OSPF Convergence In a Hub and Spoke Topology
My dear friend Micheline Murphy posted an excellent question on OSPF in a Hub and Spoke topology at the Cisco Learning Network. The scenario is a Hub and Spoke topology with two Hub routers that are ABRs belonging to area 100 and area 200. SP-101 and SP-102 belong to area 100. SP-201 and SP-202 belong to area 200. The topology is shown below:

The OSPF areas are shown below:


Some facts about the setup and intent of this post:
- All routers are Catalyst8000v running IOS-XE 17.6.3.
- Hub routers are connected to area 0 where the prefix 198.51.100.0/24 is being advertised.
- Each spoke advertises a /28 from 192.0.2.0/24.
- All interfaces are point to point as the purpose is not to simulate a NBMA topology.
- The intent is to verify what happens in a failure scenario but lab first shows the stable topology.
The expectation is that in a stable topology each Spoke will have two ECMP routes, one via each Hub, to the other spokes. The router SP-202 will be used to demonstrate. First let’s verify that everything is working as expected. SP-202 is a router in area 200:
SP-202#show ip ospf 1 Continue reading
Catalyst SD-WAN – Introduction to Configuration Groups
One of the challenges with Catalyst SD-WAN is managing templates. Depending on how successful you are in standardizing your deployment, you risk ending up with many device templates. This can also be amplified if you have several platforms as each platform requires its own set of device templates. Feature templates, while reusable, offers no concept of grouping feature templates which means that there is a lot of work involved in building a new device template. To overcome some of these challenges, Cisco has introduced Configuration Groups starting with 20.8 and going forward where 20.11 currently has the most features implemented. This is also often referred to as UX 2.0 in some presentations. Let’s take a look at Configuration Groups by looking at the building blocks.
- Configuration Group – Logical grouping of features or configuration that is applied to devices. Similar to a device template but it can be applied to different models.
- Feature Profile – Building block of configurations that can be reused across different Configuration Groups. Example feature profiles are Transport Profile, System Profile, Service Profile.
- Feature – The Feature Profile consists of features. The individual capability to be shared across Configuration Groups such as service Continue reading
Catalyst SD-WAN – Bootstrapping a Catalyst8000v Using a File on Bootflash
Yesterday I showed how to bootstrap a Catalyst8000v from the CLI. Today, I will show how to put a file on bootflash which includes the configuration but also the root certificate and the certificate of the device. This is a bit of a more streamlined process and can also be useful if you don’t know what CLI commands to use as vManage will generate the configuration for you.
Starting out, we have a freshly booted router that is in autonomous mode (non-SD-WAN):
Router#sh ver | i operating Router operating mode: Autonomous
To generate the bootstrap configuration, the process is to first go through the regular process of attaching a device to a template. Go to Configuration -> Templates and select Attach Devices:
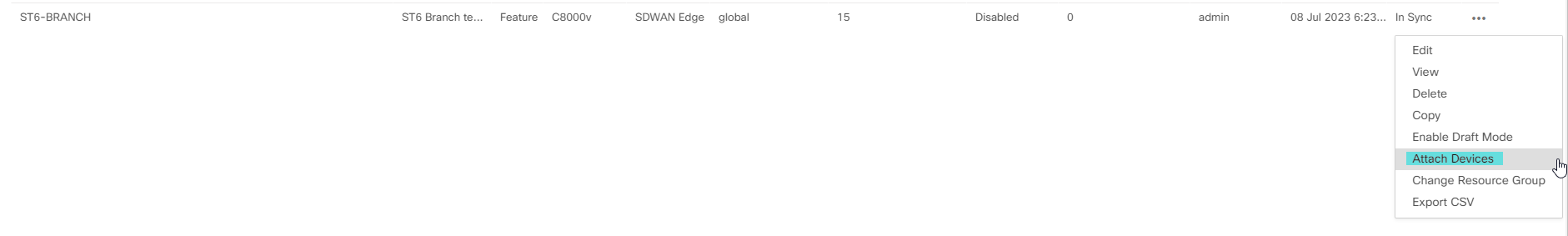
Select the correct device:
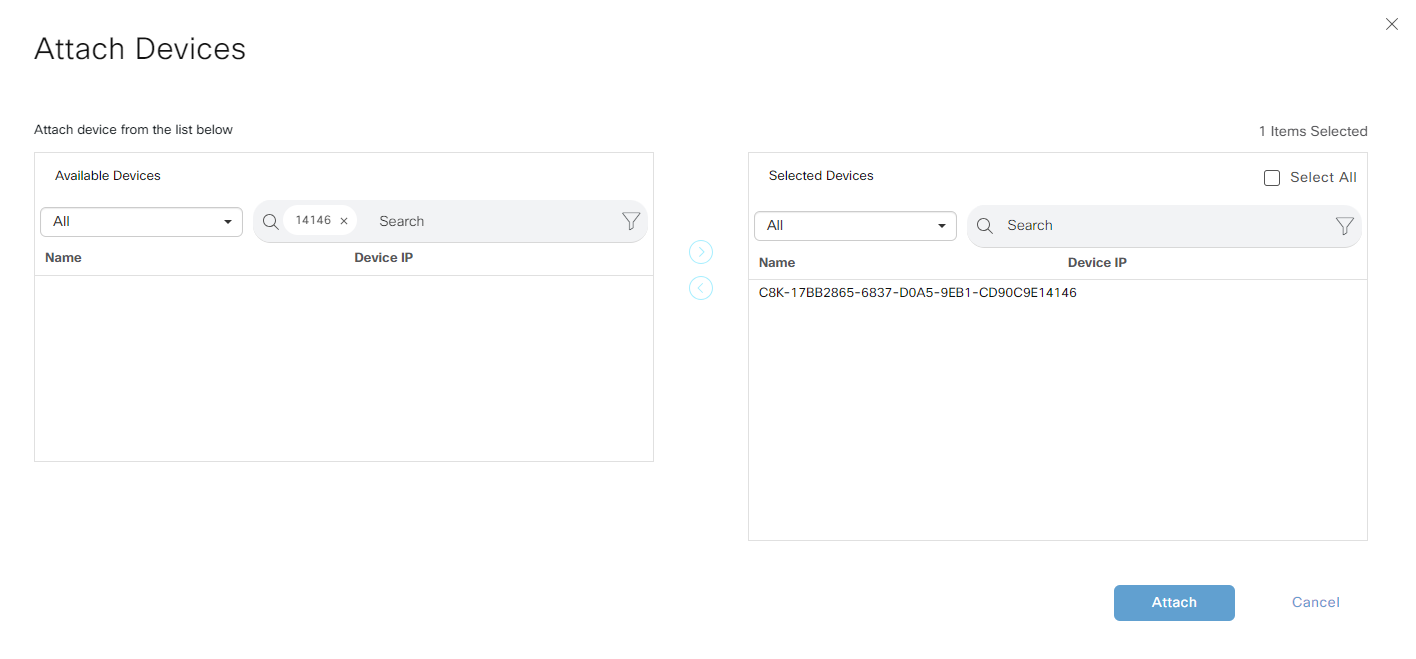
Fill in the information needed:
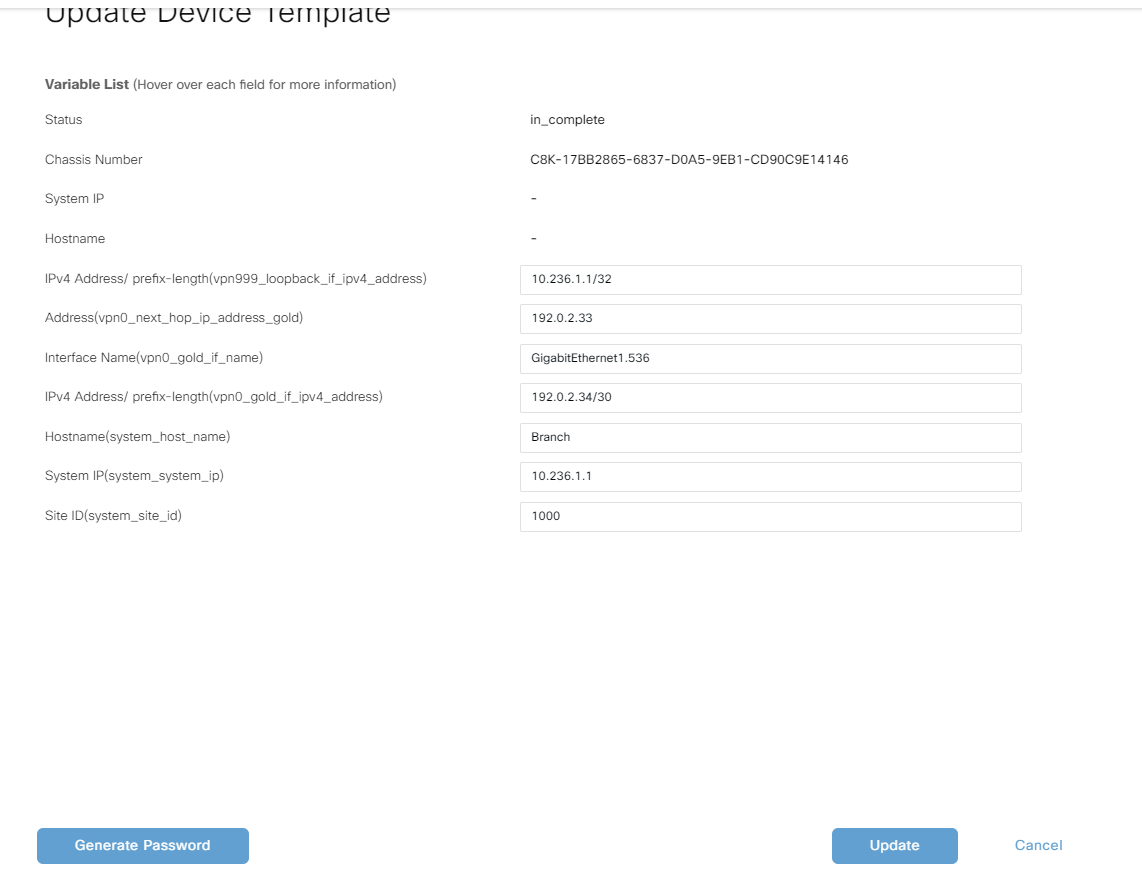
Click Update to reflect the edits:
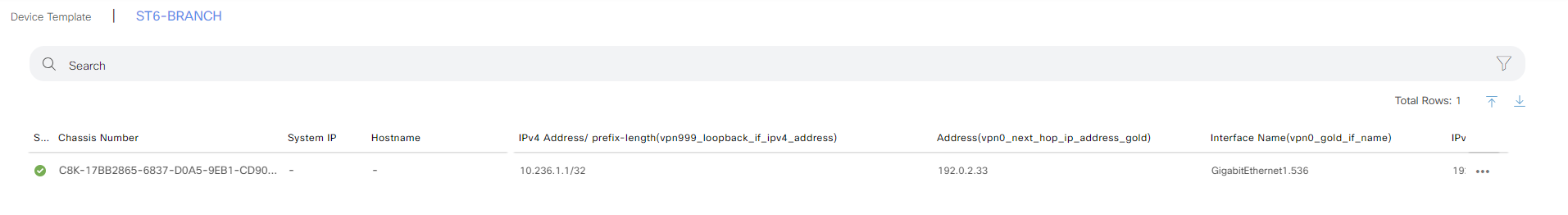
Then click Next:
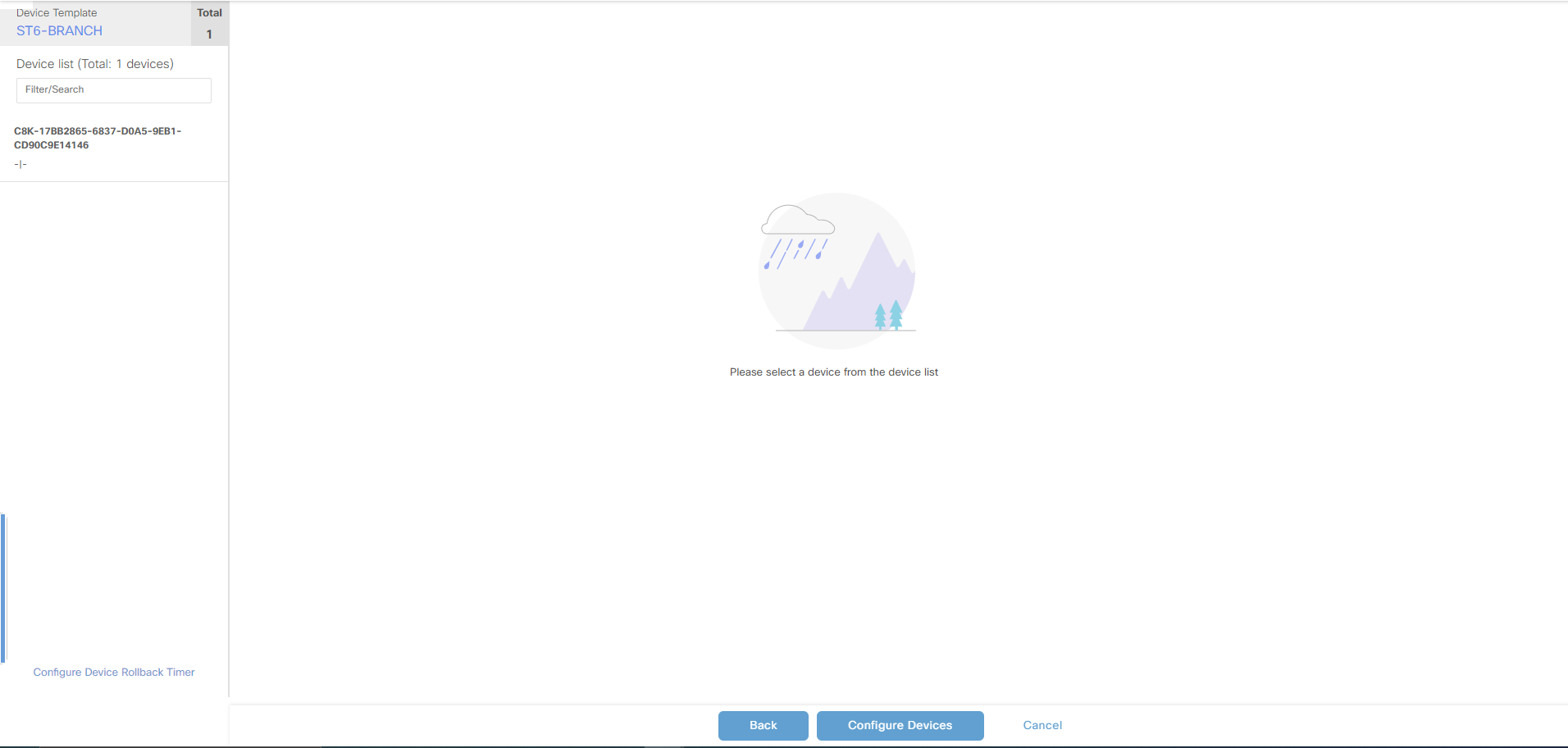
Click Configure Devices and vManage will try to push the config but the device is offline:
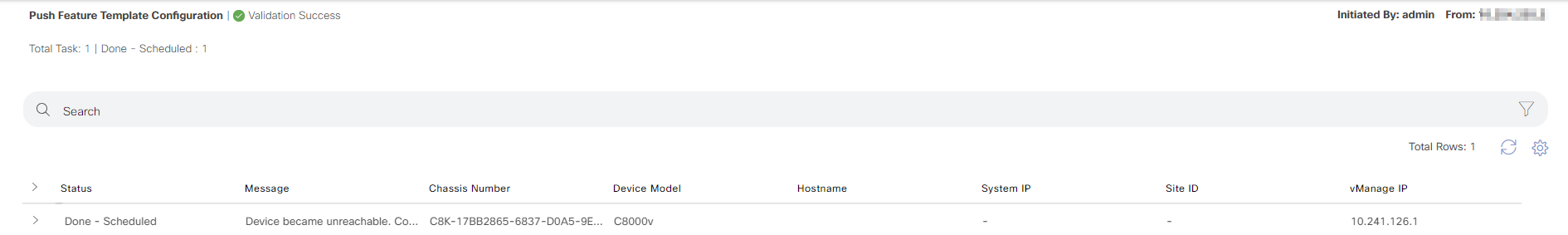
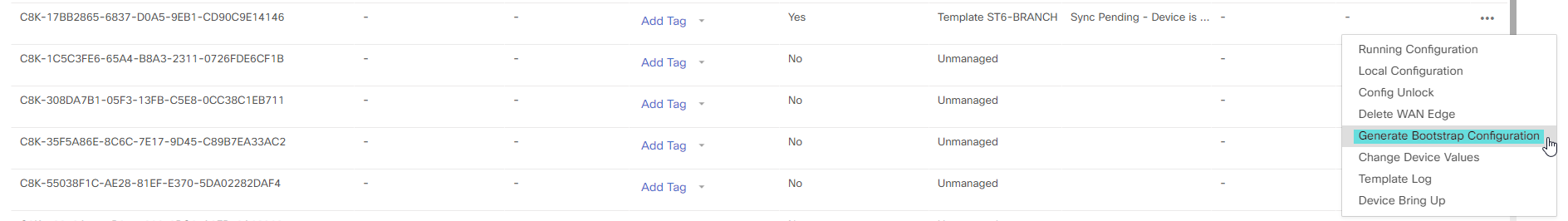
Once this is done, vManage has all the information it needs to generate the bootstrap. Go to Configuration -> Devices and select the correct device and then Generate Bootstrap Configuration:
Then vManage will disply the following window. Choose Cloud-Init and have the box selected Continue reading
Catalyst SD-WAN – Botstrapping a Catalyst8000v in a Virtual Lab
I’m rebuilding my Catalyst SD-WAN lab and thought I would give some quick pointers on how to bootstrap a Catalyst 8000v in your virtual lab. When the router first boots up, it will be in autonomous mode (non-SD-WAN mode):
Router#show version | i operating Router operating mode: Autonomous
Configure the router to be in controller mode which will cause it to reboot:
Router#controller-mode enable Enabling controller mode will erase the nvram filesystem, remove all configuration files, and reload the box! Ensure the BOOT variable points to a valid image Continue? [confirm] % Warning: Bootstrap config file needed for Day-0 boot is missing Do you want to abort? (yes/[no]): no
To bootstrap the router, the following is needed:
- System IP
- Site ID
- Organization name
- vBond name/IP
- IP address of tunnel interface (if not using DHCP)
- Tunnel interface name
- DNS server (if using name resolution)
- On-premises root cert (if using your own certificates)
- Certificate
First, verify that the router is now in controller mode:
Router#show version | i operating Router operating mode: Controller-Managed
Create a small bootstrap configuration with all the required parameters. Mine is below (some information redacted):
config-transaction system system-ip x.x.x.x site-id xxxxxxxxxx organization-name "sd-wan-lab-daniel" vbond 192. Continue reading
Building a WAN Impairment Device in Linux on VMware vSphere
In some scenarios it is really useful to be able to simulate a WAN in regards to latency, jitter, and packet loss. Especially for those of us that work with SD-WAN and want to test or policies in a controlled environment. In this post I will describe how I build a WAN impairment device in Linux for a VMware vSphere environment and how I can simulate different conditions.
My SD-WAN lab is built on VMware vSphere using Catalyst SD-WAN with Catalyst8000v as virtual routers and on-premises controllers. The goal with the WAN impairment device is to be able to manipulate each internet connection to a router individually. That way I can simulate that a particular connection or router is having issues while other connections/routers are not. I don’t want to impose the same conditions on all connections/devices simultaneously. To do this, I have built a physical topology that looks like this:

All devices are connected to a management network that I can access via a VPN. This way I have “out of band” access to all devices and can use SSH to configure my routers with a bootstrap configuration. To avoid having to create many unique VLANs in the vSwitch, Continue reading
Microsoft AZ-700 completed
I just passed the Microsoft AZ-700 exam, Designing and Implementing Microsoft Azure Networking Solutions, which means I am now certified in the two major clouds (AWS and Azure) when it comes to networking. As always after an exam, I write a summary of my experience with it and the resources I used. This is this post.
What is AZ-700?
This exam is for those that want to get certified on the networking component of Azure. Microsoft describes the exam in the following manner:
Candidates for this exam should have subject matter expertise in planning, implementing, and maintaining Azure networking solutions, including hybrid networking, connectivity, routing, security, and private access to Azure services
The breakdown of major topics and their percentage is the following:
- Design, implement, and manage hybrid networking (10-15%)
- Design and implement core networking infrastructure (20-25%)
- Design and implement routing (25-30%)
- Secure and monitor networks (15-20%)
- Design and implement Private access to Azure Services (10-15%)
There is a more detailed breakdown available as well. Always go through the exam blueprint before studying for a certification.
How to study for AZ-700
My goal when studying for this exam was to build a proficiency working with networking in Azure. That Continue reading
Is VLAN 1 Special in Cisco Networks?
I got asked why we change from VLAN 1 to another VLAN in Cisco networks. What is bad with the default setup? Is VLAN 1 really magical in a Cisco network?
When Cisco ships a Catalyst switch to you, there is no configuration provided. This means that all the ports will be access ports and the only VLAN that exists is VLAN 1. Now, we’ve all seen networks that keep it like this. Everything is one big flat network and the only VLAN in use is VLAN 1. If this is a bad configuration depends on several factors, including the size of the network, but let’s take a look at some of the drawbacks to maintaining this configuration:
- No segmentation – There is no segmentation. Every user can access every other user and anything else in the VLAN such as infrastructure, servers, IoT type devices, and so on
- Default access – The user gets access simply by connecting their PC to the switch which may not be the desired outcome
- Management access – Related to the first bullet point, if the switch has a management IP in VLAN 1, the user may be able to access and login to the Continue reading
Internet Edge IP SLA Deep Dive
It is a common design to have an internet Edge router connected to two different internet service providers to protect against the failure of an ISP bringing the office down. The topology may look something like this:
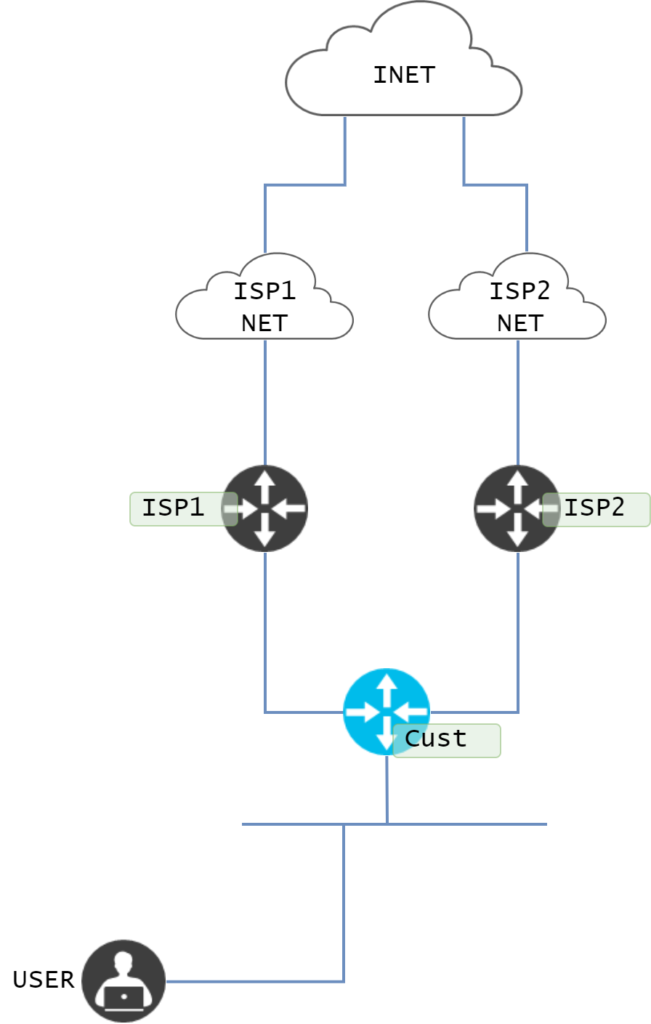
The two ISPs are used in an active/standby fashion using static routes. This is normally implemented by using two default routes where one of the routes is a floating static route. It will look something like this:
ip route 0.0.0.0 0.0.0.0 203.0.113.1 name PRIMARY ip route 0.0.0.0 0.0.0.0 203.0.113.9 200 name SECONDARY
With this configuration, if the interface to ISP1 goes down, the floating static route which has an administrative distance (AD) of 200 will be installed and traffic will flow via ISP2. The drawback to this configuration is that it only works if the physical interface goes down. What happens if ISP1’s CPE has the interface towards the customer up but the interface towards the ISP Core goes down? What happens if there is a failure in another part of the ISP’s network? What if all interfaces are up but Continue reading
Modifying Maximum Throughput of Catalyst8000v
The Catalyst8000v is Cisco’s virtual version of the Catalyst 8000 platform. It is the go to platform and a replacement of previous products such as CSR1000v, vEdge cloud, and ISRV. When installing a Catalyst8000v, it comes with a builtin shaper setting the maximum throughput to 10 Mbit/s as can be seen below:
R1#show platform hardware throughput level The current throughput level is 10000 kb/s
This is most likely enough to perform labbing but obviously not enough to run production workloads. You may be familiar with Smart Licensing on Cisco. Previously, licensing was enforced and it wasn’t possible to modify throughput without first applying a license to a device. In releases 17.3.2 and later, Cisco started implementing Smart Licensing Using Policy which essentially means that most of the licenses are trust-based and you only have to report your usage. There are exceptions, such as export-controlled licenses like HSEC which is for high speed crypto, anything above 250 Mbit/s of crypto. To modify the maximum throughput of Catalyst8000v, follow these steps:
R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#platform hardware throughput level MB ? 100 Mbps 1000 Mbps 10000 Mbps 15 Mbps 25 Mbps 250 Mbps 2500 Continue reading
Modifying Administrative Distance of Specific BGP Route
In one of the Discords that I’m in there was a user with a complex network consisting of a mix of DMVPN, BGP over MPLS VPN circuits, and SD-WAN. For some prefixes, the path via the private MPLS is preferred, for others, the SD-WAN path. Now, if a prefix is available in two different protocols, BGP vs Overlay Management Protocol (OMP), there is nothing we can do in BGP or OMP to modify which one gets installed into the Routing Information Base (RIB). This is no different than if EIGRP and OSPF were competing to install a prefix into the RIB, the protocol with the lower Administrative Distance (AD) would have its route installed.
The default AD values used on a Cisco device for these protocols are:
- eBGP – 20
- iBGP – 200
- OMP – 251
Based on the AD, OMP will always lose out. It is of course possible to change the AD of BGP, but that would have an effect of all prefixes and we lose the ability to have some prefixes preferred via BGP and others via OMP. I had never changed the AD of a specific BGP prefix before, so I turned to Twitter to see Continue reading
Using Python to Calculate Cisco SD-WAN Tunnel Numbers – Part 2
In the first post I shared with you my code to calculate tunnel numbers in Cisco SD-WAN. I’m a beginner in Python so I thought it would be a great learning experience to have someone experienced in Python, such as Rodrigo, take a look at the code and come up with improvements. As I like to share knowledge, I’m taking this journey with you all. Let’s get started!
You may recall that I had a function to calculate the tunnel number. It looked like this:
def calculate_tunnel_number(interface_name:str) -> int:
<SNIP>
return total_score
Rodrigo’s comment was that the function name is excellent as it is clear what the function does. However, my return statement returns total_score which is not clear what it does. It would be better to return tunnel_number which is what the function is calculating.
The next comment is that when splitting things and it is known how many pieces you have, it is better to unpack them, that is, assign the unwanted piece to a throwaway variable rather than using indexing. My code looked something like this:
interface_number = split_interface(interface_name)[1]
It would be better to do something like this:
_, interface_number = split_interface(interface_name)[1]
The first variable, a Continue reading
Using Python to Calculate Cisco SD-WAN Tunnel Numbers – Part 1
When using Cisco SD-WAN on IOS-XE, it uses tunnel interfaces to configure parameters of the implementation. There is a mapping between what interface the tunnel is sourcing from and the name of the tunnel interface. For example, if the tunnel source is GigabitEthernet0, the tunnel interface is Tunnel0, if the tunnel source is GigabitEthernet0.100, the tunnel interface is Tunnel100000. When provisioning a router and not using Zero Touch Provisioning (ZTP), you build a small bootstrap configuration that configures mandatory parameters such as Site ID, System IP, Organization Name, but also a tunnel interface to be able to connect to the controllers. It is possible to create this configuration in vManage, and hence find out the tunnel interface name, but I thought it would be interesting to do this with code and not be dependent on vManage.
In this post, I will describe the code I used and what my logic was when creating different parts of the code. In this first post I will use the code that I came up with. In the second part, my friend Rodrigo who runs an excellent Python blog ,analyzed my code and came up with improvements, which I will describe in that Continue reading
Viewing a Certificate Using OpenSSL
I have started taking Ed Harmoush’s Practical TLS course to learn more about TLS and certificates. When learning about TLS, you want to inspect different certificates to see the various fields and see how different organizations use certificates differently. As always, Linux comes with a great set of tools to work with certificates in the form of OpenSSL. In this post, I will show how to download a certificate and discuss some of the fields that are present in the certificate.
To get the certificate, we will use openssl with s_client and connect to a web site. I’m using twitter.com in this example:
openssl s_client -connect twitter.com:443 CONNECTED(00000003) depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA verify return:1 depth=1 C = US, O = DigiCert Inc, CN = DigiCert TLS Hybrid ECC SHA384 2020 CA1 verify return:1 depth=0 C = US, ST = California, L = San Francisco, O = "Twitter, Inc.", CN = twitter.com verify return:1 --- Certificate chain 0 s:C = US, ST = California, L = San Francisco, O = "Twitter, Inc.", CN = twitter.com i:C = US, O = Continue reading
My Journey to Getting AWS Certified Advanced Networking – Specialty Certified
Last week I took and passed the AWS Certified Advanced Networking – Specialty exam on my first attempt. In this post I will describe the study materials that I used and talk about my experience of taking this test.
What type of skills does this exam test? This is a quote from AWS:
Earning AWS Certified Advanced Networking – Specialty validates expertise in designing and maintaining network architecture for the breadth of AWS services.
The key here I think is “for breadth of AWS services”. It’s not enough to only understand general networking in AWS, you need to understand how to do networking for different AWS services such as S3, WorkSpaces, Lambda, storage gateway, and so on. There is no actual prerequisite to take the exam but it definitely doesn’t hurt if you already have the Solutions Architect Associate (this was previously a prereq) as it will help you in understanding what services are available.
The following is also listed as recommendations for who should take this exam:
- Professional experience using AWS technology, AWS security best practices, AWS storage options and their underlying consistency models, and AWS networking nuances and how they relate to the integration of AWS services.
- Knowledge Continue reading
Getting Experience with Public Cloud
Someone reached out to me and asked how you get experience with public cloud. That’s an excellent question so I thought I would give some perspective on it. There are three ways that immediately come to mind:
- Studying for a certification
- Playing around with different services in public cloud
- Getting involved in projects at work
Public cloud is a little like walking into a gigantic supermarket. You are looking for something very specific, maybe just a carton of milk, but if you have never been to this supermarket it could take you hours to find the milk. Maybe the milk is named something else in this store. To understand a specific cloud such as AWS, Azure, or GCP, you must first build up a basic understanding of what services they offer and how to use them. I normally prefer to do this by studying for a certification, such as the AWS Solutions Architect Associate, but there are also more introductory certifications such as the Cloud Practitioner or Azure Fundamentals. You can be super experienced and highly trained in a domain, such as servers or networking, but you must first learn to speak their language and understand their services. It definitely Continue reading
8 Tips for a Successful Network Migration
I have done many network migrations over the years. Now a days it’s a more rare event but this weekend we migrated some Core switches with very little down time. What are some of the things that you should do to maximize the odds of a successful migration?
Plan
If your migration went successful without planning, that doesn’t mean you are smart, just lucky. Every migration requires planning. What steps are involved in the migration? How do you validate each step? Who needs to be involved in the migration? Who needs to validate services when the migration is done? What are the criteria for a successful migration? How much time do you need to perform the migration? At what point do roll back? What are the steps involved in rolling back?
A migration plan can have varying levels of detail. I’ve worked with some very critical networks where we have had to describe each and every step in detail including every command that is involved in the migration. This takes a lot of time but you can’t cut corners when you are working with networks that can affect people’s health and lives.
Prepare
Prepare as much as you can. This Continue reading
Python Script Pulling AWS IP Prefixes – Part 3
The two previous posts described what the script does and modules used as well as how the script leverages YAML.
This time, we will go through the function that generates the access-list name. The code for this is below:
def generate_acl_name(interface_name: str) -> str:
"""Generate unique ACL name to avoid conflicts with any existing ACLs
by appending a random number to the outside interface name"""
# Create a random number between 1 and 999
random_number = random.randint(1, 999)
acl_name = f"{interface_name}_{random_number}"
return acl_name
The goal with this code is to generate a new access-list with a unique name. Note that the script doesn’t do any check if this access-list already exists which is something I will look into in an improved version of the script. I wanted to first start with something that works and take you through the process together with myself as I learn and improve on the existing code.
The function takes an interface_name which is a string. This is provided by the YAML data that we stored in the yaml_dict earlier. The function is then called like this:
acl_name = generate_acl_name(yaml_dict["outside_interface"])
The name is stored in the yaml_dict under the outside_interface mapping:
In [6]: yaml_dict Continue reading
Python Script Pulling AWS IP Prefixes – Part 2
In the previous post I described some of the design considerations for this script and what modules I use. In this post, we will look at using YAML to collect data and use it in Python in the form of a dictionary. Why YAML? YAML is commonly used as a readable way of storing configuration data and there are modules for Python to read that data.
The YAML file is a very basic one containing these mappings:
--- outside_interface: outside aws_service: s3 aws_region: eu-north-1 asa_ip: 192.168.255.241 ...
The three dashes indicate the start of the file and the three dots indicate the end of the file. We have configured what service we are interested in (S3) and in what region (eu-north-1). The outside interface in our Cisco ASA is named outside.
The natural fit to work with mappings in Python is a dictionary. We need to get the data from the file named aws_prefix.yml into a dictionary. To do that, we will use the following code:
def get_yaml_data() -> dict:
"""Gets the interface name, ASA IP address AWS service, and region
from the YAML file and returns a dictionary"""
try:
with open("aws_prefix.yml") Continue reading
Python Script Pulling AWS IP Prefixes – Part 1
I have been playing around with Python lately with the goal of building basic skills in it. I have found that to make good progress what works best for me is:
- Have a project that I find interesting to work on
- Spend a little time every day on the project
The project I decided on was to get the IP addresses that AWS uses for their services, build an access-list based on these prefixes, and then configure a Cisco ASA with that access-list. The final result looks like this:

In a series of blog posts, I will cover how I built this script. Keep in mind that my focus was to get a script that works and then improve on it. I have some plans for getting an experienced Python coder to go through the code with me and to work on improvements. Stay tuned for that!
As with any coding project, you need to come up with some general guidelines on how to get data and what is good enough. These are some of the considerations I had:
- I will get the configuration needed from a YAML file rather than a CLI (good enough for Continue reading
Route Replication the Easy Way
Easy Virtual Network (EVN) was a technology Cisco came up with back in the days to make it easier to implement VRFs without the pain of running VRF lite or the complexity of running a full MPLS + BGP network. It was actually a pretty cool technology but never became mainstream. However, as part of this technology, Cisco also made it easier to replicate, or in other words leak, routes between VRFs. You don’t need the rest of EVN to do this and this simplified way of replicating routes have kind of been forgotten by the industry. I thought I would share with you the ease of replicating routes with this feature even without BGP.
We have a straight forward topology like the one below:

The USERS switch is a L2 switch and all the L3 configuration is in the CORE router. We have implemented segmentation in the network so we have a USERS VRF and then we have a SERVICES VRF for shared services such as DNS and DHCP. Because these services are in a separate VRF, we will not have reachability to them from the USERS VRF. This lab will use the following IP addresses:
User – 10. Continue reading