Imperva Researchers Find Hundreds of Vulnerable Docker Hosts Exploited by Cryptominers
 The currency miners were relying on a Docker runC vulnerability discovered in early February (later...
The currency miners were relying on a Docker runC vulnerability discovered in early February (later...
Aqua Security, Twistlock Upgrade Their Cloud Native Security Platforms
 The increasingly complex array of cloud environments used by businesses provides bad actors with...
The increasingly complex array of cloud environments used by businesses provides bad actors with...
Verizon Scoops Up ProtectWise, Adds Managed Endpoint Protection
 The operator also unveiled its second annual Mobile Security Index, which found that more companies...
The operator also unveiled its second annual Mobile Security Index, which found that more companies...
Telia to Deploy 5G FWA Network in Finland
 The Finnish carrier is working with Nokia on the fixed wireless network equipment and is looking to...
The Finnish carrier is working with Nokia on the fixed wireless network equipment and is looking to...
Episode 46 – Bridging The Gap Between IT And The Business
Historically, engineers and practitioners have had a hard time communicating IT’s value to business leadership. This gap between IT and the business will present even greater challenges as businesses grow to depend on their networks and systems for even more strategic advantage. In this episode we explore some of the reasons why this gap exists and discuss some potential things you can do to help bridge the gap between IT engineering and business leadership.
We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus Networks makes networking software for the open, modern data center. It’s the only open networking software that allows you to affordably build and efficiently operate your network like the worlds largest data center operators. Cumulus also just launched a brand new certification program offering free resources, on-demand modules, live training, and a certifications exam. If you would like to learn more you can head on over to https://cumulusnetworks.com/certified
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Episode 46 Continue reading
Loggly
 Loggly is a cloud logging and and analysis platform. This article will demonstrate how to integrate network events generated from industry standard sFlow instrumentation build into network switches.
Loggly is a cloud logging and and analysis platform. This article will demonstrate how to integrate network events generated from industry standard sFlow instrumentation build into network switches.Loggly offers a free 14 day evaluation, so you can try this example at no cost.ICMP unreachable describes how monitoring ICMP destination unreachable messages can help identify misconfigured hosts and scanning behavior. The article uses the sFlow-RT real-time analytics software to process the raw sFlow and report on unreachable messages.
The following script, loggly.js, modifies the sFlow-RT script from the article to send events to the Loggly HTTP/S Event Endpoint:
var token = 'xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx';Some notes on the script:
var url = 'https://logs-01.loggly.com/inputs/'+token+'/tag/http/';
var keys = [
'icmpunreachablenet',
'icmpunreachablehost',
'icmpunreachableprotocol',
'icmpunreachableport'
];
for (var i = 0; i < keys.length; i++) {
var key = keys[i];
setFlow(key, {
keys:'macsource,ipsource,macdestination,ipdestination,' + key,
value:'frames',
log:true,
flowStart:true
});
}
setFlowHandler(function(rec) {
var keys = rec.flowKeys.split(',');
var msg = {
flow_type:rec.name,
src_mac:keys[0],
src_ip:keys[1],
dst_mac:keys[2],
dst_ip:keys[3],
unreachable:keys[4]
};
try { http(url,'post','application/json',JSON.stringify(msg)); }
catch(e) { logWarning(e); };
}, keys);
- Modify the script to use the correct token for your Loggly account.
- Including MAC addresses can help identify Continue reading
NTT Security Acquires Application Security Provider WhiteHat Security
 Founded by former Yahoo security officer Jeremiah Grossman, WhiteHat takes a DevSecOpps approach to...
Founded by former Yahoo security officer Jeremiah Grossman, WhiteHat takes a DevSecOpps approach to...
SSH Compromise Detection Using Flow Data
The post SSH Compromise Detection Using Flow Data appeared first on Noction.
Anyone Using Intel Omni-Path?
One of my subscribers sent me this question after watching the latest batch of Data Center Fabrics videos:
You haven’t mentioned Intel's Omni-Path at all. Should I be surprised?
While Omni-Path looks like a cool technology (at least at the whitepaper level), nobody ever mentioned it (or Intel) in any data center switching discussion I was involved in.
Read more ...Citrix Leans In on Automation to Secure Its SD-WAN
 One of the ways that Citrix has bolstered its security and automation is through an integration...
One of the ways that Citrix has bolstered its security and automation is through an integration...
Stopping Drupal’s SA-CORE-2019-003 Vulnerability
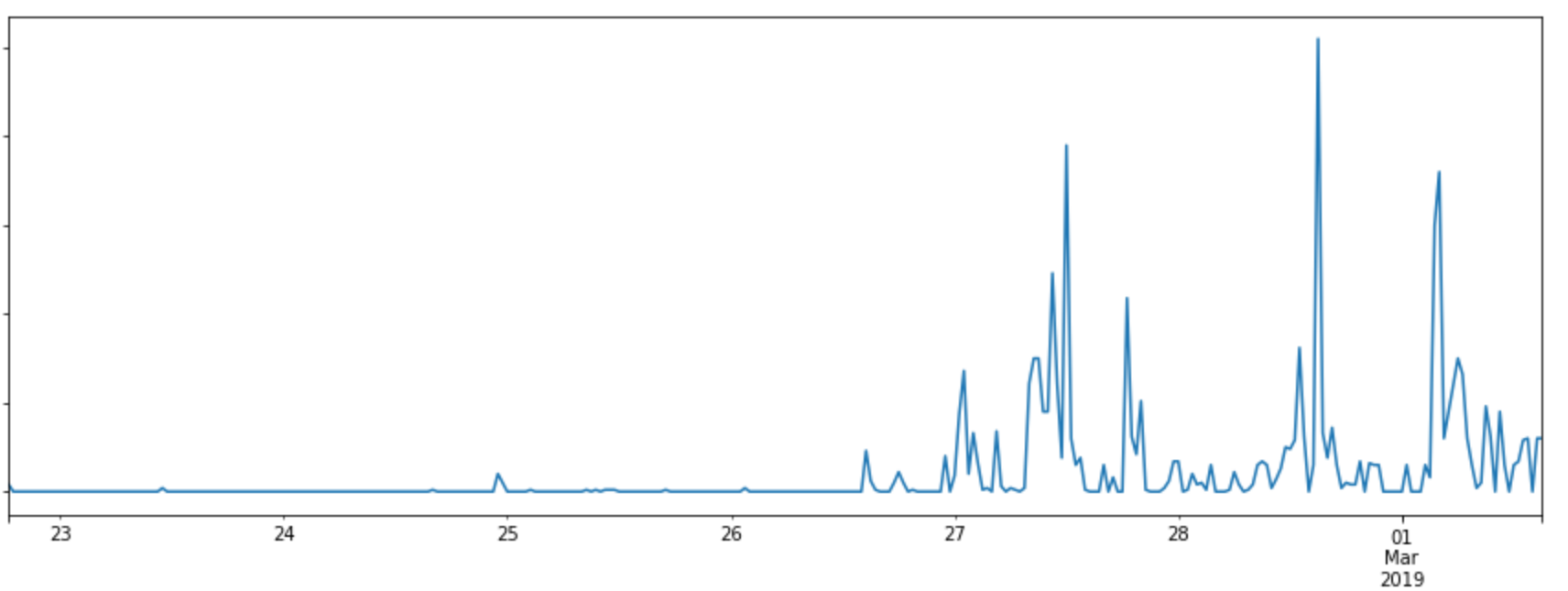
On the 20th February 2019, Drupal announced that they had discovered a severe vulnerability and that they would be releasing a patch for it the next day. Drupal is a Content Management System used by many of our customers, which made it important that our WAF protect against the vulnerability as quickly as possible.
As soon as Drupal released their patch, we analysed it to establish what kind of payloads could be used against it and created rules to mitigate these. By analysing the patch we were able to put together WAF rules to protect cloudflare customers running Drupal.
We identified the type of vulnerability we were dealing within 15 minutes. From here, we were able to deploy rules to block the exploit well before any real attacks were seen.
The exploit
As Drupal's release announcement explains, a site is affected if:
From looking at the patch we very quickly realised the exploit would be based on deserialization. The option ['allowed_classes' Continue reading
RSA Conference: Rise of the Robots (and the Women)
 The security landscape is essentially AI versus AI. May the best man, err, machine win.
The security landscape is essentially AI versus AI. May the best man, err, machine win.
Cumulus Networks Named to CRN Data Center 50
Cumulus Networks is proud to announce CRN®, a brand of The Channel Company, has named us to its 2019 Data Center 50 list.
This annual list identifies technology suppliers that offer the right management tools to help businesses and solution providers ensure data centers run with maximum performance and efficiency. We couldn’t be more thrilled! This accomplishment really solidifies our vision — to build the modern data center networks for applications of the future.
It’s been a while since we updated our blog community with our evolved vision for the modern data center, so we thought this would be a great opportunity to review a little bit about what Cumulus has been doing lately and how our products have evolved.
Our story — Building the modern data center
We pride ourselves on providing networking software to design, run and operate modern data centers that are simple, open, resilient, scalable and operationally efficient.
Our network operating system, Cumulus Linux, is a powerful, open network operating system that allows you to automate, customize and scale using web-scale principles like the world’s largest data centers.

When it comes to data center networks, traditional network solutions are unable keep up with the pace of Continue reading




