Video: netlab IP Address Management (IPAM)
Did you know that netlab includes full-blown IP address management? You can define address pools (or use predefined ones) and get IPv4 and IPv6 prefixes from those pools assigned to links, interfaces, and loopbacks. You can also assign static prefixes to links, use static IP addresses, interface addresses as an offset within the link subnet, or use unnumbered interfaces.
For an overview of netlab IPAM, watch the netlab address management video (part of the Network Automation Tools webinar), for more details read the netlab addressing tutorial.
Video: netlab IP Address Management (IPAM)
Did you know that netlab includes full-blown IP address management? You can define address pools (or use predefined ones) and get IPv4 and IPv6 prefixes from those pools assigned to links, interfaces, and loopbacks. You can also assign static prefixes to links, use static IP addresses, interface addresses as an offset within the link subnet, or use unnumbered interfaces.
For an overview of netlab IPAM, watch the netlab address management video (part of the Network Automation Tools webinar), for more details read the netlab addressing tutorial.
AMS-IX Outage: Layer-2 Strikes Again
On November 22nd, 2023, AMS-IX, one of the largest Internet exchanges in Europe, experienced a significant performance drop lasting more than four hours. While its peak performance is around 10 Tbps, it dropped to about 2.1 Tbps during the outage.
AMS-IX published a very sanitized and diplomatic post-mortem incident summary in which they explained the outage was caused by LACP leakage. That phrase should be a red flag, but let’s dig deeper into the details.
AMS-IX Outage: Layer-2 Strikes Again
On November 22nd, 2023, AMS-IX, one of the largest Internet exchanges in Europe, experienced a significant performance drop lasting more than four hours. While its peak performance is around 10 Tbps, it dropped to about 2.1 Tbps during the outage.
AMS-IX published a very sanitized and diplomatic post-mortem incident summary in which they explained the outage was caused by LACP leakage. That phrase should be a red flag, but let’s dig deeper into the details.
BGP Labs: Use BGP Route Reflectors
In the previous BGP labs, we built a network with two adjacent BGP routers and a larger transit network using IBGP. Now let’s make our transit network scalable with BGP route reflectors, this time using a slightly larger network:
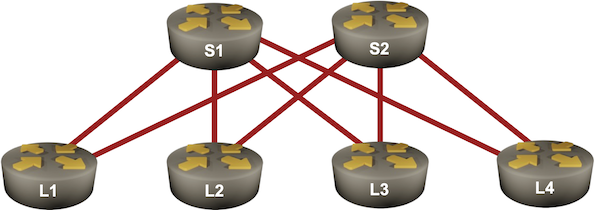
BGP Labs: Use BGP Route Reflectors
In the previous BGP labs, we built a network with two adjacent BGP routers and a larger transit network using IBGP. Now let’s make our transit network scalable with BGP route reflectors, this time using a slightly larger network:

netlab 1.7.0: Lab Validation, Fabrics, BGP Nerd Knobs
It’s been a while since the last netlab release. Most of that time was spent refactoring stuff that you don’t care about, but you might like these features:
- You can run automated lab validation tests with the netlab validate command. I will explain how I use that in BGP labs in a few days.
- If you want to build large leaf-and-spine topologies, you’ll love the fabric plugin.
- The bgp.domain plugin allows you to create topologies with multiple sites using the same BGP AS number.
- The bgp.policy plugin got AS-path prepending.
- bgp.originate plugin can be used to originate BGP IPv4 and IPv6 prefixes.
As always, we also improved the platform support:
netlab 1.7.0: Lab Validation, Fabrics, BGP Nerd Knobs
It’s been a while since the last netlab release. Most of that time was spent refactoring stuff that you don’t care about, but you might like these features:
- You can run automated lab validation tests with the netlab validate command. I will explain how I use that in BGP labs in a few days.
- If you want to build large leaf-and-spine topologies, you’ll love the fabric plugin.
- The bgp.domain plugin allows you to create topologies with multiple sites using the same BGP AS number.
- The bgp.policy plugin got AS-path prepending.
- bgp.originate plugin can be used to originate BGP IPv4 and IPv6 prefixes.
As always, we also improved the platform support:
The BGP Origin Attribute
Kristijan Taskovski asked an interesting question related to my BGP AS-prepending lab:
I’ve never personally done this on the net but….wouldn’t the BGP origin code also work with moving one’s ingress traffic similarly to AS PATH?
TL&DR: Sort of, but not exactly. Also, just because you can climb up ropes using shoelaces instead of jumars doesn’t mean you should.
Let’s deal with the moving traffic bit first.
The BGP Origin Attribute
Kristijan Taskovski asked an interesting question related to my BGP AS-prepending lab:
I’ve never personally done this on the net but….wouldn’t the BGP origin code also work with moving one’s ingress traffic similarly to AS PATH?
TL&DR: Sort of, but not exactly. Also, just because you can climb up ropes using shoelaces instead of jumars doesn’t mean you should.
Let’s deal with the moving traffic bit first.
Worth Reading: DNS over IPv6
What happens when you let a bunch of people work on different aspects of a solution without them ever talking to each other? You get DNS over IPv6. As nicely explained by Geoff Huston, this is just one of the bad things that could happen:
Worth Reading: DNS over IPv6
What happens when you let a bunch of people work on different aspects of a solution without them ever talking to each other? You get DNS over IPv6. As nicely explained by Geoff Huston, this is just one of the bad things that could happen:
Worth Reading: Use of HTTPS DNS Resource Records
Around 30 years after we got the first website, the powers that be realized it might make sense to put this is how you access a web server information (including its IPv4 and IPv6 address, and HTTP(S) support information) directly into DNS, using HTTPS Resource Records. It took us long enough 🤷♂️
Worth Reading: Use of HTTPS DNS Resource Records
Around 30 years after we got the first website, the powers that be realized it might make sense to put this is how you access a web server information (including its IPv4 and IPv6 address, and HTTP(S) support information) directly into DNS, using HTTPS Resource Records. It took us long enough 🤷♂️
30 Days Left to Buy ipSpace.net Subscription
When I announced the lifetime ipSpace.net subscription in early September, I also mentioned that you won’t be able to purchase any ipSpace.net subscription after December 31st, 2023.
As of today, you have 30 days left to decide, and don’t wait till the last minute – I plan to turn off the purchasing process sometime during the business hours of December 31st as I hope to have more interesting things to do in the evening.
The BGP Multi-Exit Discriminator (MED) Saga
Martijn Van Overbeek left this comment on my LinkedIn post announcing the BGP MED lab:
It might be fixed, but I can recall in the past that there was a lot of quirkiness in multi-vendor environments, especially in how different vendors use it and deal with the setting when the attribute does exist or does not have to exist.
TL&DR: He’s right. It has been fixed (mostly), but the nerd knobs never went away.
In case you’re wondering about the root cause, it was the vagueness of RFC 1771. Now for the full story ;)
The BGP Multi-Exit Discriminator (MED) Saga
Martijn Van Overbeek left this comment on my LinkedIn post announcing the BGP MED lab:
It might be fixed, but I can recall in the past that there was a lot of quirkiness in multi-vendor environments, especially in how different vendors use it and deal with the setting when the attribute does exist or does not have to exist.
TL&DR: He’s right. It has been fixed (mostly), but the nerd knobs never went away.
In case you’re wondering about the root cause, it was the vagueness of RFC 1771. Now for the full story ;)
BGP Labs: Set BGP Communities on Outgoing Updates
It’s hard to influence the behavior of someone with strong opinions (just ask any parent with a screaming toddler), and trying to persuade an upstream ISP not to send the traffic over a backup link is no exception – sometimes even AS path prepending is not a strong enough argument.
An easy solution to this problem was proposed in 1990s – what if we could attach some extra attributes (called communities just to confuse everyone) to BGP updates and use them to tell adjacent autonomous systems to lower their BGP local preference? You can practice doing that in the Attach BGP Communities to Outgoing BGP Updates lab exercise.
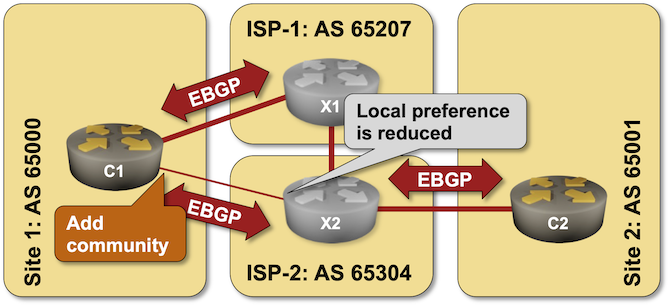
BGP Labs: Set BGP Communities on Outgoing Updates
It’s hard to influence the behavior of someone with strong opinions (just ask any parent with a screaming toddler), and trying to persuade an upstream ISP not to send the traffic over a backup link is no exception – sometimes even AS path prepending is not a strong enough argument.
An easy solution to this problem was proposed in 1990s – what if we could attach some extra attributes (called communities just to confuse everyone) to BGP updates and use them to tell adjacent autonomous systems to lower their BGP local preference? You can practice doing that in the Attach BGP Communities to Outgoing BGP Updates lab exercise.

Can a Router Use the Default Route to Reach BGP Next Hops?
TL&DR: Yes.
Starting with RFC 4271, Route Resolvability Condition:
- A route without an outgoing interface is resolvable if its next hop is resolvable without recursively using the same route.
- A route with an outgoing interface is always considered resolvable.
- BGP routes can be resolved through routes with just a next hop or an outgoing interface.