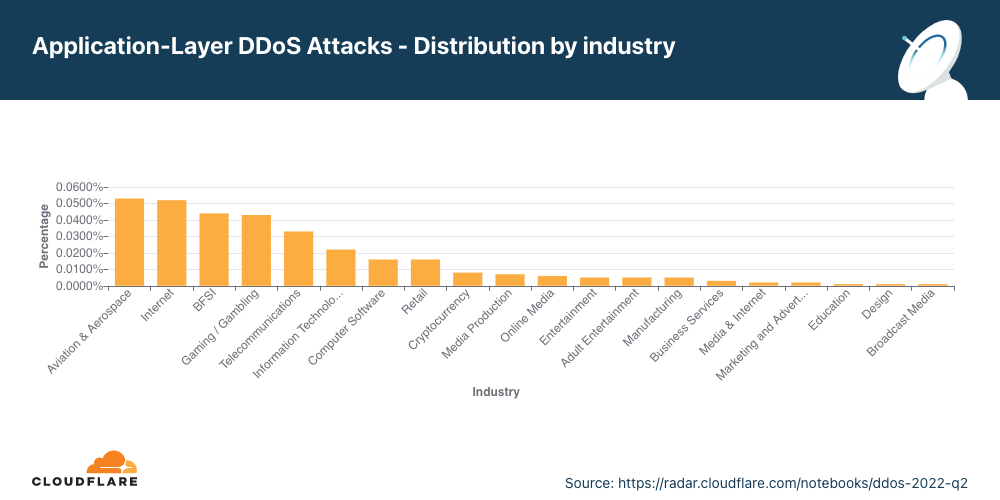
アプリケーション層DDoS攻撃<業界別>
航空・宇宙業界への攻撃は前四半期比で256%増となりました。
第2四半期では、アプリケーション層DDoS攻撃で最も標的とされたのは航空・宇宙業界でした。以下、銀行・金融機関・保険(BFSI)業界、ゲーミング/ギャンブル業界と続きます。
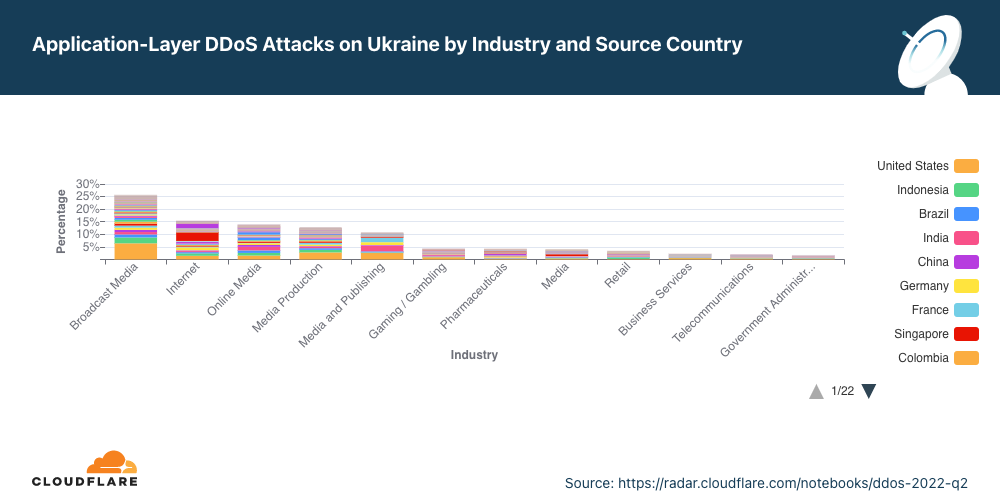
ウクライナおよびロシアのサイバースペース
ウクライナで最も狙われているのはメディア企業と出版社です。
ウクライナでの戦争が地上、空中、水上で続いているように、サイバースペースでも戦争が続いています。ウクライナ企業を標的にするエンティティは、情報を封じ込めようとしているようです。ウクライナで最も攻撃された上位6業種は、すべて放送、インターネット、オンラインメディア、出版のもので、これはウクライナを標的とするDDoS攻撃全体のほぼ80%に相当します。
もう一方の側は、ロシアの銀行、金融機関、保険(BFSI)の企業が最も多くの攻撃を受けました。DDoS攻撃全体のほぼ50%がBFSIセクターを標的としました。2番目に最も標的となったのは暗号通貨業界、次いでオンラインメディアでした。
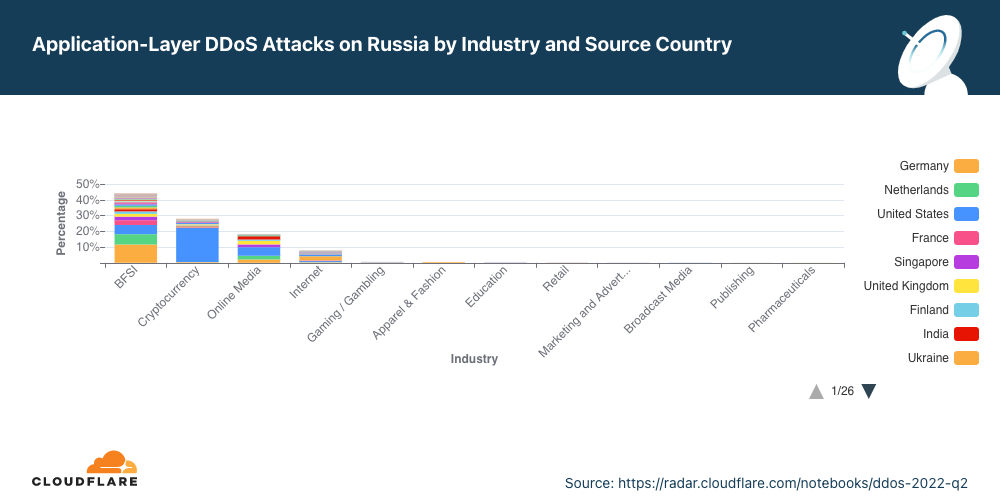
戦争の両側で、攻撃は高度に分散化され、世界中に分散されたボットネットが使用されていることが分かります。
アプリケーション層DDoS攻撃<攻撃元の国別>
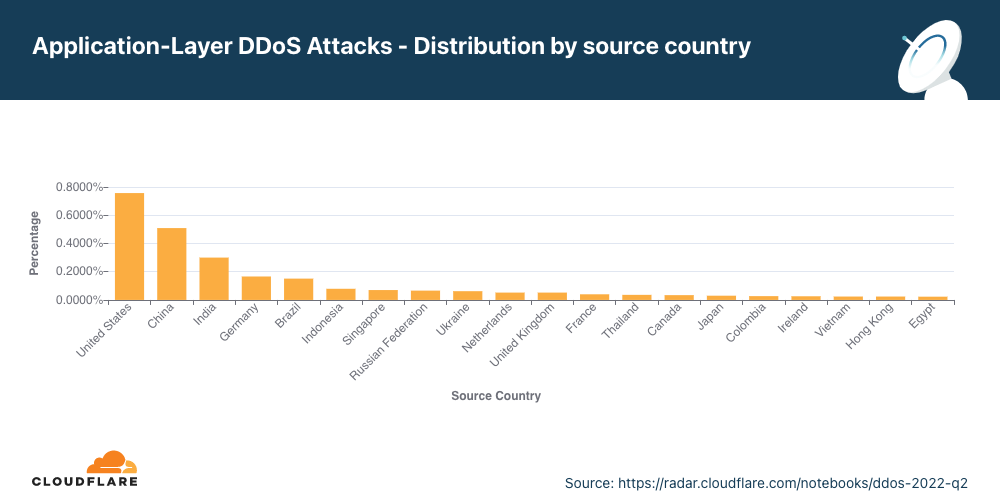
第2四半期には、中国からの攻撃が112%増となった一方で、米国からの攻撃は43%縮小しています。
HTTP攻撃の発信元を理解するため、当社は攻撃のHTTPリクエストを生成したクライアントに属する送信元IPアドレスのジオロケーションを調べました。ネットワーク層の攻撃とは異なり、HTTP攻撃ではソースIPアドレスをスプーフィングすることはできません。ある国でのDDoS活動の割合が高いということは、その特定の国が攻撃を仕掛けているということではなく、その国の国境内から活動するボットネットが存在することを示しています。
HTTP DDoS攻撃の主な発生源として、第2四半期連続で米国がトップとなりました。米国に続く2位は中国、3位と4位はインドとドイツです。米国が1位を維持しているにもかかわらず、米国発の攻撃が前四半期比で43%減少した一方で、中国からの攻撃が112%、インドからの攻撃が89%、ドイツからの攻撃が50%と、他の地域からの攻撃は増加しています。
アプリケーション層DDoS攻撃<標的国別>
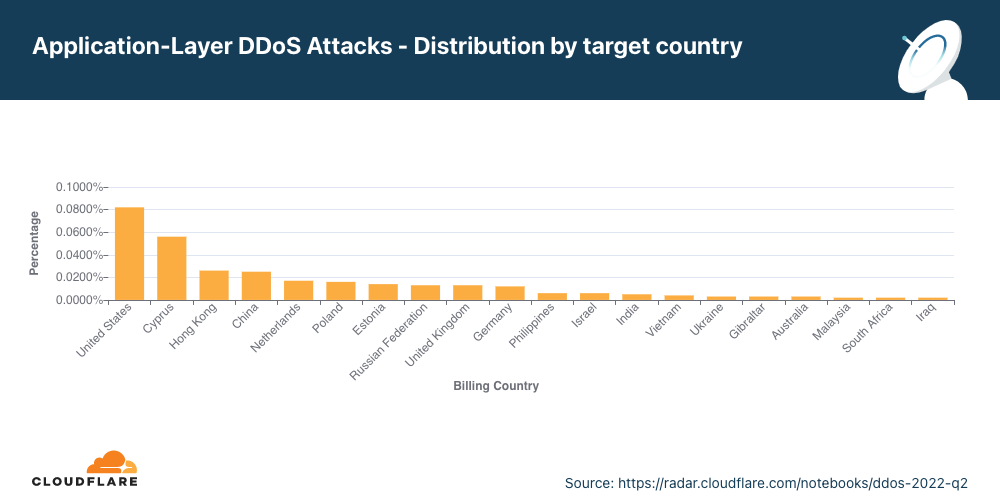
どの国が最もHTTP DDoS攻撃の標的になっているかを特定するため、お客様の請求先国別にDDoS攻撃を分類し、全DDoS攻撃に対する割合で表現しています。
米国を拠点とする国へのHTTP DDoS攻撃は前四半期比で45%増となり、アプリケーション層DDoS攻撃の主な標的として米国が1位に返り咲きました。中国企業への攻撃は前四半期比で79%減となり、1位から4位に下がりました。キプロスへの攻撃は171%増加し、第2四半期に最も攻撃された国第2位となりました。キプロスに続いて、香港、中国、ポーランドが続いています。
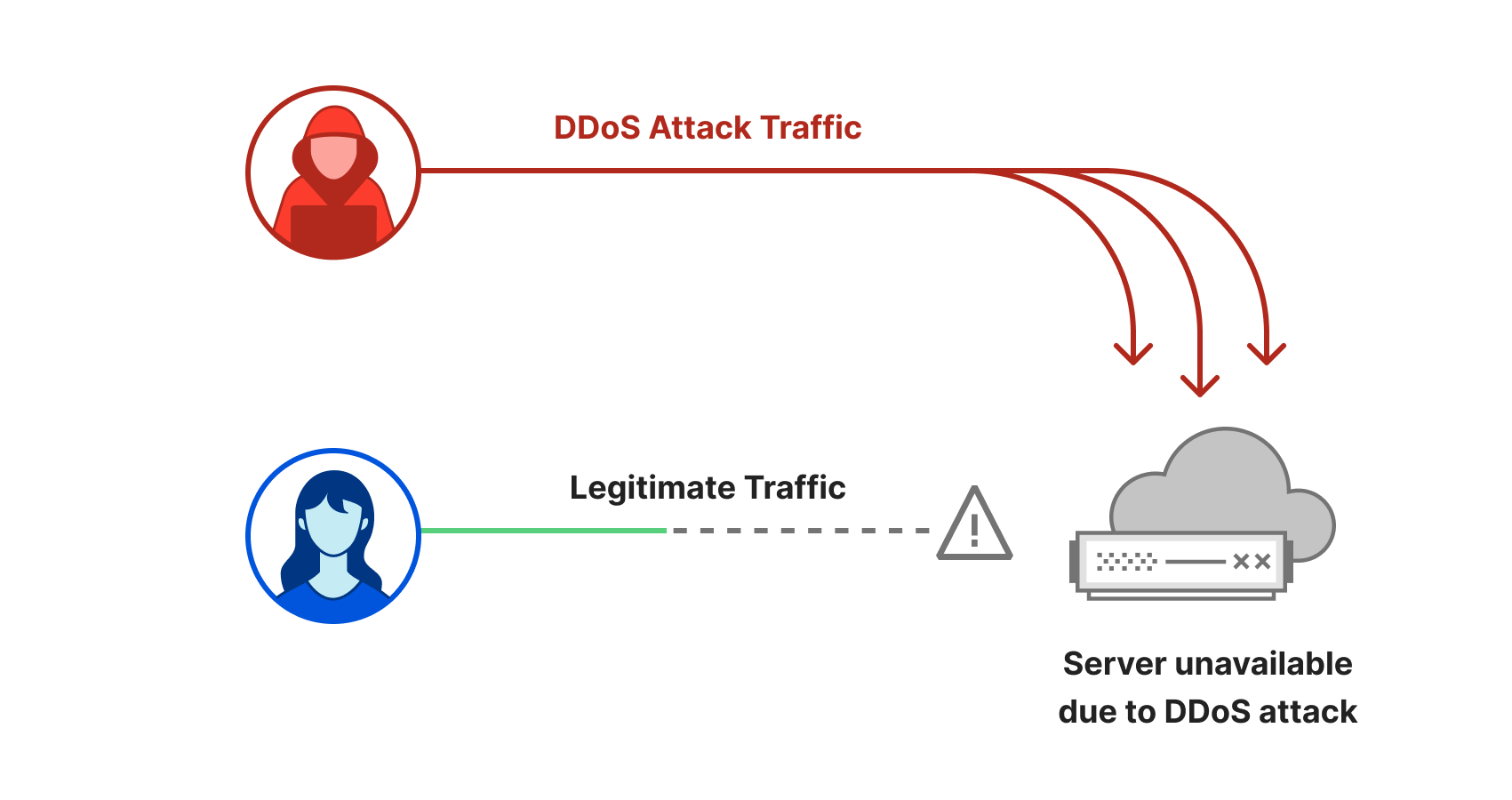
ネットワーク層DDoS攻撃
アプリケーション層攻撃は、エンドユーザーがアクセスしようとしているサービスを実行するアプリケーション(OSI参照モデルのレイヤー7)を狙うのに対し、ネットワーク層攻撃はネットワークインフラ(インラインルーターやサーバーなど)とインターネットリンクそのものを圧倒しようとします。
ネットワーク層DDoS攻撃<月別>
第2四半期のネットワーク層DDoS攻撃は前年比で75%増、100Gbps以上の帯域幅消費型攻撃は前四半期比で19%増となりました。
第2四半期は、ネットワーク層DDoS攻撃の総量が前年比で75%増となりましたが、前四半期と比較して大きな変化はありませんでした。4月は、攻撃の約40%が発生し、四半期で最も忙しい月となりました。
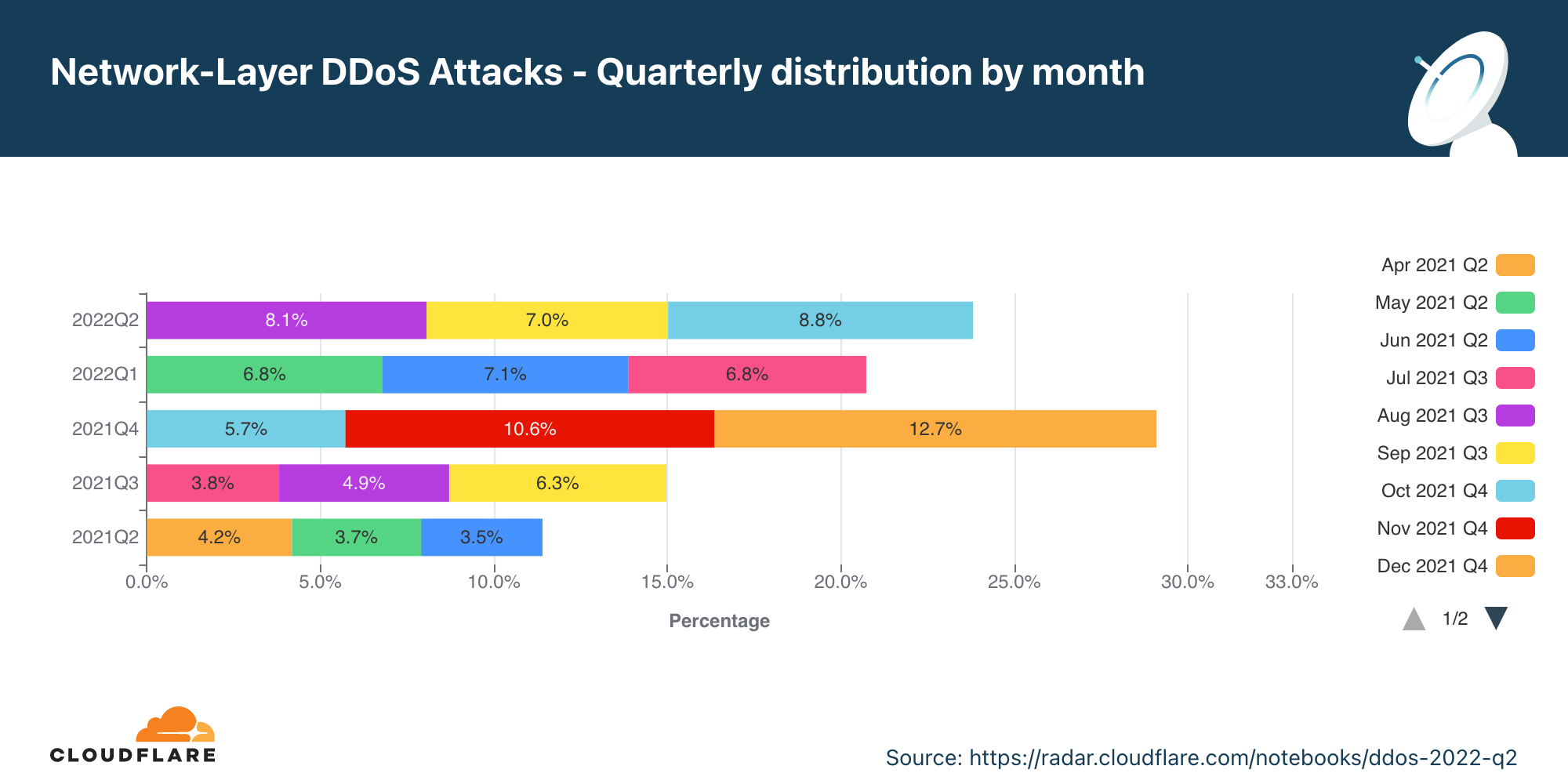
業種別ネットワーク層DDoS攻撃
第2四半期の通信会社への攻撃は、前四半期比で45%増となりました。
ネットワーク層DDoS攻撃は、2四半期連続で通信業界が最も多く標的となりました。さらに、通信会社への攻撃は前四半期比で45%増となりました。2位はゲーミング業界、続いて情報技術・サービス企業でした。

ネットワーク層DDoS攻撃<標的国別>
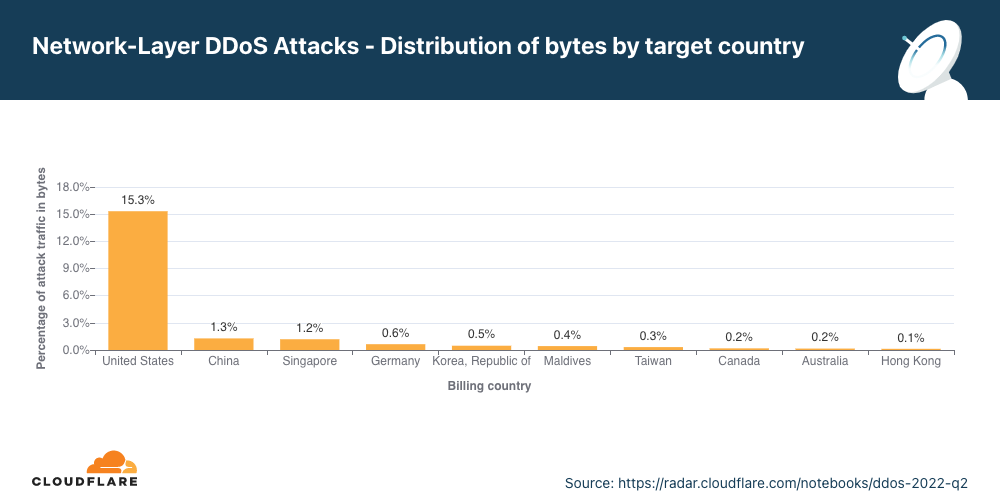
米国ネットワークへの攻撃は前四半期比で70%増となりました。
第2四半期においても、米国は最も攻撃された国です。米国に続き、シンガポールが前四半期の4位から2位に急浮上しました。3位はドイツ、それから中国、モルディブ、韓国でした。
流入国別ネットワーク層DDoS攻撃
第2四半期にCloudflareがパレスチナとアゼルバイジャンで観測したトラフィックの約3分の1は、ネットワーク層DDoS攻撃の一部でした。
ネットワーク層DDoS攻撃の発生源を把握しようとする場合、アプリケーション層の攻撃解析と同じ方法は使えません。アプリケーション層DDoS攻撃を仕掛けるには、HTTP/S接続を確立するために、クライアントとサーバーの間でハンドシェイクを成功させる必要があります。ハンドシェイクを成功させるため、攻撃者はその送信元IPアドレスを偽装することができません。そのため攻撃者はボットネット、プロキシ、およびその他の方法を使用して身元を難読化させることができますが、攻撃側クライアントの送信元IPは偽装できないため、そのIPはアプリケーション層DDoS攻撃の発信源を正しく示しています。
一方、ネットワーク層DDoS攻撃を仕掛けるには、ほとんどの場合ハンドシェイクは必要ありません。攻撃者は攻撃元を難読化し、攻撃特性にランダム性を導入して単純なDDoS防御システムでは攻撃をブロックすることを困難にするために、ソースIPアドレスを偽装することができます。そのため、偽装された送信元IPに基づいて発信源の国を導き出した場合、「偽装された国」を得ることになります。
このため、ネットワーク層DDoS攻撃の発信源を分析する際には、攻撃の発信源を把握するためにスプーフィングされた(可能性のある)ソースIPではなく、トラフィックが取り込まれたCloudflareエッジデータセンターのロケーション別にバケットを構成します。世界270以上の都市にデータセンターがあるため、レポートで地理的な精度を実現できます。ただし、コスト削減から輻輳や障害管理まで、さまざまな理由でトラフィックがバックホールされ、さまざまなインターネットサービスプロバイダや国を経由してルーティングされる可能性があるため、この方法でも100%正確ではありません。
ネットワーク層DDoS攻撃の割合が最も高いCloudflareのロケーションとして、パレスチナが2位から1位に跳ね上がりました。パレスチナに続いて、アゼルバイジャン、韓国、アンゴラと続きます。

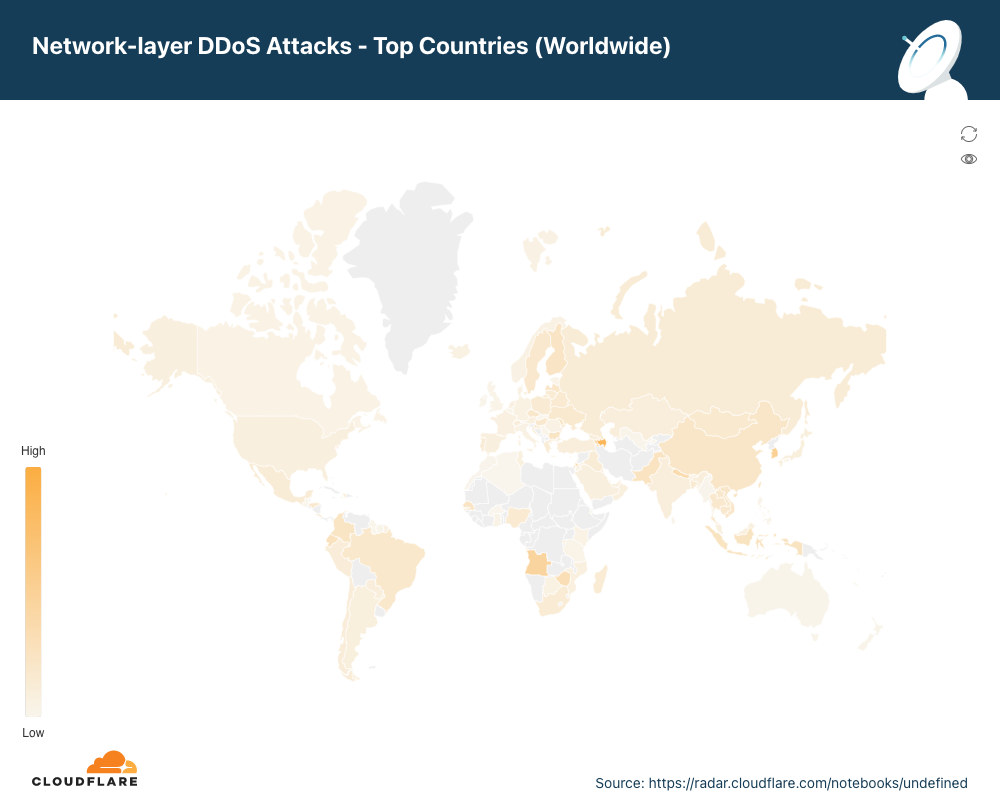
すべての地域と国を表示するには、インタラクティブマップをご覧ください。
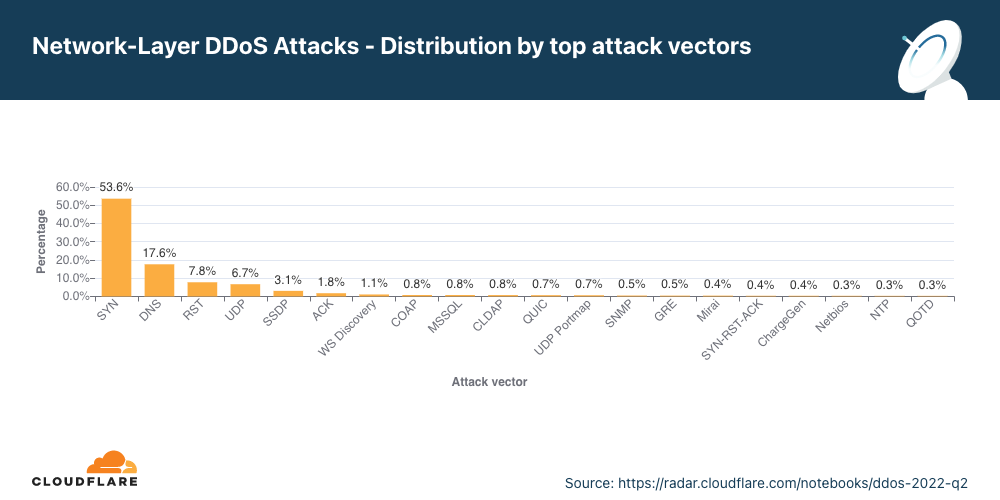
攻撃ベクトル
第2四半期では、DNS攻撃が増加し、2番目に多い攻撃ベクトルとなりました。
攻撃ベクトルとは、攻撃者がDDoS攻撃を行う際に用いる手法のことで、IPプロトコル、TCPフラグなどのパケット属性、フラッディング方法などの基準を示す言葉です。
第2四半期において、ネットワーク層に対する全攻撃の56%は、SYNフラッド でした。SYNフラッドは、依然として最も一般的な攻撃ベクトルです。この攻撃は、ステートフルなTCPハンドシェイクの最初の接続リクエストを悪用します。この最初の接続リクエストの間、サーバーは新しいTCP接続に関するコンテキストを持たず、適切な保護がなければ、最初の接続リクエストのフラッドを軽減することが困難であることが分かるかもしれません。このため、攻撃者は保護されていないサーバーのリソースを容易に消費することができます。
SYNフラッドの次は、DNSインフラストラクチャを狙った攻撃、再びTCP接続フローを悪用するRSTフラッド、UDPを使った一般的な攻撃です。
新たな脅威
第2四半期における、新たな上位の脅威にはCHARGEN、Ubiquiti、Memcachedを狙った攻撃があります。
上位の攻撃ベクトルを特定することは、組織が脅威の状況を理解するのに役立ちます。そうすることで、これらの脅威から身を守るためにセキュリティ体制を強化することができます。同様に、まだ攻撃の大部分を占めていない新たな脅威について知ることは、それらが大きな力となる前に軽減するのに役立ちます。
第2四半期には、Character Generatorプロトコル(CHARGEN)を悪用した増幅攻撃、露出したUbiquitiデバイスのトラフィックを反映した増幅攻撃、悪名高いMemcached攻撃が新たな脅威の上位にランクインしています。
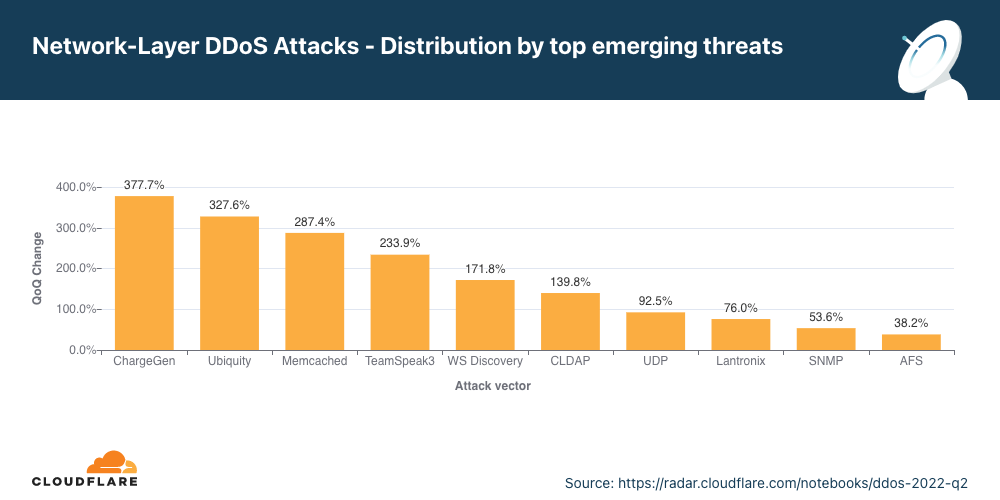
CHARGENプロトコルを悪用した増幅攻撃の開始
第2四半期には、CHARGENプロトコルを悪用した攻撃が前四半期比で378%増となりました。
RFC 864(1983)で最初に定義されたCharacter Generator(CHARGEN)プロトコルは、インターネットプロトコルスイートのサービスで、その名の通り、文字を任意に生成し、クライアントが接続を閉じるまでクライアントへの送信を停止しません。その当初の目的は、テストとデバッグでした。しかし、増幅/リフレクション攻撃を生成するために非常に簡単に悪用される可能性があるため、めったに使用されません。
攻撃者は、被害者のソースIPをスプーフィングすることができ、世界中のサポートサーバーを騙して、任意の文字のストリームを被害者のサーバーに「戻す」ことができます。この種の攻撃は、増幅/リフレクションです。十分な数のCHARGENストリームが同時に発生すると、被害者のサーバーは、保護されていない場合、殺到して正当なトラフィックに対処できなくなり、結果としてサービス拒否が発生することになります。
Ubiquiti Discoveryプロトコルを不正利用した増幅攻撃
第2四半期には、ユビキティに対する攻撃が前四半期比で313%増となりました。
Ubiquitiは、米国に拠点を置く企業で、消費者や企業向けにInternet of Things(IoT)デバイスを提供しています。Ubiquitiのデバイスは、UDP/TCPポート10001のUbiquiti Discoveryプロトコルを使用してネットワーク上で見つけることができます。
CHARGEN攻撃ベクトルと同様に、ここでも攻撃者はソースIPを被害者のIPアドレスに偽装し、10001番ポートを開放しているIPアドレスに吹き付けることができます。そして、それらは被害者に対応し、量が十分であれば実質的に殺到することになります。
memchachedを利用したDDoS攻撃
第2四半期には、Memcached DDoS攻撃は前四半期比で281%増となりました。
Memcachedは、Webサイトやネットワークを高速化するためのデータベースキャッシュシステムです。CHARGENやUbiquitiと同様に、UDPをサポートするMemcachedサーバーは、増幅/リフレクション型DDoS攻撃を仕掛けるために悪用される可能性があります。この場合、攻撃者はキャッシュシステムからコンテンツをリクエストし、UDPパケットのソースIPとして被害者のIPアドレスをスプーフィングします。被害者には、最大51,200倍に増幅されたMemcacheのレスポンスが殺到することになります。
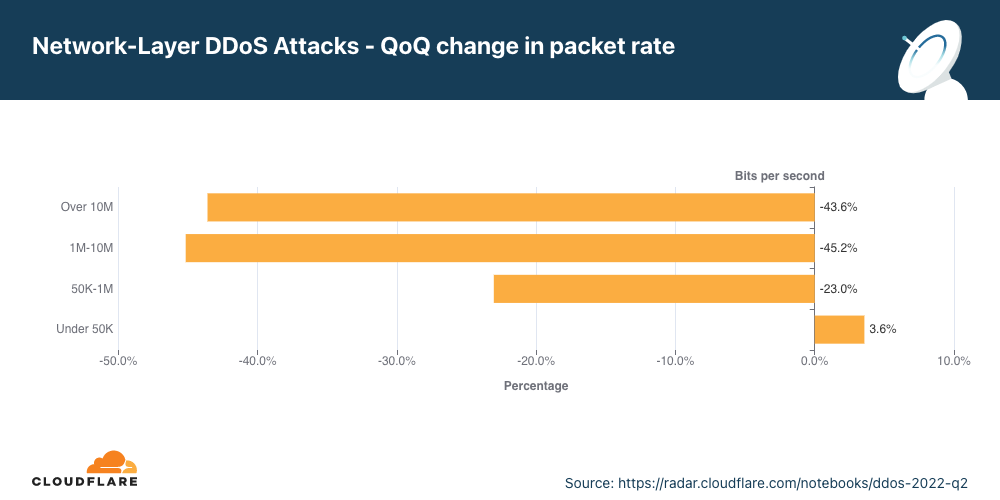
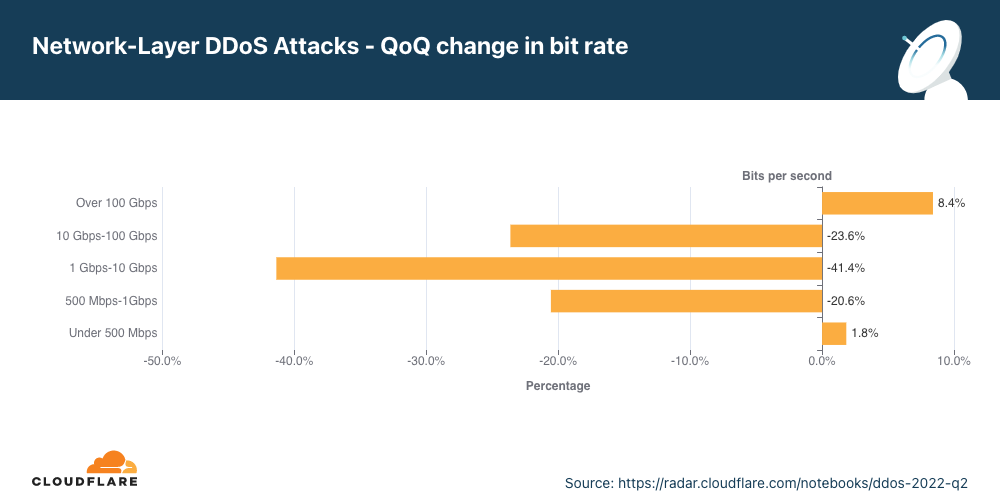
ネットワーク層DDoS攻撃<攻撃レート別>
100Gbpsを超える帯域幅消費型攻撃は前四半期比で19%増となりました。3時間以上の攻撃は9%増加しました。
L3/4 DDoS攻撃の規模の測定には、さまざまな方法があります。1つは送信するトラフィックの量で、ビットレート(具体的にはテラビット/秒またはギガビット/秒)を使用して測定するものです。もう1つは送信するパケットの数で、パケットレート(具体的には、何百万パケット/秒)を使用して測定するものです。
ビットレートの高い攻撃は、インターネットリンクの閉塞を発生させることによってサービス妨害を起こそうとし、パケットレートの高い攻撃はサーバーやルーター、その他のインラインハードウェア機器を過負荷状態に陥れようとします。これらの機器は各パケットの処理に特定量のメモリと計算能力を割きます。多数のパケットが送り付けられると機器の処理リソースが枯渇してしまう可能性があります。その場合はパケットが「ドロップ」されます。つまり、機器がそれらを処理できない状態となるのです。ユーザーに対しては、サービスの中断や拒否になります。
パケットレート別分布
ネットワーク層DDoS攻撃の大半は、毎秒5万パケット以下にとどまっています。50kppsはCloudflareの規模では低い方ですが、それでも保護されていないインターネットのプロパティを簡単にダウンさせ、標準的なギガビットイーサネット接続でさえも輻湊させることができます。
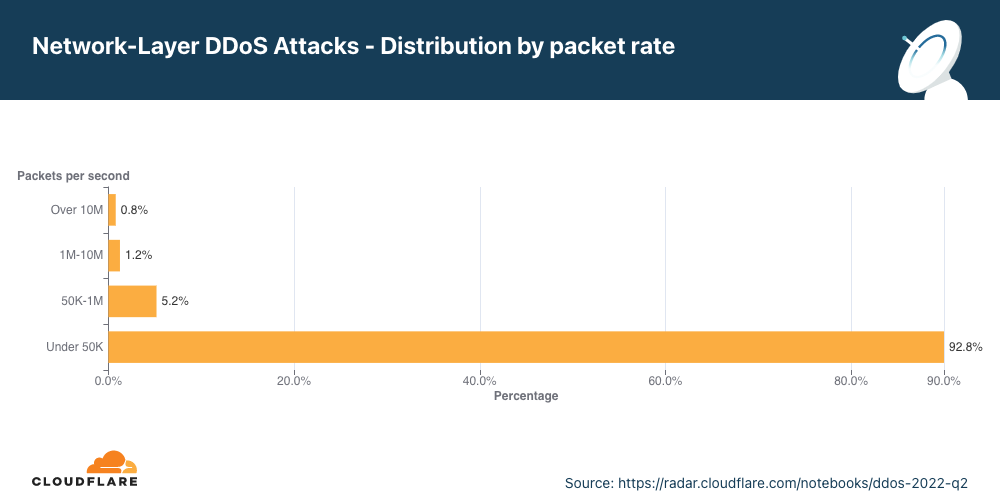
攻撃規模の変化を見ると、50 kppsを超えるパケット集中型の攻撃が第2四半期に減少し、その結果、小規模な攻撃が4%増加したことがわかります。
ビットレート別分布
第2四半期は、ネットワーク層DDoS攻撃の大半が500Mbps未満にとどまっています。これもCloudflareの規模ではわずかな減少ですが、保護されていないインターネットのプロパティを即座に停止させ、また少なくとも標準的なギガビットイーサネット接続でさえも輻湊を引き起こすことができます。
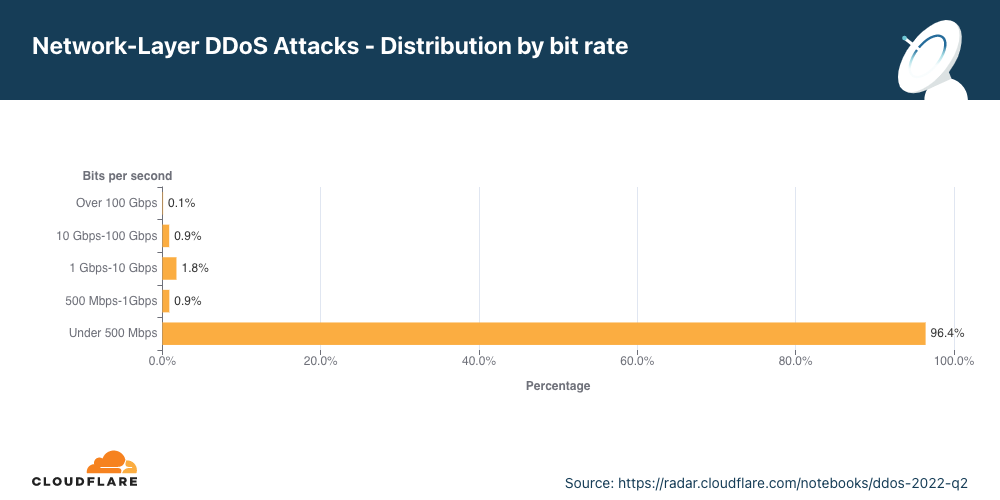
興味深いことに、500Mbpsから100Gbpsの間の大規模な攻撃は前四半期比で20~40%減少しましたが、100Gbps以上の帯域幅消費型攻撃は8%増加しました。
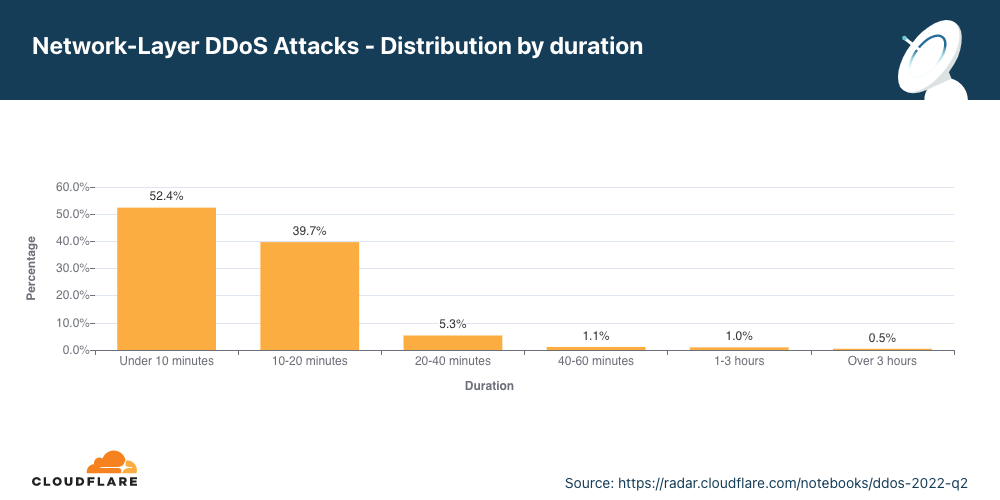
ネットワーク層DDoS攻撃<継続時間別>
第2四半期では、3時間以上の攻撃は9%増となりました。
当社では、攻撃が当社のシステムによって最初に検出されたときと、特定のターゲットに向けた攻撃シグネチャを持つ最後のパケットを確認したときの差を記録することによって、攻撃の持続時間を測定しています。
第2四半期では、ネットワーク層DDoS攻撃の51%が10分未満で終了しました。さらに41%は10〜20分でした。残りの8%は、20分から3時間以上にわたる攻撃です。
留意すべき重要な点は、たとえ数分間の攻撃であっても、それが成功すれば、その影響は最初の攻撃時間をはるかに超えて続く可能性があるということです。攻撃が成功した場合、対応するIT担当者はサービスの復旧に数時間から数日を費やすことがあります。
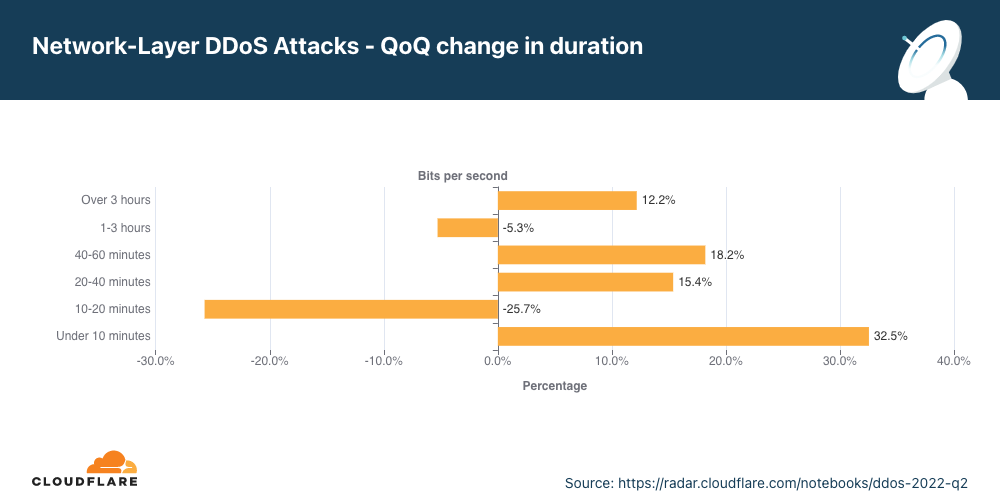
ほとんどの攻撃が短時間になっているものの、20分〜60分の攻撃が15%以上、3時間以上の攻撃が12%増となっていることがわかります。
短時間の攻撃は検出されない可能性があり、特に標的に対して数秒以内に大量のパケットやバイト、リクエストを送りつけるバースト攻撃は見逃されがちです。この場合、セキュリティ分析に基づく手作業の軽減措置に依存するDDoS攻撃対策では、攻撃への被害軽減措置がとても間に合いません。攻撃について事後の分析を通して学び、その攻撃固有のフィンガープリントでフィルタリングする新たなルールをデプロイして、次回の攻撃は検知できるよう願うしかありません。同様に、「オンデマンド」サービスを利用してセキュリティチームが攻撃中にDDoS対策サービスのプロバイダーへトラフィックをリダイレクトする場合も、オンデマンドDDoS対策のプロバイダーへトラフィックがルーティングされる前に攻撃が済んでしまうため非効率です。
これらの企業では、トラフィックを分析し、短時間の攻撃をブロックするのに十分な速さでリアルタイムのフィンガープリンティングを適用する、自動化された常時稼働型のDDoS攻撃対策サービスを使用することが推奨されます。
まとめ
Cloudflareのミッションは、より良いインターネットの構築を支援することです。より良いインターネットとは、たとえDDoS攻撃に直面しても、誰にとっても、より安全で、より速く、より信頼できるインターネットです。ミッションの一環として、2017年以降、すべてのお客様に定額制で無制限のDDoS攻撃対策を無償で提供しています。ここ数年、攻撃者がDDoS攻撃を仕掛けることはますます容易になってきています。しかし、このように簡単になったからこそ、あらゆる規模の組織があらゆる種類のDDoS攻撃から身を守ることも、これまで以上に簡単かつ無料でできるようにしたいと考えています。
まだCloudflareをお使いでない方は、当社のFreeまたはProプランを使用したWebサイトの保護を今すぐ始めるか、Magic Transitを使用したネットワーク全体の包括的なDDos攻撃対策に関してお問い合わせください。
2022 年第二季度 DDoS 攻击趋势


欢迎阅读我们的 2022 年第二季度 DDoS 攻击报告。本报告介绍有关 DDoS 威胁格局的洞察和趋势——反映了在 Cloudflare 全球网络中观察到的情况。本报告的交互式版本可在 Radar 上查看。
第二季度期间,我们观察到一些全球规模最大的攻击,包括一次 每秒 2600 万次请求的 HTTPS DDoS 攻击,这些攻击均被 Cloudflare 自动检测并缓解。此外,针对乌克兰和俄罗斯的攻击继续,并出现了一场新的勒索 DDoS 攻击活动。
要点
乌克兰和俄罗斯互联网
- 地面战斗伴随着针对信息传播的攻击。
- 乌克兰的广播媒体公司是第二季度 DDoS 攻击的最主要目标。事实上,受攻击最多的前六个行业均来自在线/互联网媒体、出版和广播。
- 另一方面,在俄罗斯,在线媒体作为受攻击最多的行业排名下降到第三位。俄罗斯的银行、金融服务和保险(BFSI)公司在第二季度成为最主要的攻击目标;几乎 50% 的应用层 DDoS 攻击均针对 BFSI 领域。俄罗斯的加密货币公司成为攻击的第二大目标。
进一步了解 Cloudflare 如何使开放互联网正常流入俄罗斯,并阻止攻击出境。
勒索 DDoS 攻击
- 我们观察到一波新的勒索 DDoS 攻击,由声称是 Fancy Lazarus 的组织发动。
- 2022 年 6 月,勒索攻击达到今年以来的最高水平:每 5 个经历过 DDoS 攻击的受访者中就有一个报称遭到勒索 DDoS 攻击或其他威胁。
- 总体而言,第二季度期间,勒索 DDoS 攻击的比例环比上升了 11%。
应用层 DDoS 攻击
- 2022 年第二季度期间,应用层 DDoS 攻击环比增长 44%。
- 美国的组织受到最多攻击,其次是塞浦路斯、中国香港和中国内地。针对塞浦路斯境内组织的攻击环比增长 171%。
- 航空航天行业是第二季度受到最多攻击的行业,其次是互联网行业,银行、金融服务和保险,以及第四位的博彩行业。
网络层 DDoS 攻击
- 2022 年第二季度期间,网络层 DDoS 攻击环比增长 75%。100 Gbps 及更大的攻击增长19%,持续 3 小时以上的攻击环比增长 9%。
- 受到最多攻击的行业为电信,游戏/博彩,信息技术和服务行业。
- 受到最多攻击的是位于美国的组织,其次是新加坡、德国和中国内地。
本报告基于 Cloudflare DDoS 防护系统自动检测并缓解的 DDoS 攻击。如需进一步了解其工作原理,请查看这篇深入剖析的博客文章。
简要说明一下我们如何测量在我们网络上观察到的 DDoS 攻击。
为分析攻击趋势,我们计算 “DDoS 活动”率,即攻击流量占我们全球网络上观察到的总流量(攻击+干净)、或在特定地点、或特定类别(如行业或账单国家)流量中的百分比。通过测量百分比,我们能够对数据点进行标准化,并避免绝对数字所反映出来的偏差。例如,如果某个 Cloudflare 数据中心接收到更多流量,则其也可能受到更多攻击。
勒索攻击
我们的系统持续分析流量,并在检测到 DDoS 攻击时自动应用缓解措施。每个遭受 DDoS 攻击的客户都会收到自动调查的提示,以帮助我们更好地了解攻击的性质和缓解是否成功。
两年多来,Cloudflare 一直对受到攻击的客户进行调查,其中一个问题是客户是否收到勒索信,要求其支付赎金来换取停止 DDoS 攻击。
第二季度期间,报称收到威胁或勒索信的受访者数量较上一季度和去年同期分别增加 11%。本季度期间,我们缓解了多次勒索 DDoS 攻击,发动者声称是高级持续性威胁(APT)组织 “Fancy Lazarus”。这些攻击活动的主要目标是金融机构和加密货币公司。

第二季度的详细数据显示, 6 月期间,有五分之一的受访者报称遭到一次勒索 DDoS 攻击或威胁——为 2022 年比例最高的月份,也是 2021 年 12 月以来的最高水平。

应用层 DDoS 攻击
应用层 DDoS 攻击,特别是 HTTP DDoS 攻击,旨在通过使 HTTP 服务器无法处理合法用户请求来造成破坏。如果服务器收到的请求数量超过其处理能力,服务器将丢弃合法请求甚至崩溃,导致对合法用户的服务性能下降或中断。

应用层 DDoS 攻击月度分布
第二季度,应用层 DDoS 攻击环比增长 44%。
总体而言,应用层 DDoS 攻击同比增长 44%,但环比减少 16%。5 月是该季度期间攻击最活跃的月份。近 47% 的应用层 DDoS 攻击发生在 5 月,而 6 月的攻击最少(18%)。

应用层 DDoS 攻击:行业分布
对航空航天行业发动的攻击环比增长 256%。
第二季度,航空航天行业是受到最多应用层攻击的行业。其次是银行、金融机构和保险行业(BFSI),排名第三的是博彩行业。

乌克兰和俄罗斯网络空间
乌克兰的媒体和出版公司受到最多攻击。
随着乌克兰的战事在海陆空继续,网络空间的对抗也在继续。以乌克兰公司为目标的实体似乎在试图掩盖信息。在乌克兰,受到攻击最多的六大行业均在广播、互联网、在线媒体和出版领域——占乌克兰所遭受 DDoS 攻击总数的接近 80%。

在战争的另一方,俄罗斯银行、金融机构和保险行业(BFSI)公司受到最多攻击。接近一半的 DDoS 攻击以 BFSI 领域为目标。第二大目标是加密货币行业,其次为在线媒体。

在战争的双方,我们都看到攻击是高度分布式的,表明使用了全球分布的僵尸网络。
应用层 DDoS 攻击:来源国家/地区分布
第二季度,源于中国的攻击增长112%,而来自美国的攻击减少 43%。
为了解 HTTP 攻击的来源,我们查看产生攻击的 HTTP Continue reading
2022 年第二季度 DDoS 攻擊趨勢


歡迎閱讀我們的 2022 年第二季 DDoS 報告。本報告包括有關 DDoS 威脅情勢的深入解析與趨勢,這些資訊從全球 Cloudflare 網路中觀察所得。Radar 上也會提供本報告的互動版本。
第二季度,我們看到了有史以來最大的一些攻擊,包括 Cloudflare 自動偵測並緩解的每秒 2600 萬個請求的 HTTPS DDoS 攻擊。此外,針對烏克蘭和俄羅斯的攻擊仍在繼續,而新的 DDoS 勒索攻擊活動又出現了。
重點內容
俄羅斯和烏克蘭網際網路
- 地面戰爭伴隨著針對資訊傳播的攻擊。
- 烏克蘭的廣播媒體公司成為第二季度 DDoS 攻擊的最大目標。事實上,前六大最受攻擊的產業均為網路/網際網路媒體、出版業和廣播業。
- 另一方面,在俄羅斯,網路媒體曾經是遭受攻擊最多的產業,如今下降到第三位。第二季度,俄羅斯的銀行、金融服務及保險業 (BFSI) 公司成為遭受攻擊最多的公司,躍居首位;BFSI 產業成為幾乎 50% 的應用程式層 DDoS 攻擊的目標。俄羅斯的加密貨幣公司是遭受攻擊第二多的公司。
更一步瞭解 Cloudflare 如何讓開放式網際網路流量流入俄羅斯,同時避免向外展開攻擊。
DDoS 勒索攻擊
- 我們觀察到新一波 DDoS 勒索攻擊,由自稱 Fancy Lazarus 的實體發出。
- 2022 年 6 月,勒索攻擊達到今年以來的最高水準:每五名經歷過 DDoS 攻擊的問卷調查受訪者中,就有一人報告受到 DDoS 勒索攻擊或其他威脅。
- 整體來說,第二季度 DDoS 勒索攻擊環比增長 11%。
應用程式層 DDoS 攻擊
- 2022 年第二季度,應用程式層 DDoS 攻擊同比增長 44%。
- 位於美國的組織是此類攻擊的主要目標,其次是賽普勒斯、香港和中國。針對賽普勒斯組織的攻擊數環比增長 171%。
- 第二季度,航空和太空產業遭受此類攻擊最多,其次是網際網路產業、銀行業、金融服務業及保險業,而遊戲/博彩業則位居第四。
網路層 DDoS 攻擊
- 2022 年第二季度,網路層 DDoS 攻擊數同比增長 75%。100 Gbps 及以上的攻擊數環比增長 19%,持續 3 小時以上的攻擊數環比增長 9%。
- 遭受此類攻擊最多的產業分別是電信業、遊戲/博彩以及資訊技術和服務業。
- 美國的組織是此類攻擊的主要目標,其次是新加坡、德國和中國。
本報告基於 Cloudflare 的 DDoS 防護系統自動偵測和緩解的 DDoS 攻擊數。如需深入瞭解該系統的運作方式,請查看此深度剖析部落格貼文。
有關我們如何衡量在網路中觀察到的 DDoS 攻擊的說明
為分析攻擊趨勢,我們會計算「DDoS 活動」率,即攻擊流量在我們的全球網路中、特定位置或特定類別(如行業或帳單國家/地區)觀察到的總流量(攻擊流量+潔淨流量)中所佔的百分比。透過衡量這些百分比,我們能夠標準化資料點並避免以絕對數字反映而出現的偏頗,例如,某個 Cloudflare 資料中心接收到更多的總流量,因而發現更多攻擊。
勒索攻擊
我們的系統會持續分析流量,並在偵測到 DDoS 攻擊時自動套用緩解措施。每個受到 DDoS 攻擊的客戶都會收到提示,請求參與一個自動化調查,以幫助我們更好地瞭解該攻擊的性質以及緩解措施的成功率。
兩年多以來,Cloudflare 一直在對受到攻擊的客戶進行調查,調查中的一個問題是,他們是否收到威脅或勒索信,要求付款以換得停止 DDoS 攻擊。
第二季度報告威脅或勒索信的受訪者數量環比和同比增長 11%。在本季度,我們一直在緩解 DDoS 勒索攻擊,這些攻擊由自稱是進階持續威脅 (APT) 組織「Fancy Lazarus」的實體發起的。金融機構和加密貨幣公司成為這起活動的主要目標。

深入探究第二季度,我們可以看到,在 6 月份,每五名受訪者中就有一人報告收到 DDoS 勒索攻擊或威脅 — 這既是 2022 年報告數量最多的月份,也是自 2021 年 12 月以來報告數量最多的月份。

應用程式層 DDoS 攻擊
應用程式層 DDoS 攻擊,特別是 HTTP DDoS 攻擊,旨在通過使 HTTP 伺服器無法處理合法用戶請求來破壞它。如果伺服器收到的請求數量超過其處理能力,伺服器將丟棄合法請求甚至崩潰,導致對合法使用者的服務效能下降或中斷。

應用程式層 DDoS 攻擊:月份分佈
第二季度,應用程式層 DDoS 攻擊數同比增長 44%。
整體來說,在第二季度,應用程式層 DDoS 攻擊數量同比增長 44%,但環比下降 16%。5 月是本季度最繁忙的月份。幾乎 47% 的應用程式層 DDoS 攻擊都發生在 5 月,而 6 月發生的攻擊數最少 (18%)。

應用程式層 DDoS 攻擊:行業分佈
針對航空和太空業的攻擊數環比增長 256%。
第二季度,航空和太空是遭受應用程式層 DDoS 攻擊最多的產業。銀行、金融機構和保險業 (BFSI) 緊隨其後,而遊戲/博彩業則位居第三。

烏克蘭和俄羅斯的網路空間
媒體和出版公司是烏克蘭遭受攻擊最多的公司。
隨著烏克蘭地面、空中和水面戰爭的繼續,網路空間的戰爭也在繼續。將烏克蘭公司作為攻擊目標的實體似乎在試圖掩蓋資訊。烏克蘭遭受攻擊最多的前六大產業均為廣播、網際網路、網路媒體和出版業 — 這幾乎占所有針對烏克蘭的 DDoS 攻擊的 80%。

而戰爭的另一方,俄羅斯的銀行、金融機構和保險 (BFSI) 公司受到的攻擊最多。幾乎 50% 的 DDoS 攻擊的目標都是 BFSI Continue reading
2022년 2분기 DDoS 공격 동향


2022년 2분기 DDoS 보고서에 오신 것을 환영합니다. 이 보고서에는 Cloudflare 네트워크 전반에서 관찰된 DDoS 위협 환경에 대한 인사이트와 동향이 담겨있습니다. 이 보고서의 인터랙티브 버전을 Radar에서도 이용할 수 있습니다.
2분기에 우리는 Cloudflare에서 자동으로 감지하고 대처한 초당 2,600만 회의 요청이 이루어진 HTTPS DDoS 공격을 포함하여 사상 최대 규모의 공격을 경험했습니다. 또한, 우크라이나와 러시아에 대한 공격은 지속되고 있으며, 새로운 랜섬 DDoS 공격이 등장하였습니다.
주요 특징
우크라이나와 러시아에서의 인터넷
- 지상에서의 전쟁은 정보 전파를 겨냥하는 공격과 함께 이루어집니다.
- 2분기에 가장 많은 DDoS 공격이 이루어진 대상은 우크라이나의 방송매체 회사들이었습니다. 실제로, 가장 많은 공격을 받은 상위 6개 산업은 모두 온라인/인터넷 매체, 출판, 방송 분야에 속했습니다.
- 반면, 러시아의 경우 온라인 매체는 가장 많은 공격을 받은 산업 순위에서 3위로 처집니다. 온라인 매체보다 순위가 높은 산업을 보면 러시아의 은행, 금융 서비스 및 보험(BFSI) 회사들이 2분기에 공격을 가장 많이 받았고, 전체 응용 프로그램 계층 DDoS 공격의 거의 50%가 BFSI 분야를 대상으로 했습니다. 두 번째로 공격을 많이 받은 것은 암호화폐 회사들이었습니다.
개방형 인터넷이 러시아로 계속 유입되도록 하고 공격이 외부로 유출되지 않도록 차단하기 위해 Cloudflare에서 어떤 일을 하는지 자세히 읽어보세요.
랜섬 DDoS 공격
- 우리는 팬시 라자러스(Fancy Lazarus)라고 자칭하는 공격자들에 의한 랜섬 DDoS 공격이 급증하는 것을 목격했습니다.
- 2022년 6월에는 랜섬 공격 건수가 올해 들어 최고 수준으로 늘어났습니다. DDoS 공격을 경험한 Continue reading
Tendances en matière d’attaques DDoS au deuxième trimestre 2022


Bienvenue dans notre rapport consacré aux attaques DDoS survenues lors du deuxième trimestre 2022. Ce document présente des tendances et des statistiques relatives au panorama des menaces DDoS, telles qu'observées sur le réseau mondial de Cloudflare. Une version interactive de ce rapport est également disponible sur Radar.
Au cours du deuxième trimestre, nous avons observé certaines des plus vastes attaques jamais enregistrées, notamment une attaque DDoS HTTPS de 26 millions de requêtes par seconde, automatiquement détectée et atténuée par nos soins. Nous avons également constaté la poursuite des attaques contre l'Ukraine et la Russie, de même que l'émergence d'une nouvelle campagne d'attaques DDoS avec demande de rançon.
Points clés
Le réseau Internet russe et ukrainien
- La guerre au sol s'accompagne d'attaques ciblant la diffusion des informations.
- Les entreprises du secteur audiovisuel ukrainien ont été les plus visées par les attaques DDoS au deuxième trimestre. Pour tout dire, les six secteurs les plus attaqués se situent tous dans le domaine des médias en ligne/Internet, de la publication et de l'audiovisuel.
- À l'inverse, en Russie, les médias en ligne reculent de secteur le plus attaqué à la troisième place. Les entreprises du secteur de la banque, des assurances et des Continue reading
Entwicklung der DDoS-Bedrohungslandschaft im zweiten Quartal 2022


Willkommen zu unserem DDoS-Bericht für das zweite Quartal 2022. Darin beschreiben wir Trends hinsichtlich der DDoS-Bedrohungslandschaft, die sich im globalen Cloudflare-Netzwerk beobachten ließen, und die von uns daraus gezogenen Schlüsse. Eine interaktive Version dieses Berichts ist auch bei Radar verfügbar.
Im zweiten Quartal haben wir einige der größten Angriffen aller Zeiten registriert, darunter eine HTTPS-DDoS-Attacke mit 26 Millionen Anfragen pro Sekunde, die von Cloudflare automatisch erkannt und abgewehrt wurde. Neben fortgesetzten Angriffen auf die Ukraine und Russland hat sich zudem eine neue Ransom-DDoS-Angriffskampagne entwickelt.
Die wichtigsten Erkenntnisse auf einen Blick
Das Internet in Russland und der Ukraine
- Der Krieg wird nicht nur physisch, sondern auch in der digitalen Welt ausgefochten. Dort zielen die Angriffe darauf ab, die Verbreitung von Informationen zu verhindern.
- In der Ukraine waren im zweiten Quartal Rundfunk- und Medienunternehmen das häufigste Ziel von DDoS-Angriffen. Tatsächlich sind die sechs am stärkten betroffenen Branchen alle den Bereichen Online-/Internetmedien, Verlagswesen und Rundfunk zuzurechnen.
- Demgegenüber sind in Russland die Online-Medien unter den Angriffszielen auf den dritten Platz zurückgefallen. Spitzenreiter war das Segment Banken, Finanzdienstleistungen und Versicherungen (Banking, Financial Services and Insurance – BFSI). Fast 50 % aller DDoS-Angriffe auf Anwendungsschicht richteten sich gegen diese Sparte. Am zweithäufigsten wurden in Russland Continue reading
Tendencias de los ataques DDoS en el segundo trimestre de 2022


Te damos la bienvenida a nuestro informe sobre los ataques DDoS del segundo trimestre de 2022, que incluye nuevos datos y tendencias sobre el panorama de las amenazas DDoS, según lo observado en la red global de Cloudflare. Puedes consultar la versión interactiva de este informe en Radar.
En el segundo trimestre, hemos observado algunos de los mayores ataques hasta la fecha, incluido un ataque DDoS HTTPS de 26 millones de solicitudes por segundo que Cloudflare detectó y mitigó automáticamente. Además, continúan los ataques contra Ucrania y Rusia, al tiempo que ha aparecido una nueva campaña de ataques DDoS de rescate.
Aspectos destacados
Internet en Ucrania y Rusia
- La guerra en el terreno va acompañada de ataques dirigidos a la difusión de información.
- Las empresas de medios de comunicación de Ucrania fueron el blanco más común de ataques DDoS en el segundo trimestre. De hecho, los seis sectores que recibieron el mayor número de ataques pertenecen a los medios de comunicación en línea/Internet, la edición y audiovisual.
- En Rusia, por el contrario, los medios de comunicación en línea descendieron al tercer lugar como el sector más afectado. En los primeros puestos, las empresas de banca, servicios financieros y seguros (BFSI) Continue reading
Tendências de ataques DDoS no segundo trimestre de 2022


Bem-vindo ao nosso relatório de DDoS do segundo trimestre de 2022. Este relatório inclui informações e tendências sobre o cenário de ameaças DDoS — conforme observado em toda a Rede global da Cloudflare. Uma versão interativa deste relatório também está disponível no Radar.
No segundo trimestre deste ano, aconteceram os maiores ataques da história, incluindo um ataque DDoS por HTTPS de 26 milhões de solicitações por segundo que a Cloudflare detectou e mitigou de forma automática. Além disso, os ataques contra a Ucrânia e a Rússia continuam, ao mesmo tempo em que surgiu uma campanha de ataques DDoS com pedido de resgate.
Destaques
Internet na Ucrânia e na Rússia
- A guerra no terreno é acompanhada por ataques direcionados à distribuição de informações.
- Empresas de mídia de radiodifusão na Ucrânia foram as mais visadas por ataques DDoS no segundo trimestre. Na verdade, todos os seis principais setores vitimados estão na mídia on-line/internet, publicações e radiodifusão.
- Por outro lado, na Rússia, a mídia on-line deixou de ser o setor mais atacado e caiu para o terceiro lugar. No topo, estão empresas como bancos, serviços financeiros e seguros (BFSI, na sigla em inglês) do país, que foram as mais visadas no segundo trimestre; Continue reading
Internet disruptions overview for Q2 2022
Cloudflare operates in more than 270 cities in over 100 countries, where we interconnect with over 10,000 network providers in order to provide a broad range of services to millions of customers. The breadth of both our network and our customer base provides us with a unique perspective on Internet resilience, enabling us to observe the impact of Internet disruptions. In many cases, these disruptions can be attributed to a physical event, while in other cases, they are due to an intentional government-directed shutdown. In this post, we review selected Internet disruptions observed by Cloudflare during the second quarter of 2022, supported by traffic graphs from Cloudflare Radar and other internal Cloudflare tools, and grouped by associated cause or common geography.
Optic outages
This quarter, we saw the usual complement of damage to both terrestrial and submarine fiber-optic cables, including one that impacted multiple countries across thousands of miles, and another more localized outage that was due to an errant rodent.
Comcast
On April 25, Comcast subscribers in nearly 20 southwestern Florida cities experienced an outage, reportedly due to a fiber cut. The traffic impact of this cut is clearly visible in the graph below, with Cloudflare traffic Continue reading
Making Page Shield malicious code alerts more actionable


Last year during CIO week, we announced Page Shield in general availability. Today, we talk about improvements we’ve made to help Page Shield users focus on the highest impact scripts and get more value out of the product. In this post we go over improvements to script status, metadata and categorization.
What is Page Shield?
Page Shield protects website owners and visitors against malicious 3rd party JavaScript. JavaScript can be leveraged in a number of malicious ways: browser-side crypto mining, data exfiltration and malware injection to mention a few.
For example a single hijacked JavaScript can expose millions of user’s credit card details across a range of websites to a malicious actor. The bad actor would scrape details by leveraging a compromised JavaScript library, skimming inputs to a form and exfiltrating this to a 3rd party endpoint under their control.
Today Page Shield partially relies on Content Security Policies (CSP), a browser native framework that can be used to control and gain visibility of which scripts are allowed to load on pages (while also reporting on any violations). We use these violation reports to provide detailed information in the Cloudflare dashboard regarding scripts being loaded by end-user browsers.
Page Shield Continue reading
A July 4 technical reading list


Here’s a short list of recent technical blog posts to give you something to read today.
Internet Explorer, we hardly knew ye
Microsoft has announced the end-of-life for the venerable Internet Explorer browser. Here we take a look at the demise of IE and the rise of the Edge browser. And we investigate how many bots on the Internet continue to impersonate Internet Explorer versions that have long since been replaced.
Live-patching security vulnerabilities inside the Linux kernel with eBPF Linux Security Module
Looking for something with a lot of technical detail? Look no further than this blog about live-patching the Linux kernel using eBPF. Code, Makefiles and more within!
Hertzbleed explained
Feeling mathematical? Or just need a dose of CPU-level antics? Look no further than this deep explainer about how CPU frequency scaling leads to a nasty side channel affecting cryptographic algorithms.
Early Hints update: How Cloudflare, Google, and Shopify are working together to build a faster Internet for everyone
The HTTP standard for Early Hints shows a lot of promise. How much? In this blog post, we dig into data about Early Hints in the real world and show how much faster the web is with it.
Private Continue reading
Optimizing TCP for high WAN throughput while preserving low latency


Here at Cloudflare we're constantly working on improving our service. Our engineers are looking at hundreds of parameters of our traffic, making sure that we get better all the time.
One of the core numbers we keep a close eye on is HTTP request latency, which is important for many of our products. We regard latency spikes as bugs to be fixed. One example is the 2017 story of "Why does one NGINX worker take all the load?", where we optimized our TCP Accept queues to improve overall latency of TCP sockets waiting for accept().
Performance tuning is a holistic endeavor, and we monitor and continuously improve a range of other performance metrics as well, including throughput. Sometimes, tradeoffs have to be made. Such a case occurred in 2015, when a latency spike was discovered in our processing of HTTP requests. The solution at the time was to set tcp_rmem to 4 MiB, which minimizes the amount of time the kernel spends on TCP collapse processing. It was this collapse processing that was causing the latency spikes. Later in this post we discuss TCP collapse processing in more detail.
The tradeoff is that using a low value for Continue reading
Managed Transforms: templated HTTP header modifications
Managed Transforms is the next step on a journey to make HTTP header modification a trivial task for our customers. In early 2021 the only way for Cloudflare customers to modify HTTP headers was by writing a Cloudflare Worker. We heard from numerous customers who wanted a simpler way.
In June 2021 we introduced Transform Rules, giving customers a simple UI letting them specify what the custom HTTP header’s name and value is—either a static string (i.e. X-My-CDN: Cloudflare) or a dynamically populated value (i.e. X-Bot-Score: cf.bot_management.score).
This made the job much simpler, however there is still a good amount of thought required—with a number of potential drop-off points on the user journey. For example, in order to dynamically populate the bot score into the value of an HTTP request header, the user needs to know the correct field name. To find that they'll need to go to the documentation site, find the correct section, etc.
When we analyzed how our customers use Transform Rules we found a set of very common use cases in the data. Four of the top eight fields used were relating to bot management; customers wanting to have the Continue reading
Internet Explorer, we hardly knew ye

On May 19, 2021, a Microsoft blog post announced that “The future of Internet Explorer on Windows 10 is in Microsoft Edge” and that “the Internet Explorer 11 desktop application will be retired and go out of support on June 15, 2022, for certain versions of Windows 10.” According to an associated FAQ page, those “certain versions” include Windows 10 client SKUs and Windows 10 IoT. According to data from Statcounter, Windows 10 currently accounts for over 70% of desktop Windows market share on a global basis, so this “retirement” impacts a significant number of Windows systems around the world.
As the retirement date for Internet Explorer 11 has recently passed, we wanted to explore several related usage trends:
- Is there a visible indication that use is declining in preparation for its retirement?
- Where is Internet Explorer 11 still in the heaviest use?
- How does the use of Internet Explorer 11 compare to previous versions?
- How much Internet Explorer traffic is “likely human” vs. “likely automated”?
- How do Internet Explorer usage patterns compare with those of Microsoft Edge, its replacement?
The long goodbye
Publicly released in January 2020, and automatically rolled out to Windows users starting Continue reading
Live-patching security vulnerabilities inside the Linux kernel with eBPF Linux Security Module

Linux Security Modules (LSM) is a hook-based framework for implementing security policies and Mandatory Access Control in the Linux kernel. Until recently users looking to implement a security policy had just two options. Configure an existing LSM module such as AppArmor or SELinux, or write a custom kernel module.
Linux 5.7 introduced a third way: LSM extended Berkeley Packet Filters (eBPF) (LSM BPF for short). LSM BPF allows developers to write granular policies without configuration or loading a kernel module. LSM BPF programs are verified on load, and then executed when an LSM hook is reached in a call path.
Let’s solve a real-world problem
Modern operating systems provide facilities allowing "partitioning" of kernel resources. For example FreeBSD has "jails", Solaris has "zones". Linux is different - it provides a set of seemingly independent facilities each allowing isolation of a specific resource. These are called "namespaces" and have been growing in the kernel for years. They are the base of popular tools like Docker, lxc or firejail. Many of the namespaces are uncontroversial, like the UTS namespace which allows the host system to hide its hostname and time. Others are complex but straightforward - NET and NS (mount) namespaces Continue reading
Hertzbleed explained


You may have heard a bit about the Hertzbleed attack that was recently disclosed. Fortunately, one of the student researchers who was part of the team that discovered this vulnerability and developed the attack is spending this summer with Cloudflare Research and can help us understand it better.
The first thing to note is that Hertzbleed is a new type of side-channel attack that relies on changes in CPU frequency. Hertzbleed is a real, and practical, threat to the security of cryptographic software.
Should I be worried?
From the Hertzbleed website,
“If you are an ordinary user and not a cryptography engineer, probably not: you don’t need to apply a patch or change any configurations right now. If you are a cryptography engineer, read on. Also, if you are running a SIKE decapsulation server, make sure to deploy the mitigation described below.”
Notice: As of today, there is no known attack that uses Hertzbleed to target conventional and standardized cryptography, such as the encryption used in Cloudflare products and services. Having said that, let’s get into the details of processor frequency scaling to understand the core of this vulnerability.
In short, the Hertzbleed attack shows that, under certain Continue reading
New partner program for SMB agencies & hosting partners now in closed beta

A fundamental principle here at Cloudflare has always been that we want to serve everyone - from individual developers to small businesses to large corporations. In the earliest days, we provided services to hosting partners and resellers around the globe, who helped bring Cloudflare to thousands of domains with free caching and DDoS protection for shared infrastructures.
Today, we want to reinforce our commitment to our hosting ecosystem and small business partners that leverage Cloudflare to help bring a better Internet experience to their customers. We've been building a robust multi-tenant partner platform that we will begin to open up to everyone searching for a faster, safer, and better Internet experience. This platform will come in the form of a Self Serve Partner program that will allow SMB agencies & hosting partners to create accounts for all their customers under one dashboard, consolidate billing, and provide discounted plans to our partners.
Deprecation of our legacy APIs
To make way for the new, we first must discuss the end-of-life of some of Cloudflare’s earliest APIs. Built and launched in 2011, our Hosting and Optimized Partner Programs allowed our initial CDN and DDoS solutions to expand to brand-new audiences around the Continue reading
Network performance update: Cloudflare One Week June 2022

In September 2021, we shared extensive benchmarking results of 1,000 networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on different measures (p95, mean), Cloudflare was the fastest provider in 49% of the top 1,000 networks around the world.
Since then, we’ve expanded our testing to cover not just 1,000 but 3,000 networks, and we’ve worked to continuously improve performance, with the ultimate goal of being the fastest everywhere and an intermediate goal to grow the number of networks where we’re the fastest by at least 10% every Innovation Week. We met that goal Platform Week May 2022), and we’re carrying the work over to Cloudflare One Week (June 2022).
We’re excited to share that Cloudflare was the fastest provider in 1,290 of the top 3,000 most reported networks, up from 1,280 even one month ago during Platform Week.
Measuring what matters
To quantify global network performance, we have to get enough data from around the world, across all manner of different networks, comparing ourselves with other providers. We use Real User Measurements (RUM) to fetch a 100kB file from different providers. Continue reading
Identifying content gaps in our documentation


If you’ve tuned into this blog for long enough, you’ll notice that we’re pretty big on using and stress-testing our own products (“dogfooding”) at Cloudflare.
That applies to our security team, product teams, and – as my colleague Kristian just blogged about – even our documentation team. We’re incredibly excited to be on the Pages platform, both because of the performance and workflow improvements and the opportunity to help the platform develop.
What you probably haven’t heard about is how our docs team uses dogfooding – and data – to improve our documentation.
Dogfooding for docs
As a technical writer, it’s pretty common to do the thing you’re documenting. After all, it’s really hard to write step-by-step instructions if you haven’t been through those steps. It’s also a great opportunity to provide feedback to our product teams.
What’s not as common for a writer, however, is actually using the thing you’re documenting. And it’s totally understandable why. You’re already accountable to your deadlines and product managers, so you might not have the time. You might not have the technical background. And then there’s the whole problem of a real-world use case. If you’re really dedicated, you can set Continue reading