Creating MPLS/VPN Labs With netlab
Two week ago I described how to create a simple VRF Lite lab with netlab VRF configuration module. Adding MPLS/VPN to the mix and creating a full-blown MPLS/VPN lab is a piece of cake. In this blog post we’ll build a simple topology with two VRFs (red and blue) and two PE-routers:
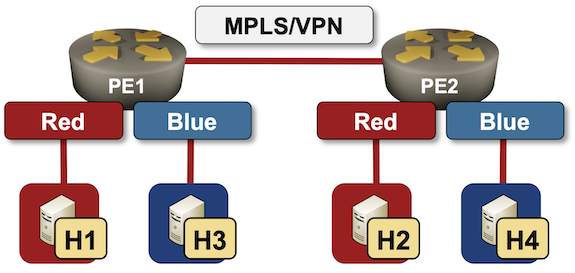
Lab topology
Is X.25 Still Alive?
Enrique Vallejo asked an interesting question a while ago:
When was X.25 official declared dead? Note that the wikipedia claims that it is still in use in parts of the world.
Wikipedia is probably right, and had several encounters with X.25 that would corroborate that claim. If you happen to have more up-to-date information, please leave a comment.
Is X.25 Still Alive?
Enrique Vallejo asked an interesting question a while ago:
When was X.25 official declared dead? Note that the wikipedia claims that it is still in use in parts of the world.
Wikipedia is probably right, and had several encounters with X.25 that would corroborate that claim. If you happen to have more up-to-date information, please leave a comment.
Detecting Byzantine Link Failures with SNMP
One of my readers has to deal with a crappy Network Termination Equipment (NTE)1 that does not drop local link carrier2 when the remote link fails. Here’s the original ASCII art describing the topology:
PE---------------NTE--FW---NMS
<--------IP-------->
He’d like to use interface SNMP counters on the firewall to detect the PE-NTE link failure. He’s using static default route toward PE on FW, and tried to detect the link failure with ifOutDiscards counter.
Detecting Byzantine Link Failures with SNMP
One of my readers has to deal with a crappy Network Termination Equipment (NTE)1 that does not drop local link carrier2 when the remote link fails. Here’s the original ASCII art describing the topology:
PE---------------NTE--FW---NMS
<--------IP-------->
He’d like to use interface SNMP counters on the firewall to detect the PE-NTE link failure. He’s using static default route toward PE on FW, and tried to detect the link failure with ifOutDiscards counter.
Multi-Platform Custom Configuration Templates in netsim-tools
In the Building a BGP Anycast Lab I described how you could use custom configuration templates to extend the functionality of netsim-tools.
That example used Cisco IOS… but what if you want to test the same functionality on multiple platforms? netsim-tools provides a nice trick: the custom configuration template could point to a directory with platform-specific templates. Let me show you how that works…
netlab Multi-Platform Custom Configuration Templates
In the Building a BGP Anycast Lab I described how you could use custom configuration templates to extend the netlab functionality.
That example used Cisco IOS… but what if you want to test the same functionality on multiple platforms? netlab provides a nice trick: the custom configuration template could point to a directory with platform-specific templates. Let me show you how that works…
OMG: Hop-by-Hop Path MTU Discovery
Straight from the “Bad Ideas Never Die” (see also RFC 1925 Rule 11) department: Geoff Huston described a proposal to use hop-by-hop IPv6 extension headers to implement Path MTU Discovery. In his words:
It is a rare situation when you can create an outcome from two somewhat broken technologies where the outcome is not also broken.
IETF should put rules in place similar to the ones used by the patent office (Thou Shalt Not Patent Perpetual Motion Machine), but unfortunately we’re way past that point. Back to Geoff:
It appears that the IETF has decided that volume is far easier to achieve than quality. These days, what the IETF is generating as RFCs is pretty much what the IETF accused the OSI folk of producing back then: Nothing more than voluminous paperware about vapourware!
OMG: Hop-by-Hop Path MTU Discovery
Straight from the “Bad Ideas Never Die” (see also RFC 1925 Rule 11) department: Geoff Huston described a proposal to use hop-by-hop IPv6 extension headers to implement Path MTU Discovery. In his words:
It is a rare situation when you can create an outcome from two somewhat broken technologies where the outcome is not also broken.
IETF should put rules in place similar to the ones used by the patent office (Thou Shalt Not Patent Perpetual Motion Machine), but unfortunately we’re way past that point. Back to Geoff:
It appears that the IETF has decided that volume is far easier to achieve than quality. These days, what the IETF is generating as RFCs is pretty much what the IETF accused the OSI folk of producing back then: Nothing more than voluminous paperware about vapourware!
Video: Kubernetes Networking Model
Pods are a basic building block of any Kubernetes-based deployment… but what exactly are they and how are they related to Kubernetes networking? Stuart Charlton unraveled that mystery in the Understanding Pods video (part of Kubernetes Networking Deep Dive webinar)
Video: Understanding Kubernetes Pods
Pods are a basic building block of any Kubernetes-based deployment… but what exactly are they and how are they related to Kubernetes networking? Stuart Charlton unraveled that mystery in the Understanding Pods video (part of Kubernetes Networking Deep Dive webinar)
netsim-tools Release 1.2.1: More MPLS and VRFs, Dell OS10, Cumulus 5.0 on Containerlab
I already mentioned the netsim-tools Easter Egg, here are the other cool features shipping in release 1.2.1:
- Dell OS10 on libvirt (including BGP, OSPFv2, OSPFv3 and VRF Lite) by Stefano Sasso
- VRFs, MPLS, and MPLS/VPN support on Mikrotik RouterOS and VyOS by Stefano Sasso
- Containerlab support for Cumulus 5.0 with NVUE including Simple VRF-Lite by Julien Dhaille
To upgrade netsim-tools, use pip3 install --upgrade netsim-tools; if you’re starting from scratch, read the installation instructions.
New in netlab: More MPLS and VRFs, Dell OS10, Cumulus 5.0 on Containerlab
I already mentioned the netsim-tools Easter Egg, here are the other cool features shipping in release 1.2.1:
- Dell OS10 on libvirt (including BGP, OSPFv2, OSPFv3 and VRF Lite) by Stefano Sasso
- VRFs, MPLS, and MPLS/VPN support on Mikrotik RouterOS and VyOS by Stefano Sasso
- Containerlab support for Cumulus 5.0 with NVUE including Simple VRF-Lite by Julien Dhaille
Network Digital Twins Work Best in PowerPoint
A friend of mine sent me the following question a few months ago:
I thought you might know the best way (currently) to create a digital clone of parts of a production network? The objective is to test changes against a test network as part of a CI/CD process. Ideally, there would be an automation that could replicate selected parts of a production network in a test network.
TL&DR: Sounds great, but you might be solving the wrong problem.
Network Digital Twins Work Best in PowerPoint
A friend of mine sent me the following question a few months ago:
I thought you might know the best way (currently) to create a digital clone of parts of a production network? The objective is to test changes against a test network as part of a CI/CD process. Ideally, there would be an automation that could replicate selected parts of a production network in a test network.
TL&DR: Sounds great, but you might be solving the wrong problem.
Everything Is Better with a GUI (even netsim-tools)
Some people think that everything is better with Bluetooth. They’re clearly wrong; according to the ancient wisdom of product managers working for networking vendors, everything is better with a GUI.
Now imagine adding network topology visualizer and GUI-based device access with in-browser SSH to an intent-based infrastructure-as-code virtual network function labbing tool. How’s that for a Bullshit Bingo winner1?
Everything Is Better with a GUI (even netlab)
Some people think that everything is better with Bluetooth (or maybe it’s AI these days). They’re clearly wrong; according to the ancient wisdom of product managers working for networking vendors, everything is better with a GUI.
Now imagine adding network topology visualizer and GUI-based device access with in-browser SSH to an intent-based infrastructure-as-code virtual network function labbing tool. How’s that for a Bullshit Bingo winner1?
Worth Reading: New Linux Command Line Tools
Julia Evans published a long list of new(ish) Linux command line tools. For example, did you ever want to have directory listing in nicely formatted JSON? How about ls -l | jc --ls | jq .?
Quite a few of these tools also work on Mac and can be installed with HomeBrew. Some are written in a scripting language, so you could (in theory) also use them on Windows (without WSL).
Worth Reading: New Linux Command Line Tools
Julia Evans published a long list of new(ish) Linux command line tools. For example, did you ever want to have directory listing in nicely formatted JSON? How about ls -l | jc --ls | jq .?
Quite a few of these tools also work on Mac and can be installed with HomeBrew. Some are written in a scripting language, so you could (in theory) also use them on Windows (without WSL).
Video: Challenges of Managed SD-WAN Services
When I published a link to the Is MPLS/VPN Too Complex? blog post to LinkedIn, someone asked whether I’m skeptical about service provider SD-WAN services due to lack of skills, and Kristijan Taskovski quickly identified the root cause in his reply:
The argument of a lack of skill is only one that is perpetuated by businesses. It’s not perpetuated by engineers. People that are trained, honed, and knowledgeable are expensive. Expense is the number one enemy for a business.
That’s exactly why I think most managed SD-WAN services will be a dismal failure.