Facebook’s Mattress Problem with Privacy

If you haven’t had a chance to watch the latest episode of the Gestalt IT Rundown that I do with my co-workers every Wednesday, make sure you check this one out. Because it’s the end of the year it’s customary to do all kinds of fun wrap up stories. This episode focused on what we all thought was the biggest story of the year. For me, it was the way that Facebook completely trashed our privacy. And worse yet, I don’t see a way for this to get resolved any time soon. Because of the difference between assets and liabilities.
Contact The Asset
It’s no secret that Facebook knows a ton about us. We tell it all kinds of things every day we’re logged into the platform. We fill out our user profiles with all kinds of interesting details. We click Like buttons everywhere, including the one for the Gestalt IT Rundown. Facebook then keeps all the data somewhere.
But Facebook is collecting more data than that. They track where our mouse cursors are in the desktop when we’re logged in. They track the amount of time we spend with the mobile app open. They track information in the background. Continue reading
Encrypting DNS end-to-end
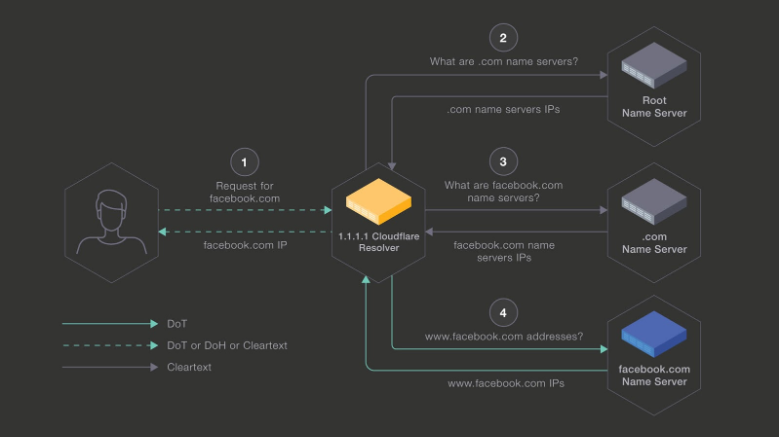
Over the past few months, we have been running a pilot with Facebook to test the feasibility of securing the connection between 1.1.1.1 and Facebook’s authoritative name servers. Traditionally, the connection between a resolver and an authoritative name server is unencrypted i.e. over UDP.
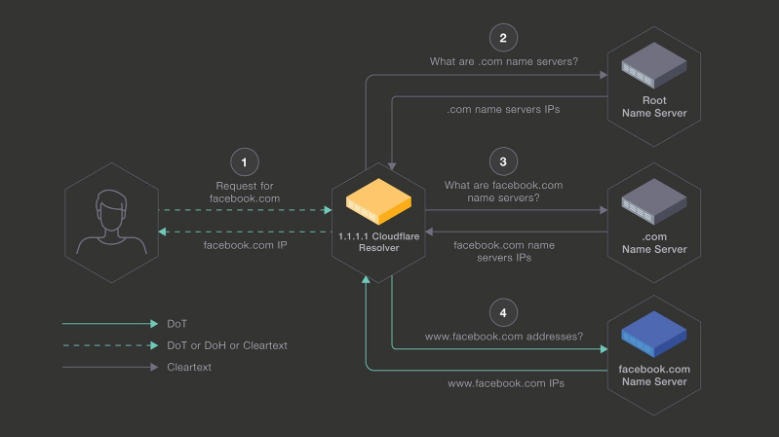
In this pilot we tested how an encrypted connection using TLS impacts the end-to-end latency between 1.1.1.1 and Facebook’s authoritative name servers. Even though the initial connection adds some latency, the overhead is amortized over many queries. The resulting DNS latency between 1.1.1.1 and Facebook’s authoritative name servers is on par with the average UDP connections.
To learn more about how the pilot went, and to see more detailed results, check out the complete breakdown over on Code, Facebook's Engineering blog.
Youth@IGF Fellow Story: How Far Are You From the Internet?

Growing up, a family friend will run all the way from her house with a pot of soup hoping to find out something we had at home that could complement the soup she had. On days when my twin sister and I were also missing a part of a meal, she will also return the good deed. Though the distance was not a short one, the thoughts of having a complete meal urged us on.
This neighbor of mine currently studies in Ukraine and none of us has or late had any thoughts of running all the way from Ghana to Ukraine – that will be a new record for the longest run.
The world is currently undergoing a difficult transformation with a rapid migration of almost all manual process to digital and the effect is a massive one both in advantages and disadvantages.
Just like distance resulted in the gap with my friend who now studies many miles away, several reasons have also been identified to be the ones causing the widening digital gap.
Some of the common ones are:
- Access – the ability to actually go online and connect to the Internet (largely relying on the constant supply Continue reading
Firewall Rules – Priority and Ordering


Firewall Rules are one of the best security features we released this year and have been an overwhelming success. Customers have been using Firewall Rules to solve interesting security related use cases; for example, advanced hotlink protection, restricting access to embargoed content (e.g. productId=1234), locking down sensitive API endpoints, and more.
One of the biggest pieces of feedback from the Cloudflare community, Twitter, and via customer support, has been around the order in which rules are actioned. By default, Firewall Rules have a default precedence, based on the actions set on the rule:

If two or more rules match a request, but have different actions, the above precedence will take effect. However, what happens if you've got a bad actor who needs to be blocked from your API, and you have other specific allow or challenge rules already created for their originating ASN or a perhaps one of your URLs? Once a Firewall Rule is matched, it will not continue processing other rule, unless you are using the Log action. Without a method of overriding the default precedence, you cannot easily achieve what's needed.
Today, we’re launching the ability for customers to change the ordering of their rules. Continue reading
Composable Infrastructure Players to Watch in 2019
 The technology is still in its infancy with only a handful of vendors shipping products. We expect to see more action in 2019.
The technology is still in its infancy with only a handful of vendors shipping products. We expect to see more action in 2019.
Service Mesh Mania
Service meshes will be an important component of your containerized environments whether on-premises or in the cloud.
That’s It for 2018 ;)
It’s been a long year – over 230 blog posts, 30 live webinar sessions, three online courses, half-dozen workshops, tons of presentations… it’s time Irena and myself disconnect, and so should you.
Wish you a quiet and merry Christmas with your loved ones and all the best in 2019! We’ll be back in early January.
Gnome3 Customise Shell Theme
Customise a Gnome3 user shell theme.Gnome3 Customise Shell Theme
I recently re-installed Ubuntu 1804 on my laptop and I though I would give the PopOS desktop theme from system76 a try. The verdict? It's very very nice. Next time I do a re-install or get a new laptop I think I will use PopOS which is based in Ubuntu anyway. Side note: If a System76...US Indicts Chinese Hackers in MSP Network Scheme
 While the government didn’t name the network providers, Reuters reports that HPE and IBM were among the compromised networks.
While the government didn’t name the network providers, Reuters reports that HPE and IBM were among the compromised networks.