Cyber Crane Mesh Topology Built with netlab
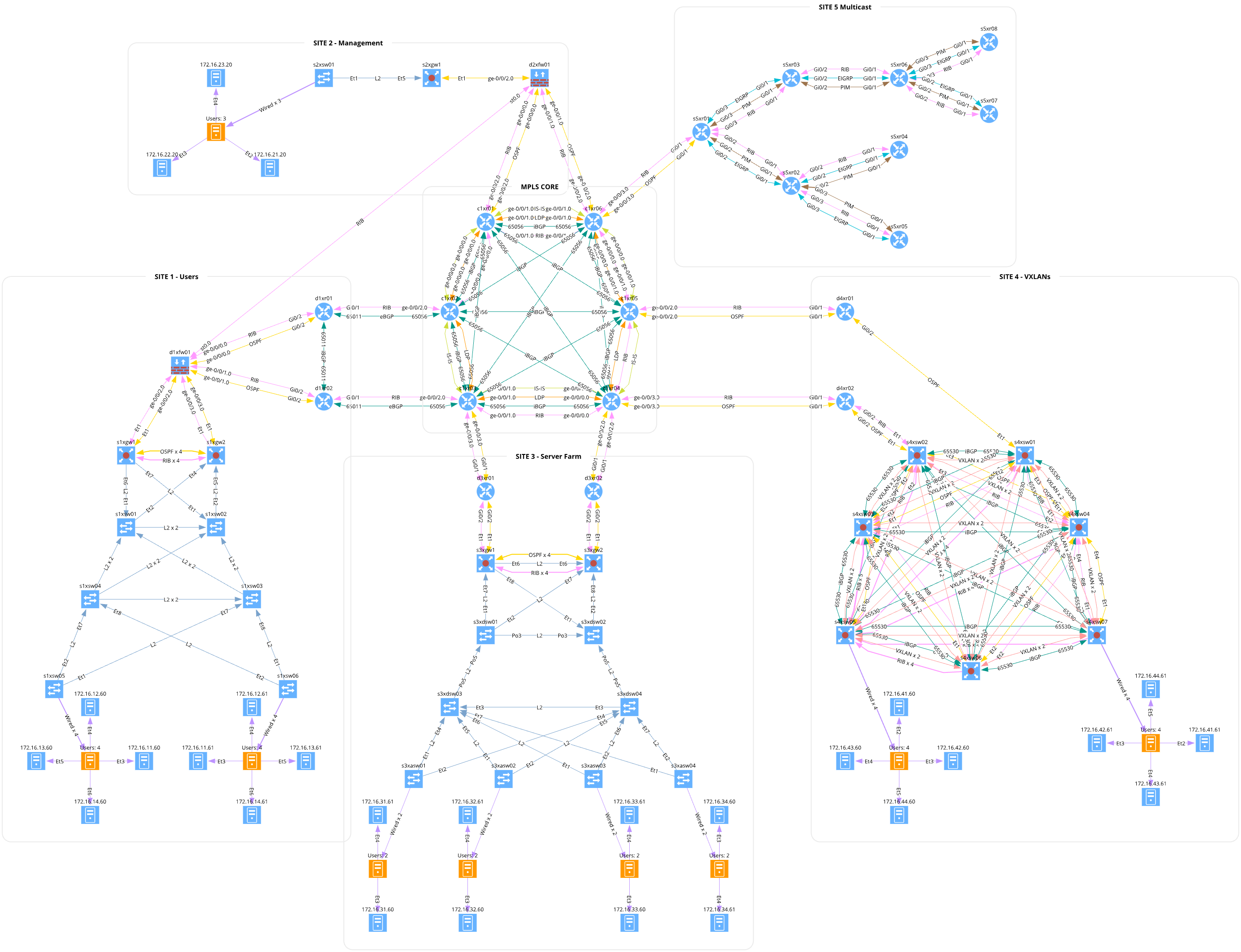
Milan Zapletal submitted the source code for a huge lab topology they built with netlab. It has almost 50 routers and over 50 Linux nodes to emulate end-users and servers.
They used netlab to configure VLANs, VRFs, IS-IS, OSPF, EIGRP, BGP, MPLS, VXLAN, and EVPN. Imagine how long it would take to configure all that by hand using a more traditional labbing tool.
Cyber Crane Mesh Topology Built with netlab
Milan Zapletal submitted the source code for a huge lab topology they built with netlab. It has almost 50 routers and over 50 Linux nodes to emulate end-users and servers.
They used netlab to configure VLANs, VRFs, IS-IS, OSPF, EIGRP, BGP, MPLS, VXLAN, and EVPN. Imagine how long it would take to configure all that by hand using a more traditional labbing tool.
Worth Reading: Talent Gap in IT
If you need a good rant about Thought Leaders, Talent Gap, and Certification-Based-Hiring, look no further than I see a different gap from here!. Here’s a choice tidbit:
Every single job description that requires some sort of certification must be treated with suspicion. Demanding a certification usually means that you don’t know what you want, and you’re just outsourcing your thinking to someone else.
Have fun!
Worth Reading: Talent Gap in IT
If you need a good rant about Thought Leaders, Talent Gap, and Certification-Based-Hiring, look no further than I see a different gap from here!. Here’s a choice tidbit:
Every single job description that requires some sort of certification must be treated with suspicion. Demanding a certification usually means that you don’t know what you want, and you’re just outsourcing your thinking to someone else.
Have fun!
Worth Exploring: PCAP Analysis with Generative AI
John Capobianco published the source code of his Packet Buddy application on GitHub. It’s a Python UI that takes a PCAP file, converts it to JSON, and includes that JSON as part of the ChatGPT chat, allowing you to discuss the captured packets with ChatGPT.
His idea is one of the best uses of generative AI in networking I’ve seen so far, as long as you remember that you’re dealing with an overconfident intern who has no problem making up an answer just to sound smart. Have fun!
Finally, if you don’t want to use ChatGPT (I wouldn’t blame you) or send captured data into The Cloud, someone already adapted his idea to use local LLMs.
Worth Exploring: PCAP Analysis with Generative AI
John Capobianco published the source code of his Packet Buddy application on GitHub. It’s a Python UI that takes a PCAP file, converts it to JSON, and includes that JSON as part of the ChatGPT chat, allowing you to discuss the captured packets with ChatGPT.
His idea is one of the best uses of generative AI in networking I’ve seen so far, as long as you remember that you’re dealing with an overconfident intern who has no problem making up an answer just to sound smart. Have fun!
Finally, if you don’t want to use ChatGPT (I wouldn’t blame you) or send captured data into The Cloud, someone already adapted his idea to use local LLMs.
DMVPN Videos Are Free to Download
It looks like DMVPN is still kicking; every other blue moon, I get a “Thank you” note from someone figuring out the DMVPN details from my first DMVPN webinar, so I decided to make those videos public. You can watch any video from the DMVPN Technology and Configuration without registration.
A tangential note in case you’re wondering how “easy” it is to refurbish old stuff:
- The webinar was recorded as a WebEx ARF recording.
- The WebEx MP4 exporter I used when trying to generate videos from my old ARF files was broken and couldn’t produce usable videos after a long silence (I muted the microphone during a coffee break). I gave up at that time
- A few weeks ago, I decided to replay the recording and create videos from the screen capture.
- Finally, it took my audio editor quite a while to make the sound recorded with 8-bit 8 kHz codec (thank you, WebEx) sound better than Apollo 11 communications with Houston.
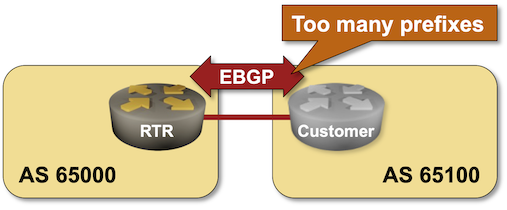
BGP Labs: Limit the Number of Accepted BGP Prefixes
Here’s an easy way to stop fat-finger incidents in which an end-user autonomous system redistributes IGP into BGP or advertises the whole DFZ routing table from affecting the entire Internet: limit the number of BGP prefixes your routers accept from your customers. You can practice this nifty feature in the next BGP lab exercise.
BGP Labs: Limit the Number of Accepted BGP Prefixes
Here’s an easy way to stop fat-finger incidents in which an end-user autonomous system redistributes IGP into BGP or advertises the whole DFZ routing table from affecting the entire Internet: limit the number of BGP prefixes your routers accept from your customers. You can practice this nifty feature in the next BGP lab exercise.

Multiline Expressions in Ansible Playbooks
Another week, another Ansible quirk 🤷♂️ Imagine you have a long Jinja2 expression, and you want to wrap it into multiple lines to improve readability. Using multiline YAML format seems to be the ideal choice:
---
- name: Test playbook
hosts: localhost
tasks:
- set_fact:
a: >
{{ 123 == 345 or
123 > 345 }}
It works every time 50% of the time (this time depending on your Ansible version).
Multiline Expressions in Ansible Playbooks
Another week, another Ansible quirk 🤷♂️ Imagine you have a long Jinja2 expression, and you want to wrap it into multiple lines to improve readability. Using multiline YAML format seems to be the ideal choice:
---
- name: Test playbook
hosts: localhost
tasks:
- set_fact:
a: >
{{ 123 == 345 or
123 > 345 }}
It works every time 50% of the time (this time depending on your Ansible version).
Rant: Multi-Vendor EVPN Fabrics
Daniel Dib tweeted about an old comment of mine a few days ago, adding1:
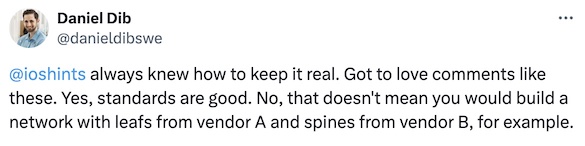
Not surprisingly, that was bound to upset a few people, and Roman Dodin quickly pointed out the EVPN interoperability tests:
Rant: Multi-Vendor EVPN Fabrics
Daniel Dib tweeted about an old comment of mine a few days ago, adding1:

Not surprisingly, that was bound to upset a few people, and Roman Dodin quickly pointed out the EVPN interoperability tests:
netlab 1.8.0: Control-Plane Daemons, BIRD, dnsmasq
I wanted to include open-source networking-related software into netlab topologies since (at least) the days I was writing the DHCP relaying saga. It turned out to be a bit more complex than I anticipated (more about that in another blog post), but I hope you’ll find it useful. netlab release 1.8.0 includes dnsmasq running as a DHCP server and BIRD running OSPF and BGP. ExaBGP and GoBGP are already on the wish list; if you have any other ideas, please start a GitHub discussion.
I had a hard time finding reasonable container images for BIRD; the BIRD team does not publish them, and everything else I found looked either abandoned or a hobby project. The solution turned out to be exceedingly simple: you cannot run the containers without Docker anyway, which means the docker build command is just a few keystrokes away. I added Dockerfiles needed to build those containers to the netlab source code and implemented the netlab clab build command as a thin wrapper around docker build. It takes just a few seconds (plus the time it takes to download the Ubuntu container image) to build the containers you need.
netlab 1.8.0: Control-Plane Daemons, BIRD, dnsmasq
I wanted to include open-source networking-related software into netlab topologies since (at least) the days I was writing the DHCP relaying saga. It turned out to be a bit more complex than I anticipated (more about that in another blog post), but I hope you’ll find it useful. netlab release 1.8.0 includes dnsmasq running as a DHCP server and BIRD running OSPF and BGP. ExaBGP and GoBGP are already on the wish list; if you have any other ideas, please start a GitHub discussion.
I had a hard time finding reasonable container images for BIRD; the BIRD team does not publish them, and everything else I found looked either abandoned or a hobby project. The solution turned out to be exceedingly simple: you cannot run the containers without Docker anyway, which means the docker build command is just a few keystrokes away. I added Dockerfiles needed to build those containers to the netlab source code and implemented the netlab clab build command as a thin wrapper around docker build. It takes just a few seconds (plus the time it takes to download the Ubuntu container image) to build the containers you need.
Worth Reading: Unbloating the Buffers
In case you’ve heard about bufferbloat but don’t know what it is: Dan Groshev wrote a nice bufferbloat for dummies blog post on the APNIC blog.
Worth Reading: Unbloating the Buffers
In case you’ve heard about bufferbloat but don’t know what it is: Dan Groshev wrote a nice bufferbloat for dummies blog post on the APNIC blog.
netlab on Packet Pushers
A few weeks ago, Ethan Banks invited me to chat about netlab, and we had great fun discussing its intricacies for almost an hour. I also managed to win the Buzzword Bingo describing netlab as
Intent-based infrastructure-as-code digital twins lifecycle management system
The podcast was published a few days ago; listen to it on the PacketPushers website or YouTube.
netlab on Packet Pushers
A few weeks ago, Ethan Banks invited me to chat about netlab, and we had great fun discussing its intricacies for almost an hour. I also managed to win the Buzzword Bingo describing netlab as
Intent-based infrastructure-as-code digital twins lifecycle management system
The podcast was published a few days ago; listen to it on the PacketPushers website or YouTube.
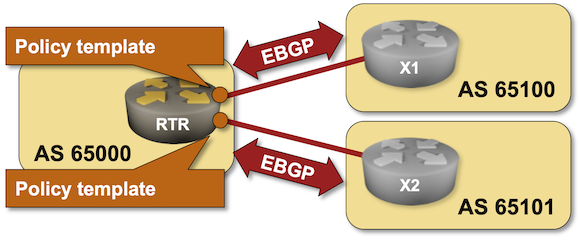
BGP Labs: Policy Templates
One of the previous BGP labs explained how you can use session templates to configure common TCP or BGP session parameters. Some BGP implementations have another templating mechanism: policy templates that you can use to apply consistent routing policy parameters to an EBGP neighbor. You can practice them in the next BGP lab exercise.