Why I joined Cloudflare in Latin America
This post is also available in Español, Português.
I am excited to announce that I recently joined Cloudflare as Vice President and Managing Director for Latin America. As many of you reading this likely already know, Cloudflare is on a mission to help build a better Internet. And that’s a big part as to why I joined this team — to contribute to this in Latin America specifically and interconnect all across the world. Cloudflare has had a strong presence in Latin America for years. First investing in the region back in 2014, when it expanded its network into Latin America to be closest to the users here — to provide even faster and reliable connections without compromising security. Over the past couple of years, our reliance on the Internet has increased, and Latin America is the fourth largest region in terms of online users globally. You can see how this makes Cloudflare’s mission even more important and presents a significant opportunity in Latin America.
A little about me
Being in the IT industry for two decades, this has shown me the profound impact of technology on everyone's lives. Working within technology for years and seeing the industry evolve, Continue reading
Arkansas engineer wins round 3 of Project Jengo, and Cloudflare continues to win at the Patent Office

We are excited to announce another Project Jengo winner, and provide you with an important update on our fight against Sable Networks.
As a reminder, Project Jengo is Cloudflare’s efforts to flip the incentive structure that has encouraged the growth of patent trolls that seek to leverage overbroad and unpracticed patents to extract settlements from operating entities. We do this by refusing to settle patent cases brought against us by trolls, and instead, use a crowdsourced bounty to identify prior art that undermines the value of the troll’s patents, and not just the ones asserted against Cloudflare. This is the second iteration of Project Jengo, which is focused on a patent troll called Sable.
Even though the case against Sable has been active for over a year now, and we’ve already achieved some great results, we haven’t let up the pressure. We’re now also giving out Cloudflare T-shirts to new Project Jengo participants – all you need to do is submit prior art related to any of the Sable patents this year and the first 100 participants with a U.S. mailing address will receive a Cloudflare t-shirt.
$5,000 to Project Jengo’s round three winner!
We have already awarded $30,000 Continue reading
Tracking shifts in Internet connectivity in Kherson, Ukraine
The Internet is not only a human right according to the United Nations, and a way to get information, but it has also become an important element in geopolitical conflicts, like the war going on in Ukraine. We have previously written about Ukrainians moving westward to escape the war and Internet outages in the country, but also about the importance of the open Internet in Russia.
Over this past week, we observed an outage in the occupied city of Kherson, south Ukraine, coupled with an apparent shift in who controls the Internet within the region. First, let’s give some context and show what we saw.
The Russian-occupied Kherson (a city of 280,000 people) experienced an Internet outage on Saturday, April 30, 2022, that began just after 16:00 UTC. The outage lasted until Wednesday, May 4, with traffic starting to return around 04:30 UTC traffic.
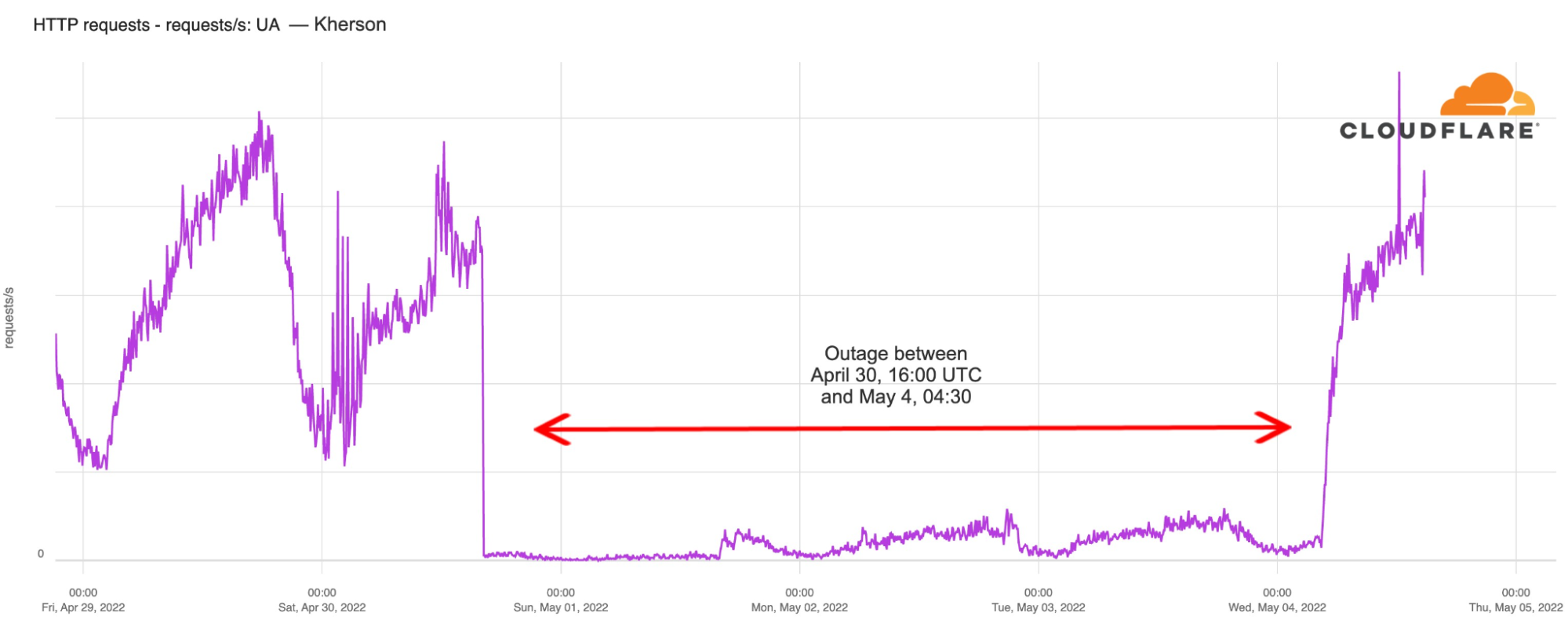
In the chart below, we can see that there was a 43% decrease in traffic from Kherson from February 23 to 24, after the war started. However, this weekend’s outage is the most significant disruption to Internet traffic in Kherson since the start of the war.
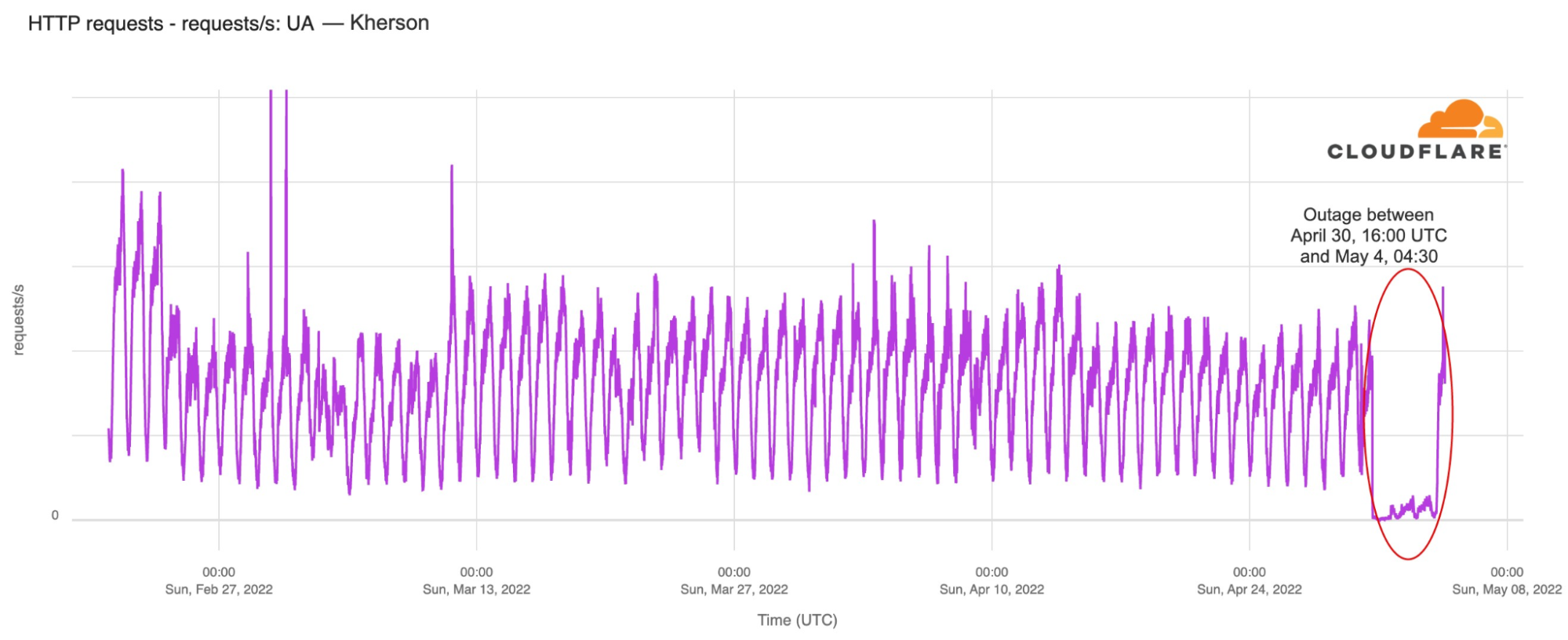
According to Ukraine’s vice Prime-Minister, Mykhailo Fedorov, and Continue reading
The deluge of digital attacks against journalists

“A free press can, of course, be good or bad, but, most certainly without freedom, the press will never be anything but bad.”
― Albert Camus

Since its founding in 1993, World Press Freedom Day has been a time to acknowledge the importance of press freedom and call attention to concerted attempts to thwart journalists’ essential work. That mission is also embedded in the foundations of our Project Galileo, which has a goal of protecting free expression online — after the war in Ukraine started, applications to the project increased by 177% in March 2022 alone.
In Uruguay today, UNESCO’s World Press Freedom Day Global Conference is underway, with a 2022 theme of “Journalism under Digital Siege.”
It is a fitting and timely theme.
While the Internet has limitless potential to make every person a publisher, bad actors — both individuals and governments — routinely deploy attacks to silence free expression. For example, Cloudflare data illustrate a trend of increased cyber attacks since the invasion of Ukraine, and journalists are frequent targets. Covering topics such as war, government corruption, and crime makes journalists vulnerable to aggression online and offline. Beyond the issue of cyber attacks, Russian authorities’ Continue reading
Wildcard proxy for everyone


Today, I have the pleasure to announce that we’re giving everyone the ability to proxy DNS wildcard records. Previously, this feature was only available to our Enterprise customers. After many of our free and pay-as-you-go users reached out, we decided that this feature should be available to everyone.
What is a wildcard DNS record?
A DNS record usually maps a domain name to one or multiple IP addresses or another resource associated with that name, so it’s a one-to-many mapping. Let’s look at an example:
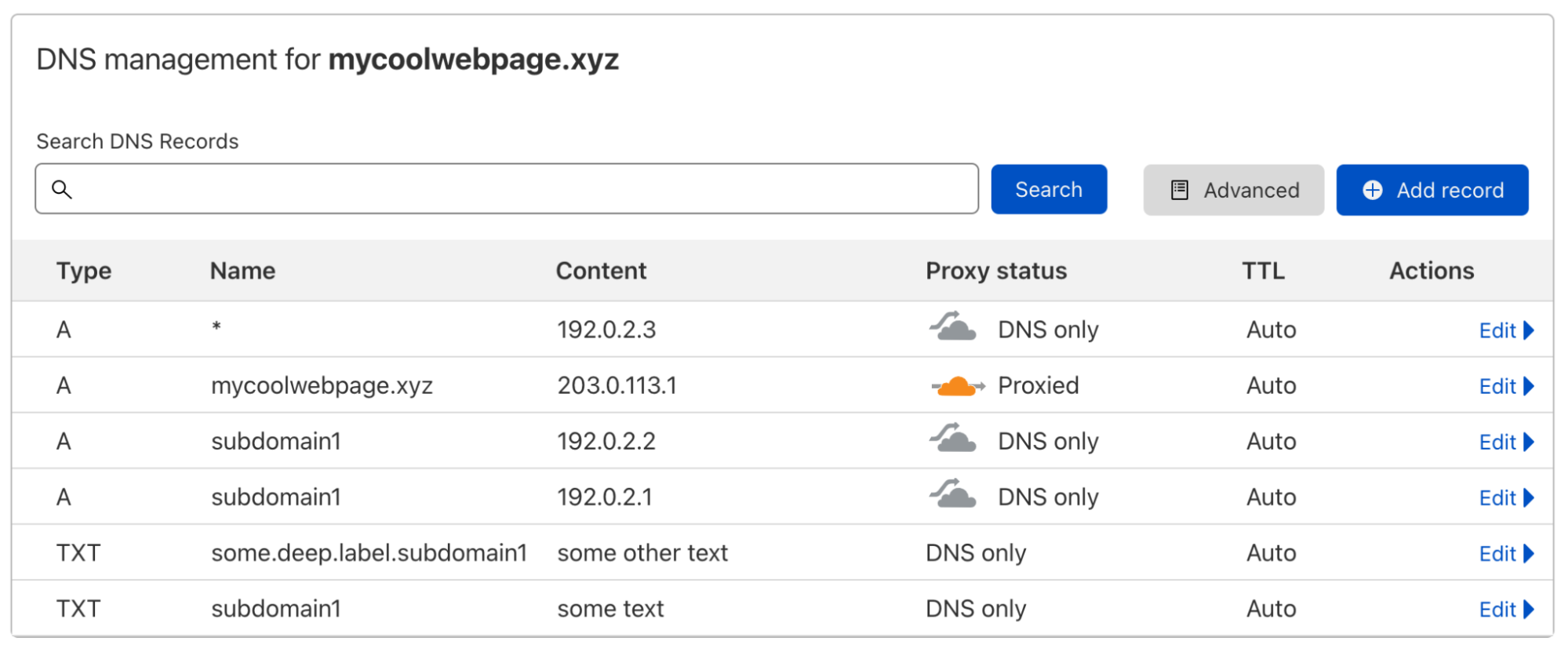
When I do a DNS lookup for the IP address of subdomain1.mycoolwebpage.xyz, I get two IP addresses back, because I have added two A records on that subdomain:
$ dig subdomain1.mycoolwebpage.xyz -t a +short
192.0.2.1
192.0.2.2
I could specify the target of all subdomains like this, with one or multiple DNS records per subdomain. But what if I have hundreds or even thousands of subdomains that I all want to point to the same resource?
This is where a wildcard DNS record comes in. By using the asterisk symbol "*" in the Name field, I can create one or multiple DNS records that are Continue reading
Cloudflare Relay Worker
Our Notification Center offers first class support for a variety of popular services (a list of which are available here). However, even with such extensive support, you may use a tool that isn’t on that list. In that case, it is possible to leverage Cloudflare Workers in combination with a generic webhook to deliver notifications to any service that accepts webhooks.
Today, we are excited to announce that we are open sourcing a Cloudflare Worker that will make it as easy as possible for you to transform our generic webhook response into any format you require. Here’s how to do it.
For this example, we are going to write a Cloudflare Worker that takes a generic webhook response, transforms it into the correct format and delivers it to Rocket Chat, a popular customer service messaging platform. When Cloudflare sends you a generic webhook, it will have the following schema, where “text” and “data” will vary depending on the alert that has fired:
{
"name": "Your custom webhook",
"text": "The alert text",
"data": {
"some": "further",
"info": [
"about",
"your",
"alert",
"in"
],
"json": "format"
},
"ts": 123456789
}Whereas Rocket Chat is looking for this format:
{
"text": "Example Continue readingThe Cloudflare network now spans 275 cities


It was just last month that we announced our network had grown to over 270 cities globally. Today, we’re announcing that with recent additions we’ve reached 275 cities. With each new city we add, we help make the Internet faster, more reliable, and more secure. In this post, we’ll talk about the cities we added, the performance increase, and look closely at our network expansion in India.
The Cities
Here are the four new cities we added in the last month: Ahmedabad, India; Chandigarh, India; Jeddah, Saudi Arabia; and Yogyakarta, Indonesia.
A closer look at India
India is home to one of the largest and most rapidly growing bases of digital consumers. Recognising this, Cloudflare has increased its footprint in India in order to optimize reachability to users within the country.
Cloudflare’s expansion in India is facilitated through interconnections with several of the largest Internet Service Providers (ISPs), mobile network providers and Internet Exchange points (IXPs). At present, we are directly connected to the major networks that account for more than 95% of the country’s broadband subscribers. We are continuously working to not only expand the interconnection capacity and locations with these networks, but also establish Continue reading
Secret Management with HashiCorp Vault

Many applications these days require authentication to external systems with resources, such as users and passwords to access databases and service accounts to access cloud services, and so on. In such cases, private information, like passwords and keys, becomes necessary. It is essential to take extra care in managing such sensitive data. For example, if you write your AWS key information or password in a script for deployment and then push it to a Git repository, all users who can read it will also be able to access it, and you could be in trouble. Even if it's an internal repository, you run the risk of a potential leak.
How we were managing secrets in the service
Before we talk about Vault, let's take a look at how we've used to manage secrets.
Salt
We use SaltStack as a bare-metal configuration management tool. The core of the Salt ecosystem consists of two major components: the Salt Master and the Salt Minion. The configuration state is owned by Salt Master, and thousands of Salt Minions automatically install packages, generate configuration files, and start services to the node based on the state. The state may contain secrets, such as passwords and API Continue reading
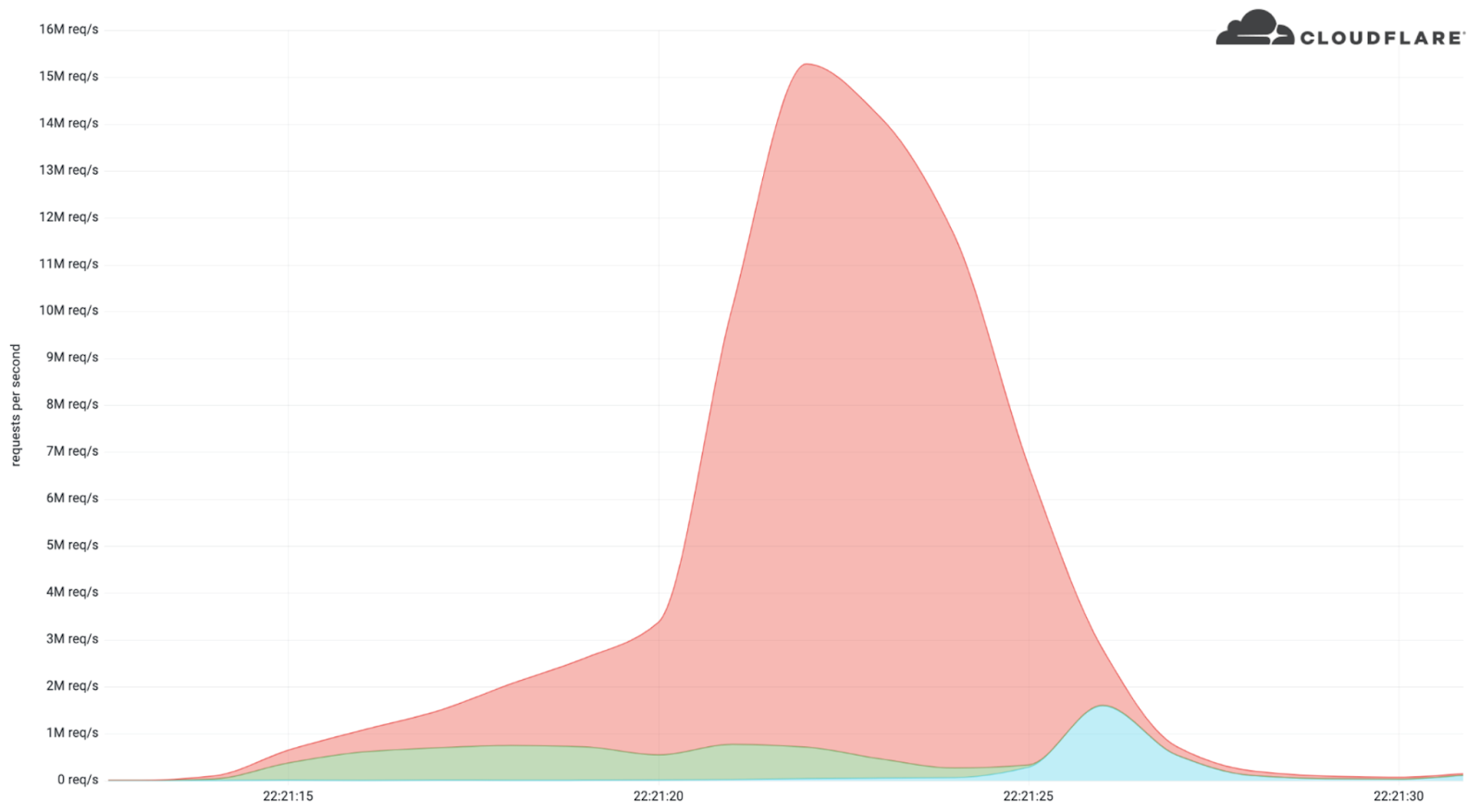
Cloudflare blocks 15M rps HTTPS DDoS attack


Earlier this month, Cloudflare’s systems automatically detected and mitigated a 15.3 million request-per-second (rps) DDoS attack — one of the largest HTTPS DDoS attacks on record.
While this isn’t the largest application-layer attack we’ve seen, it is the largest we’ve seen over HTTPS. HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection. Therefore it costs the attacker more to launch the attack, and for the victim to mitigate it. We’ve seen very large attacks in the past over (unencrypted) HTTP, but this attack stands out because of the resources it required at its scale.
The attack, lasting less than 15 seconds, targeted a Cloudflare customer on the Professional (Pro) plan operating a crypto launchpad. Crypto launchpads are used to surface Decentralized Finance projects to potential investors. The attack was launched by a botnet that we’ve been observing — we’ve already seen large attacks as high as 10M rps matching the same attack fingerprint.
Cloudflare customers are protected against this botnet and do not need to take any action.
The attack
What’s interesting is that the attack mostly came from data centers. We’re Continue reading
Two voting days, a debate and a polling rule in France impacts the Internet
We blogged previously about some trends concerning the first round of the 2022 French presidential election, held on April 10. Here we take a look at the run-off election this Sunday, April 24, that ended up re-electing Emmanuel Macron as President of France.
First, the two main trends: French-language news sites outside France were clearly impacted by the local rule that states that exit polls can only be published after 20:00.
And Internet traffic was similar on both the election days (April 10 and 24) and that includes the increase in use of mobile devices and interest in news websites — there we also saw a clear interest in the Macron-Le Pen debate on April 20.
We have discussed before that election days usually don’t have a major impact on overall Internet traffic. Let’s compare April 10 with 24, the two Sundays when the elections were held. The trends throughout the day are incredibly similar (with a slight increase in traffic on April 24), even with a two-week gap between them.
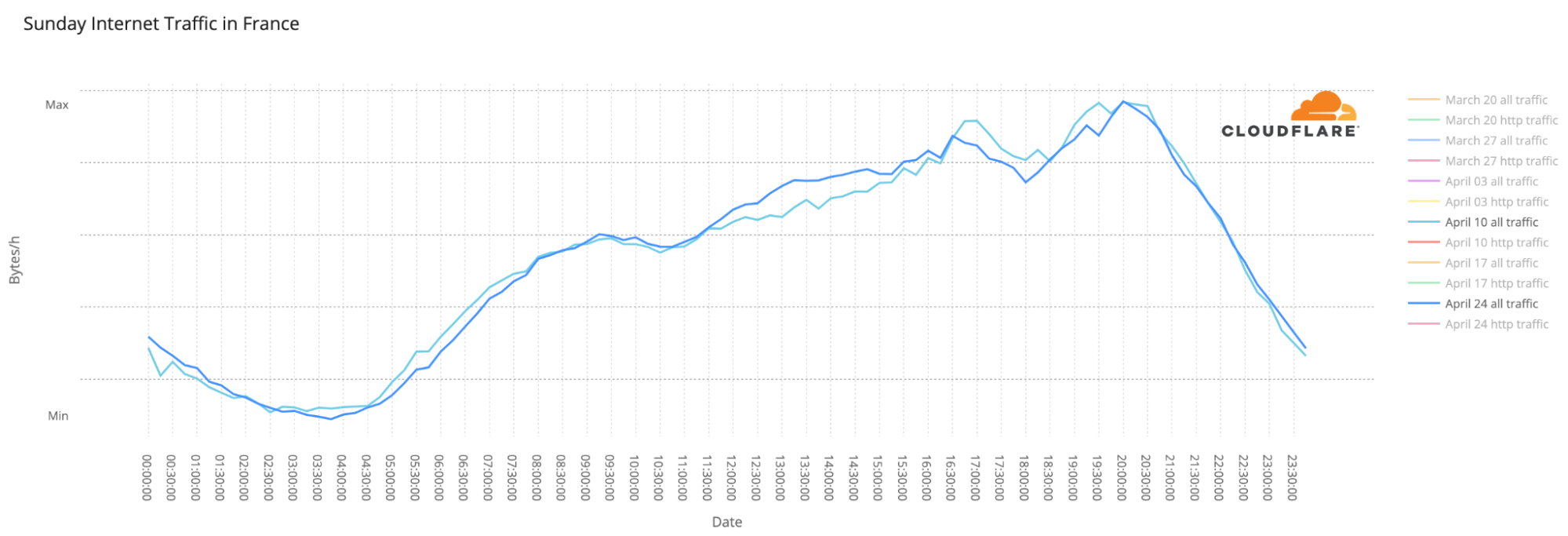
Another election-day trend is the use of mobile devices to access the Internet, mainly at night. The largest spikes in number of requests made using mobile devices in Continue reading
Deux jours de vote, un débat et une réglementation concernant les élections en France impactent l’Internet

Nous avons publié un article de blog consacré à certaines tendances concernant le premier tour de l'élection présidentielle française de 2022, qui s'est déroulé le 10 avril. Nous nous intéressons ici au second tour de l'élection, qui a eu lieu le dimanche 24 avril et a abouti à la réélection d'Emmanuel Macron à la présidence de la France.
Tout d'abord, les deux principales tendances : les sites d'information francophones situés hors de France ont été clairement impactés par la réglementation locale, qui stipule que les estimations ne peuvent être publiées qu'après 20 heures.
Le trafic Internet a été similaire les deux jours de l'élection (les 10 et 24 avril), et cela inclut l'augmentation de l'utilisation des appareils mobiles et l'intérêt pour les sites d'actualités – - là aussi, nous avons constaté un net intérêt pour le débat Macron-Le Pen du 20 avril.
Nous avons déjà évoqué le fait que les jours d'élections n'ont généralement pas un impact majeur sur le trafic Internet global. Comparons les journées des 10 et 24 avril, les deux dimanches où ont eu lieu les élections. Les tendances tout au long de la journée sont incroyablement similaires (avec une légère augmentation du trafic le 24 Continue reading
Building many private virtual networks through Cloudflare Zero Trust
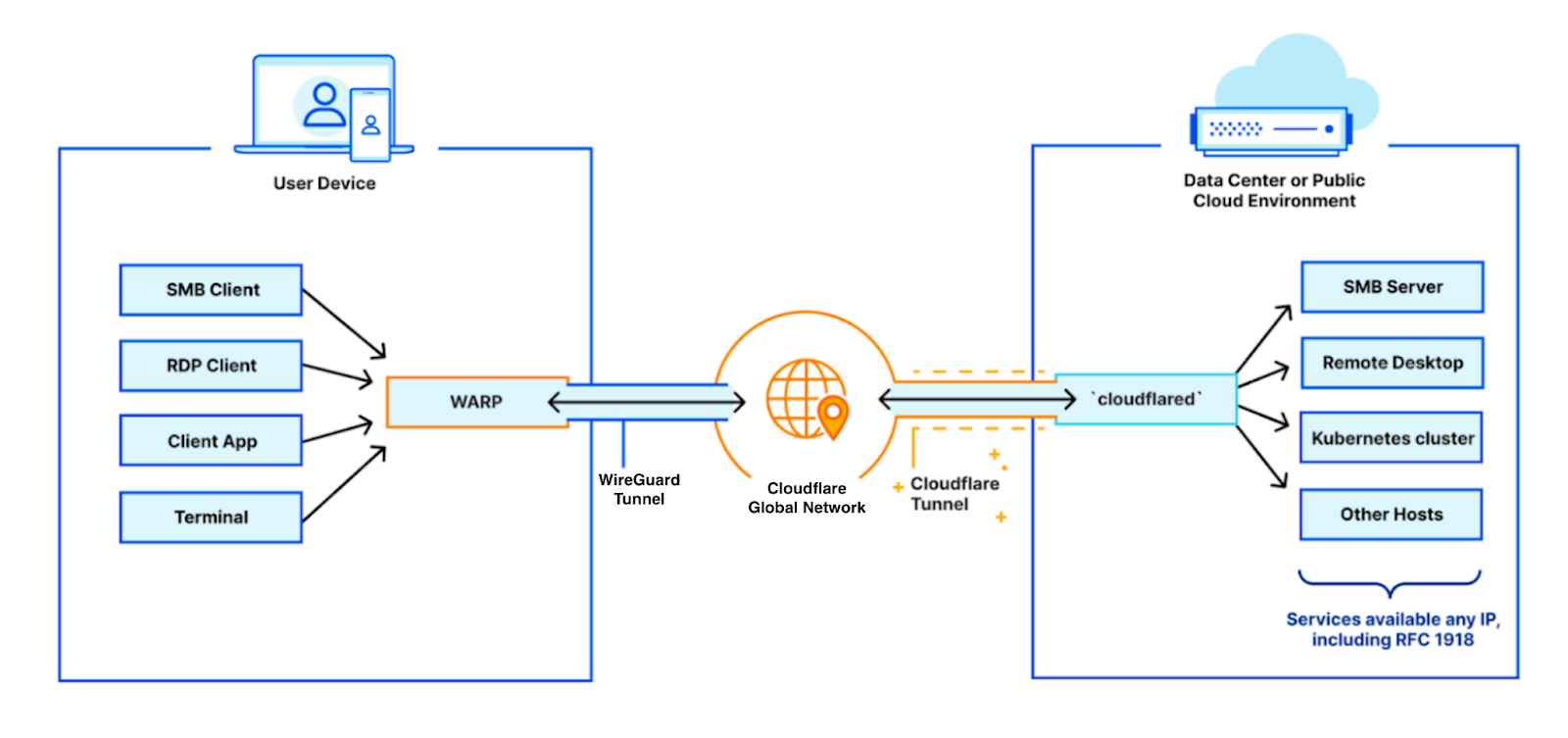
We built Cloudflare’s Zero Trust platform to help companies rely on our network to connect their private networks securely, while improving performance and reducing operational burden. With it, you could build a single virtual private network, where all your connected private networks had to be uniquely identifiable.
Starting today, we are thrilled to announce that you can start building many segregated virtual private networks over Cloudflare Zero Trust, beginning with virtualized connectivity for the connectors Cloudflare WARP and Cloudflare Tunnel.
Connecting your private networks through Cloudflare
Consider your team, with various services hosted across distinct private networks, and employees accessing those resources. More than ever, those employees may be roaming, remote, or actually in a company office. Regardless, you need to ensure only they can access your private services. Even then, you want to have granular control over what each user can access within your network.
This is where Cloudflare can help you. We make our global, performant network available to you, acting as a virtual bridge between your employees and private services. With your employees’ devices running Cloudflare WARP, their traffic egresses through Cloudflare’s network. On the other side, your private services are behind Cloudflare Tunnel, accessible Continue reading
Marcelo Affonso and Rebecca Weekly: Why we joined Cloudflare


Marcelo Affonso (VP of Infrastructure Operations) and Rebecca Weekly (VP of Hardware Systems) recently joined our team. Here they share their journey to Cloudflare, what motivated them to join us, and what they are most excited about.
Marcelo Affonso - VP of Infrastructure Operations
I am thrilled to join Cloudflare and lead our global infrastructure operations. My focus will be building, expanding, optimizing, and accelerating Cloudflare’s fast-growing infrastructure presence around the world.
Recently, I have found myself reflecting on how central the Internet has become to the lives of people all over the world. We use the Internet to work, to connect with families and friends, and to get essential services. Communities, governments, businesses, and cultural institutions now use the Internet as a primary communication and collaboration layer.
But on its own, the Internet wasn’t architected to support that level of use. It needs better security protections, faster and more reliable connectivity, and more support for various privacy preferences. What’s more, those benefits can’t just be available to large businesses. They need to be accessible to a full range of communities, governments, and individuals who now rely on the Internet. And they need to be accessible in various ways to Continue reading
Email Routing Insights


Have you ever wanted to try a new email service but worried it might lead to you missing any emails? If you have, you’re definitely not alone. Some of us email ourselves to make sure it reaches the correct destination, others don’t rely on a new address for anything serious until they’ve seen it work for a few days. In any case, emails often contain important information, and we need to trust that our emails won’t get lost for any reason.
To help reduce these worries about whether emails are being received and forwarded - and for troubleshooting if needed - we are rolling out a new Overview page to Email Routing. On the Overview tab people now have full visibility into our service and can see exactly how we are routing emails on their behalf.
Routing Status and Metrics
The first thing you will see in the new tab is an at a glance view of the service. This includes the routing status (to know if the service is configured and running), whether the necessary DNS records are configured correctly, and the number of custom and destination addresses on the zone.
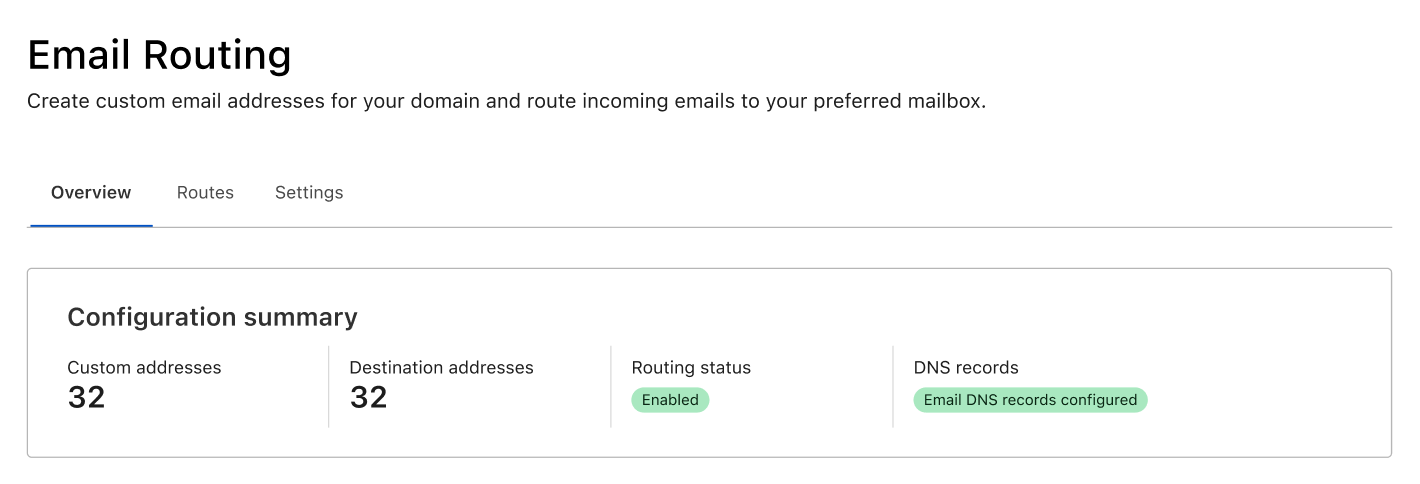
Below the configuration summary, you will see more Continue reading
Happy Earth Day: Announcing Green Compute open beta


At Cloudflare, we are on a mission to help build a better Internet. We continue to grow our network, and it is important for us to do so responsibly.
Since Earth Day 2021, some pieces of this effort have included:
- Making a commitment to powering our network with 100% renewable energy
- Hosting our first Impact Week
- Releasing our first Impact Report and emissions inventory report
- Reducing the environmental impact of web searches via Crawler Hints
- Providing customers with visibility about their Scope 3 emissions with Carbon Impact Reports
And we are just getting started. We are working to make the Cloudflare network — and our customers’ websites, applications, and networks — as efficient as possible in terms of design, hardware, systems, and protocols. After all, we do not want to lose sight of our responsibilities to our home: our planet Earth.
Green Compute for Workers Cron Triggers
During Impact Week last year, we began testing Green Compute in a closed beta. Green Compute makes Workers Cron Triggers run only in facilities that are powered by renewable energy. We are hoping to incentivize more facilities to implement responsible climate and energy policies.
With Green Compute enabled, Workers Cron Triggers will run Continue reading
US Tax Day 2022. How leaving it to the last day impacts tax sites

“Our new Constitution is now established, and has an appearance that promises permanency; but in this world nothing can be said to be certain, except death and taxes.”
— Benjamin Franklin, in a letter to Jean-Baptiste Le Roy, 1789

The famous expression highlighting that only “death and taxes” seem certain in life (something that goes back to the beginning of civilization and to Ancient Egypt) is on people’s minds during the month of April in the United States. This past Monday, April 18, 2022, was Tax Day. So, were US citizens procrastinators, leaving their federal (and state) tax returns to the last day? Traffic to tax-related official federal and state websites seems to show it: there was a spike of more than 470% on April 18.
Just for reference, we can see on Cloudflare Radar that Internet traffic in the US, from our perspective, wasn’t significantly impacted on Monday, April 18, although there was a clear peak, higher than in the previous 14 days, that night at 22:00 EST (that’s 02:00 UTC on April 19). So, traffic (that includes DNS and HTTP requests from our standpoint) was 18% higher compared to the same time on the previous Continue reading
Breaking down broadband nutrition labels


As part of the recently passed Infrastructure Investment and Jobs Act (Infrastructure Act) in the United States, Congress asked the Federal Communications Commission (FCC) to finalize rules that would require broadband Internet access service providers (ISPs) display a “label” that provides consumers with a simple layout that discloses prices, introductory rates, data allowances, broadband performance, management practices, and more.
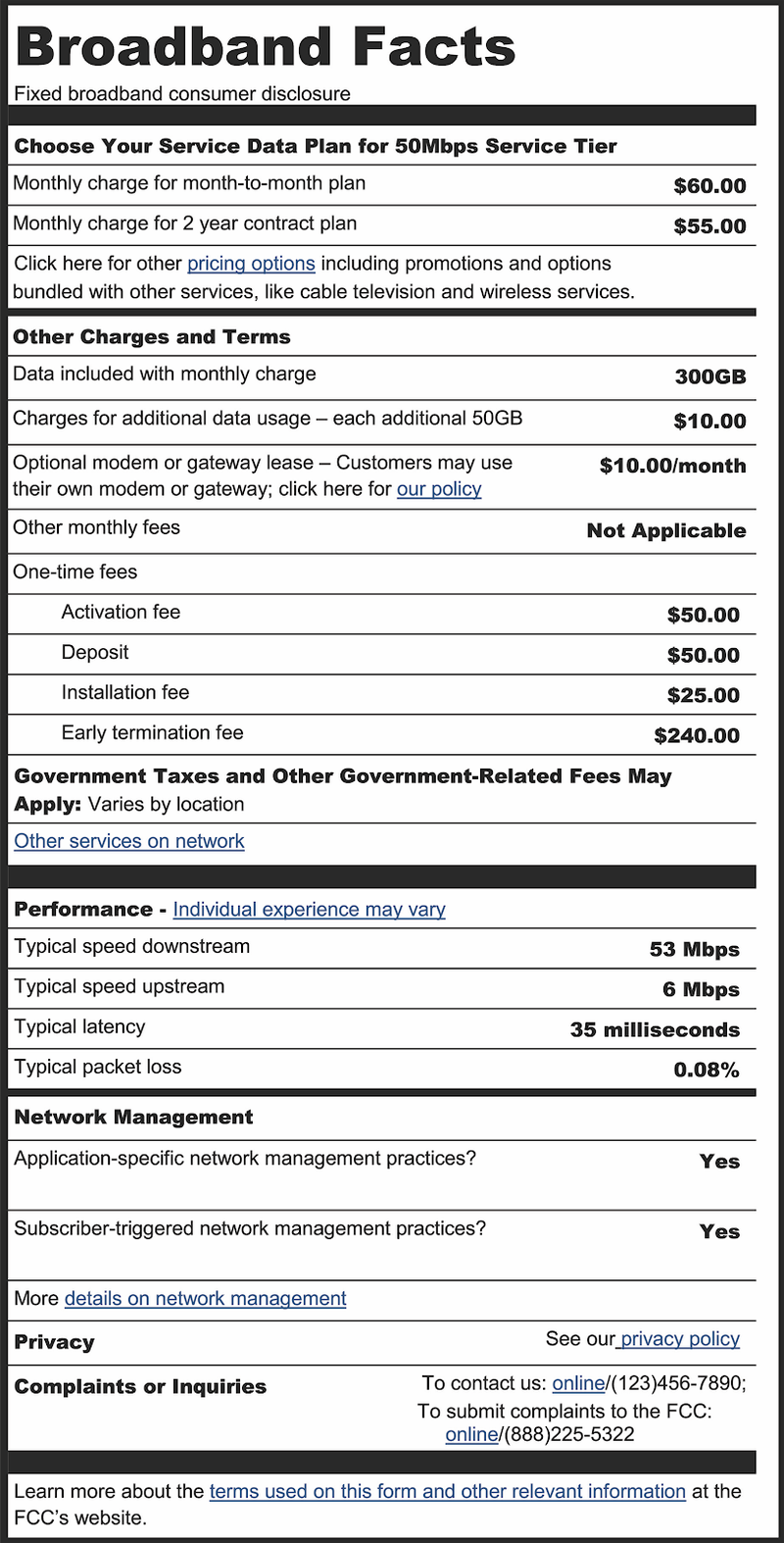
While the idea of a label is not new (the original design dates from 2016), its inclusion in the Infrastructure Act has reinvigorated the effort to provide consumers with information sufficient to enable them to make informed choices when purchasing broadband service. The FCC invited the public to submit comments on the existing label, and explain how the Internet has changed since 2016. We’re sharing Cloudflare’s comments here as well to call attention to this opportunity to make essential information accessible, accurate, and transparent to the consumer. We encourage you to read our full comments. (All comments, from Cloudflare and others, are available for public consumption on the FCC website.)
The Internet, 6 years ago
Six years can change a lot of things, and the Internet is Continue reading
Cloudflare partners with Kentik to enhance on-demand DDoS protection

We are excited to announce that as of today, network security teams can procure and use Magic Transit, Cloudflare’s industry-leading DDoS mitigation solution, and Kentik’s network observability as an integrated solution. We are excited to help our customers not just with technical simplicity, but business process simplicity as well.

Why monitoring and mitigation?
Distributed Denial of Service (DDoS) attacks are highly disruptive to businesses everywhere. According to the Cloudflare DDoS Attack Trends report, in the first half of 2021 the world witnessed massive ransomware and ransom DDoS attack campaigns that interrupted critical infrastructure, including oil pipelines, healthcare, and financial services. In the second half, we saw a growing swarm of attacks, including one of the most powerful botnets deployed (Meris), with record-breaking network-layer attacks observed on the Cloudflare network.
Along with an increase in severity, there is a proliferation of automated toolkits that make it simple and cheap for anyone to launch these attacks. Detecting and stopping these attacks manually is not effective, and network security engineers are increasingly turning to automated tools to help ensure network and application availability.
DDoS protection has evolved over the years from appliances to hybrid models to fully Internet-native solutions, like Continue reading
DDoS Attack Trends for 2022 Q1

This post is also available in 日本語, Deutsch and Français.

Welcome to our first DDoS report of 2022, and the ninth in total so far. This report includes new data points and insights both in the application-layer and network-layer sections — as observed across the global Cloudflare network between January and March 2022.
The first quarter of 2022 saw a massive spike in application-layer DDoS attacks, but a decrease in the total number of network-layer DDoS attacks. Despite the decrease, we’ve seen volumetric DDoS attacks surge by up to 645% QoQ, and we mitigated a new zero-day reflection attack with an amplification factor of 220 billion percent.
In the Russian and Ukrainian cyberspace, the most targeted industries were Online Media and Broadcast Media. In our Azerbaijan and Palestinian Cloudflare data centers, we’ve seen enormous spikes in DDoS activity — indicating the presence of botnets operating from within.
The Highlights
The Russian and Ukrainian cyberspace
- Russian Online Media companies were the most targeted industries within Russia in Q1. The next most targeted was the Internet industry, then Cryptocurrency, and then Retail. While many attacks that targeted Russian Cryptocurrency companies originated in Ukraine or the US, another major source of attacks Continue reading
The 2022 French Presidential election leaves its mark on the Internet


The first round of the 2022 French presidential elections were held this past Sunday, April 10, 2022, and a run-off will be held on April 24 between the top two candidates, Emmanuel Macron and Marine Le Pen. Looking at Internet trends in France for Sunday, it appears that when people were voting Internet traffic went down, and, no surprise, it went back up when results are coming in — that includes major spikes to news and election-related websites.
Cloudflare Radar data shows that Sundays are usually high-traffic days in France. But this Sunday looked a little different.
The seven-day Radar chart shows that there was a decrease in traffic compared to the previous Sunday between 08:00 and 16:00 UTC, that’s 10:00 and 18:00 in local time — bear in mind that polling stations in France were open between 08:00 and 19:00 (or 20:00 in big cities) local time. So, the decrease in traffic was ‘inside’ the period when French citizens were allowed to vote.
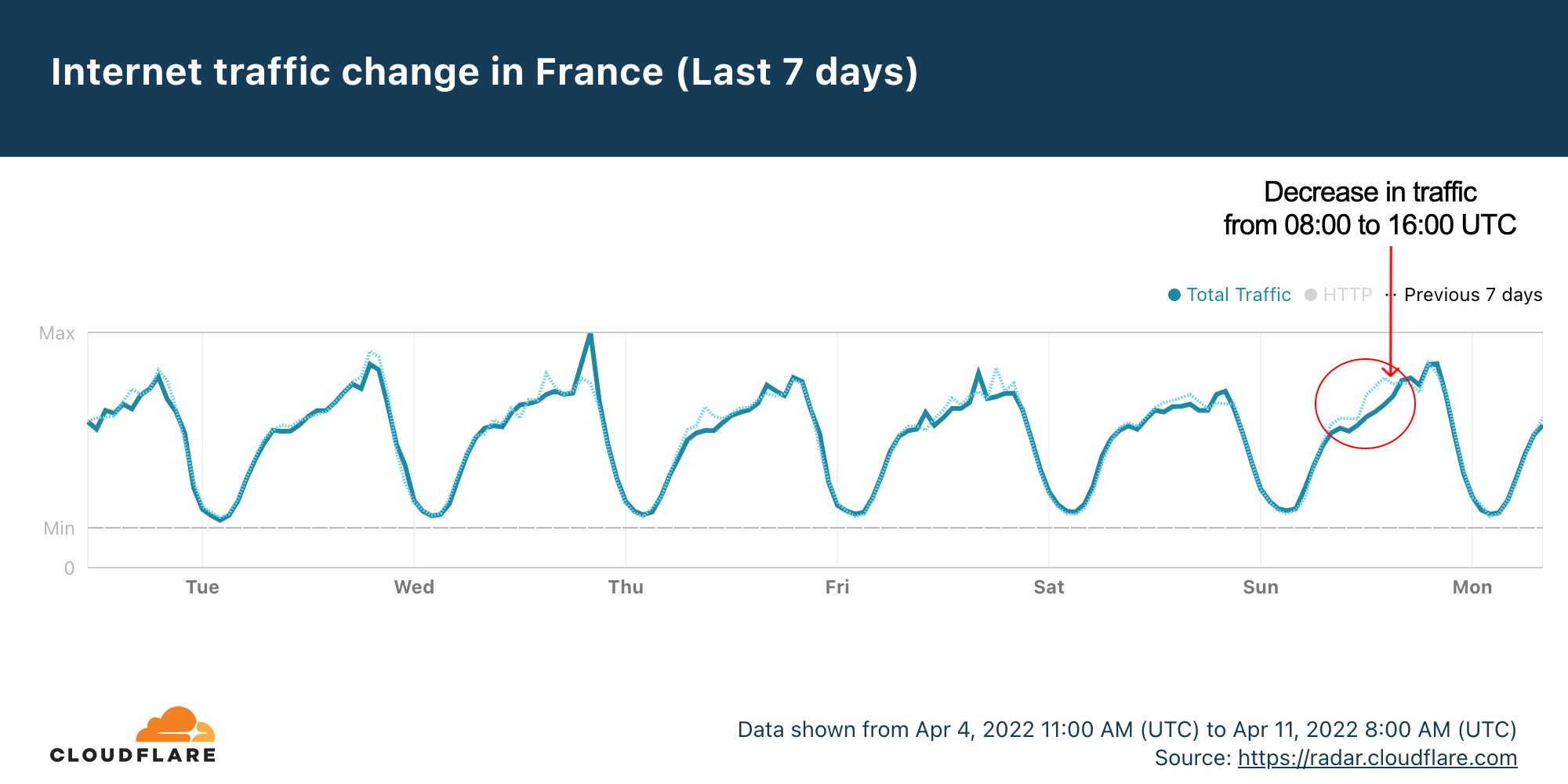
That’s a similar trend we have seen in other elections, like the Portuguese one back in January 2022.
The time of the French election day with the largest difference compared to the previous Sunday was 14:00 Continue reading