Crawler Hints: How Cloudflare Is Reducing The Environmental Impact Of Web Searches
Cloudflare is known for innovation, for needle-moving projects that help make the Internet better. For Impact Week, we wanted to take this approach to innovation and apply it to the environmental impact of the Internet. When it comes to tech and the environment, it’s often assumed that the only avenue tech has open to it is harm mitigation: for example, climate credits, carbon offsets, and the like. These are undoubtedly important steps, but we wanted to take it further — to get into harm reduction. So we asked — how can the Internet at large use less energy and be more thoughtful about how we expend computing resources in the first place?
Cloudflare has a global view into the traffic of the Internet. More than 1 in 6 websites use our network, and we observe the traffic flowing to and from them continuously. While most people think of surfing the Internet as a very human activity, nearly half of all traffic on the global network is generated by automated systems.
We've analyzed this automated traffic, from so-called “bots,” in order to understand the environmental impact. Most of the bot traffic is malicious. Cloudflare protects our clients from this malicious traffic Continue reading
Introducing Smart Edge Revalidation
Today we’re excited to announce Smart Edge Revalidation. It was designed to ensure that compute resources are synchronized efficiently between our edge and a browser. Right now, as many as 30% of objects cached on Cloudflare’s edge do not have the HTTP response headers required for revalidation. This can result in unnecessary origin calls. Smart Edge Revalidation fixes this: it does the work to ensure that these headers are present, even when an origin doesn’t send them to us. The advantage of this? There’s less wasted bandwidth and compute for objects that do not need to be redownloaded. And there are faster browser page loads for users.
So What Is Revalidation?
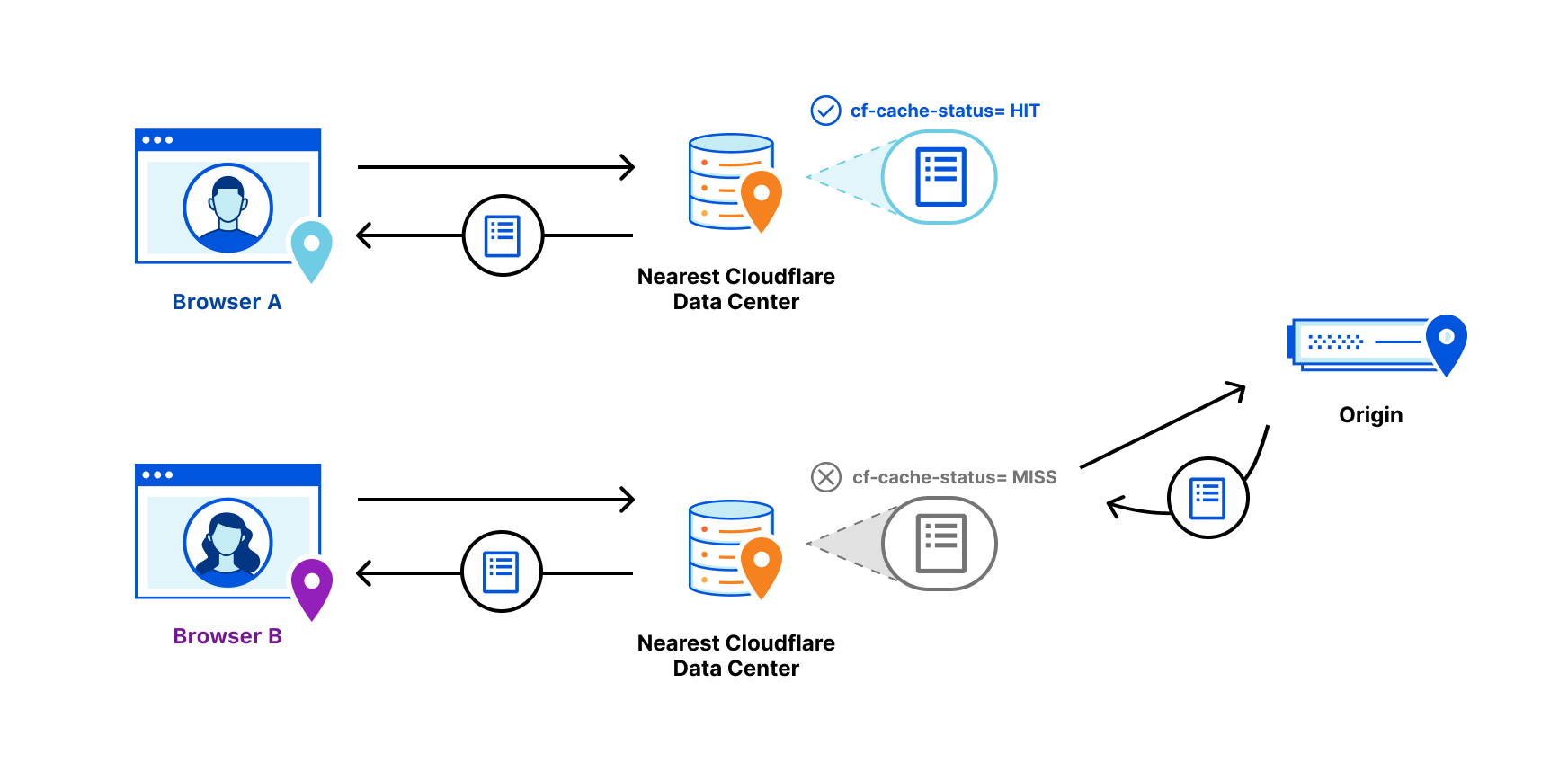
Revalidation is one part of a longer story about efficiently serving objects that live on an origin server from an intermediary cache. Visitors to a website want it to be fast. One foundational way to make sure that a website is fast for visitors is to serve objects from cache. In this way, requests and responses do not need to transit unnecessary parts of the Internet back to an origin and, instead, can be served from a data center that is closer to the visitor. As such, website operators Continue reading
Helping build a green Internet


When we started Cloudflare, we weren't thinking about minimizing the environmental impact of the Internet. Frankly, I didn't really think of the Internet as having much of an environmental impact. It was just this magical resource that gave access to information and services from anywhere.
But that was before I started racking servers in hyper-cooled data centers. Before Cloudflare started paying the bills to keep those servers powered up and cooled down. Before we became obsessed with maximizing the number of requests we could process per watt of power. And long before we started buying directly from renewable power suppliers to drive down the cost of electricity across our network.
Today, I have a very good understanding of how much power it takes to run the Internet. It therefore wasn't surprising to read the Boston Consulting Group study which found that 2% of all carbon output, about 1 billion metric tons per year, is attributable to the Internet. That’s the equivalent of the entire aviation industry.
Cloudflare: Accidentally Environmentally Friendly By Design
While we didn't set out to reduce the environmental impact of the Internet, Cloudflare has always had efficiency at its core. It comes from our ongoing fight with Continue reading
Announcing Green Compute on Cloudflare Workers
All too often we are confronted with the choice to move quickly or act responsibly. Whether the topic is safety, security, or in this case sustainability, we’re asked to make the trade off of halting innovation to protect ourselves, our users, or the planet. But what if that didn’t always need to be the case? At Cloudflare, our goal is to bring sustainable computing to you without the need for any additional time, work, or complexity.
Enter Green Compute on Cloudflare Workers.
Green Compute can be enabled for any Cron triggered Workers. The concept is simple: when turned on, we’ll take your compute workload and run it exclusively on parts of our edge network located in facilities powered by renewable energy. Even though all of Cloudflare’s edge network is powered by renewable energy already, some of our data centers are located in third-party facilities that are not 100% powered by renewable energy. Green Compute takes our commitment to sustainability one step further by ensuring that not only our network equipment but also the building facility as a whole are powered by renewable energy. There are absolutely no code changes needed. Now, whether you need to update a leaderboard every five Continue reading
Designing Edge Servers with Arm CPUs to Deliver 57% More Performance Per Watt


Cloudflare has millions of free customers. Not only is it something we’re incredibly proud of in the context of helping to build a better Internet — but it’s something that has made the Cloudflare service measurably better. One of the ways we’ve benefited is that it’s created a very strong imperative for Cloudflare to maintain a network that is as efficient as possible. There’s simply no other way to serve so many free customers.
In the spirit of this, we are very excited about the latest step in our energy-efficiency journey: turning to Arm for our server CPUs. It has been a long journey getting here — we started testing our first Arm CPUs all the way back in November 2017. It’s only recently, however, that the quantum of energy efficiency improvement from Arm has become clear. Our first Arm CPU was deployed in production earlier this month — July 2021.
Our most recently deployed generation of edge servers, Gen X, used AMD Rome CPUs. Compared with that, the newest Arm based CPUs process an incredible 57% more Internet requests per watt. While AMD has a sequel, Milan (and which Cloudflare will also be deploying), it doesn’t achieve the same Continue reading
Cloudflare: 100% Renewable & Zeroing Out Emissions Back to Day 1


As we announced this week, Cloudflare is helping to create a clean slate for the Internet. Our goal is simple: help build a better, greener Internet with no carbon emissions that is powered by renewable energy.
To help us get there, Cloudflare is making two announcements. The first is that we're committed to powering our network with 100% renewable energy. This builds on work we started back in 2018, and we think is clearly the right thing to do. We also believe it will ultimately lead to more efficient, more sustainable, and potentially cheaper products for our customers.
The second is that by 2025 Cloudflare aims to remove all greenhouse gases emitted as the result of powering our network since our launch in 2010. As we continue to improve the way we track and mitigate our carbon footprint, we want to help the Internet begin with a fresh start.
Finally, as part of our effort to track and mitigate our emissions, we're also releasing our first annual carbon emissions inventory report. The report will provide detail on exactly how we calculate our carbon emissions as well as our renewable energy purchases. Transparency is one of Cloudflare's core values. It's how Continue reading
Green Hosting with Cloudflare Pages

At Cloudflare, we are continuing to expand our sustainability initiatives to build a greener Internet in more than one way. We are seeing a shift in attitudes towards eco-consciousness and have noticed that with all things considered equal, if an option to reduce environmental impact is available, that’s the one widely preferred by our customers. With Pages now Generally Available, we believe we have the power to help our customers reach their sustainability goals. That is why we are excited to partner with the Green Web Foundation as we commit to making sure our Pages infrastructure is powered by 100% renewable energy.
The Green Web Foundation
As part of Cloudflare’s Impact Week, Cloudflare is proud to announce its collaboration with the Green Web Foundation (GWF), a not-for-profit organization with the mission of creating an Internet that one day will run on entirely renewable energy. GWF maintains an extensive and globally categorized Green Hosting Directory with over 320 certified hosts in 26 countries! In addition to this directory, the GWF also develops free online tools, APIs and open datasets readily available for companies looking to contribute to its mission.
What does it mean to be a Green Web Foundation partner?
Understand and reduce your carbon impact with Cloudflare


Today, as part of Cloudflare’s Impact Week, we’re excited to announce a new tool to help you understand the environmental impact of operating your websites, applications, and networks. Your Carbon Impact Report, available today for all Cloudflare accounts, will outline the carbon savings of operating your Internet properties on Cloudflare’s network.
Everyone has a role to play in reducing carbon impact and reversing climate change. We shared today how we’re approaching this, by committing to power our network with 100% renewable energy. But we’ve also heard from customers that want more visibility into the impact of the tools they use (also referred to as “Scope 3” emissions) — and we want to help!
The impact of running an Internet property
We’ve previously blogged about how Internet infrastructure affects the environment. At a high level, powering hardware (like servers) uses energy. Depending on its source, producing this energy may involve emitting carbon into the atmosphere, which contributes to climate change.
When you use Cloudflare, we use energy to power hardware to deliver content for you. But how does that energy we use compare to the energy it would take to deliver content without Cloudflare? As of today, you can go Continue reading
Understanding Where the Internet Isn’t Good Enough Yet


Since March 2020, the Internet has been the trusty sidekick that’s helped us through the pandemic. Or so it seems to those of us lucky enough to have fast, reliable (and often cheap) Internet access.
With a good connection you could keep working (if you were fortunate enough to have a job that could be done online), go to school or university, enjoy online entertainment like streaming movies and TV, games, keep up with the latest news, find out vital healthcare information, schedule a vaccination and stay in contact with loved ones and friends with whom you’d normally be spending time in person.
Without a good connection though, all those things were hard or impossible.
Sadly, access to the Internet is not uniformly distributed. Some have cheap, fast, low latency, reliable connections, others have some combination of expensive, slow, high latency and unreliable connections, still others have no connection at all. Close to 60% of the world have Internet access leaving a huge 40% without it at all.
This inequality of access to the Internet has real-world consequences. Without good access it is so much harder to communicate, to get vital information, to work and to study. Inequality of access Continue reading
Why I joined Cloudflare — and why I’m excited about Project Pangea


If you are well-prepared to take up the challenge, you will get to experience a moment where you are stepping forward to help build a better world. Personally, I felt exactly that when about a month ago, after a long and (COVID) complicated visa process, I joined Cloudflare as a Systems Engineer in Austin, Texas.
In the early 2000s, I experienced while travelling throughout the Benin Republic (my home country) and West Africa more generally, how challenging accessing the Internet was. I recall that, as students, we were often connecting to the web from cybercafés through limited bandwidth purchased at high cost. It was a luxury to have a broadband connection at home. When access was free (say, from high school premises or at university) we still had bandwidth constraints, and often we could not connect for long. The Internet can efficiently help tackle issues encountered (in areas like education, health, communications, ...) by populations in similar regions, but the lack of easy and affordable access, made it difficult to leverage. It is in such a context that I chose to pursue my studies in telecoms, with the hope of being able to somehow give back to the community by Continue reading
Announcing Project Pangea: Helping Underserved Communities Expand Access to the Internet For Free
Half of the world’s population has no access to the Internet, with many more limited to poor, expensive, and unreliable connectivity. This problem persists despite large levels of public investment, private infrastructure, and effort by local organizers.
Today, Cloudflare is excited to announce Project Pangea: a piece of the puzzle to help solve this problem. We’re launching a program that provides secure, performant, reliable access to the Internet for community networks that support underserved communities, and we’re doing it for free1 because we want to help build an Internet for everyone.
What is Cloudflare doing to help?
Project Pangea is Cloudflare’s project to help bring underserved communities secure connectivity to the Internet through Cloudflare’s global and interconnected network.
Cloudflare is offering our suite of network services — Cloudflare Network Interconnect, Magic Transit, and Magic Firewall — for free to nonprofit community networks, local networks, or other networks primarily focused on providing Internet access to local underserved or developing areas. This service would dramatically reduce the cost for communities to connect to the Internet, with industry leading security and performance functions built-in:
- Cloudflare Network Interconnect provides access to Cloudflare’s edge in 200+ cities across the globe through Continue reading
Introducing Flarability, Cloudflare’s Accessibility Employee Resource Group


Hello, folks! I’m pleased to introduce myself and Cloudflare’s newest Employee Resource Group (ERG), Flarability, to the world. The 31st anniversary of the signing of the Americans with Disabilities Act (ADA), which happens to fall during Cloudflare’s Impact Week, is an ideal time to raise the subject of accessibility at Cloudflare and around the world.
There are multiple accessibility-related projects and programs at Cloudflare, including office space accessibility and website and product accessibility programs, some of which we will highlight in the stories below. I wanted to share my accessibility story and the story of the birth and growth of our accessibility community with you.
About Flarability
Flarability began with a conversation between a couple of colleagues, almost two years ago. Some of us had noticed some things about the workspace that weren't as inclusive of people with disabilities as they could have been. For example, the open floor plan in our San Francisco office, as well as the positioning of our interview rooms, made it difficult for some to concentrate in the space. To kick off a community discussion, we formed a chat room, spread the word about our existence, and started hosting some meetings for Continue reading
Welcome to Cloudflare Impact Week


If I'm completely honest, Cloudflare didn't start out as a mission-driven company. When Lee, Michelle, and I first started thinking about starting a company in 2009 we saw an opportunity as the world was shifting from on-premise hardware and software to services in the cloud. It seemed inevitable to us that the same shift would come to security, performance, and reliability services. And, getting ahead of that trend, we could build a great business.

One problem we had was that we knew in order to have a great business we needed to win large organizations with big IT budgets as customers. And, in order to do that, we needed to have the data to build a service that would keep them safe. But we only could get data on security threats once we had customers. So we had a chicken and egg problem.
Our solution was to provide a basic version of Cloudflare's services for free. We reasoned that individual developers and small businesses would sign up for the free service. We'd learn a lot about security threats and performance and reliability opportunities based on their traffic data. And, Continue reading
Cloudflare’s Handling of an RCE Vulnerability in cdnjs


cdnjs provides JavaScript, CSS, images, and fonts assets for websites to reference with more than 4,000 libraries available. By utilizing cdnjs, websites can load faster with less strain on one’s own origin server as files are served directly from Cloudflare’s edge. Recently, a blog post detailed a vulnerability in the way cdnjs’ backend automatically keeps the libraries up to date.
This vulnerability allowed the researcher to execute arbitrary code, granting the ability to modify assets. This blog post details how Cloudflare responded to this report, including the steps we took to block exploitation, investigate potential abuse, and remediate the vulnerability.
This vulnerability is not related to Cloudflare CDN. The cdnjs project is a platform that leverages Cloudflare’s services, but the vulnerability described below relates to cdnjs’ platform only. To be clear, no existing libraries were modified using this exploit. The researcher published a new package which demonstrated the vulnerability and our investigation concluded that the integrity of all assets hosted on cdnjs remained intact.
Disclosure Timeline
As outlined in RyotaK’s blog post, the incident began on 2021-04-06. At around 1100 GMT, RyotaK published a package to npm exploiting the vulnerability. At 1129 GMT, cdnjs processed this package, resulting in Continue reading
AWS’s Egregious Egress


When web hosting services first emerged in the mid-1990s, you paid for everything on a separate meter: bandwidth, storage, CPU, and memory. Over time, customers grew to hate the nickel-and-dime nature of these fees. The market evolved to a fixed-fee model. Then came Amazon Web Services.
AWS was a huge step forward in terms of flexibility and scalability, but a massive step backward in terms of pricing. Nowhere is that more apparent than with their data transfer (bandwidth) pricing. If you look at the (ironically named) AWS Simple Monthly Calculator you can calculate the price they charge for bandwidth for their typical customer. The price varies by region, which shouldn't surprise you because the cost of transit is dramatically different in different parts of the world.
Charging for Stocks, Paying for Flows
AWS charges customers based on the amount of data delivered — 1 terabyte (TB) per month, for example. To visualize that, imagine data is water. AWS fills a bucket full of water and then charges you based on how much water is in the bucket. This is known as charging based on “stocks.”
On the other hand, AWS pays for bandwidth based on the capacity of their Continue reading
Empowering customers with the Bandwidth Alliance
High Egress Fees
Debates over the benefits and drawbacks of walled gardens versus open ecosystems have carried on since the beginnings of the tech industry. As applied to the Internet, we don’t think there’s much to debate. There’s a reason why it’s easier today than ever before to start a company online: open standards. They’ve encouraged a flourishing of technical innovation, made the Internet faster and safer, and easier and less expensive for anyone to have an Internet presence.
Of course, not everyone likes competition. Breaking open standards — with proprietary ones — is a common way to stop competition. In the cloud industry, a more subtle way to gain power over customers and lock them in has emerged. Something that isn’t obvious at the start: high egress fees.
You probably won’t notice them when you embark on your cloud journey. And if you need to bring data into your environment, there’s no data charge. But say you want to get that data out? Or go multi-cloud, and work with another cloud provider who is best-in-class? That’s when the charges start rolling in.
To make matters worse, as the number and diversity of applications in your IT stack increases, the Continue reading
Introducing Workers Usage Notifications
So you’ve built an application on the Workers platform. The first thing you might be wondering after pushing your code out into the world is “what does my production traffic look like?” How many requests is my Worker handling? How long are those requests taking? And as your production traffic evolves overtime it can be a lot to keep up with. The last thing you want is to be surprised by the traffic your serverless application is handling. But, you have a million things to do in your day job, and having to log in to the Workers dashboard every day to check usage statistics is one extra thing you shouldn’t need to worry about.
Today we’re excited to launch Workers usage notifications that proactively send relevant usage information directly to your inbox. Usage notifications come in two flavors. The first is a weekly summary of your Workers usage with a breakdown of your most popular Workers. The second flavor is an on-demand usage notification, triggered when a worker’s CPU usage is 25% above its average CPU usage over the previous seven days. This on-demand notification helps you proactively catch large changes in Workers usage as soon as those Continue reading
Upgrading the Cloudflare China Network: better performance and security through product innovation and partnership
Core to Cloudflare’s mission of helping build a better Internet is making it easy for our customers to improve the performance, security, and reliability of their digital properties, no matter where in the world they might be. This includes Mainland China. Cloudflare has had customers using our service in China since 2015 and recently, we expanded our China presence through a partnership with JD Cloud, the cloud division of Chinese Internet giant, JD.com. We’ve also had a local office in Beijing for several years, which has given us a deep understanding of the Chinese Internet landscape as well as local customers.
The new Cloudflare China Network built in partnership with JD Cloud has been live for several months, with significant performance and security improvements compared to the previous in-country network. Today, we’re excited to describe the improvements we made to our DNS and DDoS systems, and provide data demonstrating the performance gains customers are seeing. All customers licensed to operate in China can now benefit from these innovations, with the click of a button in the Cloudflare dashboard or via the API.
Serving DNS inside China
With over 14% of all domains on the Internet using Cloudflare’s nameservers we Continue reading
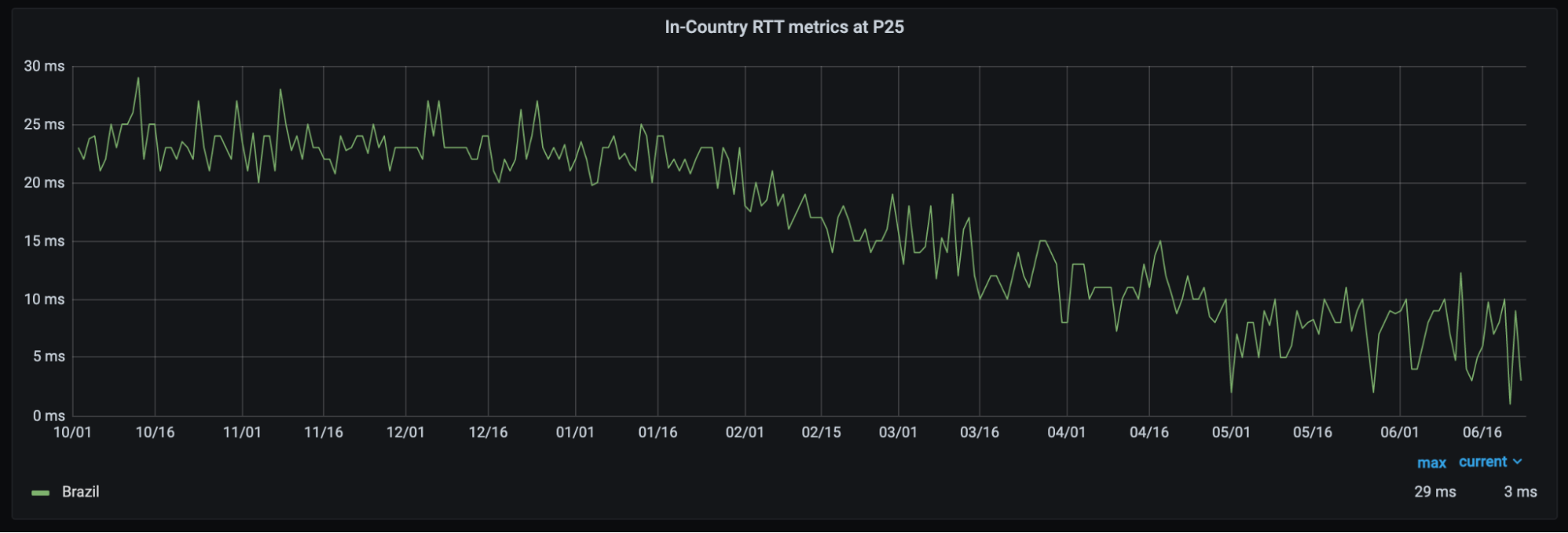
Expanding Cloudflare to 25+ Cities in Brazil
Today, we are excited to announce an expansion we’ve been working on behind the scenes for the last two years: a 25+ city partnership with one of the largest ISPs in Brazil. This is one of the largest simultaneous single-country expansions we’ve done so far.
With this partnership, Brazilians throughout the country will see significant improvement to their Internet experience. Already, the 25th-percentile latency of non-bot traffic (we use that measure as an approximation of physical distance from our servers to end users) has dropped from the mid-20 millisecond range to sub-10 milliseconds. This benefit extends not only to the 25 million Internet properties on our network, but to the entire Internet with Cloudflare services like 1.1.1.1 and WARP. We expect that as we approach 25 cities in Brazil, latency will continue to drop while throughput increases.
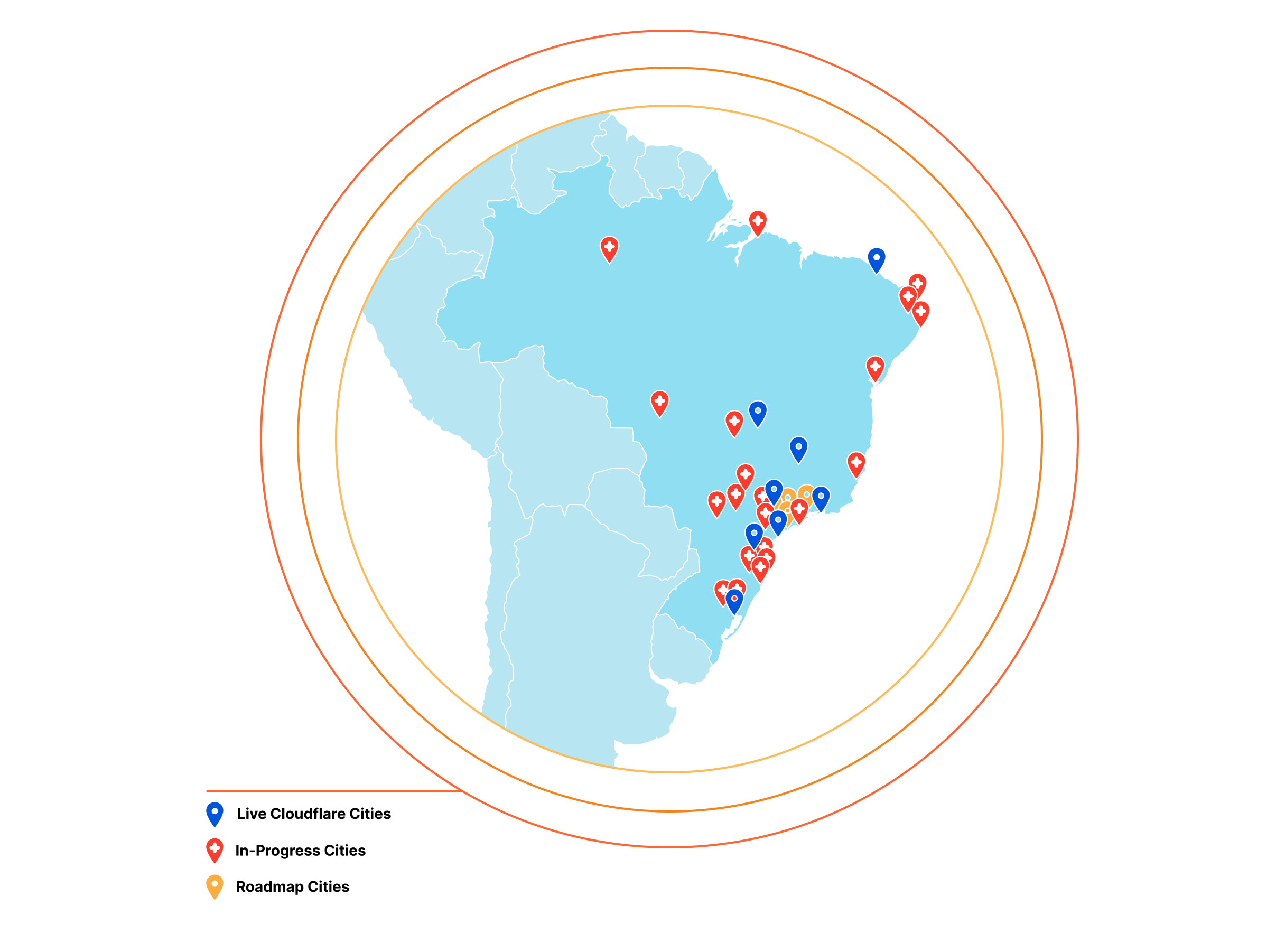
This partnership is part of our mission to help create a better Internet and the best development experience for all — not just those in major population centers or in Western markets — and we are excited to take this step on Continue reading
DDoS attack trends for 2021 Q2


Recent weeks have witnessed massive ransomware and ransom DDoS (Distributed Denial of Service) attack campaigns that interrupted aspects of critical infrastructure around the world, including one of the largest petroleum pipeline system operators, and one of the world’s biggest meat processing companies. Earlier this quarter, more than 200 organizations across Belgium, including the government and parliament websites and other services, were also DDoS’d.
And when most of the United States were celebrating Independence Day on July 4, hundreds of US companies were hit by a ransomware attack demanding 70 million USD in Bitcoin. Attackers known to be affiliated with REvil, a Russian ransomware group, exploited multiple previously unknown vulnerabilities in IT management software. The targets included schools, small public-sector bodies, travel and leisure organizations, and credit unions, to name a few. While the threat of ransomware and ransom DDoS is not new (read our posts on ransomware and ransom DDoS from 2021 Q1), the latest attacks on Internet properties ranging from wineries, professional sports teams, ferry services and hospitals has brought them from just being background noise to front page headlines affecting our day-to-day lives. In fact, recent attacks have propelled ransomware and DDoS to the top of US Continue reading