Cloudflare’s Partnership with HashiCorp and Bootstrapping Terraform with Cf-Terraforming
Cloudflare and HashiCorp have been technology partners since 2018, and in that time Cloudflare’s integration with HashiCorp’s technology has deepened, especially with Terraform, HashiCorp’s infrastructure-as-code product. Today we are announcing a major update to our Terraform bootstrapping tool, cf-terraforming. In this blog, I recap the history of our partnership, the HashiCorp Terraform Verified Provider for Cloudflare, and how getting started with Terraform for Cloudflare developers is easier than ever before with the new version of cf-terraforming.
Cloudflare and HashiCorp
Members of the open source community wrote and supported the first version of Cloudflare's Terraform provider. Eventually our customers began to bring up Terraform in conversations more often. Because of customer demand, we started supporting and developing the Terraform provider ourselves. You can read the initial v1.0 announcement for the provider here. Soon after, Cloudflare’s Terraform provider became ‘verified’ and we began working with HashiCorp to provide a high quality experience for developers.
HashiCorp Terraform allows developers to control their infrastructure-as-code through a standard configuration language, HashiCorp Configuration Language (HCL). It works across a myriad of different types of infrastructure including cloud service providers, containers, virtual machines, bare metal, etc. Terraform makes it easy for developers to follow Continue reading
Containers at the edge: it’s not what you think, or maybe it is
At Cloudflare, we’re committed to making it as easy as possible for developers to make their ideas come to life. Our announcements this week aim to give developers all the tools they need to build their next application on the edge. These include things like static site hosting, certificate management, and image services, just to name a few.
Today, we’re thrilled to announce that we’re exploring a new type of service at the edge: containers.
This announcement will be exciting to some and surprising to many. On this very blog, we’ve talked about why we believe isolates — rather than containers on the edge — will be the future model for applications on the web.
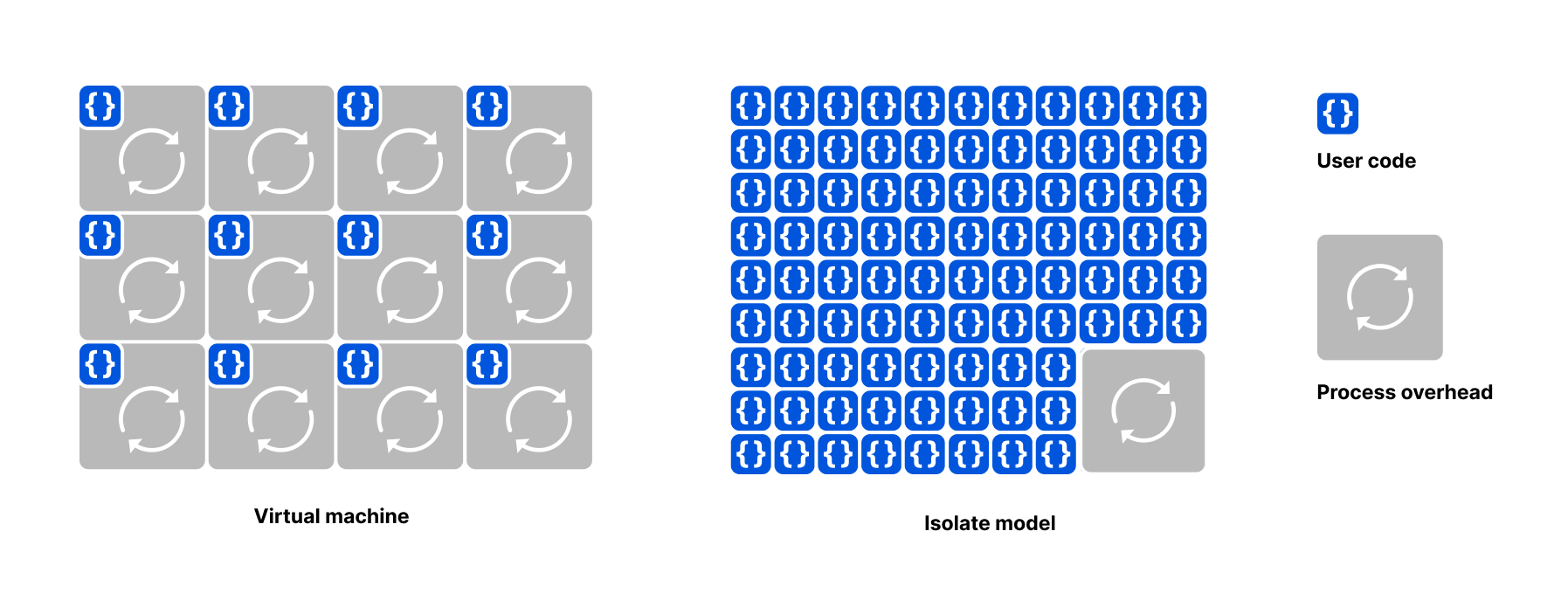
Isolates are best for Distributed Systems
Let us be clear: isolates are the best way to do edge compute, period. The Workers platform is designed to allow developers to treat our global network as one big computer. This has been a long-held dream of generations of engineers, inspiring slogans like "The Network is the Computer" — a trademark which, incidentally, we now own. Isolates and Durable Objects are finally making that vision possible.
In short, isolates excel at distributed systems. They are perfect for Continue reading
Announcing Cloudflare’s Database Partners


Cloudflare Workers is the easiest way for developers to deploy their application’s code with performance, scale and security baked in. No configuration necessary. Worker code scales to serve billions of requests close to your users across Cloudflare’s 200+ data centers.
But that’s not the only interesting problem we need to solve. Every application has two parts: code and state.
State isn’t always the easiest to work in a massive distributed system. When an application runs in 200+ data centers simultaneously, there’s an inherent tradeoff between distributing the data for better performance, availability, scale, and guaranteeing that all data centers see the same data at a given point in time.
Our goal is to make state at the edge seamless. We started that journey with Workers KV, which provides low-latency access to globally distributed data. We’re since added Durable Objects, with strong consistency and the ability to design coordination patterns on top of Workers. We’re continuing to invest in and build out these products.
However, some use cases aren’t easily implemented with Workers KV or Durable Objects. Think querying complex datasets, or communicating with an existing system-of-record. Even if we built this functionality ourselves, there will always be customers who want Continue reading
Cloudflare Stream now supports NFTs

Cloudflare Stream has been helping creators publish their videos online without having to think about video quality, device compatibility, storage buckets or digging through FFmpeg documentation. These creators want to be able to claim ownership of their works and assert control over how that ownership claim is transferred. Increasingly, many of those creators are looking to Non-Fungible Tokens (NFTs).
NFTs are a special type of smart contract that allows provable ownership of the contract on the blockchain. Some call NFTs collectibles because like coins or stamps, collectors who enjoy them buy, sell and trade them. Collectors keep track of NFTs on the Ethereum blockchain which acts as a shared source of truth of all the activity.
Today, we’re introducing a new API that takes a ERC-721 token ID and contact address and sets it on a video so every video on Stream can be represented with an NFT.
curl -X POST -H "Authorization: Bearer $AUTH_TOKEN" --data '{"contract":"0x57f1887a8bf19b14fc0d912b9b2acc9af147ea85","token":"5"}' https://api.cloudflare.com/client/v4/accounts/$ACCOUNT_ID/stream/$VIDEO_ID/nft
Once you set it, you cannot change these values so be sure to set it to an NFT you own! If you set a video you own to an NFT you don’t own, the owner of the NFT can claim Continue reading
Node.js support in Cloudflare Workers
We released Cloudflare Workers three years ago, making edge compute accessible to the masses with native support for the world’s most ubiquitous language — JavaScript.
The Workers platform has transformed so much since its launch. Developers can not only write sandboxed code at our edge, they can also store data at the edge with Workers KV and, more recently, coordinate state within our giant network using Durable Objects. Now, we’re excited to share our support of an 11 year old technology that’s still going strong: Node.js.
Node.js made a breakthrough by enabling developers to build both the frontend and the backend with a single language. It took JavaScript beyond the browser and into the server by using Chrome’s JavaScript engine, V8.
Workers is also built on V8 Isolates and empowers developers in a similar way by allowing you to create entire applications with only JavaScript — except your code runs across Cloudflare’s data centers in over 100 countries.
Our Package Support Today
There is nothing more satisfying than importing a library and watching your code magically work out-of-the-box.
For over 20k packages, Workers supports this magic already: any Node.js package that uses webpack or another polyfill Continue reading
Introducing workers.new, custom builds, and improved logging for Workers


Cloudflare Workers® aims to be the easiest and most powerful platform for developers to build and deploy their applications. With Workers, you can quickly solve problems without having to wonder: “is this going to scale?”
You write the JavaScript and we handle the rest, from distribution to scaling and concurrency.
In the spirit of quickly solving problems, we’re excited to launch three new improvements to the Workers experience, so you can take your next idea and ship it even faster.
Introducing... workers.new

First, we’re introducing https://workers.new, a shortcut that takes you directly to a JavaScript editor for creating a new Worker. Anytime you have a cool idea, need a quick fix to a problem, or just want to debug some JavaScript, you now have a simple way to go from idea to prototype. What’s more is you don’t even need to deploy the Worker to try it out!
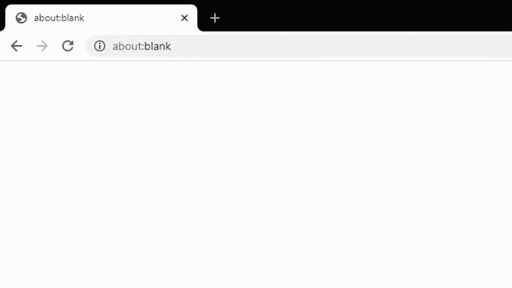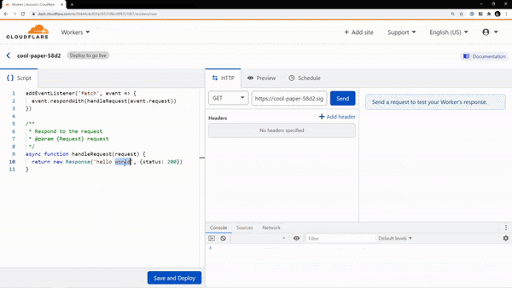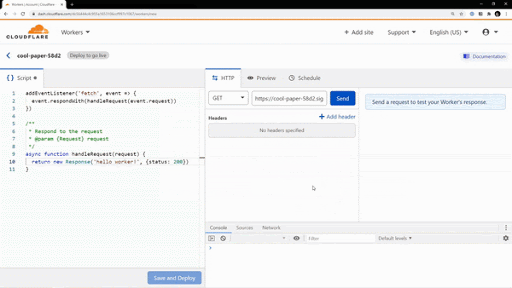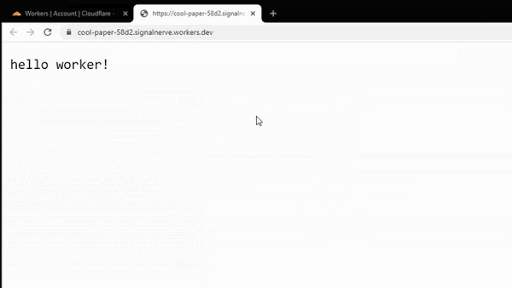
We’ve also updated the default Worker template to help you go a few steps beyond the typical “Hello, World!”. When you open the editor, you’ll now see a few examples that demonstrate how to redirect requests, modify headers, and parse responses.
Customize your build scripts

For developers Continue reading
A Boring Announcement: Free Tunnels for Everyone
A few months ago, we announced that we wanted to make Zero Trust security accessible to everyone, regardless of size, scale, or resources. Argo Tunnel, our secure method of connecting resources directly to Cloudflare, is the next piece of the puzzle.
Argo Tunnel creates a secure, outbound-only connection between your services and Cloudflare by deploying a lightweight connector in your environment. With this model, your team does not need to go through the hassle of poking holes in your firewall or validating that traffic originated from Cloudflare IPs.
In the past, Argo Tunnel has been priced based on bandwidth consumption as part of Argo Smart Routing, Cloudflare’s traffic acceleration feature. Starting today, we’re excited to announce that any organization can use the secure, outbound-only connection feature of the product at no cost. You can still add the paid Argo Smart Routing feature to accelerate traffic.
As part of that change (and to reduce confusion), we’re also renaming the product to Cloudflare Tunnel. To get started, sign up today.
If you’re interested in how and why we’re doing this, keep scrolling.
A Private Link to the Public Internet
In 2018, Cloudflare introduced Argo Tunnel, a private, secure connection between your origin Continue reading
Bringing AI to the edge with NVIDIA GPUs


Cloudflare has long used machine learning for bot detection, identifying anomalies, customer support and business intelligence. And internally we have a cluster of GPUs used for model training and inference.
For even longer we’ve been running code “at the edge” in more than 200 cities worldwide. Initially, that was code that we wrote and any customization was done through our UI or API. About seven years ago we started deploying custom code, written in Lua, for our enterprise customers.
But it’s quite obvious that using a language that isn’t widely understood, and going through an account executive to get code written, isn’t a viable solution and so four years ago we announced Cloudflare Workers. Workers allows anyone, on any plan, to write code that gets deployed to our edge network. And they can do it in the language they choose.
After launching Workers we added storage through Workers KV as programs need algorithms plus data. And we’ve continued to add to the Workers platform with Workers Unbound, Durable Objects, Jurisdictional Restrictions and more.
But many of today’s applications need access to the latest machine learning and deep learning methods. Those applications need three things: to scale easily, Continue reading
Expanding the Cloudflare Workers Observability Ecosystem


One of the themes of Developer Week is “it takes a village”, and observability is one area where that is especially true. Cloudflare Workers lets you quickly write code that is infinitely scalable — no availability regions, no scaling policies. Your code runs in every one of our data centers by default: region Earth, as we like to say. While fast time to market and effortless scale are amazing benefits, seasoned developers know that as soon as your code is in the wild… stuff happens, and you need the tools in place to investigate, diagnose, fix and monitor those issues.
Today we’re delighted to add to our existing analytics partners. We’re announcing new partnerships with six observability-focused companies that are deeply integrated into the Cloudflare Workers ecosystem. We’re confident these partnerships will provide immediate value in building the operational muscle to maintain and make your next generation of applications fast, secure and bullet-proof in production.

console.log(`Got request. Extracted name=${name}. Saving…`);
Cloudflare wrangler gives you the ability to generate, configure, build, preview and publish your projects, from the comfort of your dev environment. Writing code in your favorite IDE with a fully-fledged CLI tool that also allows you to simulate Continue reading
Location-based personalization at the edge with Cloudflare Workers
We’re excited to announce an update to Cloudflare Workers, our serverless code platform built on our global network. Geolocation data is now accessible and free for all developers on our Workers platform, including users on the free plan!
You can now serve personalized experiences for users based on their location using Workers. Personalization is critical to building intuitive apps for users and it unlocks new possibilities for what you can build on our platform. Whether you’re building a social networking app or an automatic shipping cost estimator for an e-commerce site, a one-size-fits-all experience doesn’t cut it. Location-based personalization helps you show what’s most relevant to your users, be it tickets for movies in their area or content in their local language.
With geolocation data available on the server side, there’s no configuration needed for users to set their location.
Each request to a Worker includes the user’s (example data shown):
- Country: “US”
- City: “Austin”
- Continent: “NA”
- Latitude: "30.27130"
- Longitude: “-97.74260”
- Postal code: "78701"
- Metro code(dma): “635”
- Region: “Texas”
- Timezone: “America/Chicago”
Geolocation data on Workers makes it even easier to build server rendered apps and customized services.
Refer to the documentation to learn more.
In case you need Continue reading
Developer Challenges


Welcome to Developer Week at Cloudflare! We are excited to announce we are running a series of Developer Challenges throughout the week to give you the excuse you needed to play with all our new features.
Between now and April 19 you’ll get to know the Cloudflare developer tools and walk away with a fun new app (or five) to your name. You’ll also become a part of the Cloudflare Developer community!
We hope that some of you will be inspired to create your next project using Cloudflare Workers, Workers KV, Pages, Durable Objects and all the developer-focussed products that Cloudflare offers. There’s already a vibrant community building applications using the Workers ecosystem; we hope the Developer Challenges inspire you to build on Cloudflare.
What are Developer Challenges?
We know that some people are new to the Cloudflare services for developers and that some of you have been using them for a while, so we have come up with two streams of challenges.
If you’re just getting started with Cloudflare, there will be a new challenge each day of the week that will help you level up your knowledge in no time. There’s also an extra bonus challenge Continue reading
Cloudflare Pages is now Generally Available


In December, we announced the beta of Cloudflare Pages: a fast, secure, and free way for frontend developers to build, host, and collaborate on Jamstack sites.
It’s been incredible to see what happens when you put a powerful tool in developers’ hands. In just a few months of beta, thousands of developers have deployed over ten thousand projects, reaching millions of people around the world.
Today, we’re excited to announce that Cloudflare Pages is now available for anyone and ready for your production needs. We’re also excited to show off some of the new features we’ve been working on over the course of the beta, including: web analytics, built in redirects, protected previews, live previews, and optimized images (oh, my!). Lastly, we’ll give you a sneak peek into what we'll be working on next to make Cloudflare Pages your go-to platform for deploying not just static sites, but full-stack applications.
What is Cloudflare Pages?
Cloudflare Pages radically simplifies the process of developing and deploying sites by taking care of all the tedious parts of web development. Now, developers can focus on the fun and creative parts instead.
Seamless builds for developers
Getting started with Cloudflare Pages is as Continue reading
Live stream to multiple platforms with Stream Connect
Today, we are announcing the Stream Connect beta, the first step towards supporting end-to-end live broadcasting on Cloudflare. You can use Stream Connect to push RTMPS feeds to the Cloudflare edge and have it restreamed to your audience on any platform that supports RTMPS such as Facebook, YouTube and Twitch.
What is restreaming?
Facebook, YouTube and Twitch are great platforms for creators to broadcast live video to reach billions. They each have their own unique communities and benefits for creators. If you have a band and want to broadcast a live performance for your fans, broadcasting to only one platform limits your reach. Restreaming enables you to push the live video to multiple platforms at the same time so you can meet your fans on their preferred platform.
Live video platforms accept incoming connections using a protocol called RTMP or RTMPS. Stream Connect allows you to continue using the same protocol as before. However, instead of using your local connection to send the video feed to multiple platforms, you only send it to Stream Connect. Connect uses the Cloudflare network to send your live feed to the configured media platforms.
How Stream Connect increases reliability and lowers latency
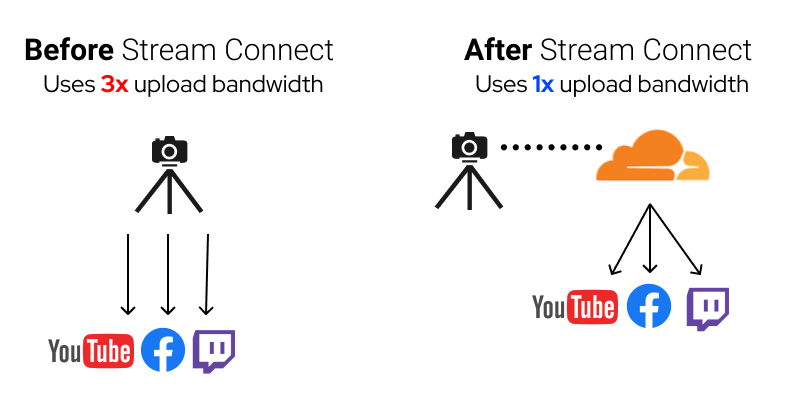
Eliminating the Continue reading
Developers, Developers, Developers: Welcome to Developer Week 2021


Runtimes, serverless, edge compute, containers, virtual machines, functions, pods, virtualenv. All names for things developers need to go from writing code to running code. It’s a painful reality that for most developers going from code they’ve written to code that actually runs can be hard.
Excruciatingly, software development is made hard by dependencies on modules, by scaling, by security, by cost, by availability, by deployment, by builds, and on and on. All the ugly reality of crystallizing thoughts into lines of code that actually run, successfully, somewhere, more than once, non-stop, and at scale.
And so… Welcome to Developer Week 2021!
Like we have done in previous Innovation Weeks (such as Security Week or Privacy Week), we will be making many (about 20) announcements of products and features to make developers’ lives easier. And by easy I mean removing the obstacles that stop you, dear developer, from writing code and deploying it so it scales to Internet size.
And Cloudflare Workers, our platform for software developers who want to deploy Internet-facing applications that start instantly and scale Internetly, has been around since 2017 (or to put it in perspective, since iPhone 8) and helping developers code and deploy in seconds Continue reading
Per Origin Host Header Override

Load Balancing as a concept is pretty straightforward. Take an existing infrastructure and route requests to the available origin servers so no single server is overwhelmed. Add in some health monitoring to ensure each server has a heartbeat/pulse so proactive decisions can be made. With two steps, you get more effective utilization of your existing resources… simple enough!
As your application grows, however, load balancing becomes more complicated. An example of this — and the subject of this blog post — is how load balancing interacts with the Host header in an HTTP request.
Host headers and load balancing
Every request to a website contains a unique piece of identifying information called the Host header. The Host header helps route each request to the correct origin server so the end user is sent the information they requested from the start.
For example, say that you enter example.com into my URL bar in my browser. You are sending a request to ‘example.com’ to send you back the homepage located within that application. To make sure you actually get resources from example.com, your browser includes a Host header of example.com. When that request reaches the back-end infrastructure, Continue reading
Dynamic URL Rewriting at the edge with Cloudflare
URLs are ugly. They are hard to read, difficult to memorise and often auto-generated for the benefit of the origin server - not the user.
Today we are announcing the immediate availability of Transform Rules for all Cloudflare plans. Transform Rules provide Cloudflare administrators with the ability to create URL rewrite rules. These rules transform HTTP requests as they flow through Cloudflare providing an interpretation layer between the human friendly and the computer friendly.
Ease of understanding
Imagine you are going on a much needed around-the-world trip and want to buy a copy of John Graham-Cumming’s book The Geek Atlas: 128 Places Where Science and Technology Come Alive to use as inspiration. Would the link https://www.travelbooks247.com/dp/0596523203/ make sense to you? Chances are the answer is no. It's hard for humans to understand these complex, contextless URLs.
This is why companies instead provide user friendly alternatives such as: https://www.travelbooks247.com/Geek-Atlas-Places-Science-Technology/dp/0596523203/ and use web servers as the interpreter. This interpretation is known as URL rewriting.
Large ecommerce retailers take HTTP requests to these human-friendly URLs and rewrite them using a simple pattern that strips the content Geek-Atlas-Places-Science-Technology/ before sending the HTTP request to the backend. The human readable hyperlink Continue reading
Jonathon Dixon: Why I joined Cloudflare


I’m excited to announce that on March 1, I joined Cloudflare as Vice President and GM, Asia Pacific (including Japan and Greater China) to help build and expand Cloudflare’s growing customer and partner base and presence in the region. We currently have over 200 passionate and customer-focused employees in APAC, with offices in Beijing, Singapore, Sydney and Tokyo.
A little about me
Singapore is where I’m based. Melbourne is home with my early years spent in Country Victoria. I love the outdoors, sports, travelling and spending time with family and friends. I am naturally intrigued by interesting people and different perspectives. I have a thirst for learning and understanding why people act and behave the way they do, and believe that understanding more about different cultures makes me a better person/leader. And what better way to do so than by being in the most diverse region in the world — Asia Pacific is home to 60% of the world’s population, with thousands of languages spoken, spanning multiple time zones. With the rise of innovation and technology adoption in the region, growth and expansion opportunities are endless.
My journey to Cloudflare
Throughout my 20-year career, I have been extremely fortunate to Continue reading
The Teams Dashboard: A New Place to Call Home
Over the past few weeks, our team has written a lot about the Cloudflare for Teams Dashboard, and more specifically, about our approach to design and the content within it. In these recent posts, we charted the journey of developing omni-directional communication channels across product, design, and content, and how these relationships directly influence the user experiences we aim to create.
Today, we’re announcing a new feature within the Teams Dash. We called it “Home”. We created Home with a simple goal in mind: design an adaptive and informative landing page where users can see a round-up of their environment.
In this last post of our series, we’ll show, rather than tell, how we collaborated as a team that rows in the same direction and towards the same goal — to create a great user experience.
In this blog post, we’ll walk you through your new Teams Home by calling out a few of the guiding principles we had in mind as we designed it. Transparency, adaptiveness, guidance and warmth aren’t only foundational words in the Cloudflare for Teams product principles — they’re part of our day-to-day brainstorming and discussion around user experience.
Here’s how the Teams Home reflects these Continue reading
How to execute an object file: Part 2
Handling relocations
In the previous post, we learned how to parse an object file and import and execute some functions from it. However, the functions in our toy object file were simple and self-contained: they computed their output solely based on their inputs and didn't have any external code or data dependencies. In this post we will build upon the code from part 1, exploring additional steps needed to handle code with some dependencies.
As an example, we may notice that we can actually rewrite our add10 function using our add5 function:
obj.c:
int add5(int num)
{
return num + 5;
}
int add10(int num)
{
num = add5(num);
return add5(num);
}
Let's recompile the object file and try to use it as a library with our loader program:
$ gcc -c obj.c
$ ./loader
Executing add5...
add5(42) = 47
Executing add10...
add10(42) = 42
Whoa! Something is not right here. add5 still produces the correct result, but add10 does not . Depending on your environment and code composition, you may even see the loader program crashing instead of outputting incorrect results. To understand what happened, let's investigate the machine code generated by the compiler. We Continue reading
Durable Objects, now in Open Beta
Back in September, we announced Durable Objects - a new paradigm for stateful serverless.
Since then, we’ve seen incredible demand and countless unlocked opportunities on our platform. We’ve watched large enterprises build applications from complex API features to real-time games in a matter of days from inception to launch. We’ve heard from developers that Durable Objects lets them spend time they used to waste configuring and deploying databases on building features for their apps. More than anything, we’ve heard that you want to start building with Durable Objects now.
As of today, Durable Objects beta access is available to anyone with a Cloudflare Workers® subscription - you can enable them now in the dashboard by navigating to “Workers” and then “Durable Objects”. You can also upgrade to the latest version of Wrangler to deploy Durable Objects!
Durable Objects are still in beta and are being made available to you for testing purposes. Storage is capped per-account at 10 GB of data, and there is no associated SLA for Object availability or durability.
What are Durable Objects?
Durable Objects provide two things: coordination across multiple Workers and strongly consistent edge storage.
Normally Cloudflare’s network executes a Continue reading